*Doctor (HTB)
HackTheBox – Doctor Write-Up
topics: Linux Privilege Escalation
Enumeration
Local Privilege Escalation
System Privilege Escalation
tools:
Enumeration
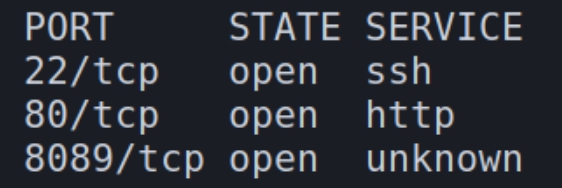
initial autorecon and nmapAutomator scans
We have three ports open on this machine SSH, HTTP and HTTPS. I first inspected the unique port 8089
HTTP
w
w
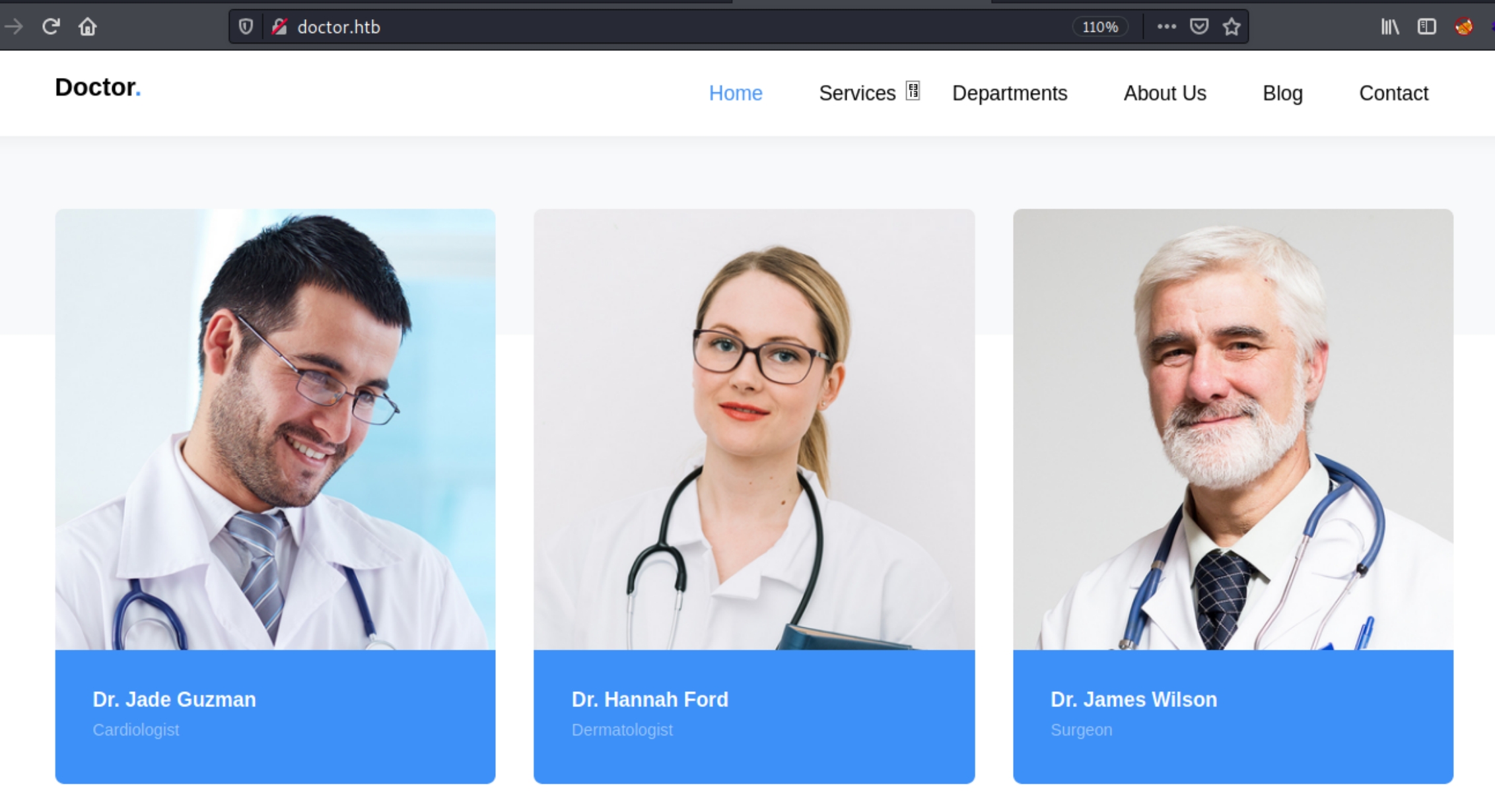
scroll further and find three pictures of highlighted doctors, need to find username syntax and/or credentials for doctors Jade Guzman, Hannah Ford, and James Wilson.
w
HTTPS
w
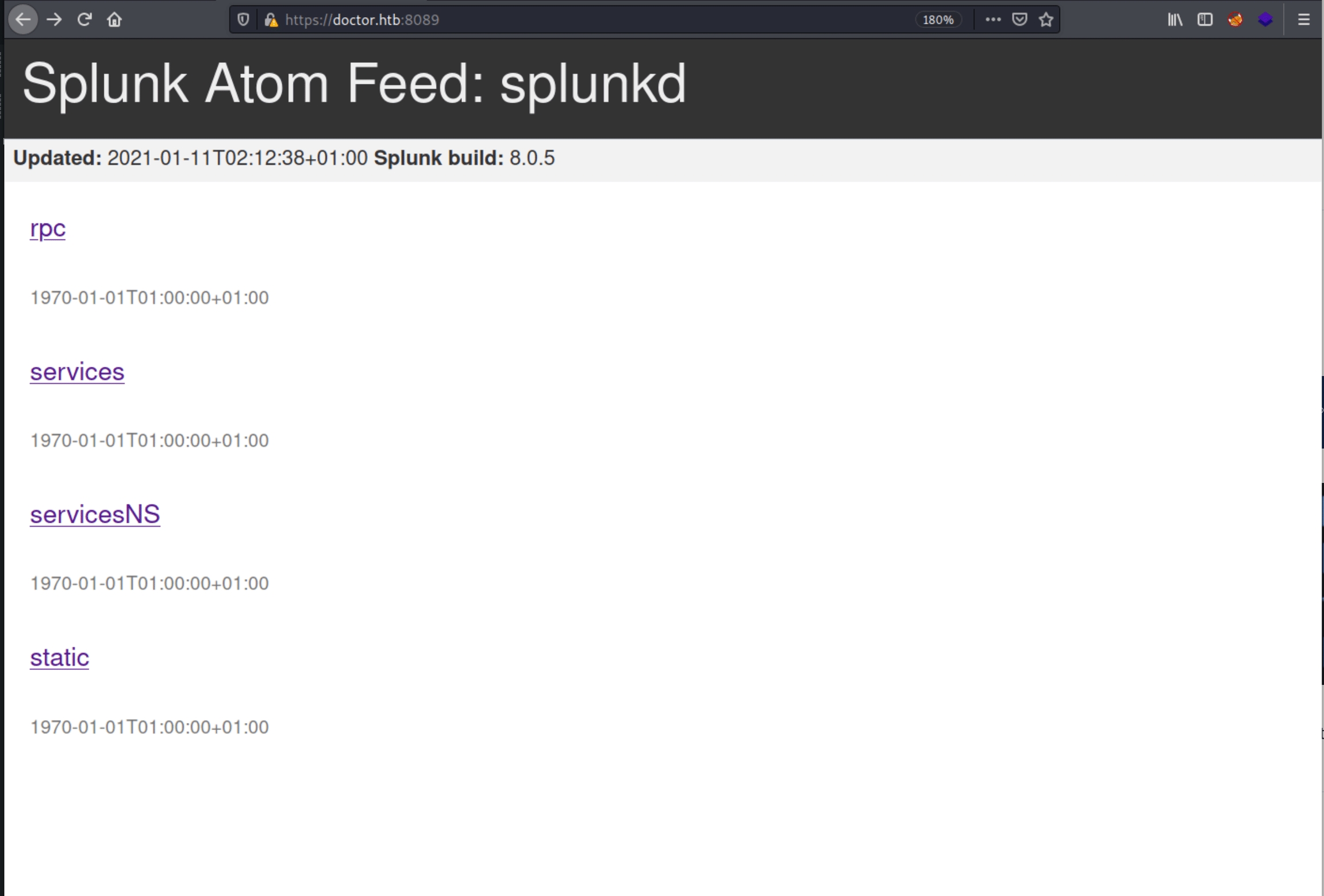
navigating to /splunk returns a 404 status code.
default creds admin:changeme do not work. changeme also doesnt work with guessed syntax of other three users found
we have three usernames and a login page for services and servicesNS both of which contain sensitive information once credentials are found.
find username syntax for HTTPS login
find passwords for usernames after syntax for HTTPS enum (decrypt?)
through research for the Splunk docs for version 8.1.1 I learned that once admin credentials are obtained, they can list all the credentials stored at the storage/passwords endpoint of the application. Presumably of all users on the system.
w
Local Privilege Escalation
Root Privilege Escalation
Last updated