OWASP Top 10 2020
TryHackMe OWASP Top 10 2020 Overview
TryHackMe – OWASP Top 10 Write-Up
topics: Web Application vulnerabilities, cross site scripting (XSS), command injection, broken authentication misconfigurations, sensitive data exposure through known vulnerabilities, XML external entity (XXE), misconfigured access control/access to logs, insecure deserialization
Overview of Vulnerabilities
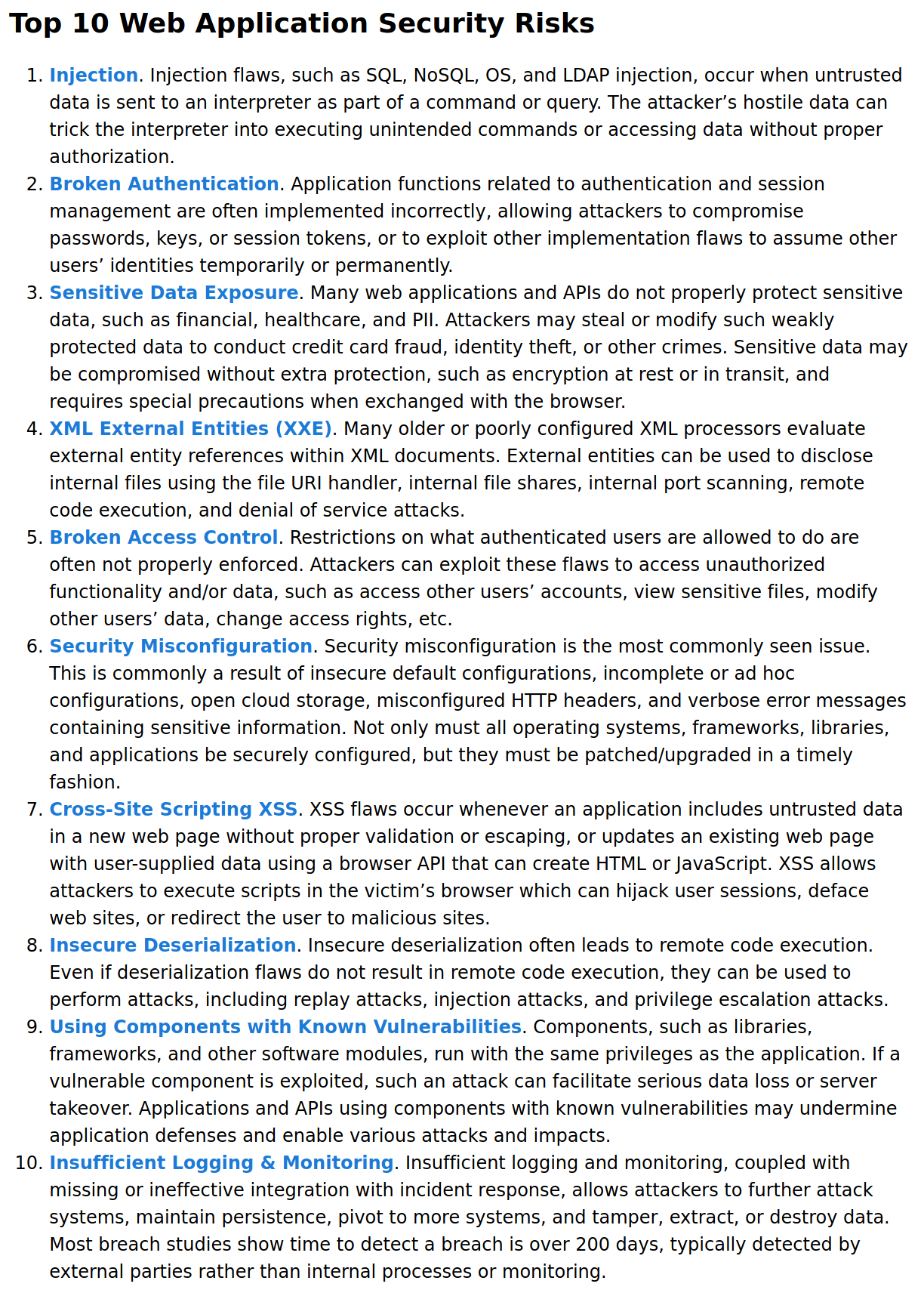
Injection
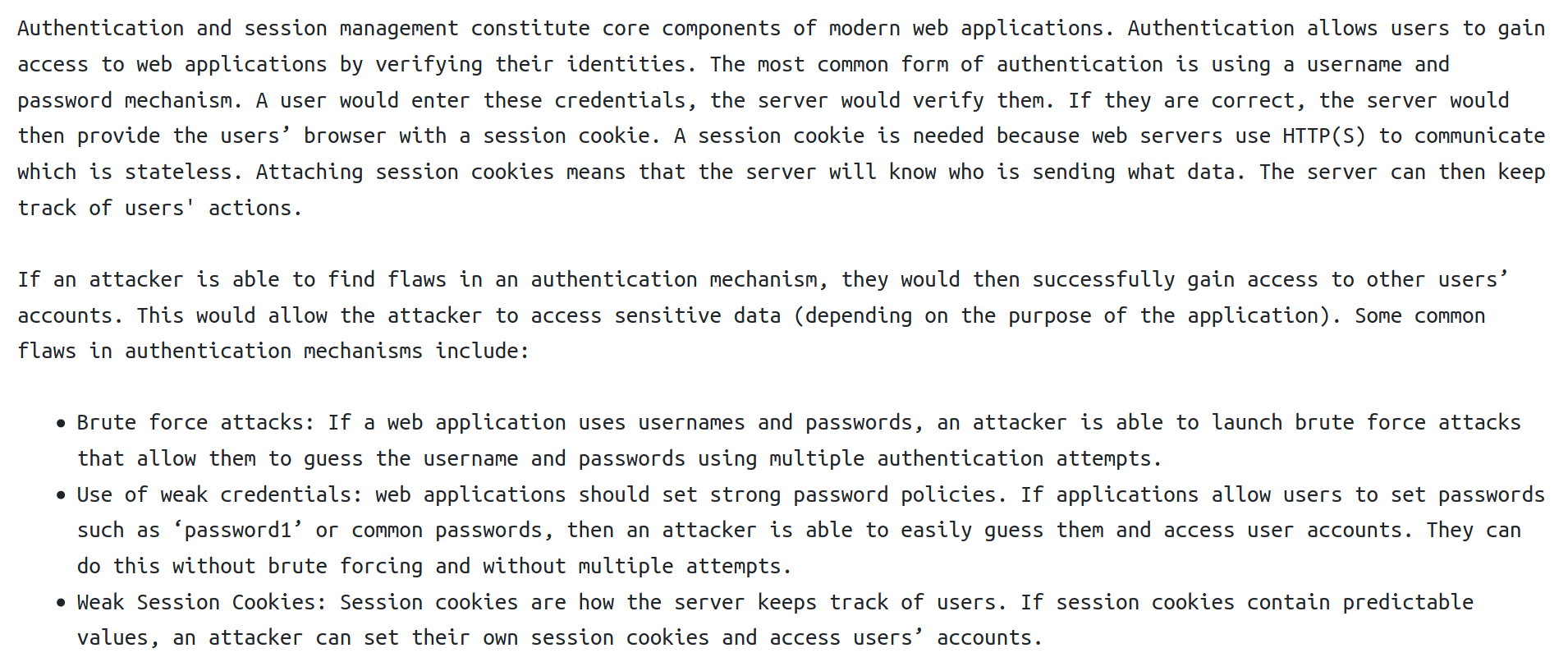
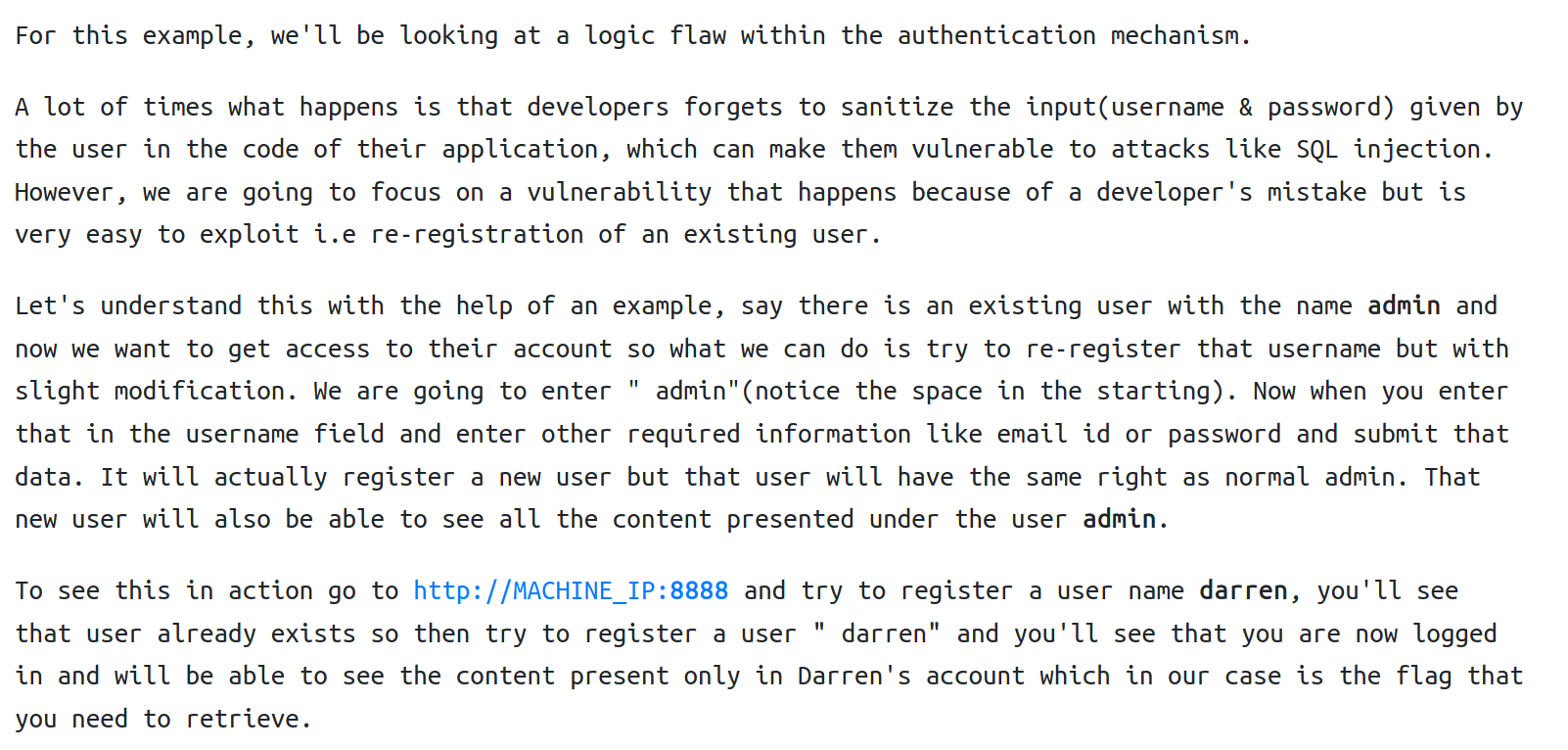
Broken Authentication
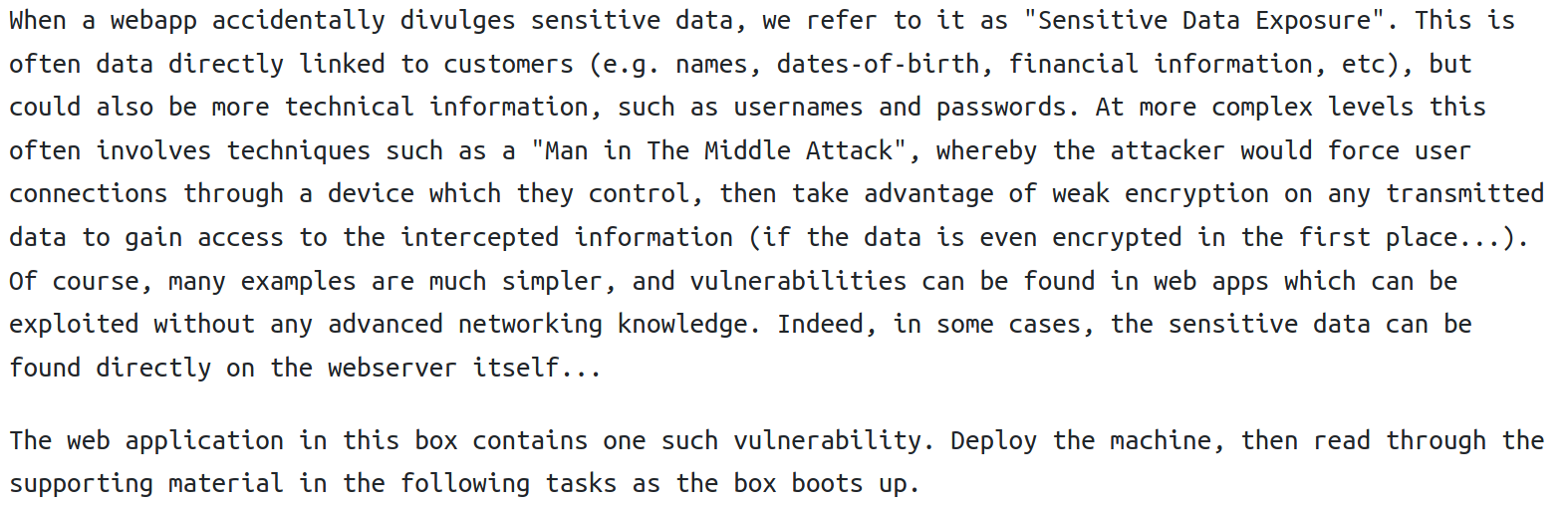
Sensitive Data Exposure
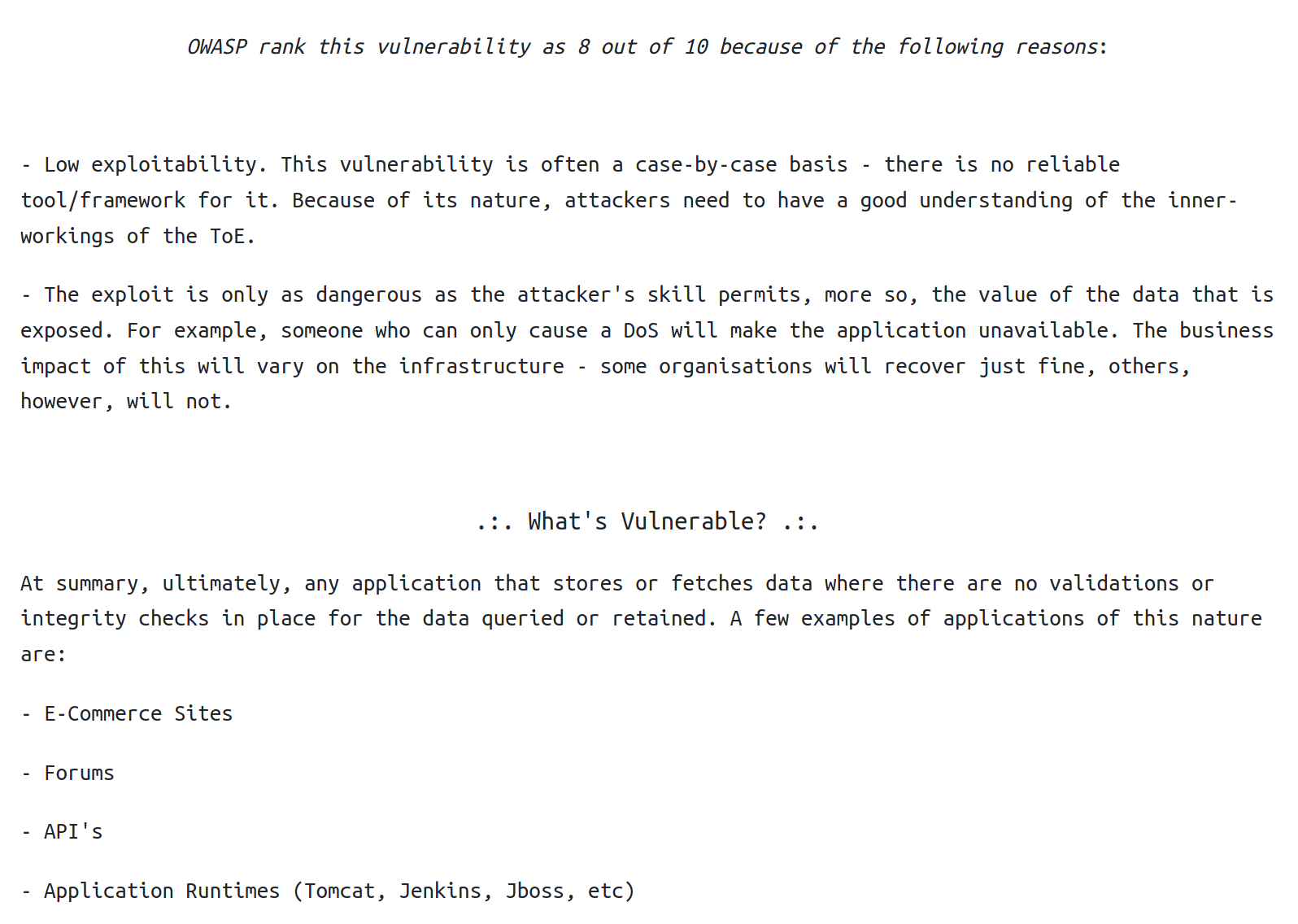
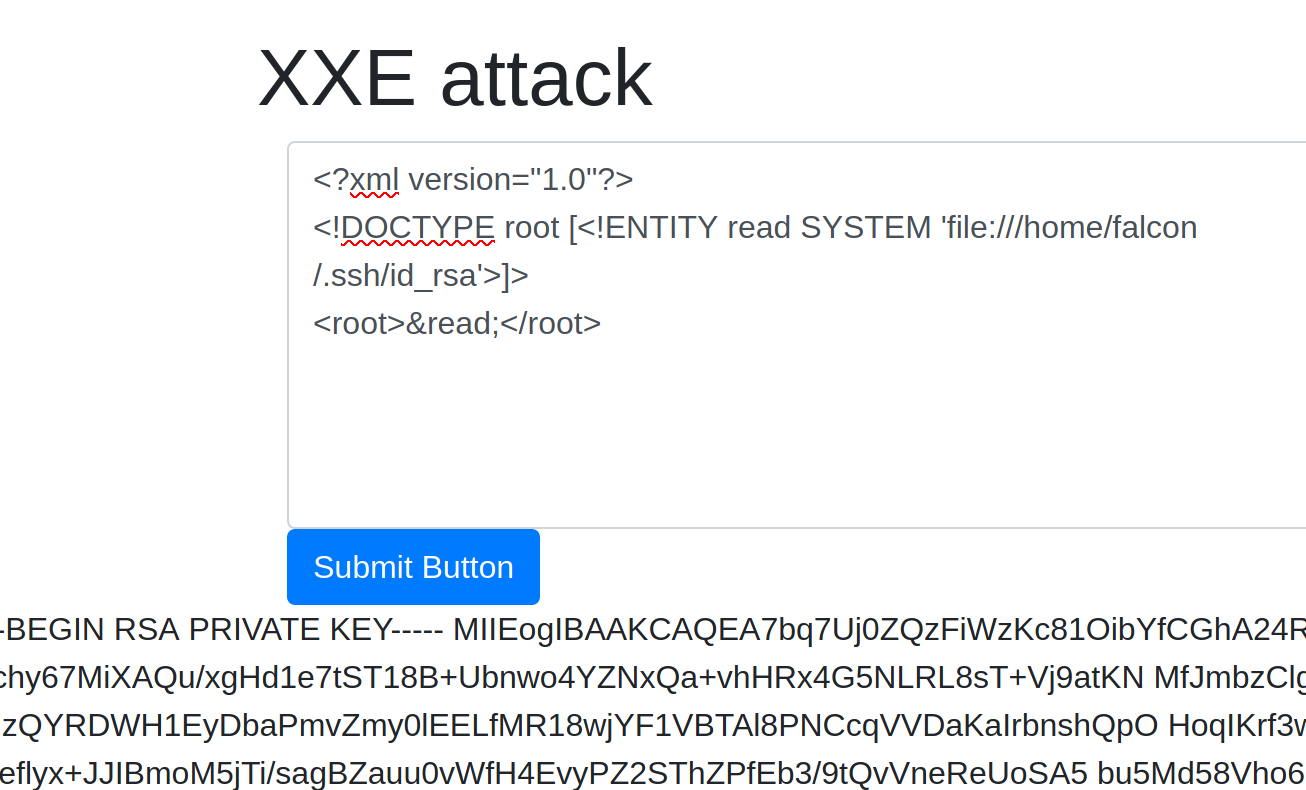
XML External Entity
Broken Access Control
Security Misconfiguration
Cross-site Scripting
Insecure Deserilization
Components with Known Vulnerabilities
Insufficient Logging & Monitoring
Overview - OWASP Top 10 Web Application Vulnerabilities
OWASP is is an online community that produces freely-available articles, methodologies, documentation, tools, and technologies revolving around Web Application Security. They categorize the most severe web application vulnerabilities in a list known as the OWASP Top 10, the vulnerabilities listed below
I will be running through basic definitions and examples of the top 10.
Injection
Per the room:
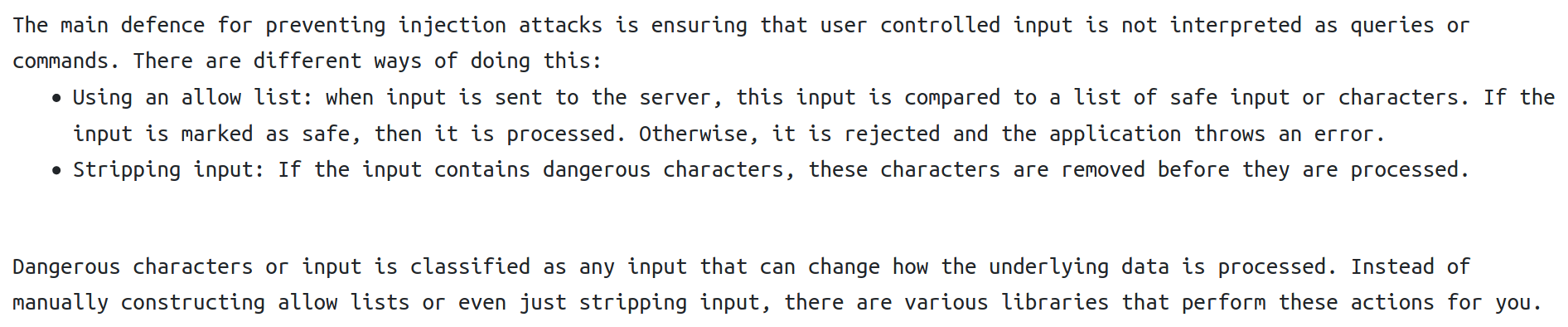
Injection flaws are very common in applications today. These flaws occur because user controlled input is interpreted as actual commands or parameters by the application. Injection attacks depend on what technologies are being used and how exactly the input is interpreted by these technologies. Some common examples include:
SQL Injection: This occurs when user controlled input is passed to SQL queries. As a result, an attacker can pass in SQL queries to manipulate the outcome of such queries.
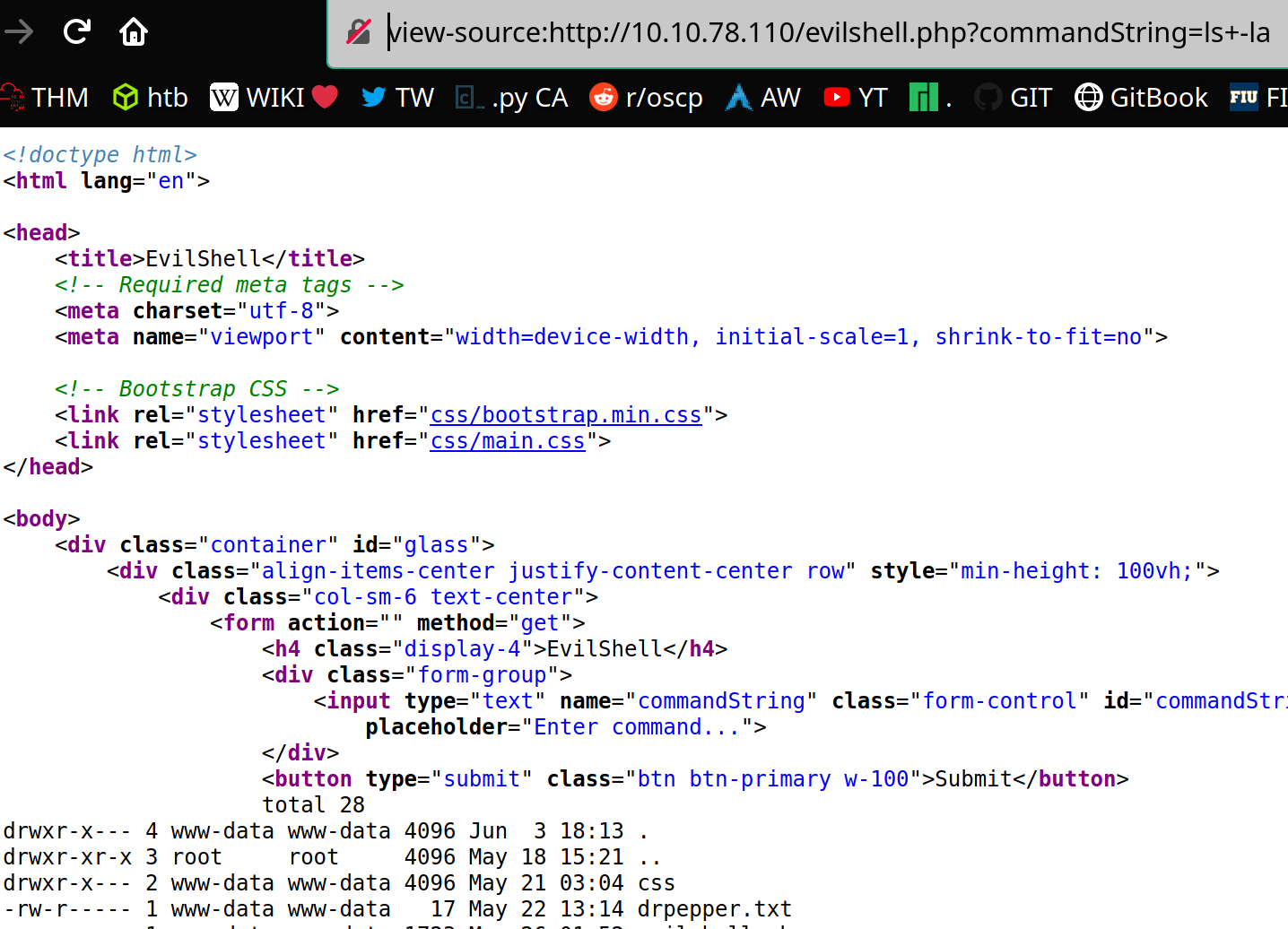
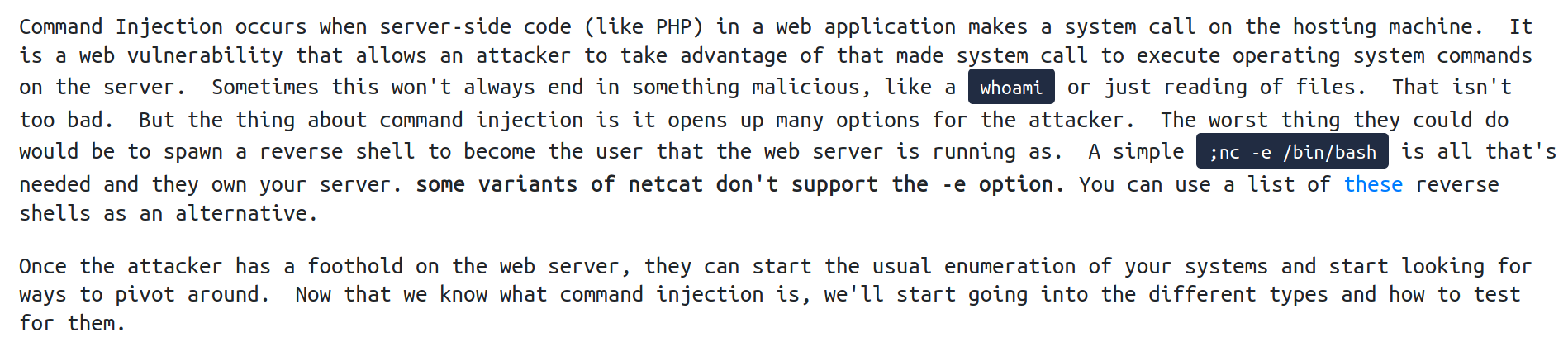
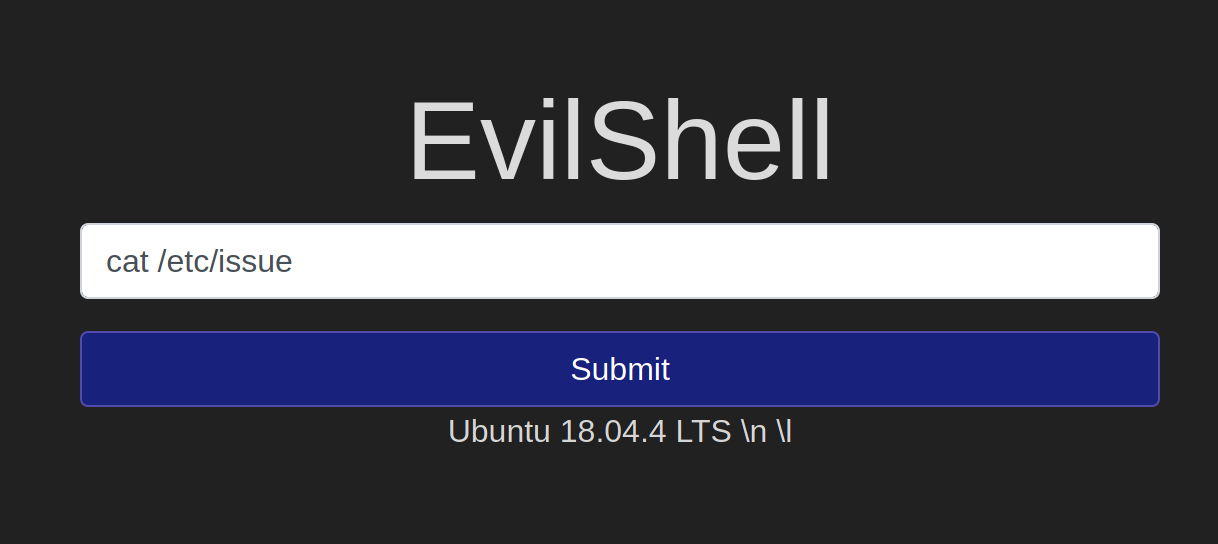
Command Injection: This occurs when user input is passed to system commands. As a result, an attacker is able to execute arbitrary system commands on application servers.
OS Command Injection
If the output of the command, such as ls, is longer, it is best to use the shell in the source code.
view-source:http://$ip/evilshell.php?commandString=ls+-la
cat /etc/issue to view the specific version
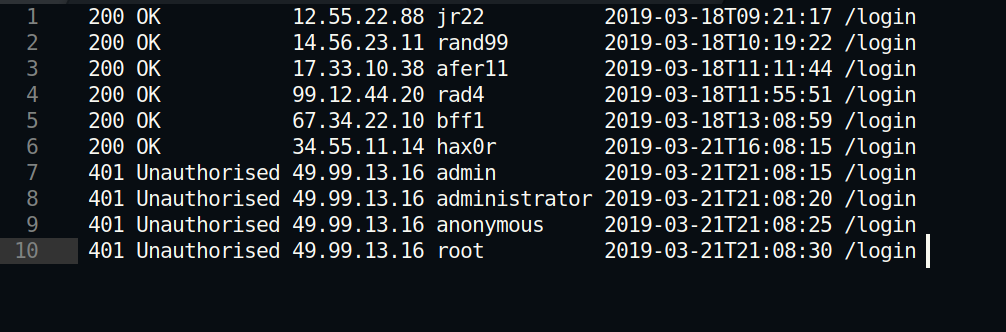
Broken Authentication
Per the room:
Below is a simple demonstration of broken authentication. Because the website developers did not sanitize user input to disallow spaces, we are able to register as known users, change their passwords and login to their personal account.
Sensitive Data Exposure
Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
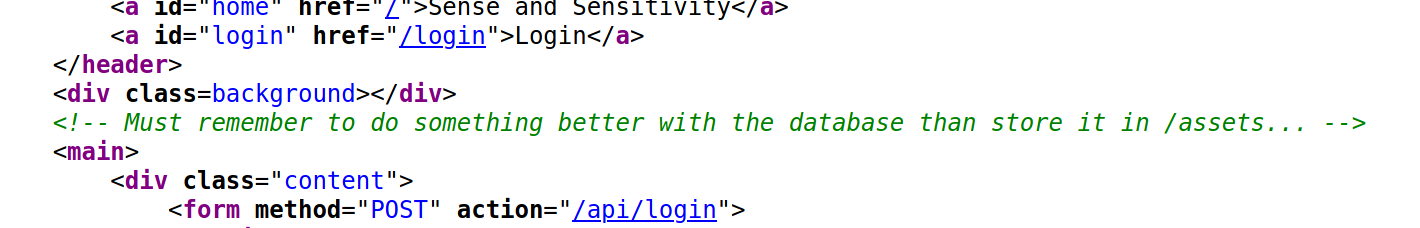
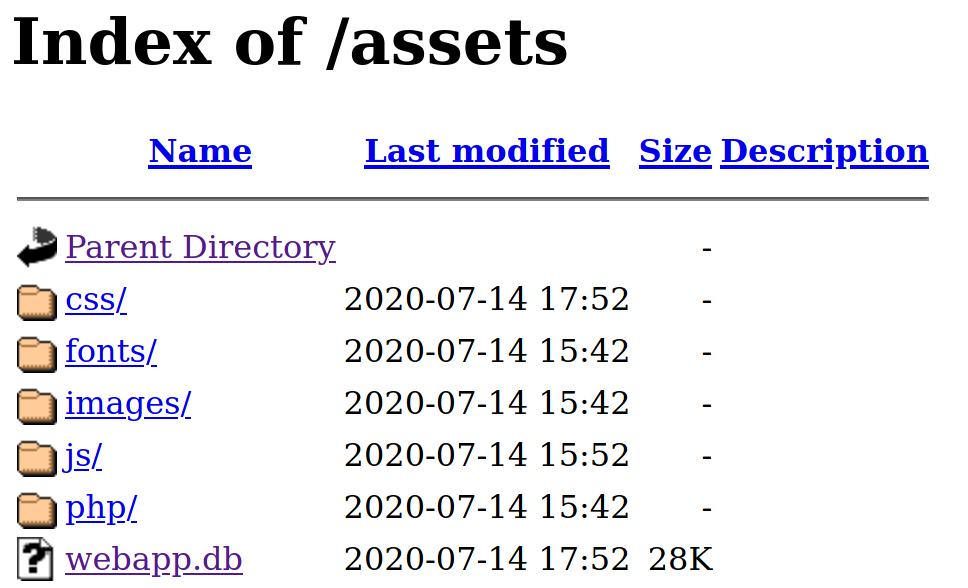
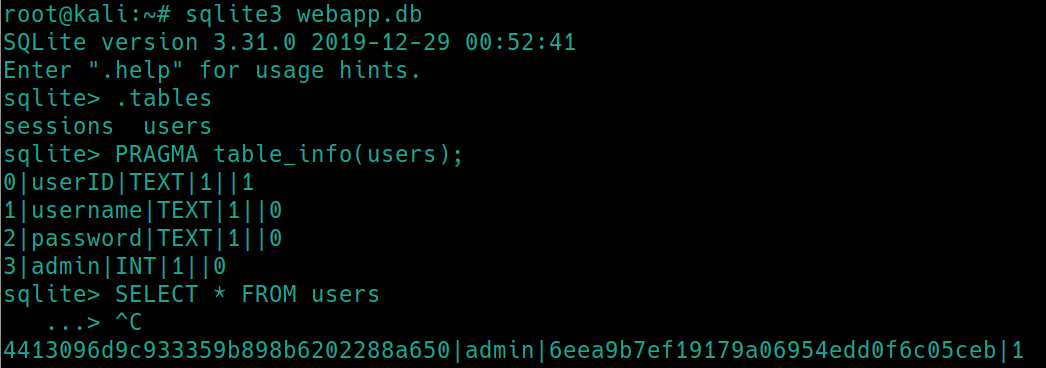
Of course we can always run a directory parsing tool such as dirsearch or gobuster. But sometimes, things are hidden in the source
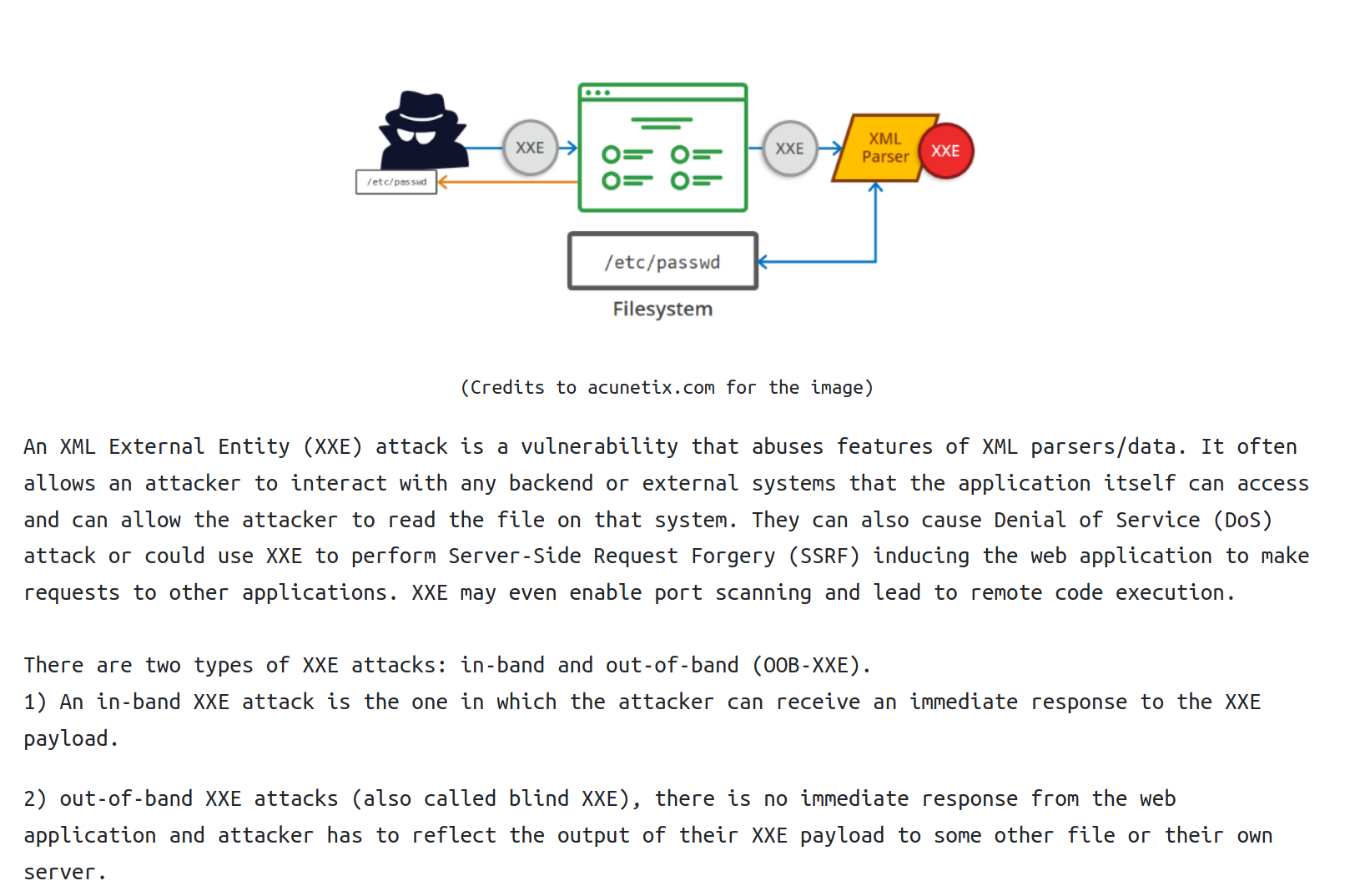
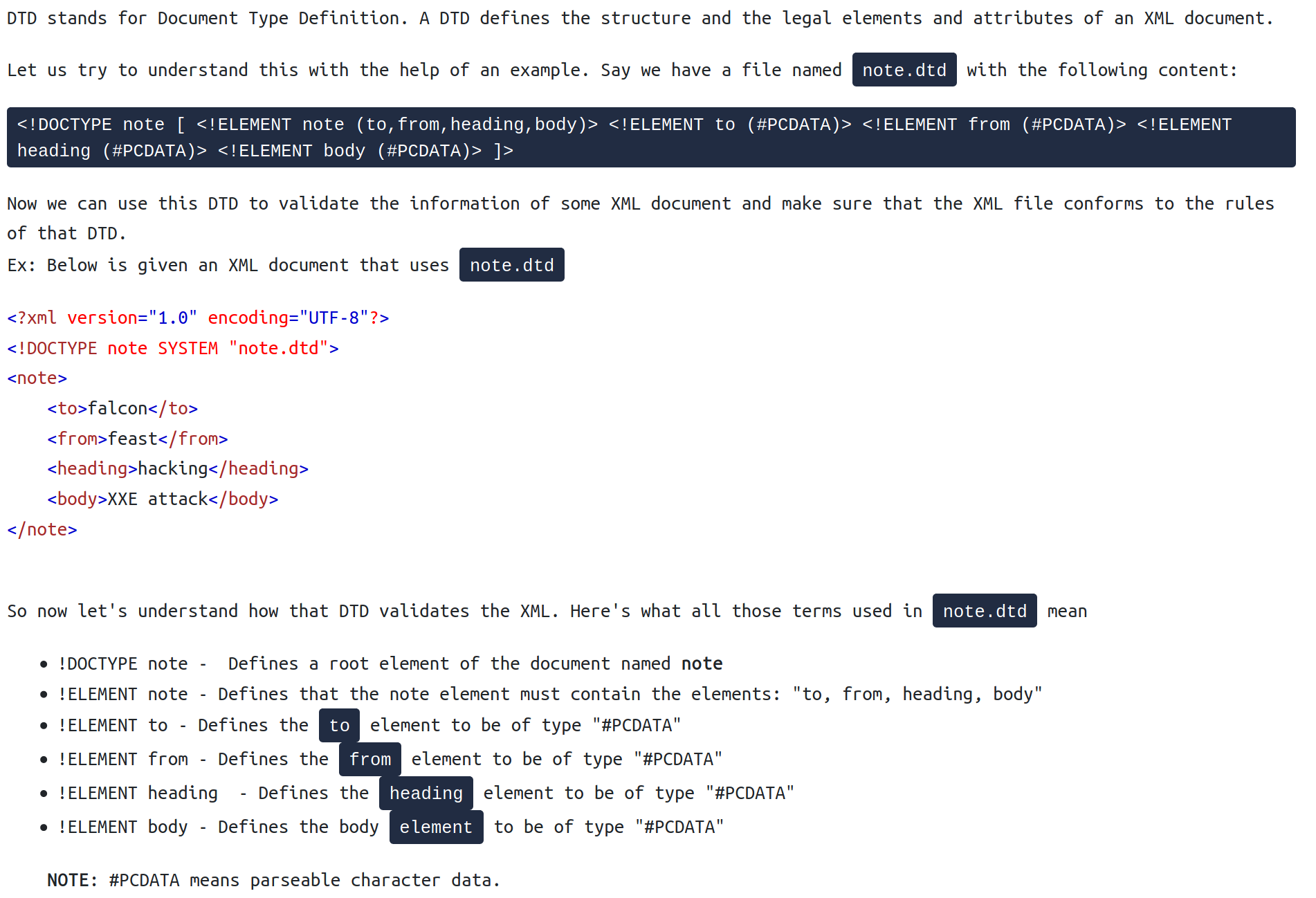
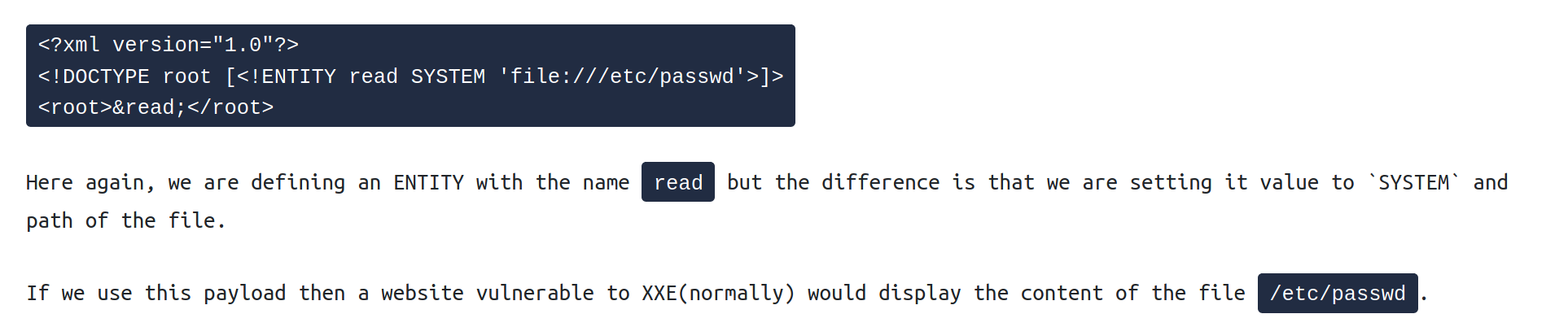
XML External Entity
Broken Access Control
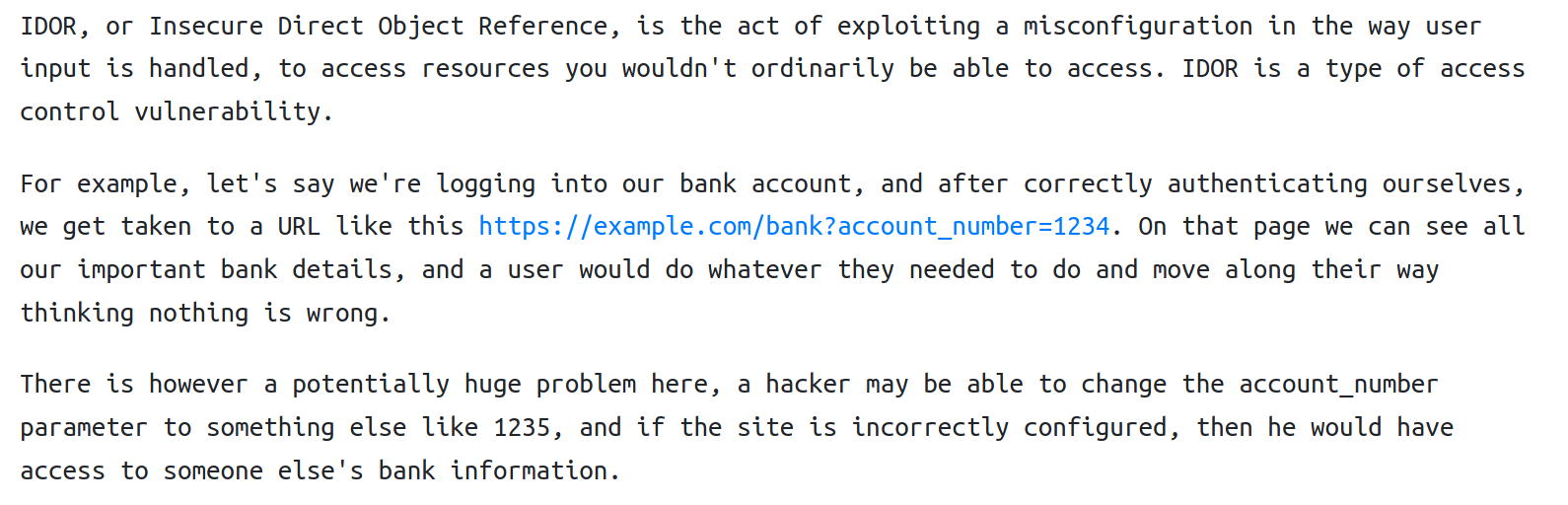
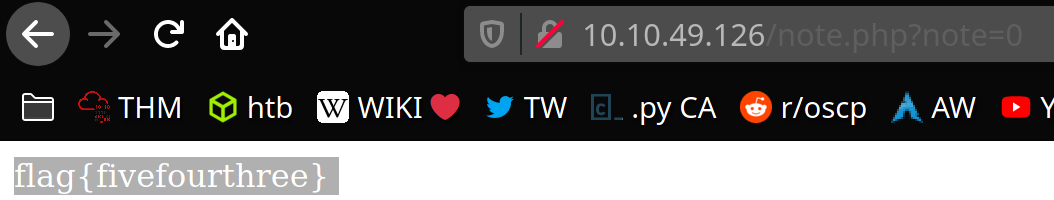
Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data, such as access other users’ accounts, view sensitive files, modify other users’ data, change access rights, etc.
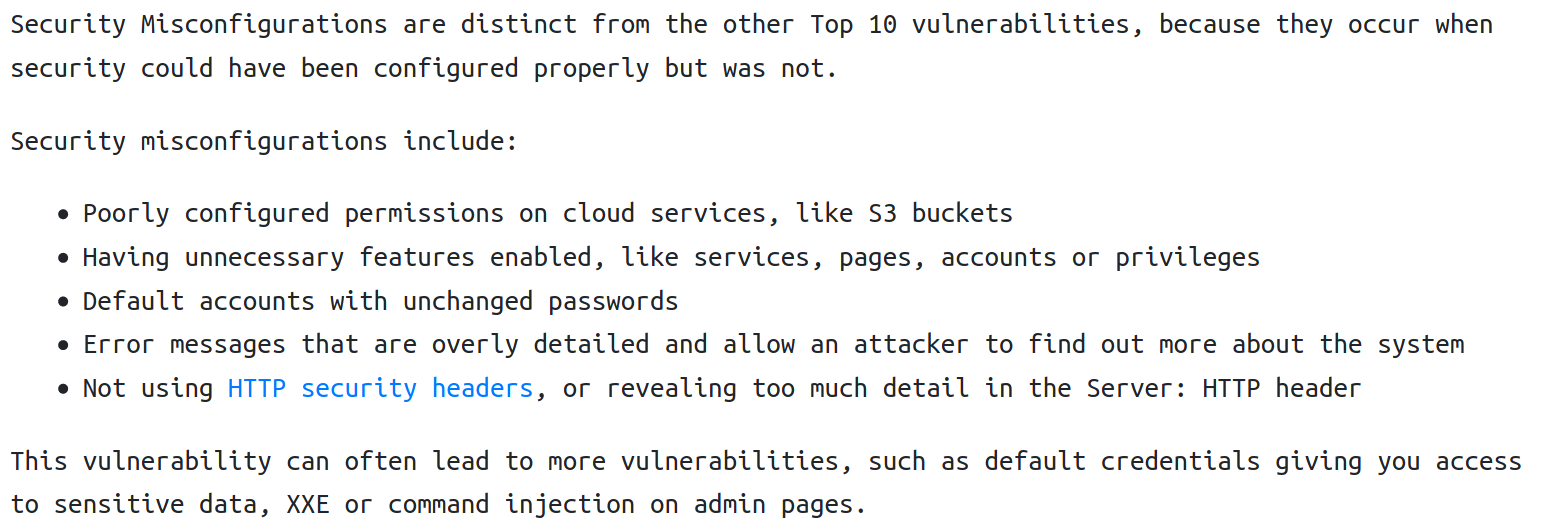
Security Misconfiguration
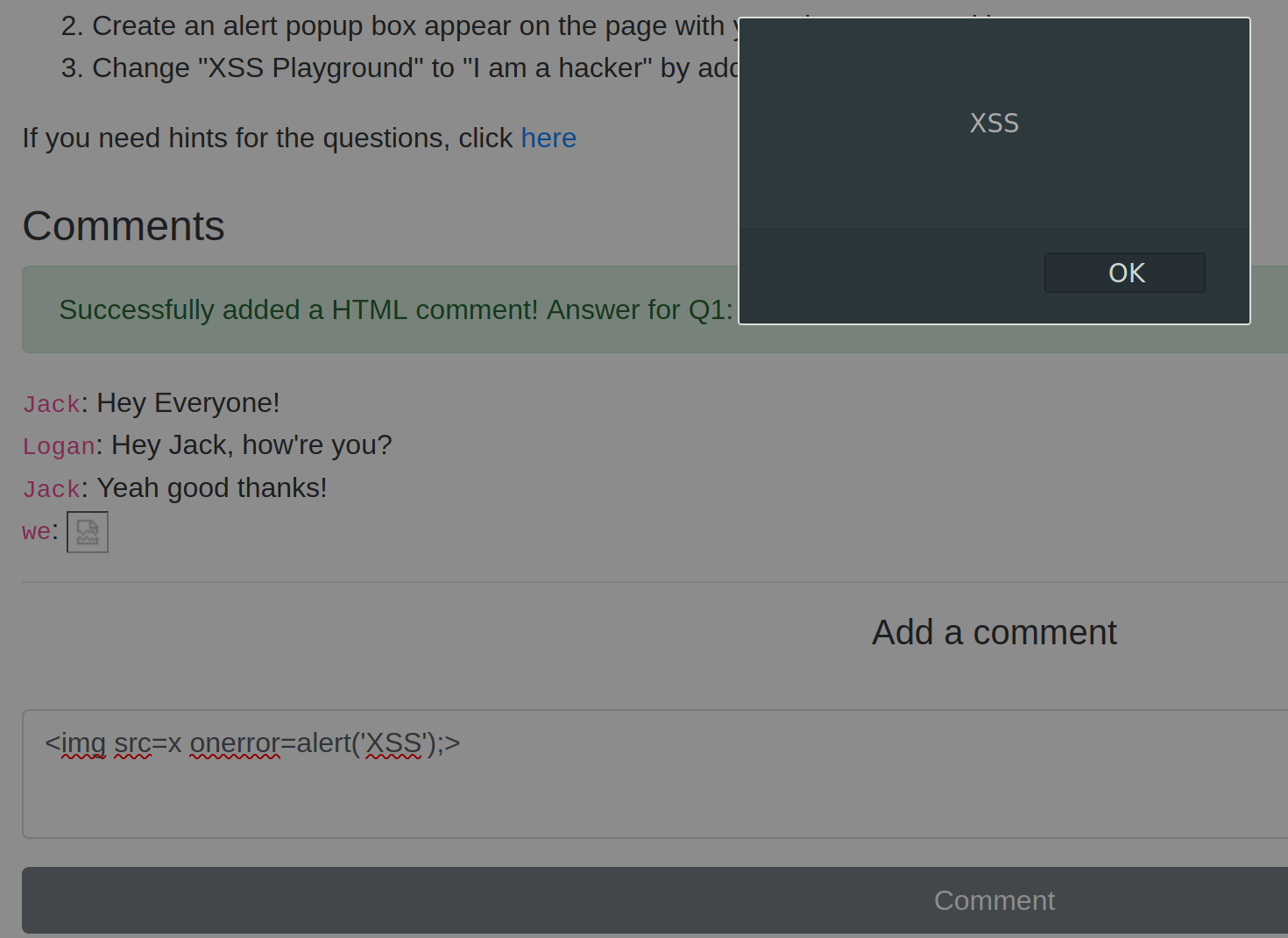
Cross-site Scripting
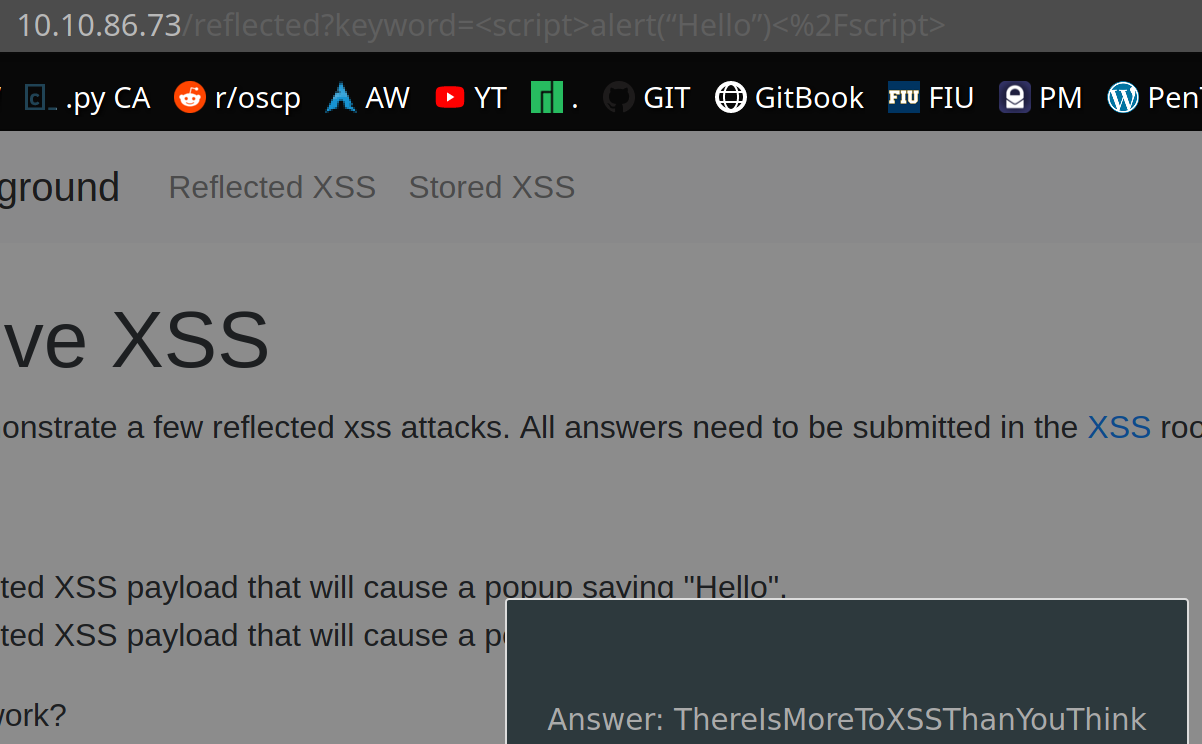
Cross-site scripting aka XSS is a security vulnerability typically found in web applications. It’s a type of injection which can allow an attacker to execute malicious scripts and have it execute on a victim’s machine. A web application is vulnerable to XSS if it uses unsanitized user input. XSS is possible in Javascript, VBScript, Flash and CSS. There are three main types of cross-site scripting:
Stored XSS - the most dangerous type of XSS. This is where a malicious string originates from the website’s database. This often happens when a website allows user input that is not sanitized (remove the "bad parts" of a users input) when inserted into the database.
Reflected XSS - the malicious payload is part of the victims request to the website. The website includes this payload in response back to the user. To summarize, an attacker needs to trick a victim into clicking a URL to execute their malicious payload.
DOM-Based XSS - DOM stands for Document Object Model and is a programming interface for HTML and XML documents. It represents the page so that programs can change the document structure, style and content. A web page is a document and this document can be either displayed in the browser window or as the HTML source.
Insecure Deserialization
Insecure deserialization can be used to impersonate user and admin cookies as well as remote code execution.
Components with Known Vulnerabilities
Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts.
This topic is vague and yet all it takes is for a company to miss one update. Every example is different and is discoverable through detailed enumeration and more often than not, searchsploit
Insufficient Logging & Monitoring
Last updated