Blaster (THM)
sequel to ice
TryHackMe – Blaster Write-Up
topics: Windows Privilege Escalation
Enumeration
Local Privilege Escalation (Exploitation)
Administrator Privilege Escalation
new tools:
tools: nmapAutomator, dirsearch, Remmina, gobuster
Enumeration
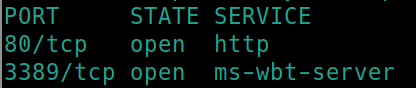
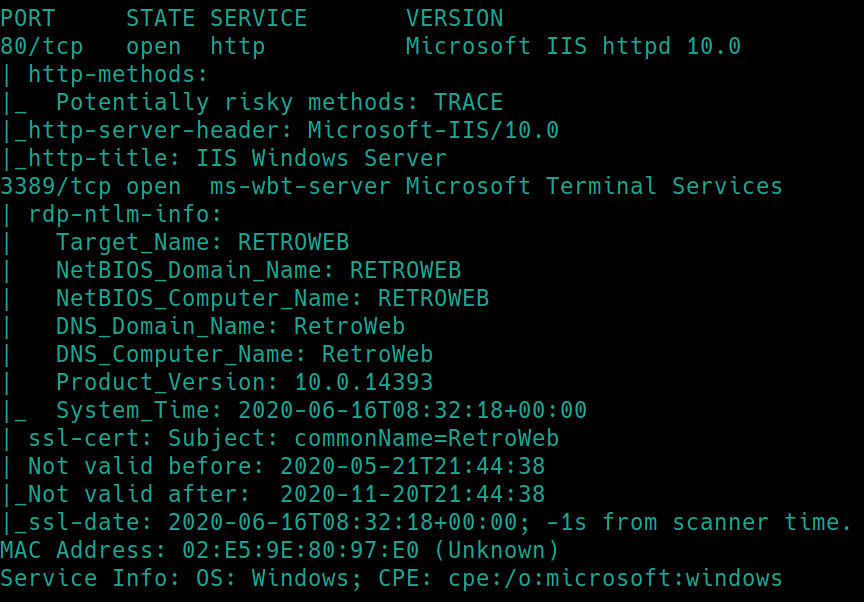
Initial nmap scan ./nmapAutomator.sh $ip Basic
There is a webserver on port 80 as well as RDP open on port 3389. Lets gobuster the website.
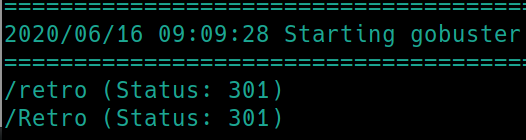
gobuster dir -u http://10.10.72.132:80 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt
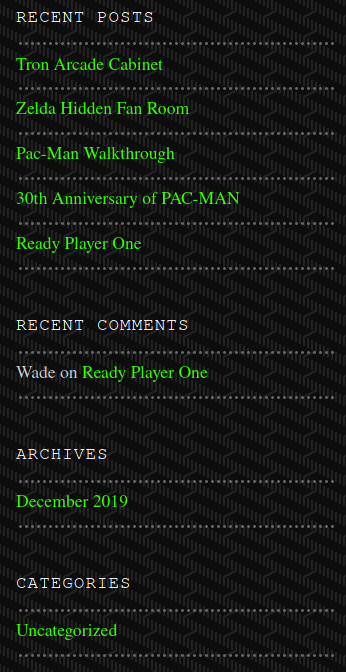
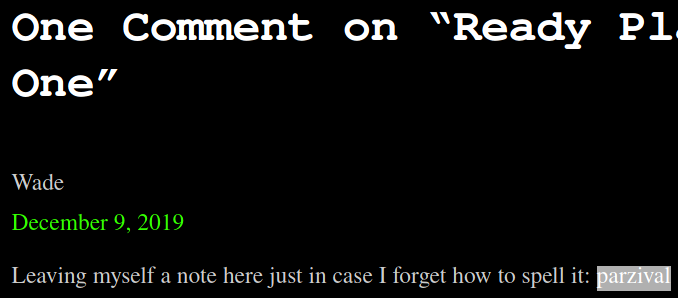
We have a hidden subdrectory named /retro, navigating to this page shows a potential username, Wade
Local Privilege Escalation
With usernames often come passwords or at the very least brute forcing passwords. Lets see what other sensitive information may be lying around here
Inspecting the recent comment reveals that Wade has left his password publically exposed, parzival
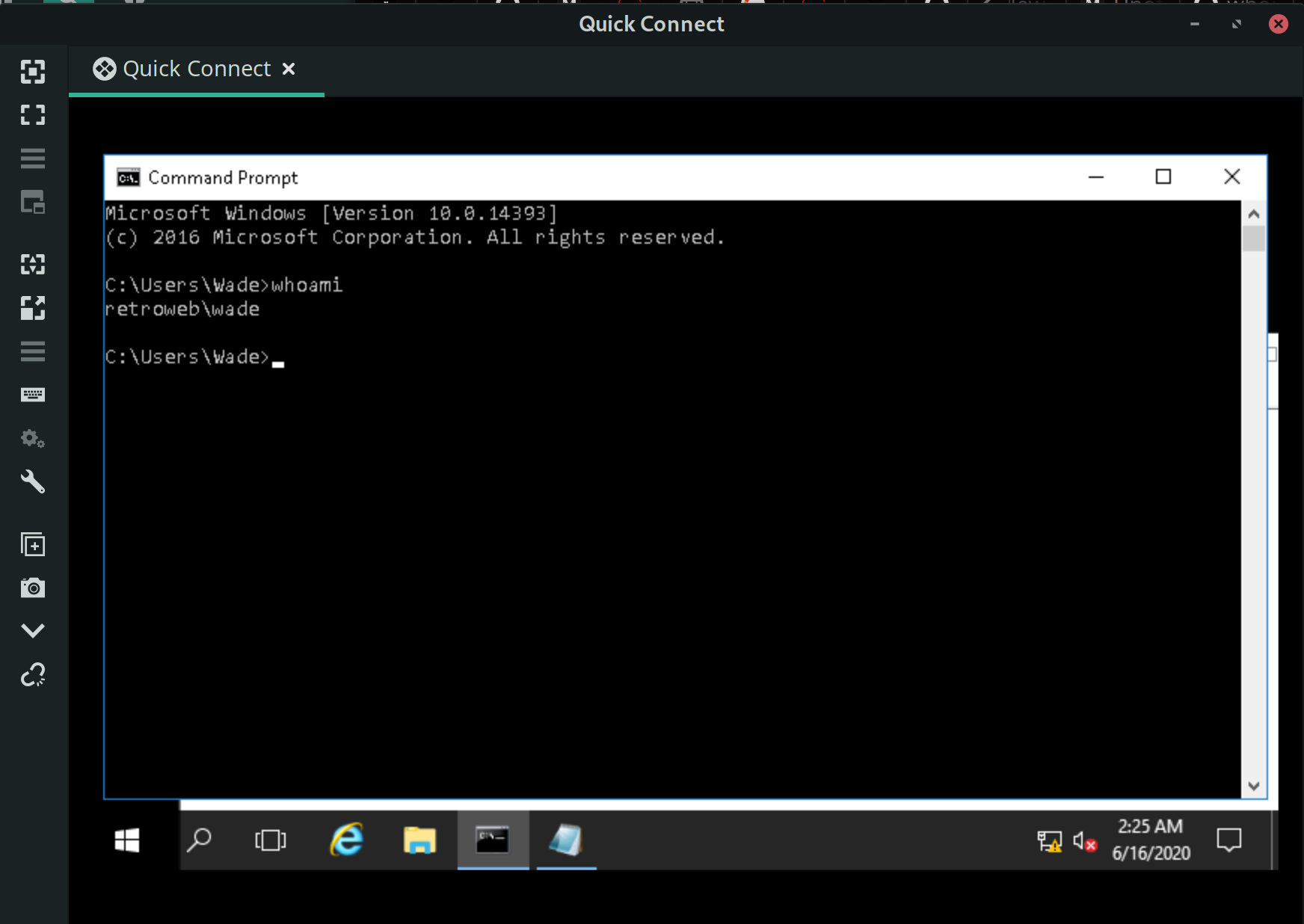
Because RDP is open, we can attempt to login with the creds, Wade:parzival
xfreerdp /u:wade /p:parzival /cert:ignore /v:$ip
Administrator Privilege Escalation
We can snoop around for common windows exploits, but I'd like to get some winPEAS practice in.
Transferring with certutil and running winPEAS.exe >> winpriv.txt yields the output
I could not find anything immediate that stuck out to me, so lets go back to the machine and come back if nothing sticks out.
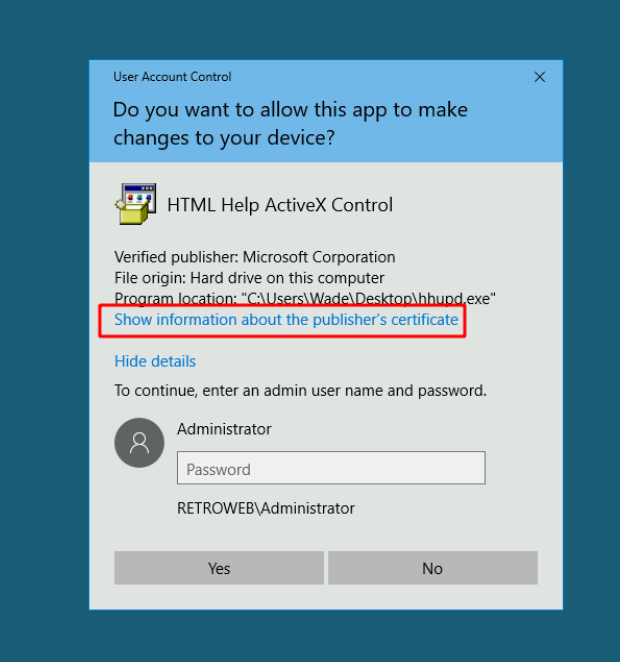
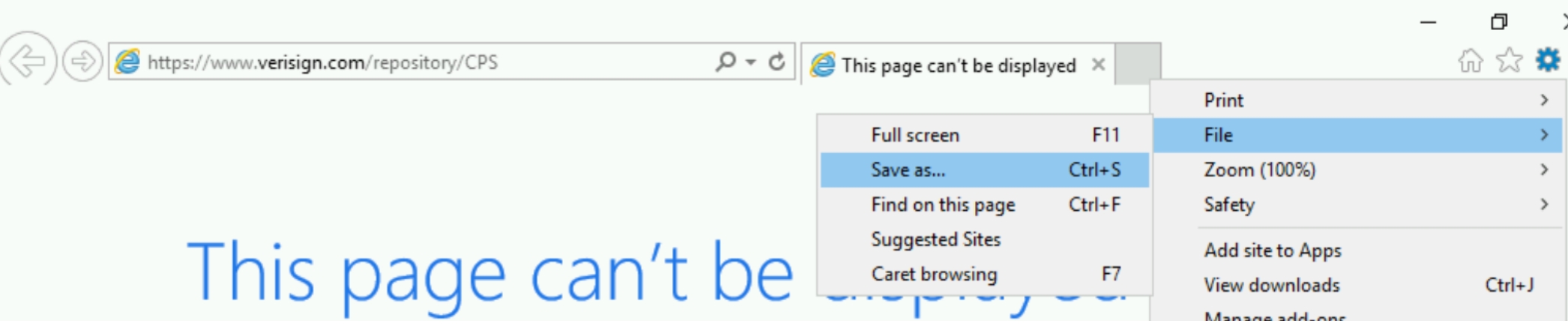
There exists an executable file on the desktop, hhupd.exe. Searching this file reveals these exploit steps to get an NT AUTHORITY\SYSTEM shell. Using CVE-2019-1388. Click run as Admin.
Click show more and then click VeriSign Commercial Software Publishers CA.
Open the file in explorer and click save as
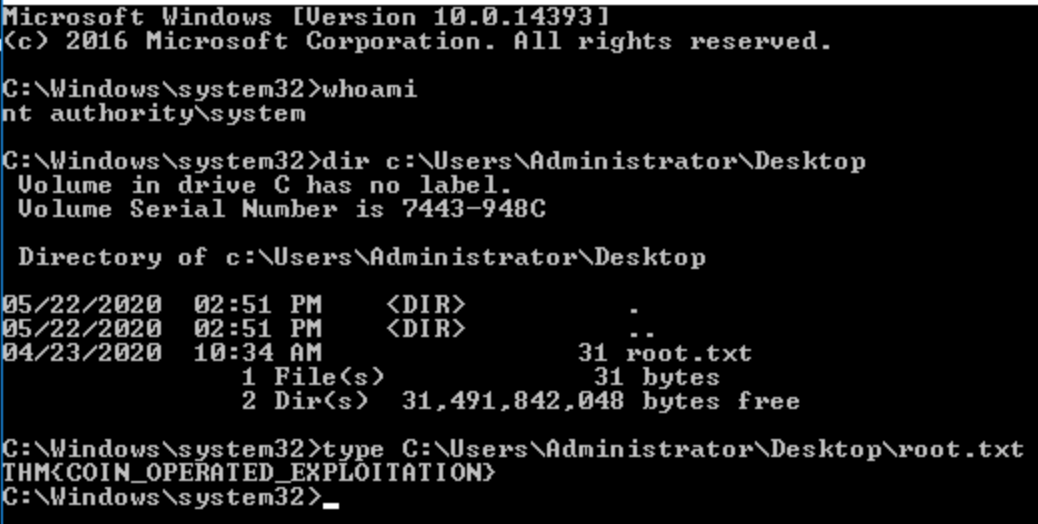
Click Ok which will open a the folder manager. Search for cmd.exe and run the program.
Last updated